- Cisco Community
- Technology and Support
- Security
- Network Security
- Deny TCP/ICMP Reverse Path Check on interface inside
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2012 12:22 AM - edited 03-11-2019 05:33 PM
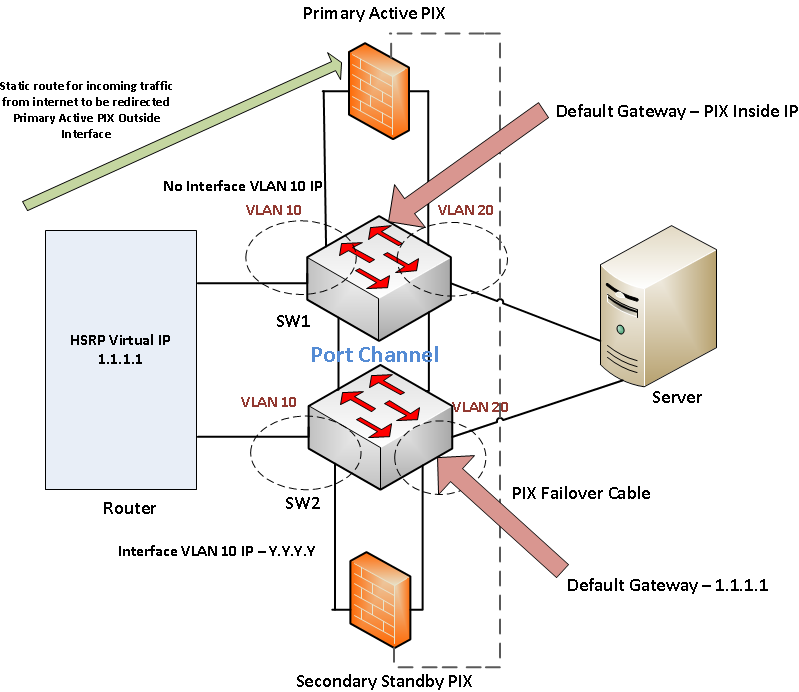
Hi all,
I was trying to take access of a Switch at the remote site from outside using interface VLAN 10 IP Y.Y.Y.Y
The public IP at my location is X.X.X.X
I could see logs on PIX on remote site mentioning that
Deny TCP/ICMP Reverse Path Check from X.X.X.X to Y.Y.Y.Y on interface inside
Deny TCP/ICMP Reverse Path Check from Y.Y.Y.Y to X.X.X.X on interface inside
and I am not able to get connected.
Upon searching the configuration , it was found that reverse path verifcation is enabled on both outside and inside
Also it was noted from the ARP table that ARP entry exists for Y.Y.Y.Y and is learned on the outside interface of PIX.
The issue started happening when IP routing was enabled on SW2.
Being a Web Server /DB Server environment , Is it safe to disable Reverse path verification on inside interface ?
Or should I be checking in detail the routes configured on PIX ?
Thanks,
Anup
Anup
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2012 05:02 AM
Hi Anup.
I would suggest the following:
-Do not disable Reverse path verification.
-Disable 'ip routing' on switch SW2 by using 'no ip routing' command. (I presume SW1 has its routing diabled).
-Configure the following on SW2:
interface vlan 10
ip add Y.Y.Y.Y m.m.m.m.m (where Y.Y.Y.Y is as the same subnet as 1.1.1.1, and m.m.m.m is the mask)
no shut
ip default-gateway 1.1.1.1
Now you should be able to connect.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2012 04:07 AM
reverse path checking explains itself, if the ASA recevies a packet on and interface and the ASA's routing table has that subnet/route on another interface - reverse path checking will drop it.
Check all of your routing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2012 05:02 AM
Hi Anup.
I would suggest the following:
-Do not disable Reverse path verification.
-Disable 'ip routing' on switch SW2 by using 'no ip routing' command. (I presume SW1 has its routing diabled).
-Configure the following on SW2:
interface vlan 10
ip add Y.Y.Y.Y m.m.m.m.m (where Y.Y.Y.Y is as the same subnet as 1.1.1.1, and m.m.m.m is the mask)
no shut
ip default-gateway 1.1.1.1
Now you should be able to connect.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2012 03:48 AM
Hi,
Can it be that after enabling IP routing , the default -gateway configurations are not relavant anymore , that I lost access from outside ? But even after disabling IP routing I am not able to restore access :-(
Thanks,
Anup
Anup
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2012 05:07 AM
Anup,
You can disable the reverse path command from the interface if you know is trsuted but at the end it is better to fix your routing problem to avoid problems in the future.
Regards,
Juan Lombana
Please rate helpful posts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2012 05:49 AM
I have lost access to the switch using VLAN IP from outside after enabling IP routing . Can it be because of the Reverse path check is denying the traffic? I tried disabling the ip routing ,but still I am unable to restore connectivity to the swutch from outside. Would reconfiguring the interface VLAN IP work ?
Sent from Cisco Technical Support Android App
Anup
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2012 01:36 PM
If you want it to remain secure, don't add an external IP to the switches. They should have an internal IP and be accessed via firewall NAT.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
