- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Adding third firewall
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Adding third firewall
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2023 09:54 AM
I am in the process of adding a third firewall to our network. We have two FTD 1140 in HA mode in the data center. The new firewall is a FTDv but will be replaced with a 1120 when it becomes available. Currently our office is connected to our data center using a VPLS. This is not going to change but the goal is to provide internet access directly from the office. The issue that I am running into is inter-vlan routing. Before adding the third firewall it wasn't a problem. Traffic between vlans would traverse the firewall and we use ACLs to control access. Now with the new firewall if I set the default gateway to be the FTDv I can access anything on the same vlan but I can't cross vlans. I know this is a routing issue and I am wondering what the best way to handle this would be.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2023 11:12 AM
@gcook0001 can you provide a diagram, as your topology is not clear.
Is routing setup correctly on connected devices to route through the FTD?
And does the FTD have all the correct routes?
Do you have Access Control rules to permit the traffic?
Do you have NAT setup, which could unintentially translate traffic?
Can you run packet-tracer from the CLI to simulate the traffic flow and provide the output for review.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2023 12:30 PM
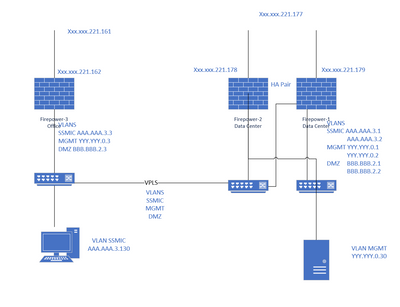
Thanks for the reply. Here is what I am looking at
The goal is to have the PC access the internet via Firepower-3, the server via Firepower-1. I need to have the PC be
able to reach the server, and vice versa. I was partially able to do this by adding a second gateway to my test pc so that it has both AAA.AAA.3.3 and AAA.AAA.3.1. Not sure if this is the best way to this. We do want the traffic traversing the firewalls when crossing vlans as we want to inspect the traffic.
I have the static routes setup
Firepower-1 - NAT Rules after
Firepower-3 - Nat Rules after
> packet-tracer input OFFICE-SSMIC icmp 172.29.3.100 0 0 172.30.0.30
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Elapsed time: 8400 ns
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 2
Type: ROUTE-LOOKUP
Subtype: No ECMP load balancing
Result: ALLOW
Elapsed time: 21900 ns
Config:
Additional Information:
Destination is locally connected. No ECMP load balancing.
Found next-hop 172.30.0.30 using egress ifc OFFICE-MGMT(vrfid:0)
Phase: 3
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Elapsed time: 7050 ns
Config:
access-group CSM_FW_ACL_ global
access-list CSM_FW_ACL_ advanced permit ip any any rule-id 268459009
access-list CSM_FW_ACL_ remark rule-id 268459009: ACCESS POLICY: Office-Policy - Mandatory
access-list CSM_FW_ACL_ remark rule-id 268459009: L7 RULE: test
Additional Information:
This packet will be sent to snort for additional processing where a verdict will be reached
Phase: 4
Type: CONN-SETTINGS
Subtype:
Result: ALLOW
Elapsed time: 7050 ns
Config:
class-map class-default
match any
policy-map global_policy
class class-default
set connection advanced-options UM_STATIC_TCP_MAP
service-policy global_policy global
Additional Information:
Phase: 5
Type: NAT
Subtype: per-session
Result: ALLOW
Elapsed time: 7050 ns
Config:
Additional Information:
Phase: 6
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Elapsed time: 7050 ns
Config:
Additional Information:
Phase: 7
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Elapsed time: 46500 ns
Config:
class-map inspection_default
match default-inspection-traffic
policy-map global_policy
class inspection_default
inspect icmp
service-policy global_policy global
Additional Information:
Phase: 8
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Elapsed time: 4200 ns
Config:
Additional Information:
Phase: 9
Type: QOS
Subtype:
Result: ALLOW
Elapsed time: 0 ns
Config:
Additional Information:
Phase: 10
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Elapsed time: 9900 ns
Config:
Additional Information:
New flow created with id 17553, packet dispatched to next module
Phase: 11
Type: EXTERNAL-INSPECT
Subtype:
Result: ALLOW
Elapsed time: 16800 ns
Config:
Additional Information:
Application: 'SNORT Inspect'
Phase: 12
Type: SNORT
Subtype: appid
Result: ALLOW
Elapsed time: 39014 ns
Config:
Additional Information:
service: ICMP(3501), client: (0), payload: (0), misc: (0)
Phase: 13
Type: SNORT
Subtype: firewall
Result: ALLOW
Elapsed time: 3662104 ns
Config:
Network 0, Inspection 0, Detection 0, Rule ID 268459009
Additional Information:
Starting rule matching, zone 4 -> 20, geo 0 -> 0, vlan 0, src sgt: 0, src sgt type: unknown, dst sgt: 0, dst sgt type: unknown, user 9999997, no url or host, no xff
Matched rule ids 268459009 - Allow
Result:
input-interface: OFFICE-SSMIC(vrfid:0)
input-status: up
input-line-status: up
output-interface: OFFICE-MGMT(vrfid:0)
output-status: up
output-line-status: up
Action: drop
Time Taken: 3837018 ns
Drop-reason: (inspect-icmp-seq-num-not-matched) ICMP Inspect seq num not matched, Drop-location: frame 0x0000556c7084ee08 flow (NA)/NA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2023 12:36 PM
@gcook0001 you could plug the VPLS directly into Firepower 3 on another dedicated internet.
Create sub-interfaces for each of the VLANs, use the Firepower SVI IP for the VLAN as the default gateway for the PCs on those VLANs. That way all traffic between VLANs is routed to the firewall and subsequently routed to another VLAN (if ACP) permits, the Internet or access the servers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2023 01:02 PM
I just thought of something. In the given diagram when the PC pings the Server since they are on different vlans the traffic goes to firepower-3, then it tries to send the traffic back to the switch. I believe this would have the same affect as a hairpin vpn connection.
So if connect the VPLS to the firewall instead it would eliminate that issue. I may have to do it at both ends for the same reason.
Please correct me if I am wrong on this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2023 01:11 PM - edited 02-16-2023 01:15 PM
@gcook0001 yes, it sounds like that what you've configured - traffic from the PC is sent up to Firepower3 (as it's the default gateway) then back down to the switch. I imagine the return traffic does not traverse Firepower3
So use the suggestion above, route the traffic in the different VLANs and the VPLS connection between separate FTD interfaces (physical or sub-interfaces), with FTD doing the routing between the VLANs and over the VPLS. Return traffic would have to take the same path.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2023 10:30 AM
Yeah. Unfortunately that was not the issue. Still trying to figure this out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-06-2023 01:18 PM
I found the following information on setting up NAT for multiple devices. What I am trying to figure out is how does a device on the internal network select which firewall to use.
Customizing NAT Rules for Multiple Devices
Because the NAT policy is shared, you can assign a given policy to more than one device. However, you can configure at most one auto NAT rule for a given object. Thus, if you want to configure different translations for an object based on the specific device doing the translation, you need to carefully configure the interface objects (security zones or interface groups) and define network object overrides for the translated address.
The interface objects determine on which devices a rule gets configured. The network object overrides determine what IP addresses are used by a given device for that object.
Consider the following scenario:
FTD-A and FTD-B have inside networks 192.168.1.0/24 attached to the interface named “inside.”
On FTD-A, you want to translate all 192.168.1.0/24 addresses to a NAT pool in the 10.100.10.10 - 10.100.10.200 range when going to the “outside” interface.
On FTD-B, you want to translate all 192.168.1.0/24 addresses to a NAT pool in the 10.200.10.10 - 10.200.10.200 range when going to the “outside” interface.
To accomplish the above, you would do the following. Although this example rule is for dynamic auto NAT, you can generalize the technique for any type of NAT rule.
Procedure
| Step 1 | Create the security zones for the inside and outside interfaces.
| ||
| Step 2 | Create the network object for the original inside network on the Object Management page.
| ||
| Step 3 | Create the network object for the translated NAT pool and define overrides.
| ||
| Step 4 | Configure the NAT rule.
|
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2023 12:58 PM
So I was finally able to find a solution that works. I had two issues. The first is in ESXI the port groups need to have the VLAN set to 0.
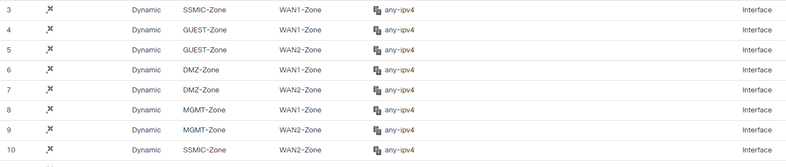
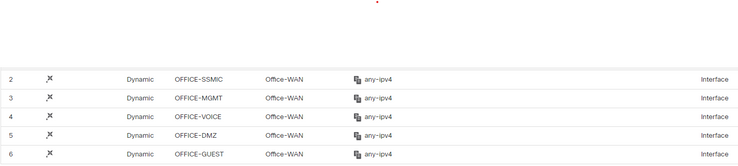
The second thing is in the FMC when creating the interfaces for the third firewall since the subnets span all the firewalls you need to use the same security zones on all the firewalls. I was using a seperate security zone on the third firewall since if I made a change it would ask me to deploy the change to all the firewalls. I wasn't sure if that would cause an issue - it doesn't.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide