- Cisco Community
- Technology and Support
- Security
- Network Security
- Connecting Grandstream IP Phones to Cisco Ise
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Connecting Grandstream IP Phones to Cisco Ise
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2020 03:12 AM - edited 10-08-2020 03:17 AM
Hello,
Im trying to add grandstream IP phones to Cisco ISE, IT i as authenticating and i am even receiving an IP address but i can not make calls. Please help me.
Overview
Event 5200 Authentication succeeded
Username C0:74:AD:17:59:6B
Endpoint Id C0:74:AD:17:59:6B
Endpoint Profile Unknown
Authentication Policy Wired >> MAB
Authorization Policy Wired >> Employees
Authorization Result PermitAccess,Employee,IPPhones,Employees
Authentication Details
Source Timestamp 2020-10-08 09:14:19.605
Received Timestamp 2020-10-08 09:14:19.605
Policy Server ISE-PAN
Event 5200 Authentication succeeded
Username C0:74:AD:17:59:6B
User Type Host
Endpoint Id C0:74:AD:17:59:6B
Calling Station Id C0-74-AD-17-59-6B
Endpoint Profile Unknown
IPv4 Address 192.168.0.160
Authentication Identity Store Internal Endpoints
Identity Group Grandstream_IP_Phones
Audit Session Id 0AC8D064000000360DD05C21
Authentication Method mab
Authentication Protocol Lookup
Service Type Call Check
Network Device Test
Device Type All Device Types#Wired
Location All Locations#=HQ
NAS IPv4 Address 10.200.208.100
NAS Port Id GigabitEthernet1/0/10
NAS Port Type Ethernet
Authorization Profile PermitAccess,Employee,IPPhones,Employees
Security Group Employees
Response Time 101 milliseconds
Other Attributes
ConfigVersionId 112
DestinationPort 1812
Protocol Radius
NAS-Port 50110
Framed-MTU 1500
OriginalUserName c074ad17596b
NetworkDeviceProfileId b0699505-3150-4215-a80e-6753d45bf56c
IsThirdPartyDeviceFlow false
AcsSessionID ISE-PAN/391434383/9120
UseCase Host Lookup
SelectedAuthenticationIdentityStores AD
SelectedAuthenticationIdentityStores Internal Users
SelectedAuthenticationIdentityStores Internal Endpoints
AuthenticationStatus AuthenticationPassed
IdentityPolicyMatchedRule MAB
AuthorizationPolicyMatchedRule Employees
EndPointMACAddress C0-74-AD-17-59-6B
ISEPolicySetName Wired
IdentitySelectionMatchedRule MAB
IsMachineIdentity false
DTLSSupport Unknown
HostIdentityGroup Endpoint Identity Groups:Grandstream_IP_Phones
Network Device Profile Cisco
Location Location#All Locations#HQ
Device Type Device Type#All Device Types#Wired
IPSEC IPSEC#Is IPSEC Device#No
RADIUS Username C0:74:AD:17:59:6B
Device IP Address 10.200.208.100
CPMSessionID 0AC8D064000000360DD05C21
Called-Station-ID 3C:41:0E:F2:25:0A
CiscoAVPair service-type=Call Check,
audit-session-id=0AC8D064000000360DD05C21,
method=mab
Result
UserName C0:74:AD:17:59:6B
User-Name C0-74-AD-17-59-6B
Class CACS:0AC8D064000000360DD05C21:TCRA-ISE-PAN/391434383/9120
Tunnel-Type (tag=0) VLAN
Tunnel-Medium-Type (tag=0) 802
Tunnel-Private-Group-ID (tag=0) 301
cisco-av-pair ACS:CiscoSecure-Defined-ACL=#ACSACL#-IP--Employee-5f6da441
cisco-av-pair device-traffic-class=voice
cisco-av-pair cts:security-group-tag=0004-00
cisco-av-pair profile-name=Unknown
LicenseTypes Base license consumed
Steps
11001 Received RADIUS Access-Request
11017 RADIUS created a new session
11027 Detected Host Lookup UseCase (Service-Type = Call Check (10))
15049 Evaluating Policy Group
15008 Evaluating Service Selection Policy
15048 Queried PIP - Normalised Radius.RadiusFlowType
15048 Queried PIP - DEVICE.Device Type
15041 Evaluating Identity Policy
15048 Queried PIP - Network Access.EapAuthentication
22072 Selected identity source sequence - Basic_Internal
15013 Selected Identity Source -AD
24432 Looking up user in Active Directory - -AD
24325 Resolving identity - C0-74-AD-17-59-6B
24313 Search for matching accounts at join point - *****.go.tz
24318 No matching account found in forest - *****.go.tz
24322 Identity resolution detected no matching account
24352 Identity resolution failed - ERROR_NO_SUCH_USER
24412 User not found in Active Directory - -AD
15013 Selected Identity Source - Internal Users
24210 Looking up User in Internal Users IDStore - C0:74:AD:17:59:6B
24216 The user is not found in the internal users identity store
15013 Selected Identity Source - Internal Endpoints
24209 Looking up Endpoint in Internal Endpoints IDStore - C0:74:AD:17:59:6B
24211 Found Endpoint in Internal Endpoints IDStore
22037 Authentication Passed
24715 ISE has not confirmed locally previous successful machine authentication for user in Active Directory
15036 Evaluating Authorization Policy
15016 Selected Authorization Profile - PermitAccess,Employee,IPPhones,Employees
15016 Selected Authorization Profile - PermitAccess,Employee,IPPhones,Employees
11022 Added the dACL specified in the Authorization Profile
15016 Selected Authorization Profile - PermitAccess,Employee,IPPhones,Employees
15016 Selected Authorization Profile - PermitAccess,Employee,IPPhones,Employees
24209 Looking up Endpoint in Internal Endpoints IDStore - C0:74:AD:17:59:6B
24211 Found Endpoint in Internal Endpoints IDStore
11002 Returned RADIUS Access-Accept
- Labels:
-
Other Network Security Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2020 03:27 AM
You are applying a DACL to the session, I don't know what is permitted/denied as you've not provided that information. Remove it, test again and see if that resolves the issue.
You have also applied an SGT of "Employees" to the session, if you aren't using TrustSec then remove it.
Have you authorised the phone into the correct Voice VLAN?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2020 03:36 AM
hello Rob,
My voice vlan is 301
This is my Dacl
permit tcp any any eq 9100
permit udp any any eq 68
deny ip any any
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2020 03:43 AM - edited 10-08-2020 03:52 AM
Ok, but did you test without the DACL applied?
Have you confirmed what ports are required for the IP phone to operate correctly? udp/68 is DHCP and tcp/9100 is used for printing and you are denying all remaining traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2020 03:53 AM
Yes i removed the DACL and still bringing up the same thing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2020 04:05 AM
Its not even hitting the last authorization policy set
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2020 04:09 AM
this is what im getting now after removing the vlan tag and vlan from the authorization profile
There have been 1 repeated authentications with the same authentication result.
The authentication details of the first passed attempt is shown here.
Overview
Event 5200 Authentication succeeded
Username C0:74:AD:17:59:6B
Endpoint Id C0:74:AD:17:59:6B
Endpoint Profile Unknown
Authentication Policy Wired >> MAB
Authorization Policy Wired >> Employees
Authorization Result PermitAccess,Employee,IPPhones,Employees
Authentication Details
Source Timestamp 2020-10-08 10:51:16.266
Received Timestamp 2020-10-08 10:51:16.266
Policy Server ISE-PAN
Event 5200 Authentication succeeded
Username C0:74:AD:17:59:6B
User Type Host
Endpoint Id C0:74:AD:17:59:6B
Calling Station Id C0-74-AD-17-59-6B
Endpoint Profile Unknown
IPv4 Address 192.168.0.160
Authentication Identity Store Internal Endpoints
Identity Group Grandstream_IP_Phones
Audit Session Id 0AC8D0640000003C0E291D49
Authentication Method mab
Authentication Protocol Lookup
Service Type Call Check
Network Device Test
Device Type All Device Types#Wired
Location All Locations#HQ
NAS IPv4 Address 10.200.208.100
NAS Port Id GigabitEthernet1/0/10
NAS Port Type Ethernet
Authorization Profile PermitAccess,Employee,IPPhones,Employees
Security Group Employees
Response Time 38 milliseconds
Other Attributes
ConfigVersionId 113
DestinationPort 1812
Protocol Radius
NAS-Port 50110
Framed-MTU 1500
OriginalUserName c074ad17596b
NetworkDeviceProfileId b0699505-3150-4215-a80e-6753d45bf56c
IsThirdPartyDeviceFlow false
AcsSessionID -ISE-PAN/391434383/9726
UseCase Host Lookup
SelectedAuthenticationIdentityStores AD
SelectedAuthenticationIdentityStores Internal Users
SelectedAuthenticationIdentityStores Internal Endpoints
AuthenticationStatus AuthenticationPassed
IdentityPolicyMatchedRule MAB
AuthorizationPolicyMatchedRule _Employees
EndPointMACAddress C0-74-AD-17-59-6B
ISEPolicySetName Wired
IdentitySelectionMatchedRule MAB
IsMachineIdentity false
DTLSSupport Unknown
HostIdentityGroup Endpoint Identity Groups:Grandstream_IP_Phones
Network Device Profile Cisco
Location Location#All Locations#HQ
Device Type Device Type#All Device Types#Wired
IPSEC IPSEC#Is IPSEC Device#No
RADIUS Username C0:74:AD:17:59:6B
Device IP Address 10.200.208.100
CPMSessionID 0AC8D0640000003C0E291D49
Called-Station-ID 3C:41:0E:F2:25:0A
CiscoAVPair service-type=Call Check,
audit-session-id=0AC8D0640000003C0E291D49,
method=mab
Result
UserName C0:74:AD:17:59:6B
User-Name C0-74-AD-17-59-6B
Class CACS:0AC8D0640000003C0E291D49:ISE-PAN/391434383/9726
Tunnel-Type (tag=0) VLAN
Tunnel-Medium-Type (tag=0) 802
Tunnel-Private-Group-ID (tag=0) 301
cisco-av-pair ACS:CiscoSecure-Defined-ACL=#ACSACL#-IP--Employee-5f6da441
cisco-av-pair device-traffic-class=voice
cisco-av-pair cts:security-group-tag=0004-00
cisco-av-pair profile-name=Unknown
LicenseTypes Base license consumed
Steps
11001 Received RADIUS Access-Request
11017 RADIUS created a new session
11027 Detected Host Lookup UseCase (Service-Type = Call Check (10))
15049 Evaluating Policy Group
15008 Evaluating Service Selection Policy
15048 Queried PIP - Normalised Radius.RadiusFlowType
15048 Queried PIP - DEVICE.Device Type
15041 Evaluating Identity Policy
15048 Queried PIP - Network Access.EapAuthentication
22072 Selected identity source sequence - Basic_Internal
15013 Selected Identity Source - AD
24432 Looking up user in Active Directory - AD
24325 Resolving identity - C0-74-AD-17-59-6B
24313 Search for matching accounts at join point - .go.tz
24318 No matching account found in forest - .go.tz
24322 Identity resolution detected no matching account
24352 Identity resolution failed - ERROR_NO_SUCH_USER
24412 User not found in Active Directory - -AD
15013 Selected Identity Source - Internal Users
24210 Looking up User in Internal Users IDStore - C0:74:AD:17:59:6B
24216 The user is not found in the internal users identity store
15013 Selected Identity Source - Internal Endpoints
24209 Looking up Endpoint in Internal Endpoints IDStore - C0:74:AD:17:59:6B
24211 Found Endpoint in Internal Endpoints IDStore
22037 Authentication Passed
24715 ISE has not confirmed locally previous successful machine authentication for user in Active Directory
15036 Evaluating Authorization Policy
15016 Selected Authorization Profile - PermitAccess,_Employee,_IPPhones,Employees
15016 Selected Authorization Profile - PermitAccess,_Employee,_IPPhones,Employees
11022 Added the dACL specified in the Authorization Profile
15016 Selected Authorization Profile - PermitAccess,_Employee,_IPPhones,Employees
15016 Selected Authorization Profile - PermitAccess,_Employee,_IPPhones,Employees
24209 Looking up Endpoint in Internal Endpoints IDStore - C0:74:AD:17:59:6B
24211 Found Endpoint in Internal Endpoints IDStore
11002 Returned RADIUS Access-Accept
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2020 04:19 AM
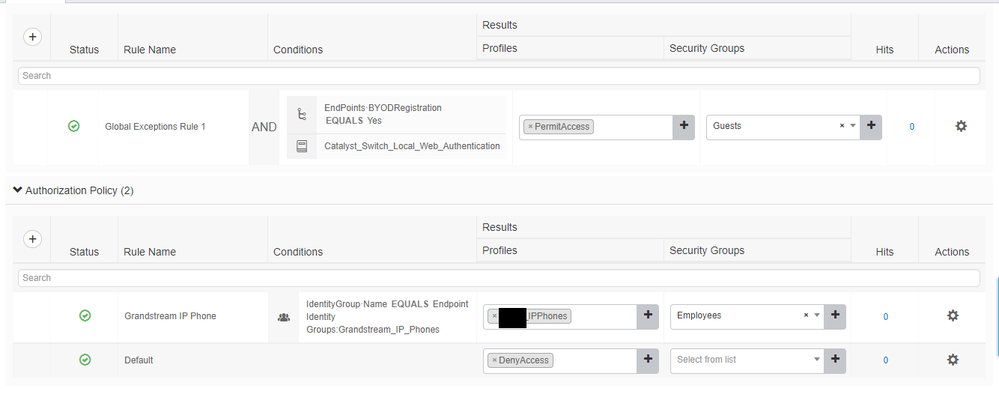
On closer inspection, the screenshots you've provided are out of order and misleading.
Your phone is matching on a local exception policy (which is applied before the Authorisation Policy), why are you using a local exception policy for this?
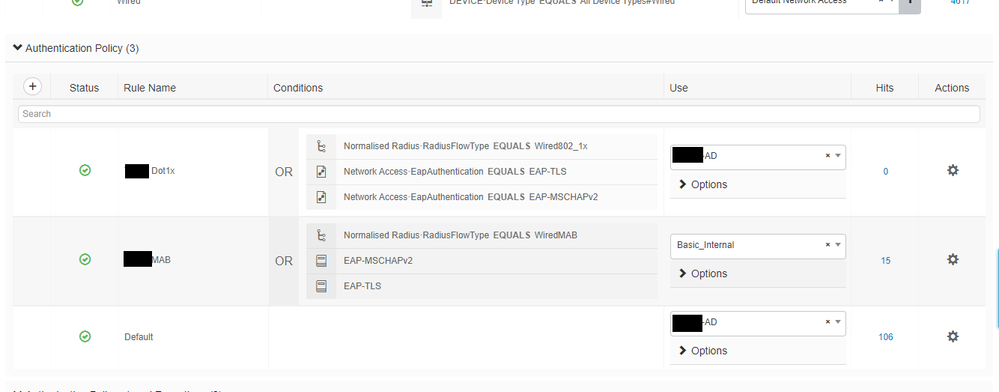
Why do you have Wired_MAB or MSCHAPv2 or TLS? The reason why the IP Phone is matching this rule is because you've defined MAB, remove it and then it should match the expected Authorisation Policy - Grandstream IP Phone.
What is the authentication session output on the switch?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2020 01:11 AM
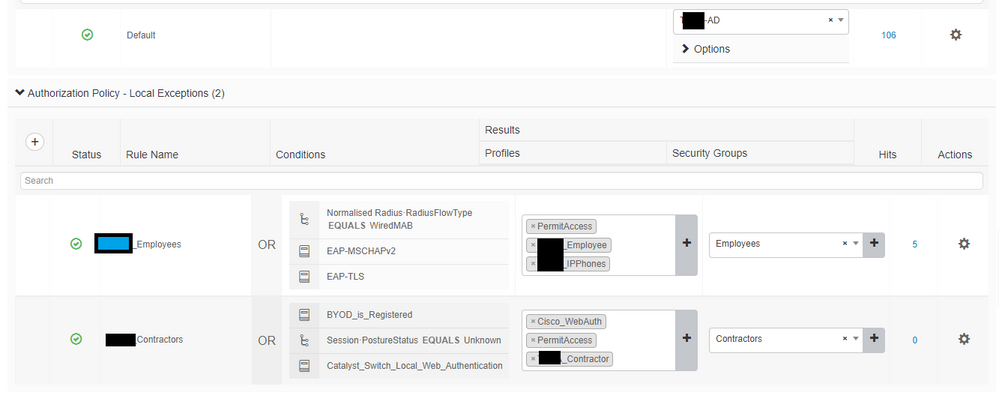
Hello Rob,
It is now matching the policy for which i created but i am still not able to make calls. I do no get any authentication session output on the switch.
Overview
Event 5200 Authentication succeeded
Username C0:74:AD:17:59:6B
Endpoint Id C0:74:AD:17:59:6B
Endpoint Profile Unknown
Authentication Policy Wired >> MAB
Authorization Policy Wired >> Grandstream IP Phone
Authorization Result PermitAccess,_IPPhones
Authentication Details
Source Timestamp 2020-10-12 07:45:58.675
Received Timestamp 2020-10-12 07:45:58.675
Policy Server -ISE-PAN
Event 5200 Authentication succeeded
Username C0:74:AD:17:59:6B
User Type Host
Endpoint Id C0:74:AD:17:59:6B
Calling Station Id C0-74-AD-17-59-6B
Endpoint Profile Unknown
IPv4 Address 192.168.0.160
Authentication Identity Store Internal Endpoints
Identity Group Grandstream_IP_Phones
Audit Session Id 0AC8D0640000000D1381A70C
Authentication Method mab
Authentication Protocol Lookup
Service Type Call Check
Network Device Test
Device Type All Device Types#Wired
Location All Locations#-HQ
NAS IPv4 Address 10.200.208.100
NAS Port Id GigabitEthernet1/0/10
NAS Port Type Ethernet
Authorization Profile PermitAccess,_IPPhones
Response Time 42 milliseconds
Other Attributes
ConfigVersionId 115
DestinationPort 1812
Protocol Radius
NAS-Port 50110
Framed-MTU 1500
OriginalUserName c074ad17596b
NetworkDeviceProfileId b0699505-3150-4215-a80e-6753d45bf56c
IsThirdPartyDeviceFlow false
AcsSessionID -ISE-PAN/391434383/43388
UseCase Host Lookup
SelectedAuthenticationIdentityStores -AD
SelectedAuthenticationIdentityStores Internal Users
SelectedAuthenticationIdentityStores Internal Endpoints
AuthenticationStatus AuthenticationPassed
IdentityPolicyMatchedRule MAB
AuthorizationPolicyMatchedRule Grandstream IP Phone
EndPointMACAddress C0-74-AD-17-59-6B
ISEPolicySetName Wired
IdentitySelectionMatchedRule MAB
IsMachineIdentity false
DTLSSupport Unknown
HostIdentityGroup Endpoint Identity Groups:Grandstream_IP_Phones
Network Device Profile Cisco
Location Location#All Locations#-HQ
Device Type Device Type#All Device Types#Wired
IPSEC IPSEC#Is IPSEC Device#No
Name Endpoint Identity Groups:Grandstream_IP_Phones
RADIUS Username C0:74:AD:17:59:6B
Device IP Address 10.200.208.100
CPMSessionID 0AC8D0640000000D1381A70C
Called-Station-ID 3C:41:0E:F2:25:0A
CiscoAVPair service-type=Call Check,
audit-session-id=0AC8D0640000000D1381A70C,
method=mab
Result
UserName C0:74:AD:17:59:6B
User-Name C0-74-AD-17-59-6B
Class CACS:0AC8D0640000000D1381A70C:-ISE-PAN/391434383/43388
cisco-av-pair profile-name=Unknown
LicenseTypes Base license consumed
Session Events
Steps
11001 Received RADIUS Access-Request
11017 RADIUS created a new session
11027 Detected Host Lookup UseCase (Service-Type = Call Check (10))
15049 Evaluating Policy Group
15008 Evaluating Service Selection Policy
15048 Queried PIP - Normalised Radius.RadiusFlowType
15048 Queried PIP - DEVICE.Device Type
15041 Evaluating Identity Policy
15048 Queried PIP - Network Access.EapAuthentication
22072 Selected identity source sequence - Basic_Internal
15013 Selected Identity Source - -AD
24432 Looking up user in Active Directory - -AD
24325 Resolving identity - C0-74-AD-17-59-6B
24313 Search for matching accounts at join point - .go.tz
24318 No matching account found in forest - .go.tz
24322 Identity resolution detected no matching account
24352 Identity resolution failed - ERROR_NO_SUCH_USER
24412 User not found in Active Directory - -AD
15013 Selected Identity Source - Internal Users
24210 Looking up User in Internal Users IDStore - C0:74:AD:17:59:6B
24216 The user is not found in the internal users identity store
15013 Selected Identity Source - Internal Endpoints
24209 Looking up Endpoint in Internal Endpoints IDStore - C0:74:AD:17:59:6B
24211 Found Endpoint in Internal Endpoints IDStore
22037 Authentication Passed
24715 ISE has not confirmed locally previous successful machine authentication for user in Active Directory
15036 Evaluating Authorization Policy
15016 Selected Authorization Profile - PermitAccess,_IPPhones
15016 Selected Authorization Profile - PermitAccess,_IPPhones
24209 Looking up Endpoint in Internal Endpoints IDStore - C0:74:AD:17:59:6B
24211 Found Endpoint in Internal Endpoints IDStore
11002 Returned RADIUS Access-Accept
i Have removed the wired mab policies.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2020 01:44 AM
What do you see if you issue the command sh auth sess int Gi1/0/10 det on the switch?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2020 02:20 AM
Hi Aref,
This is the outcome,
sh auth sess int Gi1/0/10 det
Interface: GigabitEthernet1/0/10
MAC Address: c074.ad17.596b
IPv6 Address: Unknown
IPv4 Address: 192.168.0.160
User-Name: C0-74-AD-17-59-6B
Status: Unauthorized
Domain: DATA
Oper host mode: multi-auth
Oper control dir: both
Session timeout: N/A
Restart timeout: N/A
Session Uptime: 369s
Common Session ID: 0AC8D0640000001113CF2576
Acct Session ID: Unknown
Handle: 0xA8000004
Current Policy: POLICY_Gi1/0/10
Local Policies:
Service Template: DEFAULT_LINKSEC_POLICY_SHOULD_SECURE (priority 150)
Method status list:
Method State
dot1x Stopped
mab Authc Success
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2020 03:31 AM
It seems as though it is not getting the correct ip.
Interface: GigabitEthernet1/0/10
MAC Address: c074.ad17.596b
IPv6 Address: Unknown
IPv4 Address: 192.168.0.160
User-Name: C0-74-AD-17-59-6B
Status: Authorized
Domain: VOICE
Oper host mode: multi-auth
Oper control dir: both
Session timeout: N/A
Restart timeout: N/A
Session Uptime: 103s
Common Session ID: 0AC8D0640000001B14184E8C
Acct Session ID: 0x0000000F
Handle: 0x3E000008
Current Policy: POLICY_Gi1/0/10
Local Policies:
Service Template: DEFAULT_LINKSEC_POLICY_SHOULD_SECURE (priority 150)
Server Policies:
Vlan Group: Vlan: 301
ACS ACL: xACSACLx-IP-PERMIT_ALL_IPV4_TRAFFIC-57f6b0d3
Method status list:
Method State
dot1x Stopped
mab Authc Success
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2020 10:48 AM - edited 10-12-2020 10:48 AM
Is VLAN 301 the right VLAN? where the DHCP server is located?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2020 11:26 AM
Yes it is the vlan for voice. Do i need to add ip helped for voice on the dhcp config ? Dhcp is configured on the windows server
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2020 01:47 PM
Yes, if the DHCP server is not located within the same VLAN, you need ip helper under the VLAN301 SVI, otherwise, the DHCP traffic would never reach the DHCP server. Just make sure the DHCP server has a scope for VLAN301 as well. It is interesting though to know where the phone got the IP 192.168.0.160 from.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide