- Cisco Community
- Technology and Support
- Security
- Network Security
- Logging events via third party
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Logging events via third party
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2020 05:36 AM
Under the ACP logging menu, if you have the syslog alert variable set, does that mean that in addition to sending the same event logs to the FMC, it also sends the same syslog to what you configure as?
If so, what syslog servers do you guys use that provide the same functionality as the FMC where you can search based on items such as source IP and block reason.
I find the fmc is nice for the short term but doesn't retain data long enough. Could it be that the FMC needs to be reconfigured to retain more data?
- Labels:
-
NGIPS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2020 06:08 AM
Customers who require extended log retention typically use something like Splunk ($$$) or, if they have some time to setup an open source solution, something like greylog or ELKstack.
Another option is to switch over to CDO management and use Cisco's recently-introduced Security Analytics and Logging (SAL) service. It retains 90 days of events and pricing is based on volume.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2020 06:44 AM
Thanks. Does the logging get sent to the FMC still if external syslog is configured or does that override FMC? How can I ensure my fmc is configured to allow its max potential to store logging data or retention period.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2020 09:10 PM
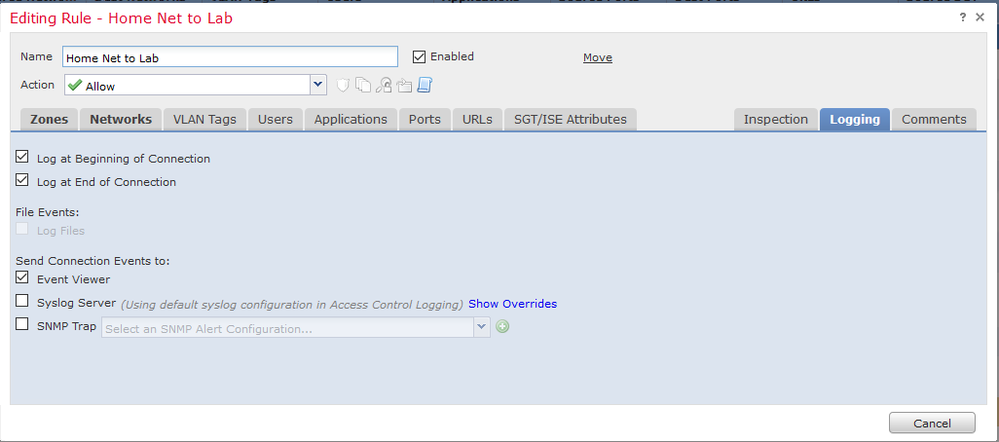
Logging will still be sent to FMC as long as your rule entries have the selection for "event viewer" in their logging setting:
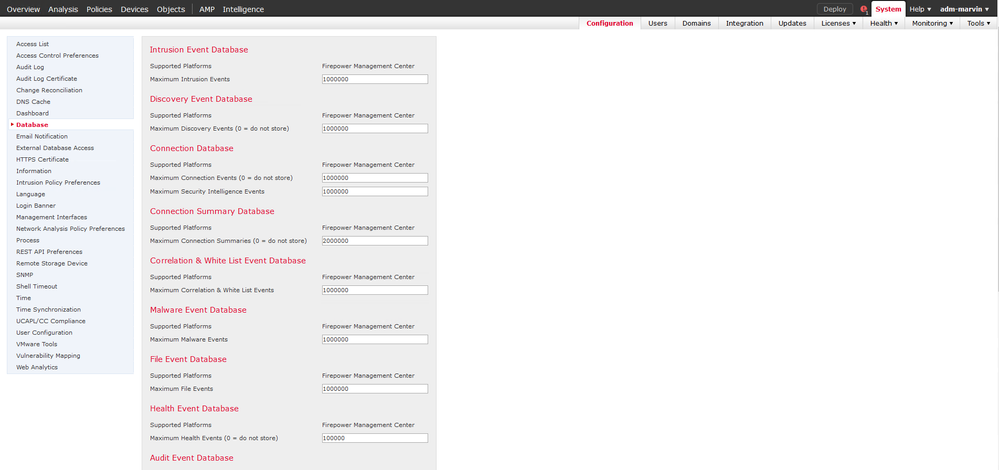
By default the system divides up the available database storage space to favor security-related logs vs pure connection events. You can see the settings as follows:
Each FMC platform has different capacity to store logs. The data sheets list that specification.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide