- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Rittal cmc 3rd Vendor attributes
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Rittal cmc 3rd Vendor attributes
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2019 04:31 AM
Hi community,
i want to authC and authZ Rittal CMC devices with ISE 2.3.
I think the radius process is not the problem for me.
I don't know how to add this device into ISE dictionaries with the appropriate attributes.
I'am searching for a solution on the following page. But unsuccessfully.
No Rittal device is listed on the link above.
Do anybody ever solve and implement such a device?
For an early answer i will be thankfully.
Kind Regards
Jacob
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2019 11:20 AM
You likely want to build a custom profile to use to identify the device. Here is a compact overview that Katherine put together on profiling that may give you a starting place.
http://www.network-node.com/blog/2019/10/18/ise-custom-profiles-cant-see-the-forest-from-the-trees
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2019 05:53 AM
Hello Damien,
that is exactly my problem. I have to create a device profile, but before i have to create a new
dictionary under System->Radius for the Rittal device.
But thank you very much for your great help and link.
Kind Regards,
Jacob
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2019 05:52 PM
I had a similar requirement with some Juniper devices that were not present in the ISE RADIUS Dictionary. I was able to create these attributes because the 3rd party vendor was quite clear about the attribute values and their type (STRING/INTEGER etc)
If you have this, then it's easy. If you have to reverse engineer, then it's more effort. What information do you have?
As @Damien Miller pointed out, you can also use Device Profiles - but the purpose of Device Profiles is to provide an abstraction layer to the user, which leads to a normalization of the Policy Set configuration. What does this mean exactly? It means that you can use a nice Policy Set Condition abstraction like, e.g. "Wireless 802.1X" (which already exists in ISE) and you don't need to care how Cisco, Aruba, HPE, Meraki do it - because the magic mappings/definitions are defined in Device Profiles. But these device profiles do not define the 3rd party RADIUS attributes themselves. Device Profiles define how we should interpret them for the purposes of Policy Set logic. Device Profiles are pure genius in the ISE product and if used wisely, can be very powerful.
One caveat with device profiles. You have to match the Device Profile type that is assigned to your Authorization Profile, with the Device Profile that is assigned to the NAS - UNLESS - you use a generic Device Profile in Authorization Profile. EEEH? What?? e.g. Your NAS is an Aruba WLC. You Policy Set evaluates an AuthZ Result that you want to return to the Aruba WLC - and this Profile is of type "Cisco". ISE will let you do this, but it will result in failure - the AuthZ profile won't be sent out. This means that you need to pay special attention. It also explains why some people still use Cisco Device Profiles everywhere, even in a multi-vendor NAS deployment.
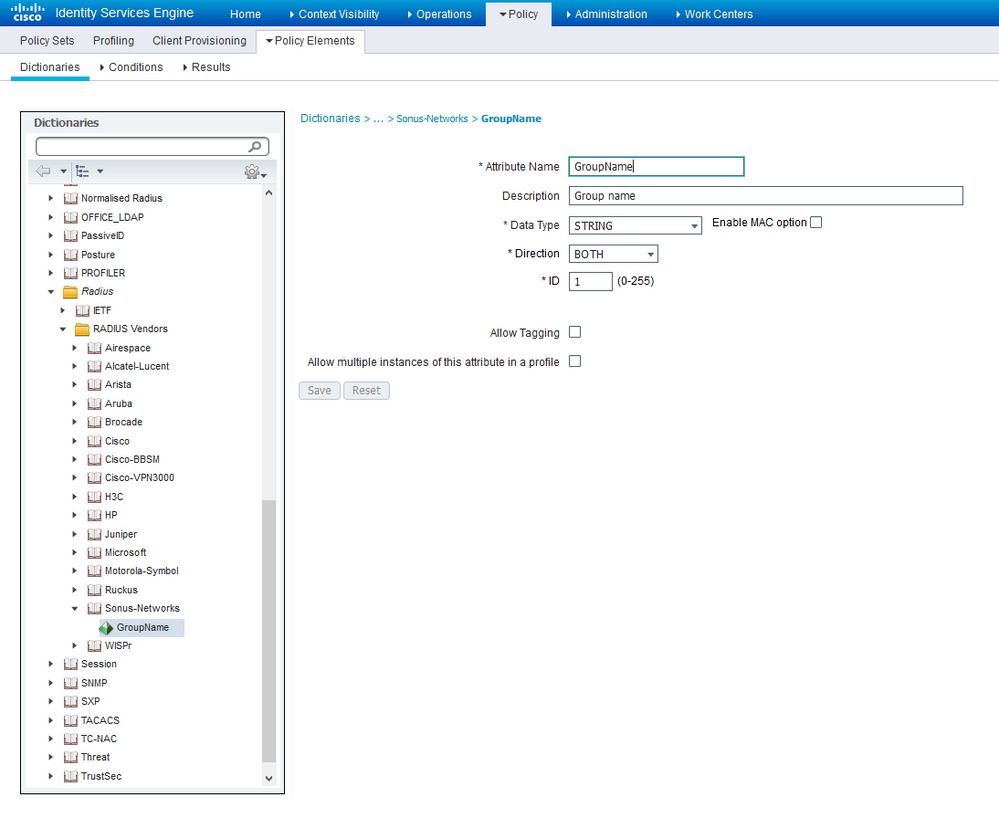
If you have a 3rd party NAS which uses its own bizzare RADIUS attributes, then you need to add them to the ISE Dictionary as shown below:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2019 06:04 AM
Hello Arne,
i try the same respectively similar settings with Riverbed and it works very well.
With Riverbed i'am able to download the ISE RADIUS Dictionary settings from.....
In this case with Rittal.cmc i haven't any vendor specific Radius attributes.
Only in a manual i found the following hint about the attributes.
So i try to do it with 2 attributes.
1. Group Name
2. Group Selection with "cmc-group"
Next week i give you a feedback, if my settings are functional for this purpose.
Thank you very much for your great help. Also Damien.
Kind Regards,
Jacob
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide