- Cisco Community
- Technology and Support
- Security
- Network Security
- ASA 8.4 denying traffic
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2013 07:17 AM - edited 03-11-2019 06:34 PM
I'm having a (fairly common) problem with my ASA in that I cannot get traffit to pass through it. I can't determine the source of this problem and would greatly apprecaite some help getting traffic from my inside network (10.1.2.1, please ignore anything labled 192.168.X.X) to my outside network.
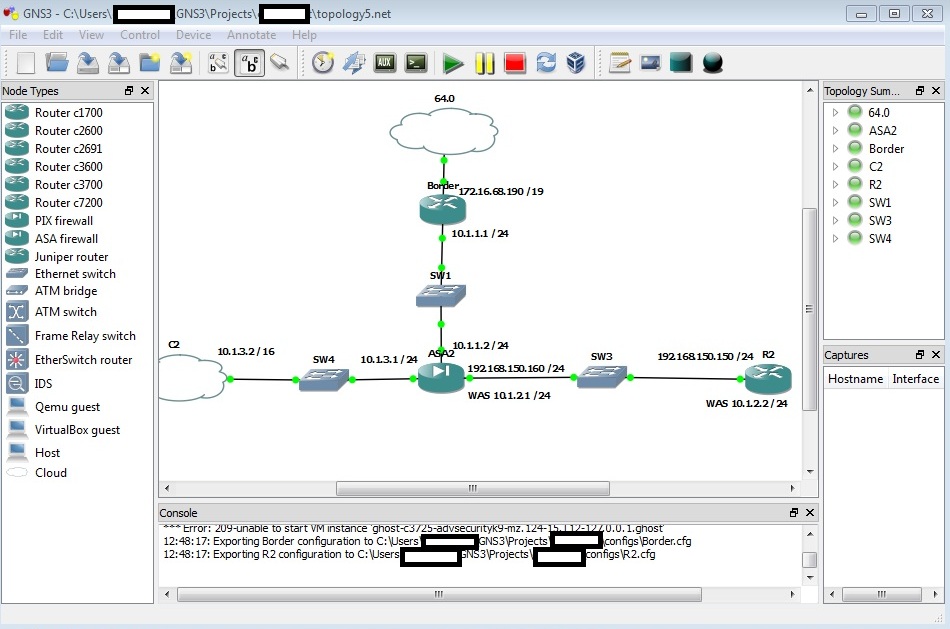
Attached is a screen of my topology. Here's a quick run down of what works:
-The border router can ping the Internet, itself, and the ASA's outside int (10.1.1.2)
-The ASA can ping everything
-An ASDM can connect and can manage the ASA via the 10.1.3.2 management cloud
-The inside router (R2) can ping the inside int of the ASA but not the outside
I've tried in both the CLI and ASDM to:
-Add network objects to prepare configuring NAT (objects required after 8.3 I believe)
-Configure NAT (static)
-Configure ACL's to allow any traffic in any direction (just for these initial testing purposes)
-Allow ICMP inspection (which was weird because my ASA had no global_policy and I had to make one)
The ASDM doesn't show any logging traffic when I try to ping from R2 (192.168.150.150 or old 10.1.2.2) to my Border (either ints, both being inside 10.1.1.1 and outside 172.16.68.190). Again, I can't even ping the outside int of the ASA from R2.
Attached is also my sloppy ASA conf, riddled with all kinds of rules in my attempt to get any traffic passing through. I'd really appreciate any help given.
: Saved
:
ASA Version 8.4(2)
!
hostname ciscoasa
enable password k6tXKjip9Mk3IW7M encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface GigabitEthernet0
nameif outside
security-level 0
ip address 10.1.1.2 255.255.255.0
!
interface GigabitEthernet1
nameif inside
security-level 0
ip address 192.168.150.160 255.255.255.0
!
interface GigabitEthernet2
nameif management
security-level 0
ip address 10.1.3.1 255.255.255.0
!
interface GigabitEthernet3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet5
shutdown
no nameif
no security-level
no ip address
!
ftp mode passive
object network myinside
host 10.1.2.2
description router
object network map_mine
host 192.168.150.150
access-list global_policy extended permit icmp any interface outside
access-list ICMPACL extended permit icmp any any
access-list inside_access_in extended permit ip any any
access-list inside_access_out extended permit ip any any
access-list from_outside extended permit ip any 192.168.150.0 255.255.255.0
pager lines 24
logging enable
logging monitor debugging
logging asdm informational
mtu outside 1500
mtu inside 1500
mtu management 1500
icmp unreachable rate-limit 1 burst-size 1
icmp permit any inside
asdm image disk0:/asdm-647.bin
no asdm history enable
arp timeout 14400
!
object network myinside
nat (any,any) static 10.1.1.3
object network map_mine
nat (inside,outside) static 10.1.1.3 dns
access-group from_outside in interface outside
access-group inside_access_in in interface inside
access-group inside_access_out out interface inside
route outside 0.0.0.0 0.0.0.0 10.1.1.1 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
http server enable
http 10.1.3.2 255.255.255.255 inside
http 10.1.3.2 255.255.255.255 management
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
username cake password xZd2e2HEUR7yWQ2e encrypted privilege 15
!
class-map global-class
match default-inspection-traffic
class-map inspection_default
match default-inspection-traffic
class-map ICMP-CLASS
match access-list ICMPACL
!
!
policy-map global_policy
policy-map global-policy
class global-class
inspect icmp
inspect dns
inspect esmtp
inspect ftp
inspect h323 h225
inspect h323 ras
inspect ip-options
inspect netbios
policy-map gobal_policy
class inspection_default
inspect icmp
inspect icmp error
policy-map ICMP-POLICY
class ICMP-CLASS
inspect icmp
!
service-policy global-policy global
prompt hostname context
no call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http
https://tools.cisco.com/its/service/oddce/services/DDCEServicedestination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
crashinfo save disable
Cryptochecksum:bc22d0ed0e534b08f1f2cc5194e37695
: end
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2013 09:37 AM
Hi,
The most simple NAT configuration you could do for the networks behind the ASA would be
nat (inside,outside) after-auto source dynamic any interface
As long as the "inside" interface "security-level" is higher than the "outside" interfaces, the traffic should go through. Furthermore, having the "inspect icmp" should already allow ICMP Echo Replys through from either side of the firewall. Have you enabled the use of the "global_policy" ?
Naturally you will still need to remember to add default route for the "inside" router pointing towards the ASA "inside" interface IP address and also a default route on the ASA pointing towards the "outside" router interface.
Naturally if you still want to add an ACL then you could add
access-list INSIDE-IN permit ip any any
access-group INSIDE-IN in interface inside
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2013 07:43 AM
Hi,
Some quick comments.
Configure these interfaces "security-level" to "100"
interface GigabitEthernet1
nameif inside
security-level 100
ip address 192.168.150.160 255.255.255.0
!
interface GigabitEthernet2
nameif management
security-level 100
ip address 10.1.3.1 255.255.255.0Then add the following configuration
same-security-traffic permit inter-interface
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2013 07:48 AM
Also,
Notice that you can only ping an ASA interface from behind that interface.
So "inside" can be pinged from behind "inside"
The "outside" can be pinged behind "outside"
BUT you CANT ping "outside" from a host thats behind "inside"
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2013 08:14 AM
I've configured these interfaces as you said to, but I still cannot ping through the firewall. My goal is to allow R2, the "inside" router be able to ping to the outside router "border" to then go out to the internet. Still, with your changes, I cannot ping the Border from R2.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2013 01:38 PM
I guess you could configure a default PAT rule just to be safe
nat (inside,outside) after-auto source dynamic any interface
Also, make sure that the R2 has a default route towards the ASA interface IP address. If there is additional network configured on the R2, make sure that you use the correct IP address as the source for ICMP. Or route the additional networks on the ASA towards the R2 so the routing is fine.
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2013 10:49 AM
Still no changes after doing this.
Can you confirm with me what cmd should be input to R2 to ensure the default route is set correctly for my schema? This is driving me crazy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2013 10:54 AM
Hi,
The R2 should naturally have a default route configure for it to be able to reach every network that is not directly connected to it or is not adverticed to it.
ip route 0.0.0.0 0.0.0.0 192.168.150.160
Would seem to be the correct "ip route" configuration to point the default route from R2 towards the ASA "inside" interface IP address.
You can naturally check the routing table beforehand with the command
show ip route
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2013 07:38 AM
Still nothing. I'm taking the below steps to make this problem as simple as possible.
To avoid any unforseen issues, I created a new topology:
Router 1 ----> ASA ----> Router2
I used the same IP's as in my lab topology:
Router1: f0/0 = 10.1.1.1 /24
ASA: g0 = 10.1.1.2 /24 (outside, security level 0)
g1 = 10.1.2.1 /24 (inside, security level 1)
Router2: f0/0 = 10.1.2.2 /24
I added a class inspection_default and a global_policy policy-map since they didn't previously exist:
policy-map gobal_policy
class inspection_default
inspect icmp
inspect icmp error
[At this point] I still cannot ping from the inside to the outside. I believe I still need the two following things:
1) ACLs
2) NAT definitions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2013 08:57 AM
Any ideas? Even establishing a working ASA in this example scenario would help me out tremendously as I could copy the config over and edit the interface IPs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2013 09:37 AM
Hi,
The most simple NAT configuration you could do for the networks behind the ASA would be
nat (inside,outside) after-auto source dynamic any interface
As long as the "inside" interface "security-level" is higher than the "outside" interfaces, the traffic should go through. Furthermore, having the "inspect icmp" should already allow ICMP Echo Replys through from either side of the firewall. Have you enabled the use of the "global_policy" ?
Naturally you will still need to remember to add default route for the "inside" router pointing towards the ASA "inside" interface IP address and also a default route on the ASA pointing towards the "outside" router interface.
Naturally if you still want to add an ACL then you could add
access-list INSIDE-IN permit ip any any
access-group INSIDE-IN in interface inside
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2013 11:09 AM
Life saver! With your guidance, I was able to create a test topology that allowed inside traffic to my outside interfaces through the ASA. Further, I was able to successfully apply these findings in my lab topology. Here's what I did for my test topology:
-Added an outside router (c2600), an ASA, and an inside router.
-Configured the interfaces exactly as I have them in my original post.
-Configured NAT in the ASA via your mentioned command, "nat (inside,outside) after-auto source dynamic any interface
".
-Configured and enabled a global_policy for traffic inspection:
"class-map inspection_default
match default-inspection-traffic
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect icmp
inspect icmp error
service-policy global_policy global"
-Added the default-network in the inside router: "ip default-network 10.1.2.1"
That's it! I was able to ping from the inside interfaces right through the ASA to the inside interfaces of outward facing devices. Since my ASA's previous config was so sloppy in my lab topology, I wound up deleting the ASA all together and reconfiguring it from scratch (along with the inside router just to be safe). Unfortunately, I didn't forsee me losing my ASDM image, so am currently recopying it from my tftp server to reconfigure connectivity from my management cloud to the ASA.
Thanks for the help! Hopefully this thread will help others (and possibly myself again) in the future.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


