- Cisco Community
- Technology and Support
- Security
- Network Security
- could you try to issue a
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Trying to configure firewall rule but acl-drop is denied...what is my issue?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2014 08:30 AM - edited 03-11-2019 09:23 PM
I am trying to allow ip 162.213.47.1/24 and Ranges below.
Firewall must allow access to our MarcomCentral® Servers
CIDR Format: 162.213.47.0/24
Netrange Format (Range of IP addresses): 162.213.47.1-254
If desired ports can be restricted to 80 and 443 (required for traffic on internet)
I am trying to get this company PTI that has the 162.213.47.0/24 address's to be able to access our outside network and pass data through.
After setting up the rules I can that I am getting hits so data is moving. However when running a packet trace the acl-drop is denied by the #13 configured rule. I dont understand why my rule isn't working. It should allow those IP's to pass data to our side.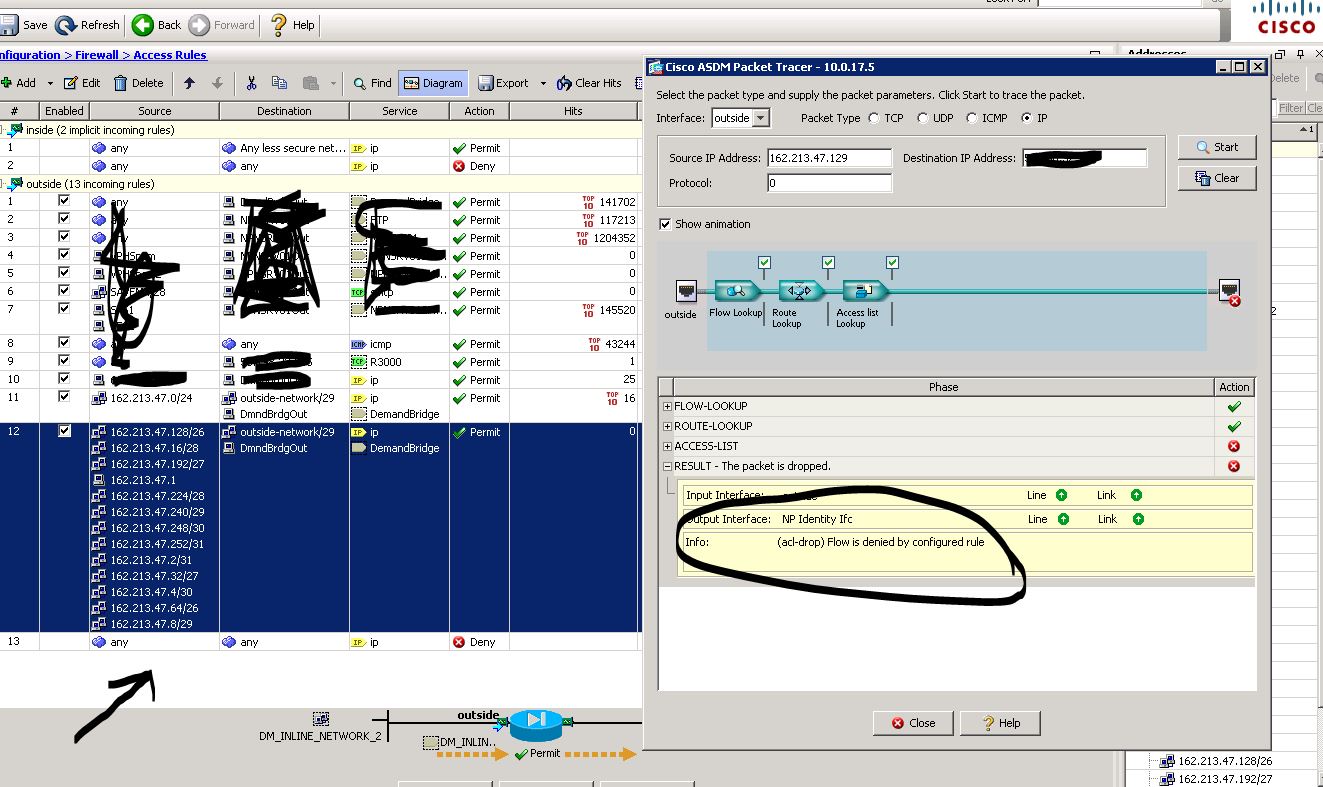
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2014 12:55 PM
could you try to issue a different packet tracer as follows:
packet-tracer input outside tcp 162.213.47.129 1234 <your public IP> 80 detail
If you are trying to allow web access via 80 and 443 to your internal servers, then you need to also make sure that they have static NAT and that the ASA has a route to their subnet if it is not directly connected to the ASA.
--
Please remember to select a correct answer and rate helpful posts
Please remember to select a correct answer and rate helpful posts
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


