- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Block DNS over HTTPS requests in Firepower
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2021 08:11 AM
Hi,
We have a number of 5506-X devices licensed for URL, IPS, and Malware filtering on the Firepower Module. These are installed in an education setting and therefore it is critical that certain content is blocked for the children using the network. We have discovered today that a certain user has been able to access pornographic thumbnail images from google searches due to the fact that Google Chrome is set to use Secure DNS (DNS over HTTPS) on their device on a public/BYOD network.
What is the best way to prevent users from attempting to use DNS over HTTPS on the Firepower module, and enforce standard DNS requests? We are using ADSM on this device and have no FMC.
Any ideas or suggestions would be gratefully received.
Thanks,
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2021 07:50 AM - edited 05-03-2021 07:50 AM
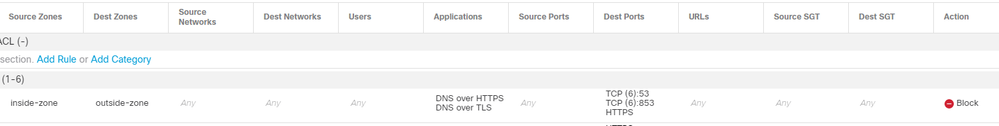
You could try blocking the Application "DNS over HTTPs" or "DNS over TLS".
Worked in my lab just fine, this is FTD 6.7.0.1 managed by FMC though.
BR
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2021 07:50 AM - edited 05-03-2021 07:50 AM
You could try blocking the Application "DNS over HTTPs" or "DNS over TLS".
Worked in my lab just fine, this is FTD 6.7.0.1 managed by FMC though.
BR
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2021 11:14 PM
Thanks for the response Rick. I actually found this option when looking at this last week but forgot to update the thread.
To confirm this can blocked using an application rule in ASDM.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2021 09:32 AM
What @rschlayer said - that's the best option you have with the setup you've described. The application blocking settings should be available in the Firepower configuration section of ASDM.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide