- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Device Administration using RADIUS Cisco ISE 2.3
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2018 07:47 AM - edited 02-21-2020 10:43 AM
Hi,
Is it possible using ISE 2.3 as AAA for device administration with RADIUS protocol instead of TACACS+?
If I only enable Device Admin Service in ISE Policy Service, can I use RADIUS for authentication and authorization for network device login?
If that is possible, can you share me the guide of how to configure in ISE 2.3 and in network device (let says it is Cisco Switch)?
So far, I tested in Cisco Switch by using test aaa command, but there is no any log recorded in Cisco ISE. I'm afraid that something configuration is missing in ISE so that the switch can't contact to ISE using RADIUS protocol.
Thank you
Arie
Solved! Go to Solution.
- Labels:
-
Other NAC
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2018 09:35 AM
This guide should help you for network devices, there is also a chapter that covers configuring RADIUS.
Once you get the switch configured properly to contact your ISE server with requests you should be able to create rules for what you need to do.
As a general rule the authentication protocol is going to be PAP, and the attribute details should look like this for the authorization profile.
Access Type = ACCESS_ACCEPT
Service-Type = 6
cisco-av-pair = shell:priv-lvl=15
Other than that you just need to create authentication and authorization rules to match the type of authentication you are doing. (AD, local, etc.)
Hopefully this gives you a good start on what is needed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2018 01:57 AM
Hi,
Enable Session services.
Device administration refers strictly to TACACS.
Regards,
Octavian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2018 09:35 AM
This guide should help you for network devices, there is also a chapter that covers configuring RADIUS.
Once you get the switch configured properly to contact your ISE server with requests you should be able to create rules for what you need to do.
As a general rule the authentication protocol is going to be PAP, and the attribute details should look like this for the authorization profile.
Access Type = ACCESS_ACCEPT
Service-Type = 6
cisco-av-pair = shell:priv-lvl=15
Other than that you just need to create authentication and authorization rules to match the type of authentication you are doing. (AD, local, etc.)
Hopefully this gives you a good start on what is needed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2018 10:16 PM
Hi,
Before I jump in to configuration, I test if the port 1812 and 1813 between switch and ISE is open or not.
Using N7K, I telnet to ISE server and with port 1812 but the connection is timed out (not open). No firewall between N7K and ISE. However, when I check with port 49 (TACACS+), it's open.
I'm afraid that there is something missing with ISE configuration for RADIUS port 1812 and 1813.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2018 12:22 AM - edited 01-12-2018 12:27 AM
If it's a multi-node deployment, be sure to perform your check for RADIUS services against the Policy Service Node(s) (PSNs).
You can check your ISE PSN nodes for the listener from the cli with
tech netstat | i 1812 tech netstat | i 1813
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2018 12:47 AM
Hi,
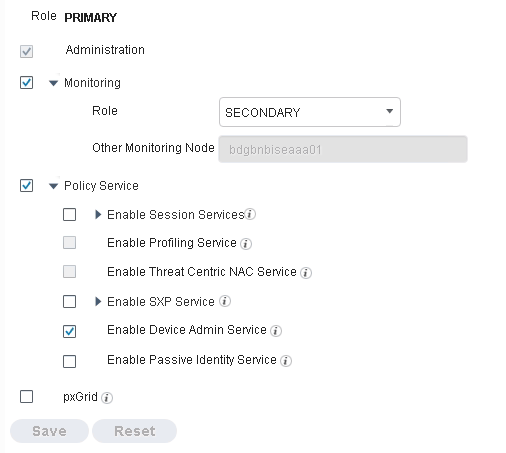
In the Policy Service Node Deployment, I only check Device Admin Service
How to enable RADIUS service?
Also, I tried with the CLI command but nothing to show.
Thank you
Arie
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2018 12:45 AM
Hi,
Tacacs is TCP based.
Radius is UDP - no telnet check....
If you want to check radius connectivity between NAD and ISE just do a #test aaa ....
Thanks,
Octavian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2018 12:49 AM
I see. So that's why I can't check with telnet.
And then, how to make sure that RADIUS service is enabled in ISE?
Thank you
Arie
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2018 01:57 AM
Hi,
Enable Session services.
Device administration refers strictly to TACACS.
Regards,
Octavian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2018 01:13 AM - edited 01-13-2018 01:35 AM
Hi,
I have enable Session Service and I already see the 1812 and 1813 port on netstat
I will continue to policy sets configuration
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2018 01:46 AM
Btw, the authentication and authorization has successfully work. If I'm using RADIUS, can I see the accounting? Where can I find the RADIUS accounting report?
Thanks
Arie
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide