- Cisco Community
- Technology and Support
- Security
- Network Security
- ASA5525 multi-mode site to site vpn problem
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2017 03:25 AM - edited 03-12-2019 01:58 AM
I don't have a ton of experience with ASA firewalls, but I've searched everywhere and I can't seem to find a solution to this.
The topology is as follows
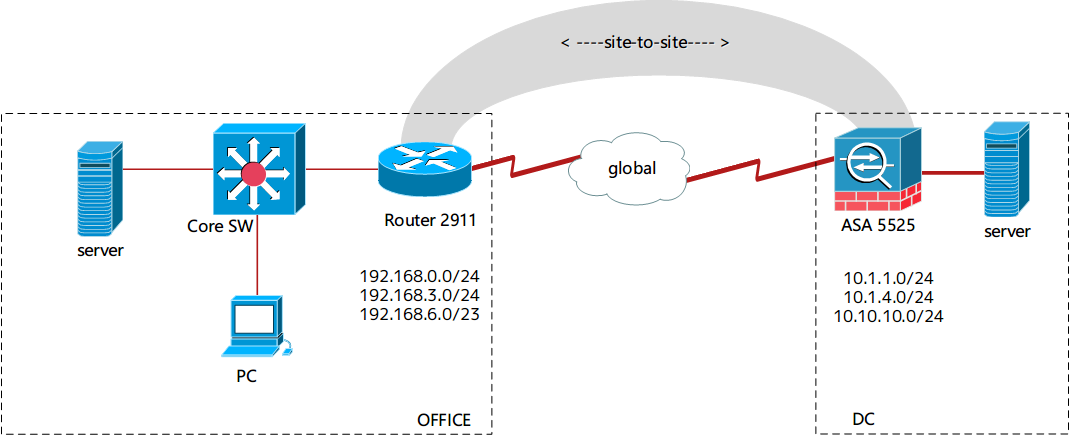
I have 2 sites connected by a Site-to-Site VPN with ASA and Router.The ASA at DC is work on multi-mode.
OFFICE: VLAN1 192.168.0.0
vlan 2 192.168.3.0
vlan 3 192.168.6.0
DC :inside 10.1.1.0
inside14 10.1.4.0
inside10 10.10.10.0
Traffic from all vlans of OFFICE to inside(10.1.1.0) in DC is perfect across the VPN. All 192.168.* can ping 10.1.1.*
but other interface in DC like inside10 and inside 14 can't be ping and vice-versa.
Then i do 'show crypto isakmp sa ' 'show crypto ipsec sa' on ASA and 2911.
the isakmp sa is all right.
on ASA I found that the ipsec sa about peer 10.10.10.0 / 192.168.3.0 is wrong .
it just has 'pkts decaps' count ,the 'pkts encrypt' number is 0

on Router 2911 ,the situation is just the opposite
'pkts decaps' number is 0 ,the 'pkts encrypt' number is 174

I think the correct ipsec sa should be like the follow:

How can i solve this problem?
ASA and router configurtion is below
ASA - system configurtion:
fw1# sh run
: Saved
:
: Serial Number: F*******
: Hardware: ASA5525, 8192 MB RAM, CPU Lynnfield 2394 MHz, 1 CPU (4 cores)
:
ASA Version 9.4(2)6 <system>
!
hostname bj-shidc-fw1
!
interface GigabitEthernet0/0
!
interface GigabitEthernet0/1
!
interface GigabitEthernet0/2
!
interface GigabitEthernet0/3
!
interface GigabitEthernet0/4
!
interface GigabitEthernet0/4.10
vlan 10
!
interface GigabitEthernet0/4.14
vlan 14
!
interface GigabitEthernet0/5
description LAN/STATE Failover Interface
!
interface GigabitEthernet0/6
shutdown
!
interface GigabitEthernet0/7
!
interface Management0/0
!
!
class default
limit-resource All 0
limit-resource Mac-addresses 16384
limit-resource ASDM 5
limit-resource SSH 5
limit-resource Telnet 5
!
class ctx1
limit-resource VPN Burst Other 100
limit-resource VPN Other 750
limit-resource VPN IKEv1 in-negotiation 100.0%
limit-resource SSH 5.0%
limit-resource ASDM 15.0%
!
boot system disk0:/asa942-6-smp-k8.bin
(****)
asdm image disk0:/asdm-752-153.bin
asdm history enable
(****)
admin-context admin
context admin
(******)
config-url disk0:/admin.cfg
!
context c2
member ctx1
allocate-interface GigabitEthernet0/1
allocate-interface GigabitEthernet0/4
allocate-interface GigabitEthernet0/4.10
allocate-interface GigabitEthernet0/4.14
config-url disk0:/c2.cfg
join-failover-group 2
!
ASA -Context configurtion:
fw1/c2# sh run
: Saved
:
: Hardware: ASA5525
:
ASA Version 9.4(2)6 <context>
!
interface GigabitEthernet0/1
nameif outside
security-level 0
ip address [ DC-IP] 255.255.255.224 standby [DC-IP2]
!
interface GigabitEthernet0/4
nameif inside
security-level 100
ip address 10.1.1.1 255.255.255.0 standby 10.1.1.9
!
interface GigabitEthernet0/4.10
nameif inside10
security-level 100
ip address 10.10.10.1 255.255.255.0 standby 10.10.10.9
!
interface GigabitEthernet0/4.14
nameif inside14
security-level 100
ip address 10.1.4.1 255.255.255.0 standby 10.1.4.9
!
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network my-inside-net
subnet 10.1.1.0 255.255.255.0
object network inside10
subnet 10.10.10.0 255.255.255.0
object network inside14-net
subnet 10.1.4.0 255.255.255.0
object network inside10-net
subnet 10.10.10.0 255.255.255.0
object-group network vpn
network-object 192.168.0.0 255.255.255.0
network-object 192.168.3.0 255.255.255.0
network-object 192.168.6.0 255.255.254.0
access-list in-nat-out extended permit icmp any any
access-list idc-bjzb extended permit ip 10.1.1.0 255.255.255.0 192.168.0.0 255.255.255.0
access-list idc-bjzb extended permit ip 10.1.1.0 255.255.255.0 192.168.3.0 255.255.255.0
access-list idc-bjzb extended permit ip 10.1.1.0 255.255.255.0 192.168.6.0 255.255.254.0
access-list idc-bjzb extended permit ip 10.1.4.0 255.255.255.0 192.168.3.0 255.255.255.0
access-list idc-bjzb extended permit ip 10.1.4.0 255.255.255.0 192.168.6.0 255.255.254.0
access-list idc-bjzb extended permit ip 10.10.10.0 255.255.255.0 192.168.0.0 255.255.255.0
access-list idc-bjzb extended permit ip 10.10.10.0 255.255.255.0 192.168.3.0 255.255.255.0
access-list idc-bjzb extended permit ip 10.10.10.0 255.255.255.0 192.168.6.0 255.255.254.0
nat (inside,outside) source static any any destination static vpn vpn
nat (inside14,outside) source static any any destination static vpn vpn
nat (inside10,outside) source static inside10 inside10 destination static vpn vpn
!
object network my-inside-net
nat (inside,outside) dynamic interface
object network inside14-net
nat (inside14,outside) dynamic interface
object network inside10-net
nat (inside10,outside) dynamic interface
access-group in-nat-out in interface outside
route outside 0.0.0.0 0.0.0.0 ****** 1
(****)
crypto ipsec ikev1 transform-set VPNset esp-3des esp-md5-hmac
crypto ipsec security-association pmtu-aging infinite
crypto map VPNmap 1 match address idc-bjzb
crypto map VPNmap 1 set peer [OFFICE-IP ]
crypto map VPNmap 1 set ikev1 transform-set VPNset
crypto map VPNmap interface outside
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
(*****)
tunnel-group [OFFICE-IP ] type ipsec-l2l
tunnel-group [OFFICE-IP ] ipsec-attributes
ikev1 pre-shared-key *****
Router 2911 configurtion:
r01#sh run
Building configuration...
Current configuration : 7304 bytes
version 15.2
service timestamps debug datetime msec
service timestamps log datetime localtime show-timezone
service password-encryption
!
hostname r01
aaa new-model
!
aaa authentication login default local
!
!
!
aaa session-id common
ip cef
!
!
!
no ip domain lookup
no ipv6 cef
!
!
!
ip ssh authentication-retries 4
!
!
crypto isakmp policy 10
encr 3des
authentication pre-share
group 2
crypto isakmp key VPNkey address [DC-IP]
!
!
crypto ipsec transform-set VPNset esp-3des esp-md5-hmac
mode tunnel
!
!
!
!
!
crypto map VPNmap 10 ipsec-isakmp
set peer [DC-IP]
set transform-set VPNset
match address office-dc
!
!
!
!
!
interface Embedded-Service-Engine0/0
no ip address
shutdown
!
interface GigabitEthernet0/0
description telcom
ip address [OFFICE-IP] 255.255.255.240
ip nat outside
ip virtual-reassembly in
duplex auto
speed auto
crypto map VPNmap
!
interface GigabitEthernet0/1
no ip address
shutdown
duplex auto
speed auto
!
interface GigabitEthernet0/2
ip address 172.16.1.2 255.255.255.0
ip nat inside
ip virtual-reassembly in
duplex auto
speed auto
!
ip nat inside source list nat interface GigabitEthernet0/0 overload
ip route 0.0.0.0 0.0.0.0 [sp-gw]
ip access-list extended office-dc
permit ip 192.168.0.0 0.0.0.255 10.1.1.0 0.0.0.255
permit ip 192.168.3.0 0.0.0.255 10.1.1.0 0.0.0.255
permit ip 192.168.6.0 0.0.1.255 10.1.1.0 0.0.0.255
permit ip 192.168.3.0 0.0.0.255 10.10.10.0 0.0.0.255
permit ip 192.168.0.0 0.0.0.255 10.10.10.0 0.0.0.255
permit ip 192.168.6.0 0.0.1.255 10.10.10.0 0.0.0.255
permit ip 192.168.3.0 0.0.0.255 10.1.4.0 0.0.0.255
permit ip 192.168.6.0 0.0.1.255 10.1.4.0 0.0.0.255
permit ip 192.168.0.0 0.0.0.255 10.1.4.0 0.0.0.255
ip access-list extended nat
deny ip 192.168.0.0 0.0.7.255 10.1.1.0 0.0.0.255
deny ip 192.168.0.0 0.0.7.255 10.1.4.0 0.0.0.255
deny ip 192.168.0.0 0.0.7.255 10.10.10.0 0.0.0.255
permit ip any any
!
!
!
end
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2017 03:52 AM
This looks like the ASA is not encrypting return traffic from the router. A few things to look at:
1) Add the "route-lookup" keyword on all your VPN identity NAT statements
2) Why do you have config on your physical G0/4 interface? Ideally, you should split the G0/4 into G0/4.1,4.10 and 4.14.I have a feeling that the port is being used as an access port and only the G0/4 interface works. Change your config to have all 3 networks under sub-interfaces.
Refer to this article for reference:
http://www.petenetlive.com/KB/Article/0001085
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2017 03:52 AM
This looks like the ASA is not encrypting return traffic from the router. A few things to look at:
1) Add the "route-lookup" keyword on all your VPN identity NAT statements
2) Why do you have config on your physical G0/4 interface? Ideally, you should split the G0/4 into G0/4.1,4.10 and 4.14.I have a feeling that the port is being used as an access port and only the G0/4 interface works. Change your config to have all 3 networks under sub-interfaces.
Refer to this article for reference:
http://www.petenetlive.com/KB/Article/0001085
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2017 07:45 PM
thank you for reply
1. i will try it in one day night.
2. a cisco 2960 switch is under g0/4. the up link interface works in trunk mode.
Servers in vlan 10 and 14 works fine.
I suspect that the mulit-mode ASA blocked packets, because some time ago when the asa wokes in single-mode, the ipsec vpn with the same configurtion is well.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


