- Cisco Community
- Technology and Support
- Security
- Network Security
- Edit ACP Policy in FTD2100?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Edit ACP Policy in FTD2100?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2023 06:47 AM - edited 03-29-2023 07:18 AM
I know the ACP Policy (in the FMC GUI not FTD) consists of different policies, but I am trying to make sense of all the Prefilters configured as most don't show any hits. These policies are automatically applied to the FTD or connected devices?
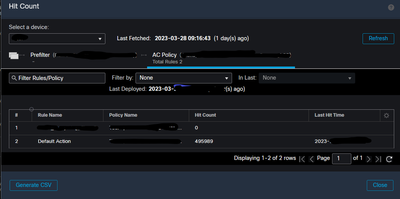
Click on the AC Policy in Hit Count window and it shows 2 rules, and only Default ACtion rule is getting hits so seems traffic is allowed via this rule.
Default Prefilter Policy from main Pre-filter window is blank with no rules (states cant add rules, can only change default action options) says it is for allowing all tunnels.
How do I view/edit this rule for the AC Policy (if possible) or how do I confirm what default action is?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2023 12:45 AM
I don't know of an easy way to do this. If you need to optimize your rules you can use Policies > Access Control > Access Control > add/edit policy > Analyze Hit Counts feature in FMC. This is probably the easiest way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2023 05:13 AM
Yes I do reference Hit Counts. Thing is, I create rules but tightening up source, ports, etc. for what I know for sure is used and needed and place that rule in front of wider source to ANY dest/port rule, but it never gets hit.
When doing packet-tracer, it always references an implicit rule (can't find which one its referring to) and some other rules that I can't find based on ID, or the MyRule test which is a blocking statement so that would not be how the traffic is being allowed in.
Take a look at packet-tracer below. I have scrubbed some IPs and names for simplicity and privacy. Are you able to confirm based on the output which rule is allowing the 1.1.1.1 traffic to 2.2.2.2 in through the Outside interface?
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide