- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Ask the expert- Best practices on Cisco FirePOWER
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Ask the expert- Best practices on Cisco FirePOWER
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2018 05:10 PM - edited 02-21-2020 07:30 AM

This topic is a chance to discuss more about all you need to know about Cisco FirePOWER security solution. On this session, Marvin Rhoads will be answering all kind of questions about FirePOWER Management Center (FMC), FirePOWER Threat Defense (FTD) and FirePOWER service modules to FirePOWER appliances. All kind of topics related to this solution, such as operation, configuration, design architecture, troubleshooting, installation and licensing will be covered.
Centralize, integrate, and simplify security management on your network
To participate in this event, please use the ![]() button below to ask your questions
button below to ask your questions
Ask questions from Monday, March 19th to Friday 30th 2018
Featured Expert

Marvin is passionate about helping and learning from his peers in the industry. He has been an active Cisco Support Community contributor since 2001. He has been named as a Cisco Designated VIP for 6 years in a row. In 2017 he was recognized as a member of the elite Cisco Support Community Hall of Fame program.
Marvin might not be able to answer each question due to the volume expected during this event. Remember that you can continue the conversation at the Security Category.
Find other events or open new discussions https://supportforums.cisco.com/t5/community-ideas/bd-p/5911-discussions-community-ideas
**Ratings Encourage Participation! **
Please be sure to rate the Answers to Questions
- architecture
- ask the expert
- best practices
- cisco
- Cisco Designated VIP
- cisco Firepower
- Cisco Support Community
- configuration
- deployment
- design
- firepower
- firewalling
- fmc
- forum
- FTD
- Hall of Fame
- installation
- intrusion prevention
- ise
- licensing
- marvin rhoads
- ngfw
- NGIPS
- operations
- security
- threat defense
- top Contributor
- troubleshooting
- vip
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2018 01:03 AM
Can you clarify your requirements a bit? Are you looking to use the devices for instructional purposes or operationally?
What exactly did you purchase (exact SKUs and licenses)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2018 03:28 PM
We are an educational institution teaching CCNA security with Cisco certified instructors.
We recently purchased three ASA 5506X.
My question was do I need to register them (to access Firepower) if they are only to be used in isolated labs within the institution.
If they are to be registered how do I do that so that different classes, across the years that we will be using the devices
can gain access to Firepower.
Currently we have
3 cisco 5506x each with a control licence PAK
Thanks Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2018 04:47 AM
The Firepower module on an ASA 55000 series requires a license be assigned to it. At a minimum you need the Control license (free) which you already have.
For it to be fully useful and illustrate all of the available features you would add the IPS subscription, URL Filtering and Malware licenses.
You can use either a local manager (ASDM running on a PC or Mac) or remote manager (Firepower Management Center or FMC server) to assign licenses to the systems.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2018 07:43 PM
Marvin,
Can FTD make internal to external route decisions based on Layer 4 - 7 critera? If so, can you direct me to a configuration good example online? An example of this would be a customer directing business related internet out their 100Mbps ISP, and social media traffic out their lower cost ISP or backup ISP, or SIP traffic out a dedicated ISP and all other traffic out another.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2018 08:11 PM
That's not possible as far as I know.
Routing decisions are based solely on classic routing criteria (IP address, best match based on prefix length, administrative distance etc.) and not on any of the L4-7 criteria that we have available in Access Control Policies.
What's available is described in the configuration guide here:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2018 09:38 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2018 09:00 PM
Good morning Marvin
I have a question regarding FTD devices and crypto mining. What is the recommended method of stopping applications on the internal network that may communicate with mining pools?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2018 01:20 AM
Cisco's security intelligence organization Talos has a pretty comprehensive article here:
http://blog.talosintelligence.com/2018/01/malicious-xmr-mining.html
They note the following:
COVERAGE
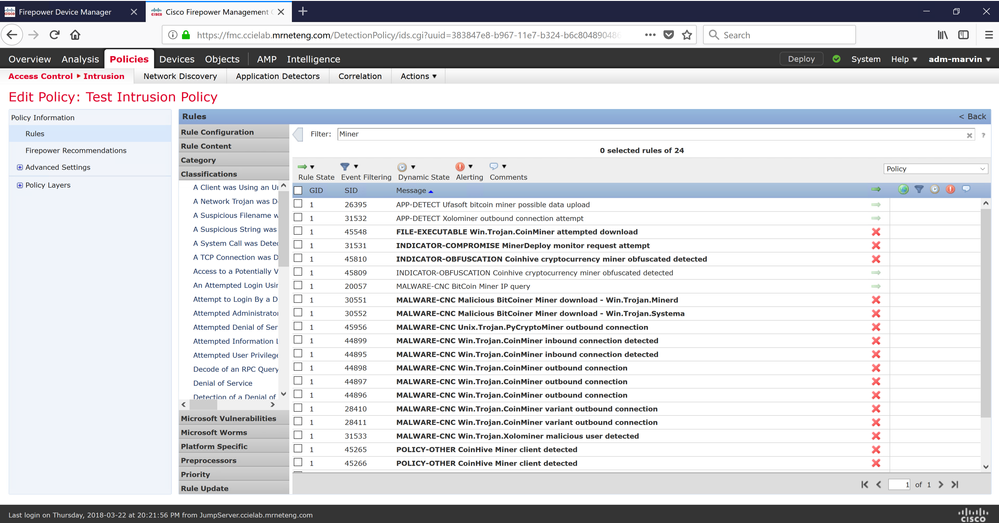
There are different ways to address miners and there is detection built in to Cisco security products to detect this activity. There is a specific detection name in AMP for coin miners, W32.BitCoinMiner. However, as these miners can be added as modules to various other threats, the detection names may vary. Additionally there are a couple NGIPS signatures designed to detect mining activity as well. However, these rules may not be enabled by default in your environment depending on the importance of potentially unwanted applications (PUA) in your network. The signatures that detect this type of activity includes, but isn't limited to: 40841-40842, 45417, and 45548-45550.
Also, technologies like Threat Grid have created indicators to clearly identify when mining activity is present when a sample is submitted.
Most of the common miner apps and related indicators will be blocked by a default Intrusion Policy
If you look at your FMC, you can see the signatures they reference (and enable them if you wish) in your intrusion policy as follows (example subset only, a few more searches would be necessary to display them all as the search terms must be distinct since they are Boolean ANDed if you use multiple terms):
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2018 06:32 AM
I have setup dynamic feed lists for O365 and other Microsoft Services via these instructions:
https://www.staffeldt.net/cisco-fmc-intelligence-feeds-and-objects/
Using Minemeld I have pulled an generated the two lists needed to whitelist all of the Microsoft IP's and URL's.
However, the URL list that is generated by these feeds includes wildcards in the url list. eg:
*.office.com *.office365.com account.office.net api.office.com appsforoffice.microsoft.com
Are these wildcards supported in a network feed?
Thanks,
Dan.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2018 07:30 AM
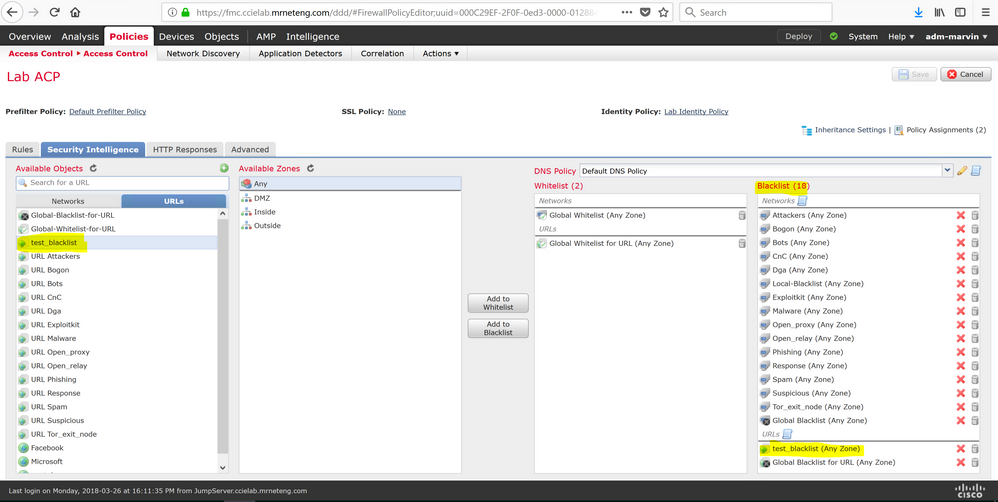
Yes, your whitelist can include wildcard URL objects.
In a DNS list entry, you can specify an asterisk (*) wildcard character for a domain label. All labels match the wildcard. For example, an entry of www.example.* matches both www.example.com and www.example.co.
Source:
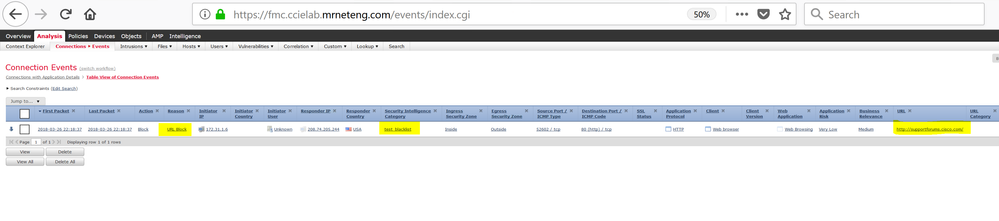
I tested it using the local blacklist feature (easier to test) and it works.
First under Objects > Object Management > Security Intelligence > URL Lists and Feeds add the text file you created. I named mine "test_blacklist".
Then make sure you have it referenced in your active access control policy under the Security Intelligence tab. (Mine is a blacklist, obviously yours would be under whitelist)
Finally deploy your policy. You should then see the hits (assuming you are logging connection events) in your event viewer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2018 07:52 AM
Hi Marvin,
I know you could write a book about best practices for installing and operating Firepower, but do you have a checklist of sorts that you could share that would identify the top things to ensure are set correctly (i.e. - modify default discovery process, logging at the end instead of beginning, etc.) ?
Thanks,
Jeff
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2018 08:23 AM
Actually a book has been written just recently by an author more qualified than me. Please refer to Nazmul Rajib's "Cisco Firepower Threat Defense". It's published by Cisco Press and available via the usual channels. He includes several best practices.
There are also several good Cisco Live presentations.
Personally I use a combination of those plus some training guides that I'm unfortunately not at liberty to share as they contain copyrighted and/or NDA-protected material .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2018 11:16 AM
Hi Marvin,
Can we block mobile devices accessing anyconnect vpn in FTD firewall, we dont have ISE, we are looking this option in firewall if this is possible ? and also if you can share one example of FTD anyconnect vpn with certificate authentication ?
Thanks
Basavaraj
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2018 11:19 AM
Hi Marvin,
Can you please explain the architecture of IPS snort rules and how can we edit existing snort rule or if i want to create custom snort is it possible ?
Thanks
Basavaraj
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2018 07:55 PM
Snort rules are a very deep subject. I'd recommend you start with something like one of the excellent Cisco Live presentations to get started. For example, BRKSEC-3300, which you can find here:
As noted there (specifically see slide 35 onwards), Firepower Intrusion rules are Snort rules. You can enable or disable specific ones or create / import your own if the ones provided don't meet all of your needs.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide