- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Unable to start http service on Firepower 2100
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Unable to start http service on Firepower 2100
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2022 11:29 AM - edited 04-11-2022 11:38 AM
Hello,
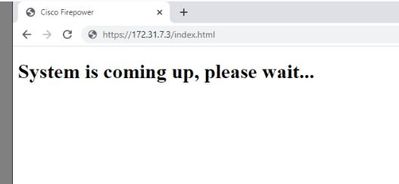
I am trying to start using the firewall 2100 via https, but for some reason I am getting this: System is coming up, please wait...
Also the service is up,
firepower-2110 /system # scope services
firepower-2110 /system/services # show ip-b
Permitted IP Block:
IP Address Prefix Length Protocol
--------------- ------------- --------
172.31.7.0 24 https
172.31.7.0 24 ssh
192.168.45.0 24 https
192.168.45.0 24 ssh
BTW, is it possible to set up this type of ASA using ASDM instead of this new platform?
Any idea?
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2022 01:20 AM
Are you running the ASA image or FTD image on your appliance?
If ASA image it the appliance in platform or appliance mode?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-13-2022 06:52 AM
Hello,
I would like to run the ASA image instead of FTD image on the appliance, I mean continue using the ASDM and conventional CLI.
is it possible?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2022 06:52 AM
Do you know which is running now? If you have FTD and want to switch to ASA you need to reimage the appliance.
https://www.cisco.com/c/en/us/td/docs/security/firepower/quick_start/reimage/asa-ftd-reimage.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2022 03:19 PM
Many thanks for your time, I really appreciate it.
I was able to reimage the FTD -> ASA, following the link that you shared,
But, for some reason I am not able to start the ASDM, I can ping the ASA (inside interface), however it's accessible from the management interface. I checked everything and both inside and management interfaces are configured equally.
UNABLE TO LAUNCH DEVICE MANAGER
Here is the procedure that I executed.
FTD→ASA: Firepower 1000, 2100; Secure Firewall 3100
This task lets you reimage the Firepower 1000 or 2100, or the Secure Firewall 3100 from FTD to ASA. By default, the ASA is in Appliance mode. After you reimage, you can change the ASA to Platform mode.
Note | After performing this procedure, the FXOS admin password is reset to Admin123. |
Procedure
| Step 1 | Make sure the image you want to upload is available on an FTP, SCP, SFTP, or TFTP server connected to the Management 1/1 interface, or a USB drive. For more information about the Management 1/1 interface settings, see the FTD show network and configure network commands in the FTD command reference. | ||||
| Step 2 | Unlicense the FTD.
| ||||
| Step 3 | Connect to the FXOS CLI, either the console port (preferred) or using SSH to the Management 1/1 interface. If you connect at the console port, you access the FXOS CLI immediately. Enter the FXOS login credentials. The default username is admin and the default password is Admin123. If you connect to the FTD management IP address using SSH, enter connect fxos to access FXOS. | ||||
| Step 4 | Download the package to the chassis.
| ||||
| Step 5 | When the new package finishes downloading (Downloaded state), boot the package.
| ||||
| Step 6 | Wait for the chassis to finish rebooting. ASA 9.13 and later (defaults to Appliance mode) The ASA starts up, and you access user EXEC mode at the CLI. Example:[...] Attaching to ASA CLI ... Type help or '?' for a list of available commands. ciscoasa> ASA 9.12 and earlier (defaults to Platform mode) FXOS comes up first, but you still need to wait for the ASA to come up. After the application comes up and you connect to the application, you access user EXEC mode at the CLI. Example:[...] Cisco FPR Series Security Appliance firepower-2110 login: admin Password: Successful login attempts for user 'admin' : 1 Cisco Firepower Extensible Operating System (FX-OS) Software TAC support: http://www.cisco.com/tac Copyright (c) 2009-2018, Cisco Systems, Inc. All rights reserved. [...] User enable_1 logged in to ciscoasa Logins over the last 1 days: 1. Failed logins since the last login: 0. [press Enter to see the prompt below:] firepower-2110# connect asa Attaching to ASA CLI ... Press 'Ctrl+a then d' to detach. Type help or '?' for a list of available commands. ciscoasa> |
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide