- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Hairpin Traffich through different interface?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2020 11:19 PM - edited 02-21-2020 09:52 AM
Hi all,
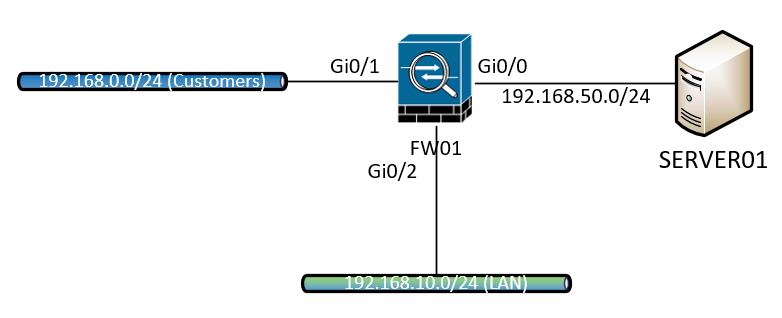
I think i have a simple question but i have no solution for it. Imagine the following topology:
I've left out all the unimportant stuff.
Now basically what my question is: is there any way i can make SERVER01 ingress at Gi0/1 (Customer interface) without messing around with the physical connections?
Why? Server01 will be running vulnerability scanning software, but we want to scan from Customers perspective and Server01 in this case will be running in the Cloud. The best situation will be if Server01 ingresses at Gi0/1 since that ACL will be applied. I want to prevent to make double ACL's since the "effect" of vulnerability scanning will be lost if i manually need to (re)create the same ACL as Gi0/1. And in this case i can't just apply the Gi0/1 ACL to Gi0/0 as well since there is a lot more stuff coming from the cloud.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-27-2020 10:04 AM
Short answer: No.
When the server traffic ingresses, the ASA will lookup the egress interface based on the routing table and (possibly) and NAT override. You could put in a NAT rule to make the server seem like it's on the customer network but that won't make it hit the inbound ACL on Gi0/1.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-27-2020 10:04 AM
Short answer: No.
When the server traffic ingresses, the ASA will lookup the egress interface based on the routing table and (possibly) and NAT override. You could put in a NAT rule to make the server seem like it's on the customer network but that won't make it hit the inbound ACL on Gi0/1.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-27-2020 12:09 PM
Hi Marvin,
Thanks for the response. I was already afraid of that answer but it is what it is.
Do you perhaps have a suggestion if we would want to perform a vulnerability scan of some sort from customers perspective, but where it's kind of complicated to connect a machine from the customers side.
Basically the only thing i want to avoid is to seperately build 2 ACL's. Not that i'm lazy, but to completely "trust" the outcome of a vulnerability scanning report. I'm not really sure how to deal with this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-27-2020 01:33 PM
If you could insert a small switch between your ASA and the customer(s) you could plug your scanning tool into that.
Or if the ASA in question was a 5506 with bridge-group interface support then you could make the customer and scanning server interfaces part of the same bridge-group.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide