- Cisco Community
- Technology and Support
- Security
- Network Security
- %ASA-3-305006
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
%ASA-3-305006
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2012 01:44 AM - edited 03-11-2019 04:08 PM
hi people
I have a issue when i trying with the Cisco VPN- Client, when i connect with this profile out of my network i can connect with no problems in this VPN, but then when i connect in my network can´t. I dont have any received packet´s. i show you in the picture below.
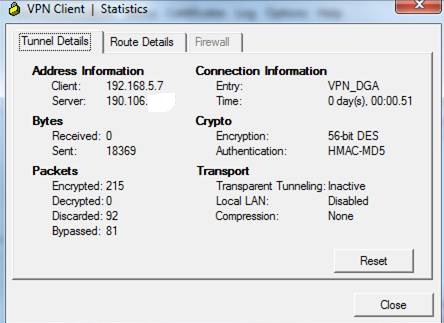
I have a ASA 5520, When i try to connect with the VPN client show me this messege "
"%ASA-3-305006: regular translation creation failed for protocol 50 src INSIDE:192.168.50.149 dst OUTSIDE:190.106.X.X"
I have others VPN connections and i don´t have this problemes,
I have in my configuration
"crypto isakmp nat-traversal"
" inspect ipsec-pass-thru "
I see in some of forums that is the solution for this problem but not in my case
Regards.
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2012 01:06 AM
Hello Adan,
Can you share with us the running configuration>
Regards,
Julio
Senior Network Security and Core Specialist
CCIE #42930, 2xCCNP, JNCIP-SEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2012 01:46 AM
ASA Version 8.2(1)
!
interface GigabitEthernet0/0
description ***** OUTSIDE *****
nameif OUTSIDE
security-level 0
ip address 186.73.X.X 255.255.255.248
!
interface GigabitEthernet0/1
description ***** INSIDE *****
nameif INSIDE
security-level 100
no ip address
interface GigabitEthernet0/3
description ***** DMZ *****
nameif DMZ
security-level 10
ip address 10.254.254.1 255.255.255.248
!
object-group protocol TCP-UDP
protocol-object tcp
protocol-object udp
object-group service MONITOREO tcp
port-object eq https
port-object eq 8443
port-object eq 8100
port-object eq 8200
port-object eq 8300
port-object eq 8400
port-object eq 3389
access-list VPN_NAT0 remark ********************* ACL NAT0 PARA VPNs *********************
access-list VPN_NAT0 extended permit ip 192.168.99.0 255.255.255.0 192.168.0.0 255.255.255.0
access-list VPN_NAT0 extended permit ip 192.168.99.0 255.255.255.0 192.168.22.0 255.255.255.0
access-list VPN_NAT0 extended permit ip 192.168.99.0 255.255.255.0 192.168.6.0 255.255.255.0
access-list VPN_NAT0 extended permit ip 192.168.98.0 255.255.255.0 192.168.0.0 255.255.255.0
access-list VPN_NAT0 extended permit ip 192.168.98.0 255.255.255.0 192.168.22.0 255.255.255.0
access-list VPN_NAT0 extended permit ip 192.168.98.0 255.255.255.0 192.168.6.0 255.255.255.0
access-list VPN_NAT0 extended permit ip 192.168.99.0 255.255.255.0 10.254.254.0 255.255.255.248
access-list VPN_NAT0 extended permit ip 192.168.98.0 255.255.255.0 172.39.1.0 255.255.255.0
access-list VPN_NAT0 extended permit ip 192.168.99.0 255.255.255.0 172.39.1.0 255.255.255.0
access-list VPN_NAT0 remark ******************* ACL NAT0 PARA CLIENTES *******************
access-list VPN_NAT0 extended permit ip 192.168.99.0 255.255.255.0 10.254.254.8 255.255.255.252
access-list VPN_NAT0 extended permit ip 192.168.99.0 255.255.255.0 10.254.254.12 255.255.255.252
access-list VPN_NAT0 extended permit ip 192.168.99.0 255.255.255.0 10.254.254.16 255.255.255.252
access-list VPN_NAT0 remark ********************* ACL NAT0 PARA VPNs *********************
access-list VPN_NAT0 remark ******************* ACL NAT0 PARA CLIENTES *******************
access-list IN extended deny object-group TCP-UDP any any eq 1434
access-list IN extended deny object-group TCP-UDP any any range 995 999
access-list IN extended deny object-group TCP-UDP any any eq 65000
access-list IN extended deny object-group TCP-UDP any any eq 31338
access-list IN extended deny object-group TCP-UDP any any eq 31337
access-list IN extended deny object-group TCP-UDP any any eq 27374
access-list IN extended deny object-group TCP-UDP any any eq 12345
access-list IN extended deny object-group TCP-UDP any any eq 9996
access-list IN extended deny object-group TCP-UDP any any eq 8866
access-list IN extended deny object-group TCP-UDP any any eq 6677
access-list IN extended deny object-group TCP-UDP any any eq 5554
access-list IN extended deny object-group TCP-UDP any any eq 5190
access-list IN extended deny object-group TCP-UDP any any eq 4000
access-list IN extended deny object-group TCP-UDP any any range 135 139
access-list IN extended deny object-group TCP-UDP any any eq 6667
access-list IN extended permit tcp 192.168.99.0 255.255.255.0 10.254.254.0 255.255.255.248
access-list IN extended permit ip any any
access-list IN remark ****************************************************
access-list OUT remark ********** ENTRADAS DE INTERNET **********
access-list OUT extended deny tcp any any eq smtp log
access-list OUT extended deny tcp any eq smtp any log
access-list OUT extended permit icmp any any
access-list OUT extended permit tcp any host 186.Y.X.X eq ssh log
access-list OUT extended permit tcp any host 186.Y.X.Z eq https
access-list OUT extended permit tcp any host 186.Y.X.Z eq www
access-list OUT extended permit tcp any host 186.Y.X.V eq 8400
access-list OUT extended permit tcp any host 186.Y.X.V eq 8443
access-list OUT extended permit tcp any host 186.Y.X.V eq 8100
access-list OUT extended permit tcp any host 186.Y.X.V eq 8200
access-list OUT extended permit tcp any host 186.Y.X.V eq 8300
access-list OUT extended permit tcp any host 186.Y.X.V eq https
access-list OUT extended deny ip any any
access-list OUT remark ********** ENTRADAS DE INTERNET **********
access-list DMZ-OUT remark *************** ACL NAT0 DMZ ***************
access-list DMZ-OUT extended permit ip 10.254.254.0 255.255.255.248 192.168.99.0 255.255.255.0
access-list DMZ-OUT extended permit ip 10.254.254.0 255.255.255.248 192.168.0.0 255.255.255.0
access-list DMZ-OUT extended permit ip 10.254.254.0 255.255.255.248 192.168.6.0 255.255.255.0
access-list DMZ-OUT extended permit ip 10.254.254.0 255.255.255.248 172.39.1.0 255.255.255.0
access-list DMZ-OUT remark ********** ACL NAT0 CLIENTES DMZ ***********
access-list DMZ-OUT extended permit ip 10.254.254.0 255.255.255.248 10.254.254.8 255.255.255.252
access-list DMZ-OUT extended permit ip 10.254.254.0 255.255.255.248 10.254.254.12 255.255.255.252
access-list DMZ-OUT extended permit ip 10.254.254.0 255.255.255.248 10.254.254.16 255.255.255.252
access-list DMZ-OUT extended permit ip 10.254.254.0 255.255.255.248 10.254.254.24 255.255.255.248
access-list DMZ-OUT extended permit ip 10.254.254.0 255.255.255.248 host 192.168.99.127
access-list DMZ-OUT extended permit ip 10.254.254.0 255.255.255.248 10.254.254.32 255.255.255.252
access-list DMZ-OUT remark ********** ACL NAT0 CLIENTES DMZ ***********
access-list DMZ-OUT remark *************** ACL NAT0 DMZ ***************
access-list DMZ-IN remark *************** ACL INSIDE ***************
access-list DMZ-IN extended permit icmp any any
access-list DMZ-IN extended permit tcp host 10.254.254.5 host 192.168.0.40 eq smtp
access-list DMZ-IN extended permit ip 10.254.254.0 255.255.255.248 any
access-list NAT-DATOS-NOC remark **************ACL REDES NATEADAS A INTERNET *********************
access-list NAT-DATOS-NOC extended permit ip 192.168.99.0 255.255.255.0 any
access-list NAT-DATOS-NOC extended permit ip 172.16.1.0 255.255.255.0 any
mtu OUTSIDE 1500
mtu INSIDE 1500
mtu VOZ-NOC 1500
mtu DATOS-NOC 1500
mtu DMZ 1500
mtu management 1500
ip local pool ING_VPN_POOL 172.39.1.1-172.39.1.254 mask 255.255.255.0
no failover
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-621.bin
no asdm history enable
arp timeout 14400
nat-control
global (OUTSIDE) 1 X.X.X.148
global (OUTSIDE) 2 X.X.X.149
global (DATOS-NOC) 2 interface
global (DMZ) 1 interface
nat (VOZ-NOC) 0 access-list VPN_NAT0
nat (VOZ-NOC) 1 192.168.98.0 255.255.255.0
nat (DATOS-NOC) 0 access-list VPN_NAT0
nat (DATOS-NOC) 1 access-list NAT-DATOS-NOC
nat (DATOS-NOC) 1 192.168.99.0 255.255.255.0
nat (DMZ) 0 access-list DMZ-OUT
<--- More --->
nat (DMZ) 2 10.254.254.0 255.255.255.248
static (DMZ,OUTSIDE) X.X.X.150 10.254.254.5 netmask 255.255.255.255
access-group OUT in interface OUTSIDE
access-group IN in interface INSIDE
access-group DMZ-IN in interface DMZ
route OUTSIDE 0.0.0.0 0.0.0.0 X.X.X.145 1
crypto isakmp identity address
crypto isakmp enable OUTSIDE
crypto isakmp policy 10
authentication pre-share
encryption des
hash md5
group 2
lifetime 86400
crypto isakmp policy 20
authentication pre-share
encryption aes-192
hash sha
group 2
lifetime 86400
crypto isakmp policy 21
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime 86400
crypto isakmp policy 65535
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto isakmp nat-traversal 15
telnet timeout 15
console timeout 15
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
group-policy VPN-GCNOC internal
group-policy VPN-GCNOC attributes
vpn-idle-timeout 30
vpn-tunnel-protocol IPSec
split-tunnel-policy tunnelspecified
split-tunnel-network-list value VPN_ING
user-authentication enable
address-pools value ING_VPN_POOL
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect sqlnet
inspect sunrpc
inspect xdmcp
inspect netbios
inspect tftp
inspect
inspect ipsec-pass-thru
inspect http
inspect pptp
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2012 12:13 PM
Hello Adan,
I do no see the nat for the Inside interface on this configuration....
Can you share the following:
packet-tracer input inside udp 192.168.50.149 500 190.106.X.X 500
Regards,
DO rate all the helpful posts
Senior Network Security and Core Specialist
CCIE #42930, 2xCCNP, JNCIP-SEC
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
