- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- How to Configure IPSec VPN Connection between Cisco vEdge and Microsoft Azure
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
04-18-2019 10:08 PM - edited 09-19-2019 12:18 PM
This how-to is a step-by-step guide to configure an IPSec VPN Connection from an on-premise Cisco vEdge device to Microsoft Azure.
⚠️ NOTE: If you are looking for a guide to setup Azure CloudOnramp for IaaS in an automated way via vManage, please see this configuration guide.
Hardware and Software used in this guide
-
vEdge running software version 18.4.0
-
Microsoft Azure account with valid subscription
Prerequisites
vEdge must be fully registered to vBond / vSmart / vManage.
Step-by-step instructions
This guide assumes that the Azure cloud hasn't been configured, some of these steps can be skipped if the resources are already established.
Configuring a VPN Gateway in Azure
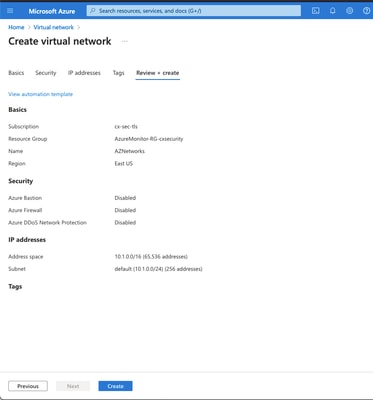
Create a virtual network (VNET) in Azure. The address space should ideally not overlap with any other subnets you have in use anywhere else in your network. Also create a first subnet within the virtual network. In this example we use 10.1.0.0/16 as the address space for the entire VNET and 10.1.0.0/24 for the first subnet. The names for the VNET and the subnet are arbitrary.
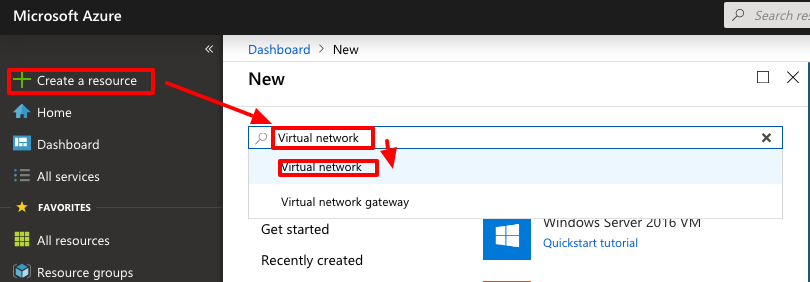
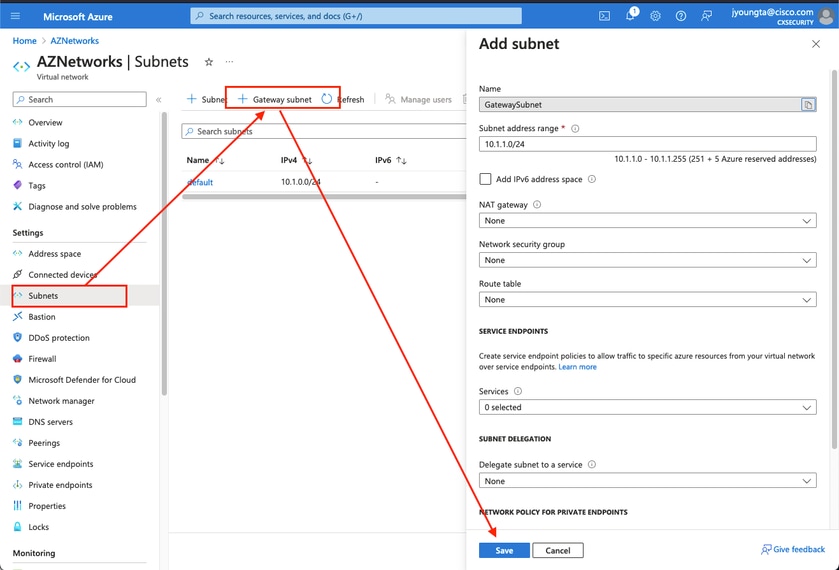
Create a so called "Gateway Subnet" inside the new VNET. The Gateway Subnet can be of size /27 to conserve IP address space.
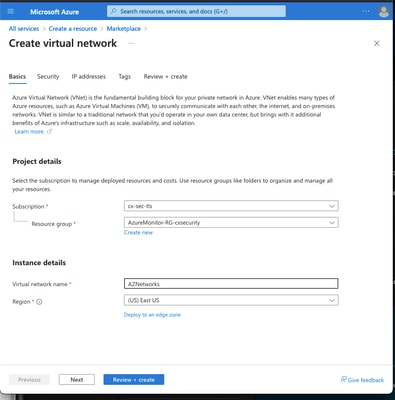
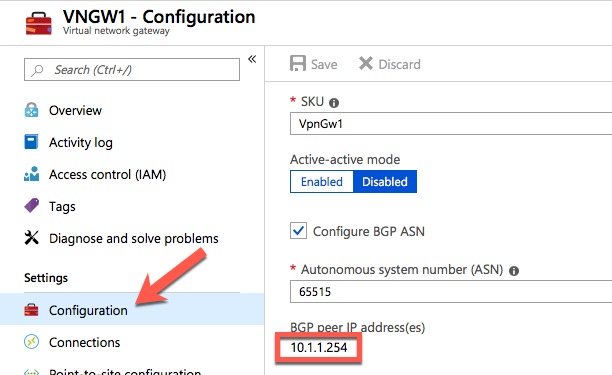
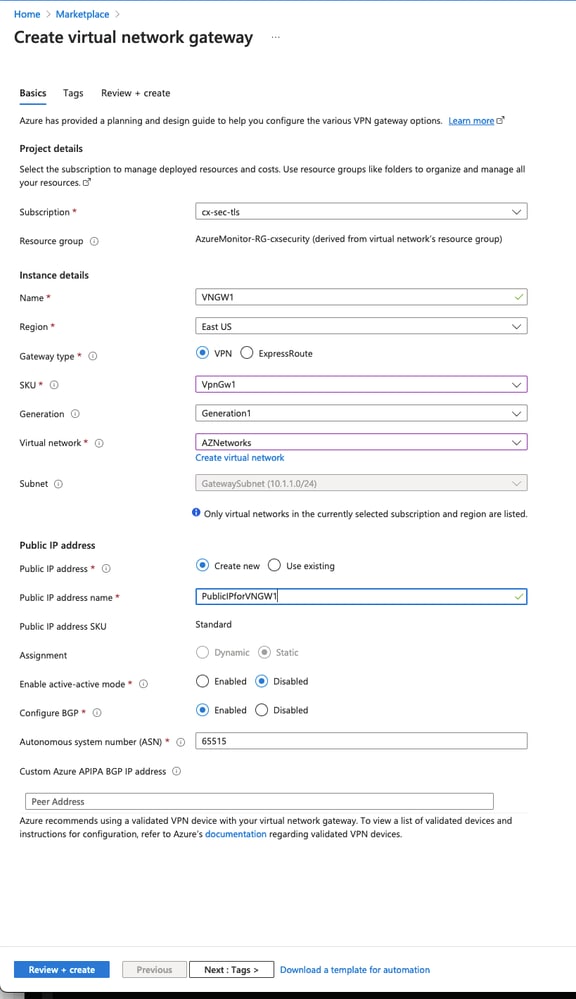
Create a virtual network gateway. This is the VPN endpoint inside Azure to which your vEdge will establish the IPSec connection.
| Parameter | Description |
|---|---|
| Name | Arbitrary name for this virtual network gateway |
| Gateway Type | Select VPN to enable IPSesc |
| VPN Type | Select Route-based which should generally be preferred over policy-based (crypto-map) VPNs. |
| SKU | Need to select VpnGw1 or greater based on the amount of traffic needed. Basic doesn't support BGP |
| Enable active/active mode | Disable. This how-to does currently not support active/active mode. |
| Public IP address | Create a new public IP address |
| Configure BGP ASN | Enable BGP |
| Autonomous system number (ASN) | Leave this as the default 65515. This is the ASN Azure presents itself as. |
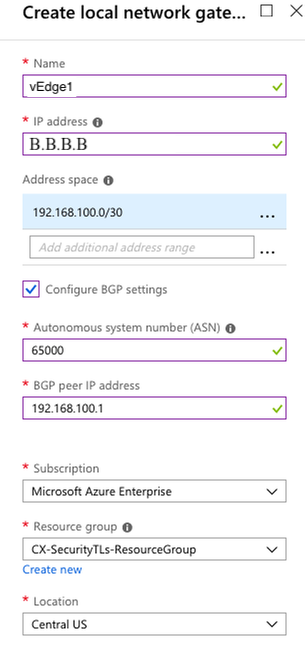
Create a local network gateway. The local network gateway represents your vEdge.
| Parameter | Description |
|---|---|
| Name | Arbitrary name for your local vEdge |
| IP Address | Public IP address of your vEdge |
| Address Space |
Address space for the tunnel interface |
| Configure BGP Settings | Check to enable BGP |
| ASN | ASN configured on the vEdge |
| BGP peer IP address | IP address on the vEdge which terminates the BGP connection |
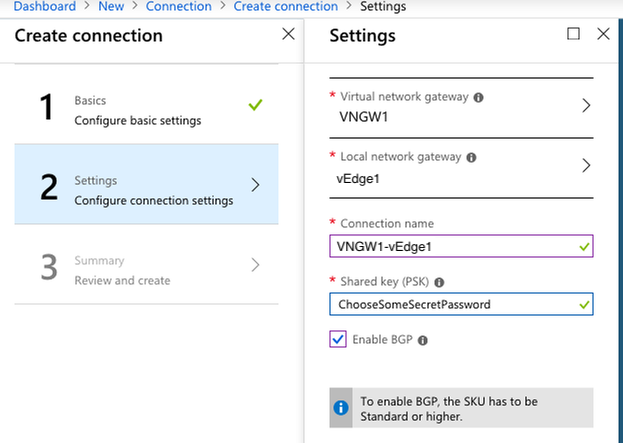
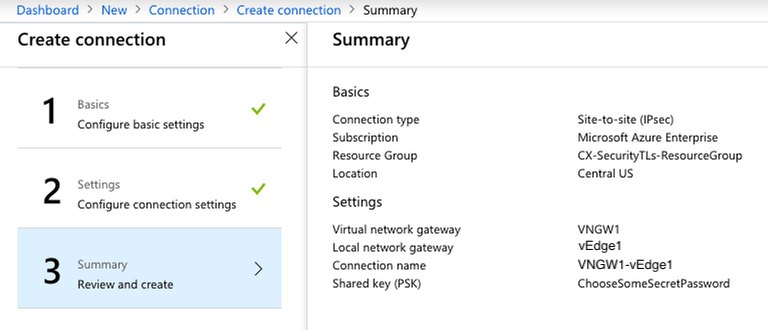
Create a new connection between the virtual network gateway and the local network gateway.
Configure vEdge
Retrieve the public IPv4 address of the virtual network gateway in Azure.
Login to your vEdge to create & configure the IPSec interface.
The tunnel source interface (ge0/0 in the example below) needs to be the WAN facing interface which is configured with the public IP (i.e. B.B.B.B in the case of this how-to). It needs to be reachable from the Azure virtual network gateways public IP (i.e. from A.A.A.A in the case of this how-to).
vedge1# config
vedge1(config)# vpn 0 interface ipsec1
vedge1(config-interface-ipsec1)# ip address 192.168.100.1/30
vedge1(config-interface-ipsec1)# tunnel-source-interface ge0/0
vedge1(config-interface-ipsec1)# tunnel-destination A.A.A.A
vedge1(config-interface-ipsec1)# mtu 1400
vedge1(config-interface-ipsec1)# tcp-mss-adjust 1350
vedge1(config-interface-ipsec1)# no shutdown
Configure the IKE Version 2 parameters.
vedge1(config)# vpn 0 interface ipsec1 ike
vedge1(config-ike)# version 2
vedge1(config-ike)# group 2
vedge1(config-ike)# cipher-suite aes256-cbc-sha2
vedge1(config-ike)# rekey 86400
vedge1(config-ike)# authentication-type pre-shared-key pre-shared-secret ChooseSomeSecretPassword
vedge1(config-pre-shared-key)# local-id B.B.B.B
vedge1(config-pre-shared-key)# remote-id A.A.A.A
Configure IPsec tunnel parameters.
vedge1(config)# vpn 0 interface ipsec1
vedge1(config-interface-ipsec1)# ipsec
vedge1(config-ipsec)# cipher-suite aes256-cbc-sha1
vedge1(config-ipsec)# replay-window 512
Retrieve the IP address of the BGP router in Azure.
Create a static route to reach the BGP router in Azure from vEdge.
vedge1(config)# vpn 0
vedge1(config-vpn-0)# ip route 10.1.1.254/32 192.168.100.2
Configure BGP on vEdge.
vedge1(config)# vpn 0 router bgp 65000
vedge1(config-bgp-65000)# neighbor 10.1.1.254 remote-as 65515 ebgp-multihop 255 update-source ipsec1
vedge1(config-neighbor-10.1.1.254)# address-family ipv4-unicast
vedge1(config-address-family-ipv4-unicast)# exit
vedge1(config-neighbor-10.1.1.254)# exit
vedge1(config-bgp-65000)# address-family ipv4-unicast
Commit all changes on vEdge and exit configuration mode.
vedge1(config)# commit
vedge1(config)# end
Verify
Perform the following steps to verify the IPSec tunnel on vEdge
Verify the ipsec1 interface is in up/up state and receiving / transmitting packets.
vedge1# show interface | include ipsec1
0 ipsec1 ipv4 192.168.100.1/30 Up Up NA vlan service 1400 00:00:00:00:00:01 1000 full 1316 0:00:29:28 1943 37
Verify the sate of the IPSec IKE session, check for SPIs and state.
vedge1# show ipsec ike sessions | include ipsec1
0 ipsec1 2 10.0.0.7 4500 A.A.A.A 4500 d12a70f1676929a3 f447897484c3dd7e aes256-cbc-sha2 2 (MODP-1024) IKE_UP_IPSEC_UP 0:00:33:59
Verify that the BGP connection is established.
vedge1# show bgp summary vpn 0
vpn 0
bgp-router-identifier 1.1.1.9
local-as 65000
rib-entries 4
rib-memory 448
total-peers 1
peer-memory 4816
Local-soo SoO:0:600
ignore-soo
MSG MSG OUT PREFIX PREFIX PREFIX
NEIGHBOR AS RCVD SENT Q UPTIME RCVD VALID INSTALLED STATE
---------------------------------------------------------------------------
10.1.1.254 65515 23 22 0 0:00:18:32 3 3 3 established
Verify that BGP is receiving routes from Azure.
vedge1# show ip routes vpn 0 bgp
Codes Proto-sub-type:
IA -> ospf-intra-area, IE -> ospf-inter-area,
E1 -> ospf-external1, E2 -> ospf-external2,
N1 -> ospf-nssa-external1, N2 -> ospf-nssa-external2,
e -> bgp-external, i -> bgp-internal
Codes Status flags:
F -> fib, S -> selected, I -> inactive,
B -> blackhole, R -> recursive
PROTOCOL NEXTHOP NEXTHOP NEXTHOP
VPN PREFIX PROTOCOL SUB TYPE IF NAME ADDR VPN TLOC IP COLOR ENCAP STATUS
------------------------------------------------------------------------------------------------------
0 10.1.0.0/16 bgp i - 10.1.1.254 - - - - F,S,R
0 192.168.100.0/30 bgp i - 10.1.1.254 - - - - -
0 192.168.100.1/32 bgp i - 10.1.1.254 - - - - -
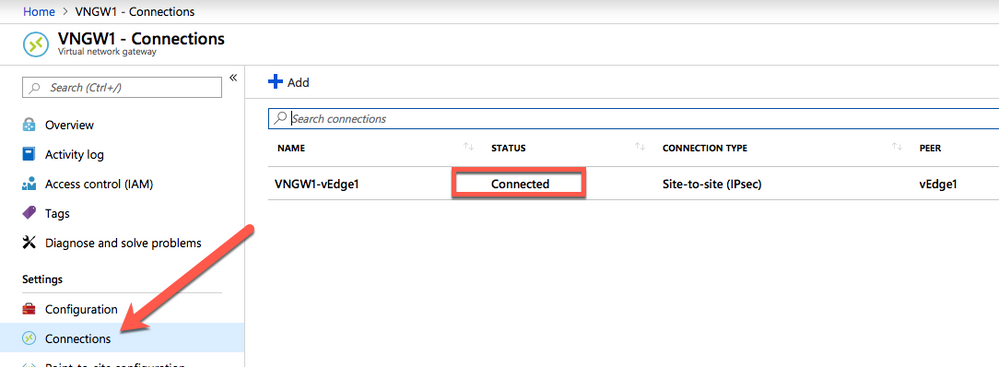
Perform the following steps to verify the IPSec tunnel in Azure
Check the status of the connection to vEdge in the virtual network gateway
References
Please see these links for additional information:
- https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-about-vpn-devices
- https://sdwan-docs.cisco.com/Product_Documentation/Software_Features/Release_18.4/Security/02Configuring_Security_Parameters/Configuring_IKE-Enabled_IPsec_Tunnels
Acknowledgments
For the creation of this how-to the following configuration example was extensively used and a lot of screenshots copied verbatim:
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: