- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE Wired Guest Fallback Authorization for Non-domain Machines
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2023 02:12 PM
Hello all,
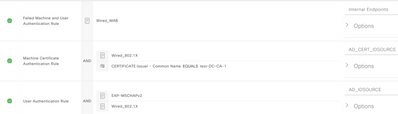
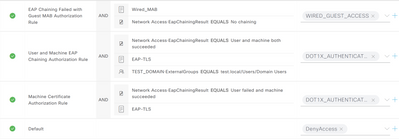
I have implemented EAP chaining using the AnyConnect NAM module for domain-joined machines which is working as expected. What is not working is when I attempt to connect a non-domain computer to a port configured for dot1x and mab. The machine never connects and I don't even see the attempts in the logs. The non-domain machine does not have AnyConnect installed and would be equivalent to an employee bringing a personal machine into the office and connecting it to the wired network (ie no AnyConnect or Internal Certs). I feel like I'm missing something but can't figure it out. Here are some screen shots of my policy set:
Here is the switchport configuration:
interface GigabitEthernet1/0/1
switchport mode access
switchport nonegotiate
authentication event fail action next-method
authentication event server dead action authorize
authentication event server alive action reinitialize
authentication order dot1x mab
authentication priority dot1x mab
authentication port-control auto
authentication violation restrict
mab
dot1x pae authenticator
dot1x timeout tx-period 10
spanning-tree portfast edge
spanning-tree bpduguard enable
I have played around with the config from ISE and the switch port by changing some settings around to see if I can get it to work but all has failed. For instance, in ISE, I've tried changing the order of the AuthC and AuthZ rules. On the switch, I've changed the authentication order and priority parameters around but to no avail. Any assistance in the right direction would be greatly appreciated. Feel free to ask for any additional information.
Thanks!
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
-
Wired
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2023 02:41 PM
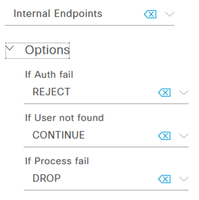
On your AuthC rule for MAB, you need to ensure that ISE allows the session to 'fall-through' to the AuthZ Process if the MAC address is not already in the endpoint database. This is done by setting the option for 'If User not found = CONTINUE'
In your AuthZ Policy, there is little value in having a separate rule for MAB since anything that is not matching your 802.1X rules is going to hit the default. When the Wired Guest use case is deployed, it's common to just set your Guest redirect rule as the result for the Default rule. You would then need an AuthZ rule above it that matches on the Guest flow (and optionally the Remember Me flow) and provides the resulting authorization.
See the ISE Guest Access Prescriptive Deployment Guide for more information on how the Guest flow works and example policies.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2023 02:41 PM
On your AuthC rule for MAB, you need to ensure that ISE allows the session to 'fall-through' to the AuthZ Process if the MAC address is not already in the endpoint database. This is done by setting the option for 'If User not found = CONTINUE'
In your AuthZ Policy, there is little value in having a separate rule for MAB since anything that is not matching your 802.1X rules is going to hit the default. When the Wired Guest use case is deployed, it's common to just set your Guest redirect rule as the result for the Default rule. You would then need an AuthZ rule above it that matches on the Guest flow (and optionally the Remember Me flow) and provides the resulting authorization.
See the ISE Guest Access Prescriptive Deployment Guide for more information on how the Guest flow works and example policies.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2023 05:28 AM
Thank you, Greg. I apologize for the late response but appreciate yours. I will review the URL provided and test it out in my lab to confirm all is working as expected. Thanks again!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide