- Cisco Community
- Technology and Support
- Security
- Network Security
- OK, so there would be no
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Security context admin via shared interface
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-20-2015 09:50 PM - edited 03-11-2019 11:55 PM
Hi,
we just set a couple of ASA 5520 in security context mode, with :
- system context,
- admin context,
- 2 production contexts.
So far so good.
However, we can't poll via snmp thru the admin context the interfaces that have been configured into the production contexts. Another annoying side effect is the fact that the admin context cannot send syslog messages for events happening in the production contexts.
So every context needs to be polled separatly, and every context sends its own syslog messages.
-> Is it correct or is there a way to manage all contexts (snmp; syslog...) through the admin context ?
At last, we woud like to send all management traffic through the same interface.
For now, eth0/1 is allocated exclusively to admin context.
-> Could we share this interface between contexts, just the way described in the figure below, so that at last all admin traffic from all contexts would be sent to that interface, dedicated to management traffic ? (seems ok but I was wondering about restrictions for interfaces allocated to admin context). What I want to do is share the interface 0/1 between contexts in the same way eth0/0 is shared in the figure below :
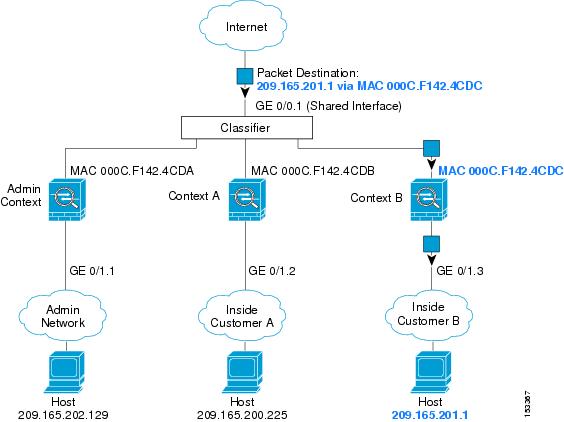
regards,
Pascal
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2015 03:17 AM
Hi,
Yes , you have to configure logging on every context seperately to send the syslogs.
For the 2nd issue , you can share that interface in multiple contexts and send the traffic through.
Refer:-
http://www.cisco.com/c/en/us/td/docs/security/asa/asa90/configuration/guide/asa_90_cli_config/monitor_syslog.html#pgfId-1082019
Thanks and Regards,
Vibhor Amrodia
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2015 03:47 AM
OK, so there would be no problem sharing a standard interface between security contexts and admin contexts.
One step further, would it be possible to share the management interface this way ?
I mean, would it be possible to allocate management interface
- in security context A, IP address 10.1.1.1, mac1 (mac is generared by ios for shared interfaces)
- in security context B, IP address 10.1.1.2, mac2 (...),
- in admin context, IP address 10.1.1.3, mac3 (...)
?
Or is the management interfaces allocated to admin context only ?
Thanks for your input,
Pascal
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
