- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Is ISRg3 IOS-XE PKI/SCEP with OTP enrolment possible?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-04-2021 09:41 AM
Hi Guys,
I have an ISRg3 WAN running IOS PKI & SCEP with flexVPN which is working well. I have tested the Hub CA with both SCEP 'Grant Auto' and 'Terminal Manual' Spoke enrolment which works great. However, I'm after a halfway house in an ideal world.. I would like to setup SCEP with OTP passwords to authenticate each cert enrolment with a OTP temporary key using the following OTP command at the Hub CA.. The idea is that the OTP is then handed to the spoke router administrator to allow cert enrolment.
crypto pki server cs-label password generate [minutes]
Is certainly looks like it is possible to setup on IOS-XE.. But I can't find enough detail or figure out how to actually make it work. Can anyone help please?
SCEP, which is the only supported enrollment protocol, supports two client authentication mechanisms—manual and preshared key. Manual enrollment requires the administrator at the certification authority (CA) server to specifically authorize the enrollment requests; enrollment using preshared keys allows the administrator to preauthorize enrollment requests by generating a one-time password.
Thanks a lot
Matt
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-04-2021 12:00 PM - edited 03-04-2021 12:09 PM
Hi Matt,
Long time no speak, hope you are well?
The cisco docs aren't that clear.
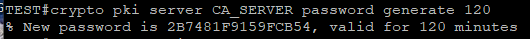
On the CA server generate the OTP, the output displays the password, copy and paste the password.
On the spoke router enrolling for the certificate you define the OTP under the trustpoint, using the password command - pasting the password from the CA server. Authenticate and enroll as normal, when enrollment takes place it will use the password specified for the SCEP enrollment password.
crypto pki trustpoint TEST_CA
password 2B7481F9159FCB54
crypto pki authenticate TEST_CA
crypto pki enroll TEST_CA
If the password is correct the certificate should automatically be approved, the output on the console should confirm this. Run show crypto pki certificates on the spoke router, confirm the status is available.
On the CA server you can run debugs - debug pki scep and debug pki server which should shed some light on the enrollments.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-04-2021 12:00 PM - edited 03-04-2021 12:09 PM
Hi Matt,
Long time no speak, hope you are well?
The cisco docs aren't that clear.
On the CA server generate the OTP, the output displays the password, copy and paste the password.
On the spoke router enrolling for the certificate you define the OTP under the trustpoint, using the password command - pasting the password from the CA server. Authenticate and enroll as normal, when enrollment takes place it will use the password specified for the SCEP enrollment password.
crypto pki trustpoint TEST_CA
password 2B7481F9159FCB54
crypto pki authenticate TEST_CA
crypto pki enroll TEST_CA
If the password is correct the certificate should automatically be approved, the output on the console should confirm this. Run show crypto pki certificates on the spoke router, confirm the status is available.
On the CA server you can run debugs - debug pki scep and debug pki server which should shed some light on the enrollments.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2021 12:33 AM
Morning Rob
Great to hear from you. Thanks a lot for providing the missing link.. Everything now works perfectly in my lab, I searched everywhere for that info to no avail.
I'm well thanks, I hope you're also well? I'll drop you a message on LinkedIn it would be nice to catch up.
Thanks again
Matt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2022 02:44 AM
I know it has been a long time.
However I have a question , In the case that I choose the OTP mechanism to be the only way to authenticate the spoke scep enrollment , do I have to configure the CA server to reject all other requests ? .
similar to that crypto pki server cs-label reject all
As I believe if I did not configure that , all of the other spoke SCEP requests can be granted normally even without the password configured
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide