- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Need expert help with Firepower intervlan routing
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2024 09:18 AM
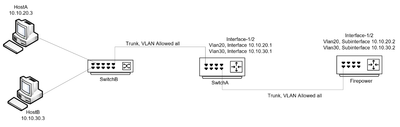
(FP)Firepower 1000 has routed sub-interfaces as shown in diagram. HostA is able to ping HostB, and vice-versa. FP Vlan20 responds to ping request from HostA. FP Vlan30 responds to ping request from HostB. All works with the following exception, FP Vlan30 does not respond to ping request from HostA; and FP Vlan20 does not respond to ping request from HostB. (no nat; basic ACL allow all). So 2-questions,
Is this normal for FTD?
And is it possible to configure FP 1/3 interface as an L3 virtual bridge on a switchport or trunk and associating the 1/3 Interface with the 1/2 Interface, then connecting the1/3 Interface to an access port on SwitchA vlan1; to allow tagged and untagged traffic to flow thru FP 1/3 Interface to SwitchA?
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2024 09:37 AM
By "design" you can't ping or reach an interface of the FTD (same behaviour on the ASA devices) that is setting on the opposite side, the exception for this would be if you configure such interface for management over VPN, so what you are seeing is a normal expected behaviour.
Regarding grouping the interfaces to allow the tagged and untagged traffic, you don't need to do that as you had already done it. When you configure the sub-interface you have to associate the VLAN ID as you had already done, which means that for that traffic via those sub-interfaces the traffic must be tagged, however, you can still use the physical interface for the untagged traffic and that would work with the native VLAN that would be configured on the trunk link on the switch. On the other side, if you need more capacity over the existing port then you can configure port channel.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2024 09:51 AM
Omg'
Now it clear to me'
Hosta can ping hostb
But hosta can not ping vlan IP in fw of hostb
This by defualt deny by asa and firepower
No need any config.
The fw not like router that can ping from interface to interface.
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2024 09:37 AM
By "design" you can't ping or reach an interface of the FTD (same behaviour on the ASA devices) that is setting on the opposite side, the exception for this would be if you configure such interface for management over VPN, so what you are seeing is a normal expected behaviour.
Regarding grouping the interfaces to allow the tagged and untagged traffic, you don't need to do that as you had already done it. When you configure the sub-interface you have to associate the VLAN ID as you had already done, which means that for that traffic via those sub-interfaces the traffic must be tagged, however, you can still use the physical interface for the untagged traffic and that would work with the native VLAN that would be configured on the trunk link on the switch. On the other side, if you need more capacity over the existing port then you can configure port channel.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2024 09:51 AM
Omg'
Now it clear to me'
Hosta can ping hostb
But hosta can not ping vlan IP in fw of hostb
This by defualt deny by asa and firepower
No need any config.
The fw not like router that can ping from interface to interface.
MHM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide