- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Cannot ping across Cisco Firewall 2110
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2023 11:35 AM
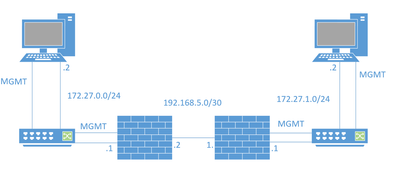
I have a bit of a unique situation which I am struggling with. The topology is a bit weird so let me explain the end goal. We want to physically separate the two sides of this network into two autonomous networks with each side having their own firewall to control what traffic enters their side. Here is part of the set up:
The issue is that I cannot ping the PC on the right from the PC on the left. I can ping the default gateway of 172.27.0.1, but I cannot ping the p2p interface of 192.168.5.2. On the actual firewall, I can ping the PC at 172.27.0.2 and the outside interface of the other firewall at 192.168.5.1, but I cannot ping the inside interface of the other firewall at 172.27.1.1 or the PC at 172.27.1.2. I haven't done much for the actual configuration of the firewalls, just added a generic allow all policy and messed around with the routes but I haven't had any success.
The firewalls are Cisco Firepower 2110 and I'm managing them locally using FDM. The switches are both Catalyst 9200's and the end points are just generic windows. I'm not too familiar with this stuff so any help is appreciated.
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2023 02:09 PM - edited 03-27-2023 02:09 PM
@donovanrodriguez9726 there's no point testing traffic on a directly connected interface. Run packet tracer from source IP of pc1 to pc2 ip.
Repeat the packet tracer test from both firewalls.
Also don't test from the firewalls ip address, generate traffic through the firewall, not to/from.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2023 11:45 AM
@donovanrodriguez9726 you can only ping the firewall interface closest to you. You cannot ping through the firewall to one of the firewall's far interfaces, that's by design.
If you cannot ping the PC at 172.27.1.2, you have confirmed the PC has the correct routing?
Do you have NAT configured?
Run packet-tracer from the CLI of the firewalls to confirm connectivity to the PC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2023 12:30 PM
No NAT running, we are purely using the firewalls for acl purposes essentially. What do you mean by correct routing exactly? I'm able to ping from 172.27.0.2 to 172.27.0.1 should I have routing from 172.27.0.1 -> 172.27.1.2?
I'm trying to figure out the packet-tracer deal, standby. Thanks for reaching out though.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2023 12:47 PM
@donovanrodriguez9726 yes you will need full routing. The Pc should have the local FW ip address as the default gateway and the FWs should have a route to the remote network, or a default route via the other FW.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2023 01:17 PM
Would this route work?
Name Interface Network Gateway
DefaultRoute Inside (172.27.0.1) 172.27.1.0/24 192.168.5.2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2023 01:18 PM
I'm more used to standard router routes, ip route 172.27.1.0 255.255.255.0 next-hop-ip
Not sure how the security routes work
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2023 01:23 PM
@donovanrodriguez9726 it's the same logic on the firewall.
Define the destination network/mask and the next hop ip address.
You'll need to define routes on both FWs and obviously both PCs will need the default gateway as the FW inside interface IP address.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2023 02:03 PM
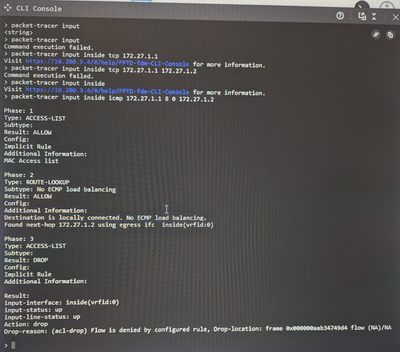
So I did verify connectivity from the PC's to the DGs. I then went and ran the packet-tracer it seems that something is blocking the ICMP traffic.
I only have one access policy, see below:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2023 02:09 PM - edited 03-27-2023 02:09 PM
@donovanrodriguez9726 there's no point testing traffic on a directly connected interface. Run packet tracer from source IP of pc1 to pc2 ip.
Repeat the packet tracer test from both firewalls.
Also don't test from the firewalls ip address, generate traffic through the firewall, not to/from.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2023 02:41 PM
I was finally able to figure it out. Packet tracer was a huge help. For the static route I needed to have the interface as the outside interface instead of the inside one.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2023 12:24 PM
This VPN and you want to mgmt the FW through tunnel?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2023 12:31 PM
Not using an VPN's or any sort of NATing.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide