Hi all,
I can't seem to find a good intrusion rule to detect DNSCAT2 tunneling traffic.
I've set up a working DNSCAT2 tunnel, and copied all DNS traffic with a SPAN port to a passive interface on our FTD.
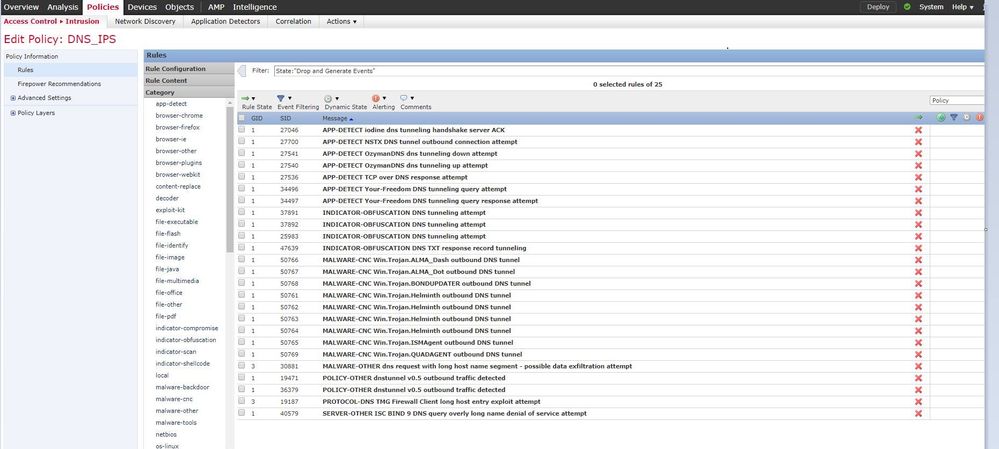
Then created a dedicated rule with application "DNS" and a dedicated intrusion profile with all DNS tunneling detection rules I could find. (refer to picture).
I see the DNS traffic appearing in the connection events, and they pass via the correct rule with the dedicated intrusion profile on it.
However, the only rule that triggers is 30881 - dns request with long host name segment - possible data exfiltration event.
Unfortunately this rule is not very useful for detecting DNS tunneling, because we see it also triggers for the typically big cloud dns-names you see nowadays.
Does anyone know a good way to detect dns tunneling with the FTD?
edit:
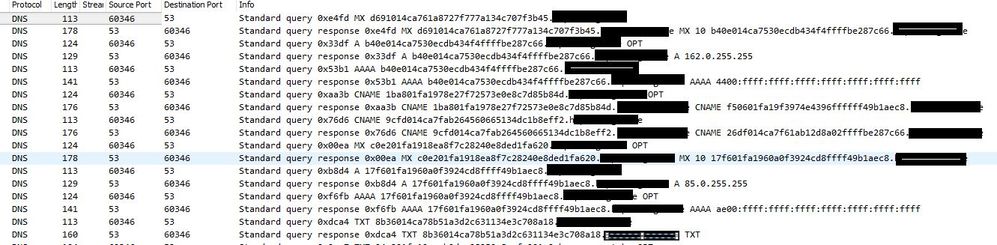
and example of a dnscat2 tunnel
Best Regards,
Joeri