- Cisco Community
- Technology and Support
- Security
- Network Security
- FTP traffic block by server and reqeust-command
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
FTP traffic block by server and reqeust-command
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-08-2011 06:03 PM - edited 03-11-2019 03:00 PM
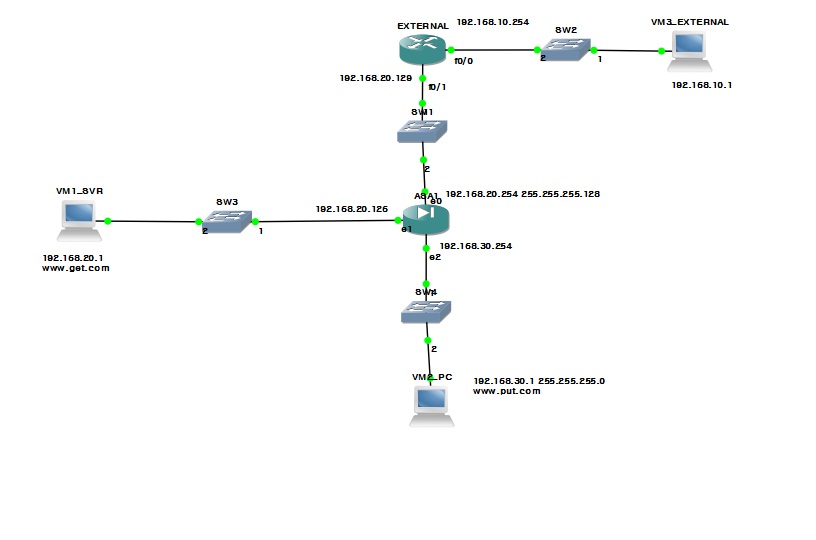
Hi, Im studenty who studing MPF FTP, but Im struggling with blocking ftp traffic by using server regex and reqeust-command,
I have two ftp servers, one located in DMZ - www.get.com , reset all request-command except get command
one located in inside - www.put.com, reset all request-command execept put command
from the outside PC, every single request command is working. but without assigning any server regex, it works,
With Outside PC, I did assign ip address (mapped ip on ASA) with domain name on -hosts file-
here is my configuration
ciscoasa(config)# sh run
: Saved
:
ASA Version 8.0(2)
!
hostname ciscoasa
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0/0
nameif outside
security-level 0
ip address 192.168.20.254 255.255.255.128
!
interface Ethernet0/1
nameif dmz
security-level 50
ip address 192.168.20.126 255.255.255.128
!
interface Ethernet0/2
nameif inside
security-level 100
ip address 192.168.30.254 255.255.255.0
!
interface Ethernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/4
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/5
shutdown
no nameif
no security-level
no ip address
!
passwd 2KFQnbNIdI.2KYOU encrypted
regex GET_SITE2 "[Gg][Ee][Tt]\.[Cc][Oo][Mm]"
regex GET_SITE3 "([0-9A-Za-z])*[Gg][Ee][Tt]\.[Cc][Oo][Mm]"
regex GET_SITE4 ".*\.get\.com"
regex PUT_SITE "put\.com"
regex GET_SITE "get\.com"
regex PUT_SITE2 ".*\.put\.com"
ftp mode passive
access-list EXTERNAL extended permit tcp any host 192.168.20.201 eq ftp log
access-list EXTERNAL extended permit tcp any host 192.168.20.202 eq ftp log
access-list EXTERNAL extended deny ip any any log
pager lines 24
mtu outside 1500
mtu dmz 1500
mtu inside 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
static (dmz,outside) 192.168.20.201 192.168.20.1 netmask 255.255.255.255
static (inside,outside) 192.168.20.202 192.168.30.1 netmask 255.255.255.255
access-group EXTERNAL in interface outside
route outside 0.0.0.0 0.0.0.0 192.168.20.129 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
no crypto isakmp nat-traversal
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
!
class-map type regex match-any PUT_SITE_LIST
match regex PUT_SITE
match regex PUT_SITE2
class-map type regex match-any GET_SITE_LIST
match regex GET_SITE
match regex GET_SITE2
match regex GET_SITE3
match regex GET_SITE4
class-map type inspect ftp match-all L7_GET_CLASS
match server regex class GET_SITE_LIST
match not request-command get
class-map type inspect ftp match-all L7_PUT_CLASS
match not request-command put
match server regex class PUT_SITE_LIST
class-map L3/4_GET_CLASS
match port tcp eq ftp
!
!
policy-map type inspect ftp L7_FTP_POLICY
parameters
class L7_GET_CLASS
reset log
class L7_PUT_CLASS
reset log
policy-map L3/4_GET_POLICY
class L3/4_GET_CLASS
inspect ftp strict L7_FTP_POLICY
!
service-policy L3/4_GET_POLICY interface outside
prompt hostname context
Cryptochecksum:00000000000000000000000000000000
: end
ciscoasa(config)#
ASA able to inspect the traffic i think because packet is increased when client is logged in ,
can you please help me with this problem ??
thanks !!
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2011 08:31 PM
Terry,
I would like to help you on this one, but first I need to understand what is your goal with the Layer 7 inspection. If you want to block when certain commands are typed the ASA has a list of them. Regex area really used when there is a type of file name, server and so on....
What is exactly what you are trying to block?
Mike
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2011 04:05 PM
thanks for reply,
I want to block all other request-command except get command for www.get.com
and block all other request-command except put command for www.put.com
thanks !!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2011 04:28 PM
what If you try something like this:
regex SERVER_GET get\.com
regex SERVER_PUT put\.com
class-map type inspect match-all ftp GET
match not request-command get
match server SERVER_GET
class-map type inspect match-all ftp PUT
match not request-command put
match server SERVER_PUT
Policy-map type inspect ftp FTP-SERVICE
class GET
reset log
class PUT
reset log
Note the match-all which means that it will need to match both statements included on the class map.
Let me know if it works fine.
Mike
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2011 04:30 PM
thanks for reply back,
I did try that configuration but, It did not work, both put and get command working for both of them,
and packet has been pass through ASA, (service-policy packet is increased)
ciscoasa(config)# sh service-policy
Interface outside:
Service-policy: L3/4_FTP_POLICY
Class-map: L3/4_FTP_CLASS
Inspect: ftp strict FTP_SERVICE, packet 32, drop 0, reset-drop 0
ciscoasa(config)# sh run
: Saved
:
ASA Version 8.0(2)
!
hostname ciscoasa
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0/0
nameif outside
security-level 0
ip address 192.168.20.254 255.255.255.128
!
interface Ethernet0/1
nameif dmz
security-level 50
ip address 192.168.20.126 255.255.255.128
!
interface Ethernet0/2
nameif inside
security-level 100
ip address 192.168.30.254 255.255.255.0
!
interface Ethernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/4
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/5
shutdown
no nameif
no security-level
no ip address
!
passwd 2KFQnbNIdI.2KYOU encrypted
regex SERVER_PUT "put\.com"
regex SERVER_GET "get\.com"
ftp mode passive
object-group icmp-type ICMP
icmp-object echo
icmp-object echo-reply
icmp-object unreachable
access-list EXTERNAL extended permit tcp any host 192.168.20.201 eq www
access-list EXTERNAL extended permit tcp any host 192.168.20.202 eq www
access-list EXTERNAL extended permit tcp any host 192.168.20.202 eq ftp
access-list EXTERNAL extended permit tcp any host 192.168.20.201 eq ftp
access-list EXTERNAL extended permit icmp any host 192.168.20.201 object-group ICMP
access-list EXTERNAL extended permit icmp any host 192.168.20.202 object-group ICMP
access-list EXTERNAL extended deny ip any any log
pager lines 24
mtu outside 1500
mtu dmz 1500
mtu inside 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
nat-control
global (outside) 1 interface
nat (inside) 1 192.168.30.0 255.255.255.0
static (dmz,outside) 192.168.20.201 192.168.20.1 netmask 255.255.255.255
static (inside,outside) 192.168.20.202 192.168.30.1 netmask 255.255.255.255
access-group EXTERNAL in interface outside
route outside 0.0.0.0 0.0.0.0 192.168.20.129 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
no crypto isakmp nat-traversal
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
!
class-map type inspect ftp match-all PUT
match not request-command put
match server regex SERVER_PUT
class-map type inspect ftp match-all GET
match not request-command get
match server regex SERVER_GET
class-map L3/4_FTP_CLASS
match port tcp eq ftp
!
!
policy-map type inspect ftp FTP_SERVICE
parameters
class GET
reset log
class PUT
reset log
policy-map L3/4_FTP_POLICY
class L3/4_FTP_CLASS
inspect ftp strict FTP_SERVICE
!
service-policy L3/4_FTP_POLICY interface outside
prompt hostname context
Cryptochecksum:00000000000000000000000000000000
: end
ciscoasa(config)#
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
