- Cisco Community
- Technology and Support
- Security
- Network Security
- FMC to remote FTD deployment
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
FMC to remote FTD deployment
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2017 06:46 AM - edited 02-21-2020 06:45 AM
Want to deploy an ASA5506-X (running FTD v6.2.2) to a remote site and then be able to set up and manage a Site-to-Site VPN back to HQ where FMC server is located.
A) Is this even possible?
B) What is the best way to do this?
Remote FTD -----> Internet -----> HQ --> FMC
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2018 06:22 PM
You cannot configure NAT via cli (ssh session - never use telnet).
If you configure via local manager (FDM) and then change to remote manager (FMC), the configuration is lost.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2019 12:24 PM
Has this issue been "fixed" or addressed in newer versions of code (like anytime after 6.4?). Curious as I will be running up against this as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2018 12:27 PM
Did you attempt this as of yet and if so, which method did you use? I have the same scenario and I wanted to see if one method is better than the others. On top of what you have listed, my FTD in the remote site is the device that is doing the VPN for the networks behind it, so I can't/won't be relying on MPLS or some other VPN device for reachability.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-06-2018 08:34 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2018 08:21 AM
Simply stated, you cannot do the same process with FTD as we can with ASA/FirePower which sucks. To do so either requires tricky setup, which is dangerous if you have problems down the road at your remote site, or requires more hardware. Maybe this is by design now. Either way you cannot simply add a locally managed FTD to a FMC at your main site. I know that the features parity are not the same yet, but I sure hope this is resolved down the road.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2018 05:38 PM
I found this article VERY helpful!
https://www.theroutingtable.com/add-remote-firepower-firewall-to-firepower-management-center/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2018 08:28 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2018 06:43 AM
Any further traction on how to's on this? We are looking to encrypt this connection via IPSec. Running a ASA code with an SFR module is not an option and we will look at other vendors.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2018 07:04 AM
Note that the connection between and FTD device and the managing FMC is already encrypted (TLS running over tcp/8305).
If you do a packet capture on the flow you will see it does an SSL/TLS handshake and uses the respective certificates from FMC and the FTD device to setup a secure channel for management and eventing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2018 07:11 AM
Very true. I've setup many networks where the FMC and FTD are located in separate continents. Whilst the FP Management/Event Comms are encrypted, stick to security by design and use an MPLS or VPN between the two networks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2022 08:32 AM
Hi meconomou. How did the setup work for you? Is it supported by Cisco TAC? The setup you described seems the safest and easiest from an operations perspective... I only get concerned if it's not supported or if there is any security risk having the management interface on the internet (even though there is an ssh access-list on it). It gives the most flexibility since you can send out a firewall with a public IP on the management interface... and it can be up and running at the same time as the firewall you are replacing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2022 11:24 AM
Recent versions of FTD now support using the firewall's outside data interface for management, as an alternative to using the management port. You have to do the configuration including IP addresses from the console serial port, and there are a few restrictions on it (routed-mode only, not for HA/Cluster, etc.), but you can finally get away from needing two public IP addresses to support a remote FTD.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-23-2019 10:56 PM
Losing sleep over this problem too.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
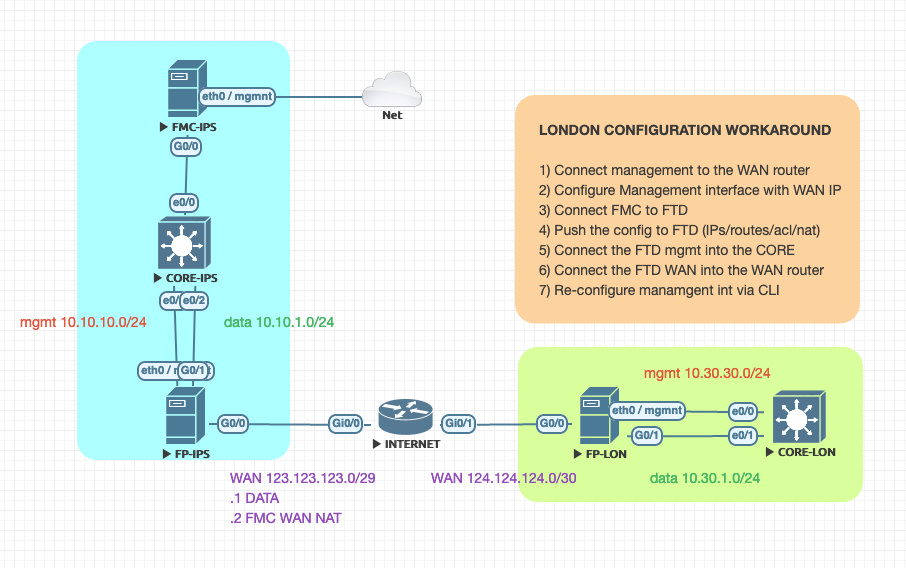
09-08-2020 06:14 AM - edited 09-09-2020 01:07 AM
Hi Stuart,
Here's a workaround:
- configure the management with the public IP address and connect it to internet
- when you add the manager configuration don't forget to add the nat-id: "configure manager add x.x.x.x registration-key nat-id"
- when you add the FTD on the FMC DO NOT SET the FTD IP address but just the registration-key and nat-id, so the FMC will wait for the FTD to connect back
- once the FTD is connected, push the configuration with the real WAN/LAN ip addresses/routes/acls/nats. Since the management works on a sort of vrf, there will be no conflict
- connect the FTD WAN interface to INTERNET
- connect both FTD LAN and MANAGEMENT interface to the internal switch
- configure the routing on the switch
- re-configure the FTD management via the CLI: "configure network ipv4 manual x.x.x.x y.y.y.y z.z.z.z"
- the management traffic will be routed to the switch, go back to the INSIDE, get natted behind the OUTSIDE out to internet
- enjoy
WHILE THIS IS NOT A CISCO CERTIFIED PROCEDURE, IT DOES WORK IF YOU FOLLOW ALL THE ABOVE STEPS.
Ciao!
Andrea
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2022 06:33 AM
Ciao Andrea,
You are saying:
FP-LON configure mgmt interface with wan ip? How to connect with the other FTD_IPS? I don't understand that part? If you can help me to understand?
Grazie
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide