- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Firepower 2110 - Secondary Outside interface port for 1 ISP router
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2021 10:08 AM
Hello,
Public IP block from ISP gave is all occupied, so I requested extended IP block to ISP.
so I got new IP block with new port (same router), but I am not sure how can I make this new IP block to apply my firepower.
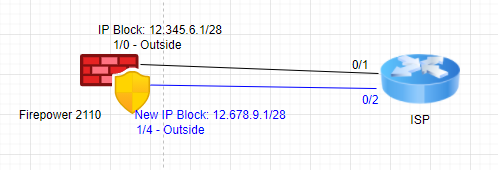
Here is the image what I am considering:
The blue line is about to newly add.
ISP provider gave me a notification that they are configured new IP block on 0/2 port. So I don't know If I can use same firepower. Is this possible without loop?
What else should I configure on my firepower to make it?
Thank you.
Solved! Go to Solution.
- Labels:
-
Network Management
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2021 11:45 AM - edited 09-15-2021 11:47 AM
@eeebbunee no I am saying on the router the ISP would create a static route for the new network with a next hop of the firewalls current outside interface IP address. You don't need to apply the new network on a physical interface. You then create static NAT rules on the firewall.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2021 12:48 PM
@eeebbunee correct. You then need to create static NAT rules with those new IP addresses.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2021 10:26 AM
@eeebbunee you should get your ISP to route the new subnet to the outside IP address of your existing interface. You then just need to create NAT rules using an IP address from the new subnet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2021 11:41 AM
Thanks for the reply.
You mean the existing interface (Router 0/1 port) needs to have both IP blocks?
New IP block has totally different IP address, so that's why ISP setup the other port.
Please correct me which part am I misunderstand.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2021 11:45 AM - edited 09-15-2021 11:47 AM
@eeebbunee no I am saying on the router the ISP would create a static route for the new network with a next hop of the firewalls current outside interface IP address. You don't need to apply the new network on a physical interface. You then create static NAT rules on the firewall.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2021 12:41 PM
Okay, so If I'm correctly understand, ISP router is configured by ISP provider by adding static route.
For example) 12.678.9.1 x.x.x.x(subnet) via 12.345.6.1(my existing firewall outside)
Therefore, I don't need to make physical connection between ISP router and my firewall, am I correct?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2021 12:48 PM
@eeebbunee correct. You then need to create static NAT rules with those new IP addresses.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-16-2021 08:39 AM
I was thinking about one more physical connection between firewall and ISP because ISP provider told me to do it (use another ports), but I will request them to change routing configuration followed your advise.
I really appreciate it..!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2021 07:11 AM
Rob, My ISP is providing me two ranges ( totally different) and have added a static route on the Internet Router for the new range pointing to the FW outside interface having IP from the existing range.
New range could be used to create NAT rules for traffic coming from the inside interface on the FW, correct.
Will I be able to create NAT rules for AnyconnectVPN users ( connecting via the existing interface IP) using the new range ?
Thanks very much in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2021 07:21 AM
@ashwanik2008 Not sure I totally understand your question.
Do you want to NAT traffic from a VPN user using one of those new IP addresses, yes that would probably work - not tried it myself but something like this:-
nat (outside,inside) source static RAVPN RAVPN-NATTED destination static LAN LAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2021 07:27 AM
Thanks for quick reply, Rob.
I meant the internet bound traffic from AnyConnect VPN users, ( OUTSIDE, OUTSIDE) hair-pinned on the OUTSIDE interface.
OUTSIDE interface has an IP from the existing range but requirement is to use new range for NAT statements for these remote users.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2021 07:34 AM
Try this:-
object network RAVPN
subnet <vpn ip pool network> <subnet mask>
nat (outside,outside) dynamic <ip address from new range>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2021 07:57 AM
Yes, that`s what I`m gonna try. Thanks Rob
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2021 11:33 AM
Is your goal to load balance or to set up a secondary route (in case of failure)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2021 11:44 AM
This is for secondary route, to using 1:1 NAT rule. Currently public IP addresses ran out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2021 11:53 AM
Full disclosure, I am studying for my CCNA and trying to utilize these boards and questions to grow myself as a tech, so I just wanted to say that before I offer a suggestion.
If I am not mistaken you should be able to issue the commands on your router that will allow for a backup default route:
ip route 0.0.0.0 0.0.0.0 gi0/1
ip route 0.0.0.0 0.0.0.0 gi0/2 5
Issuing the "5" at the end created a floating static route that will only be placed in the routing table and used in case the primary route "gi0/1" is removed from the routing table.
Sorry if I misunderstood your issue.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide