- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: ASA- access-list issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA- access-list issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2019 03:07 AM
Hi,
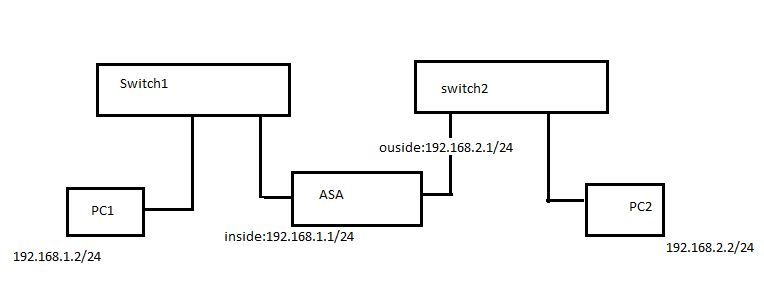
I have created a topology as shown in above diagram in vsphere client.Now i would like to ping from PC1 to PC2 and vice versa. But i could not able to ping.Below are the configurations that i have used for the setup.
PC1 configs:
IP : 192.168.1.2/24 ; default gateway : 192.168.1.1;
PC2 configs: 192.168.2.2/24; default gateway : 192.168.2.1;
ASA configs :
interface GigabitEthernet0/0
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface GigabitEthernet0/1
nameif outside
security-level 0
ip address 192.168.2.1 255.255.255.0
ciscoasa(config)# sh running-config access-list
access-list list1 extended permit icmp 192.168.1.0 255.255.255.0 192.168.2.0 255.255.255.0
ciscoasa(config)# sh running-config access-group
access-group list1 in interface inside
Please help me to sort out the issue.
Thanks in advance.
- Labels:
-
Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2019 03:29 AM
Hi there,
Have you enabled ICMP inspection? Assuming you are using the default inspection policy:
!
policy-map global_policy
class inspection_default
inspect icmp
!
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2019 03:54 AM
You do not require that ACL applied to the inside interface, the reason is it's a higher security level, so inherently it has access to the outside interface.
Conversely, the outside interface does not have any access to the inside, unless traffic is explicitly permitted.
Essentially, for PC2 to reach PC1, you would need to do the same.
In addition you would need inspect icmp, as stated.
Finally, you need to ensure the client firewalls (i.e. Windows Firewall) is configured to permit ICMP (which it does not, by default).
Martin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2019 04:40 AM
Thanks for your response.
After enabling the icmp inspection now both sides able to ping.
but i couldn't understand what is the functionality of icmp inspection.
And i also i like to inform that inside interface is not able to access the outside interface without ACL.
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2019 05:35 AM
You shouldn't need an ACL ( furthermore, it's not recommended)
As to the question, it's because ICMP is not stateful and does not contain sequence, port numbers etc.
'Inspect ICMP' creates a DACL, so that echo-reply's etc are permitted if the traffic originated from the inside interface.
Martin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2019 06:00 AM
Hi there,
What @Martin Carr mentions about why the inspection is required is correct.
Regarding the need for the ACL...
Unless a permit statement is placed at the end of an ACL it has an implicit deny. In the case of your ACL, since it is INbound on the inside interface without that particular ACE the ICMP traffic will be denied. It is worth remembering that on an ASA in the absence of ACLs traffic is always permitted from a higher security level to a lower one, therefore this particular ACL is not required and the inspect statement will ensure that the return traffic is permitted without the need of further ACLs.
Hope that makes sense, and don't forget to mark correct/ helpful posts ;)
cheers,
Seb.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
