- Cisco Community
- Technology and Support
- Security
- Network Security
- GNS3 VM ASA No Route to Host
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
GNS3 VM ASA No Route to Host
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2016 09:04 AM - edited 03-12-2019 12:43 AM
Hi all,
I am hoping somebody can assist me here. I know there are similar posts on these types of issues, however none seem to have assisted me in resolving my issue.
I have created a lab in GNS3 utilizing the GNS3 VM: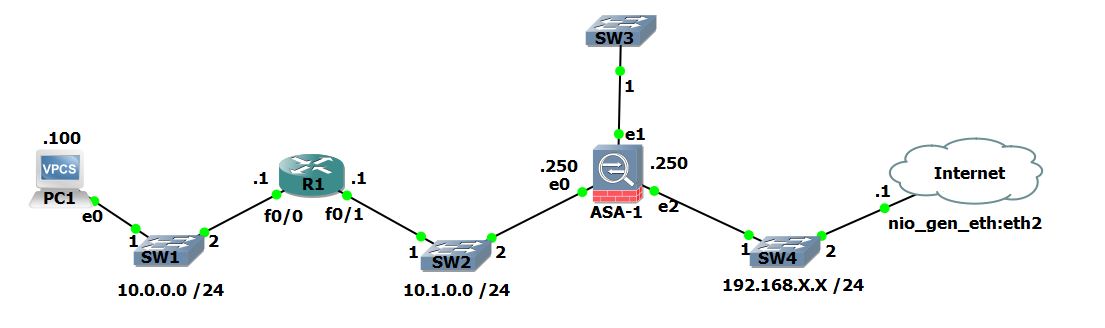
It is fairly straightforward in terms of networks. I have a directly connected inside network of 10.1.0.0/24 and an outside network of 192.168.8.0/24.
The problem I am having is as follows: I am unable to pass traffic through the firewall from inside to outside with the following Drop-reason: (no-route) No route to host
When pinging from the firewall I am able to ping outside to 8.8.8.8, however, when pinging from the inside interface, PC1 or R1 I am not able to reach 8.8.8.8. It is worth noting that I am able to ping the inside interface of ASA-1 from both PC1 and R1.
Quite simply put, the ASA seems to have no route between two directly connected interfaces (inside & outside).
Tests:
Ping from PC1 to ASA inside interface - Successful
Ping from PC1 to 8.8.8.8 - Unsuccessful
Ping from ASA-1 to 8.8.8.8 - Successful
Ping from ASA-1 inside interface - Unsuccessful
Packet-Tracer Results:
ciscoasa# packet-tracer input inside icmp 10.1.0.1 8 0 192.168.8.250
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 2
Type: ROUTE-LOOKUP
Subtype: input
Result: ALLOW
Config:
Additional Information:
in 192.168.8.250 255.255.255.255 identity
Phase: 3
Type: ROUTE-LOOKUP
Subtype: input
Result: ALLOW
Config:
Additional Information:
in 192.168.8.250 255.255.255.255 identity
Result:
input-interface: inside
input-status: up
input-line-status: up
output-interface: NP Identity Ifc
output-status: up
output-line-status: up
Action: drop
Drop-reason: (no-route) No route to host
Show Route:
Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default, U - per-user static route, o - ODR
P - periodic downloaded static route
Gateway of last resort is 192.168.8.1 to network 0.0.0.0
C 192.168.8.0 255.255.255.0 is directly connected, outside
S 10.0.0.0 255.0.0.0 [1/0] via 10.1.0.1, inside
C 10.1.0.0 255.255.255.0 is directly connected, inside
S* 0.0.0.0 0.0.0.0 [1/0] via 192.168.8.1, outside
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2016 10:05 AM
Hi -
Based on your drawing and output I can tell you the packet tracer is correct. Since 192.168.8.250 is assigned to the ASA, you will never be able to ping it from another ASA interface. It's that simple. The ASA is a funny beast that way.
A packet tracer to 192.168.8.1 should report success.
Please post a packet tracer going from 10.0.0.100 to 8.8.8.8.
HTH
PSC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2016 11:50 AM
Hi Paul,
Okay, you are right in saying the packets are not dropped when doing a packet tracer to 192.168.8.1.
I am still unable to ping 8.8.8.8 from 10.0.0.100, here is the packet-tracer output as requested:
ciscoasa# packet-tracer input inside icmp 10.0.0.100 8 0 8.8.8.8
Phase: 1
Type: ROUTE-LOOKUP
Subtype: input
Result: ALLOW
Config:
Additional Information:
in 0.0.0.0 0.0.0.0 outside
Phase: 2
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 3
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 4
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
Additional Information:
Phase: 5
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 4, packet dispatched to next module
Result:
input-interface: inside
input-status: up
input-line-status: up
output-interface: outside
output-status: up
output-line-status: up
Action: allow
Just to add additional context, the 192.168.8.X network is the personal home network on which my GNS3 host sits. Do you think this may be a NAT issue? I did follow a lab where PAT was configured on the ASA using the external IP (192.168.8.250) as a network object, however I was still unable to ping and halted the lab right there to troubleshoot.
Mark
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2016 01:55 PM
Hi Mark -
Let's start by talking about ICMP. You need to understand that it is a connectionless protocol. ICMP echo (type 8) packets are only loosely tied to echo-reply (type 0) packets. So packets flowing out through the firewall don't get an embryonic port created for return traffic unless you have application inspection enabled or you override the behavior by creating an inbound ICMP rule. The easiest (and preferred) way to deal with this is by enabling ICMP inspection in the default policy-map.
You will also need NAT rule for the traffic unless you have static routes installed on 192.168.8.1 pointing to the firewall for the 10.0.0.0/15 network. This is because the upstream router won't know how to get back to your test network. (The packet tracer shows that no network translation occurs in your current configuration.)
PSC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2016 11:19 AM
Thanks Paul.
The device I have with me unfortunately is not capable of static routes. I went for the NAT option, using a simple static NAT on the ASA where I assigned 192.168.8.110 to the internal IP of 10.0.0.100. Unfortunately I was still not able to ping out to 8.8.8.8.
I should be able to try static routes this weekend with another router.
This one is still very much up in the air.
Mark
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2016 06:02 PM
hi markaellis,
for the 10.0.0.0 to ping 8.8.8.8, two things have to happen. first, you will have to create a NAT entry on the ASA to allow 10.0.0.0 to go outside. when this is done, you may be able to access the internet from the browser but still won't be able to ping 8.8.8.8. the reason being is that ASA by default drops the ICMP packets. to enable that, you will have to allow it on the ASA. i'm not home at the moment. when i go home, i'll give you a step by step config so that you can get it to work. this topology is similar to Keith Parker's 210-260 topology if not the same. if you have access to CBTnuggets videos, you will be able to follow step by step to reach your goal. however, if you don't have access, i'll post it for you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-10-2016 01:47 PM
hi Mark,
ok, going back to your problem. since i have no config on R1, i would go and assume that you have made a route to the 10.0.0.0 network on R1. you should add the following command to R1
ip route 0.0.0.0 0.0.0.0 10.1.0.250
now going back to the ASA, you should also make a route to the inside like this:
route inside 10.0.0.0 255.255.255.0 (or 255.0.0.0) 10.1.0.1
you should be able to get a connection between the pc1 and the ASA and vice versa.
to get PC1 to browse the internet, you will have to NAT the inside network. if you are using ASDM, see the attached step. please note that you will need to change the IP to match your network as mine is a little bit different. you would need to change the network 10.1.10.0 to 10.0.0.0. you will need to do a PAT and the translated address is outside as shown. if you don't have ASDM and you do it from the CLI, here is the config
object network (whatever you want to call it)
subnet 10.0.0.0 255.255.255.0
nat (inside,outside) dynamic (the name of the object network) interface
after that, you should be able to get pc1 to surf the internet normally.
as for the pinging, you shouldn't be able to ping still, although you can access the internet as ASA doesn't inspect ICMP packets. so we will have to enable it. we would go to ASDM and do the following
Configuration>Firewall>Service policy Rules> edit the global policy and tick the ICMP as shown in the file attached.
i hope this helps. post if it doesn't work still.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2016 01:43 AM
Thank you for the response and apologies for the delay. I have been tied down with work.
You are 100% correct in saying the is the same topology in CBTNuggets. I did in fact follow the same steps however I found myself achieving different results. I would just like to point out again that communication between the 10.0.0.0 /24 network and the ASA is working 100%. R1 is indeed configured as you suggested. I can also get out to the internet from the ASA. In the CBTNuggets video, NAT is added and he is then able to set PC1's DNS to 8.8.8.8 which resolves when pinging www.google.com. Unfortunately mine does not resolve and it was at this point where I began this troubleshooting process. The vPC I am using does not have a way to browse the internet as far as I am aware.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


