- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- Configuring MACsec Switch to Host with Cat9k & ISE
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 07-20-2021 08:03 AM
Table of Contents
Summary
Requirements
Configuration
1. IBNS 2.0
2. Switch \ RADIUS Config
3. AAA Config
4. IBNS Policy Map
5. SwitchPort
6. ISE Results Policy
7. ISE Policy
Summary
MACsec is IEEE standard 802.1AE. It was developed by the IEEE to compliment the 802.1X-2004 standard. MACsec was developed to allow authorized systems to connect and then encrypt data that is transmitted across the wire and to keep a man-in-the-middle from being able to insert frames onto the wire. Some businesses and government entities are required to protect data while it is at rest and while it is in transit and all organizations should protect that data. MACsec does not authorize the systems connecting to the network, that's 802.1x responsibility; MACsec enables those systems to encrypt traffic destined for the network. MACsec is for use on wired networks only. Cisco supports Switch to Host MACsec with MKA on Catalyst 9200, 9300, 9400, 9500, 9600, and on 3650 and 3850. Cisco recommends that all new MACsec implementations use MACsec Key Agreement (MKA).
This is one of several MACsec documents I'm writing. For questions about terminology please see this document.
Please comment if you have questions or concerns!
Requirements
Basic knowledge of ISE policies
Basic knowledge of 802.1x
Basic knowledge of 802.1x authentication, supplicant
Basic knowledge of AnyConnect NAM
Configuration
All of this is being performed on a switch that is in a lab environment. Please, please do this in a lab before doing it in production.
1. IBNS 2
While this is supported in IBNS 1, in this example I am using IBNS 2. This is a newer method of configuring 802.1x policies that offer more flexibility and easier configuration once you get over the hurdle of learning classes, class-maps, policy-maps, and service-policies. In IOS XE lingo IBNS 1 is called legacy and IBNS 2 is called new style or eEdge.
Here is an awesome document for learning more about IBNS 1 vs. IBNS2.
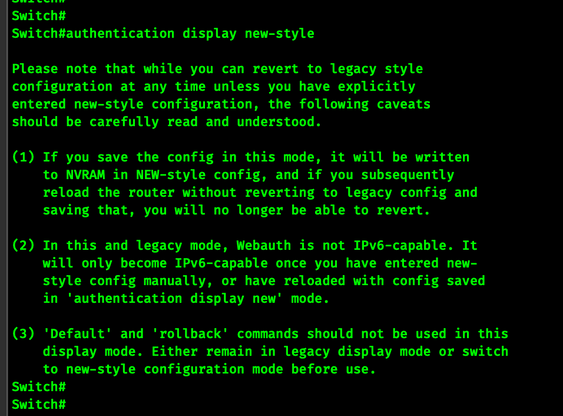
Enable IBNS 2 using the following command in EXEC mode.
authentication display new-style
When you enter this command you will be given a one-time warning! Please, please read it and understand the ramifications of enabling IBNS 2. There is no going back once you start configuring IBNS 2. Also if you have 802.1x authentication already configured on your switch it will be converted to IBNS 2 format, which can be a bit messy.
Sometime in the near future, I will likely write another document for an IBNS 1.0 config but for now, we will keep going.
2. Configuring the switch to look at ISE for RADIUS
Here we will configure two ISE PSNs. We will use the friendly name ise-psn1 and ise-psn2. We will use the automate-tester command to send 'test' RADIUS authentications to the PSN in order to make verify it is still alive. Finally, we will create a AAA group with the friendly name ISE-RADIUS and configure it to contain both the ISE PSNs.
!
username RADIUS-TEST password cisco123
!
radius server ise-psn1
address ipv4 192.168.10.22 auth-port 1645 acct-port 1646
automate-tester username RADIUS-TEST ignore-acct-port idle-time 10
key radius-shared-secret
!
radius server ise-psn2
address ipv4 192.168.10.23 auth-port 1645 acct-port 1646
automate-tester username RADIUS-TEST ignore-acct-port idle-time 10
key radius-shared-secret
!
aaa group server radius ISE-RADIUS
server name ise-psn1
server name ise-psn2
!
3. Configuring the switch for AAA
We need to configure the switch for AAA RADIUS so that it can perform two functions, dot1x and MACsec encryption.
!
aaa authentication dot1x default group ISE-RADIUS
aaa authorization network default group ISE-RADIUS
aaa accounting update newinfo periodic 2880
!
aaa server radius dynamic-author
client 192.168.10.22 server-key radius-shared-secret
client 192.168.10.23 server-key radius-shared-secret
!
4. Configuring the IBNS 2 Policy Map
Ok, not everyone that uses dot1x is using IBNS 2. If you are not, I'd encourage you to consider it. It is 'the new way' of doing things that adds a lot of functionality to the authentication process. It's also likely that cutting-edge features will appear in IBNS 2 first.
This may look big bad and scary but it's actually pretty easy to follow the logic.
The Policy-Map has the friendly name DOT1X_MAB_SHOULD_SECURE. This script will be applied to the switchport with a service-policy.
Let's take a look a the policy map.
In the first event named session started we start both dot1x and mab processes. This tells the switch to run both processes at the same time, this helps the endpoint get onto the network faster than if they had to wait for dot1x to fail before starting the MAB process.
The second event is for violations. Documentation on event violations is sparse, if \ when I find some I will add it here.
The third event, agent-found, comes into effect when EAP messages are received from the endpoint. This indicates the endpoint has an 802.1x supplicant configured. In cases where the endpoint is participating in 802.1x, we stop the MAB process and force .1x authentication.
The fourth event, authentication failure has two classes. Basically, if the AAA is down, the RADIUS server is unavailable just authorize the endpoint onto the switchport and stop the process. This is a fail-open method. The second class in this event is hit if the endpoint has a supplicant but they do not successfully authenticate. In that event, they will be authenticated using MAB.
The fifth event, remote authentication successful is hit when the ISE sends the ACCESS-ACCEPT attribute to the switch. In that event, the switch calls a default service template called DEFAULT_LINKSEC_POLICY_SHOULD_SECURE. This template and several other service templates are installed into the running configuration when you enable IBNS 2.
!
policy-map type control subscriber DOT1X_MAB_SHOULD_SECURE
event session-started match-all
10 class always do-all
10 authenticate using dot1x priority 10
20 authenticate using mab priority 20
event violation match-all
10 class always do-all
10 restrict
event agent-found match-all
10 class always do-until-failure
10 terminate mab
20 authenticate using dot1x priority 10
event authentication-failure match-all
10 class AAA-DOWN do-all
10 authorize
20 activate service-template CRITICAL
30 terminate dot1x
40 terminate mab
20 class DOT1X-FAILED do-all
10 authenticate using mab
event remote-authentication-success match-all
10 class always do-until-failure
10 activate service-template DEFAULT_LINKSEC_POLICY_SHOULD_SECURE
!
5. Configuring the Switchport
If you are familiar with 802.1x configuration on a switchport you will be familiar with all this configuration except for maybe the macsec command and the service-policy command.
On this switchport we are enabling authentication, IBNS 2 uses access-session instead of authentication for most commands, we enable MAB, we configured the Port Access Entity (PAE) to operate in Authenticator mode, enable some endpoint spanning tree protection and the SHOULD_SECURE policy from the policy-map we created in the previous step.
You may notice I've configured this switchport as an access port but I have not configured a VLAN. This is because I'm using ISE to dynamically assign a VLAN to the switchport. We will see how to do that in a later step.
!
interface GigabitEthernet1/0/21
description Link to Windows 10 with AnyConnect
switchport mode access
macsec
authentication periodic
authentication timer reauthenticate server
access-session host-mode multi-domain
access-session closed
access-session port-control auto
mab
dot1x pae authenticator
dot1x timeout tx-period 10
spanning-tree portfast
spanning-tree bpduguard enable
service-policy type control subscriber DOT1X_MAB_SHOULD_SECURE
!
It's important to note the host modes. There are four options and only 3 are supported with MACsec.
* single-host - only one MAC address is allowed on the switchport
* multi-domain - one MAC address in Data Domain and one MAC address in Voice Domain
* multi-auth - this is NOT supported with MACsec
* multi-host - multiple MAC addresses in Data Domains, this is NOT recommended because, after the first successful client, authentication is not required for other clients, which is not secure.
6. Configuring ISE Results Policy
ISE uses Results Policies to send attributes back to the switch. I'm sending a few attributes, some are mandatory for MACsec, others I'm sending because of different reasons. Read on...
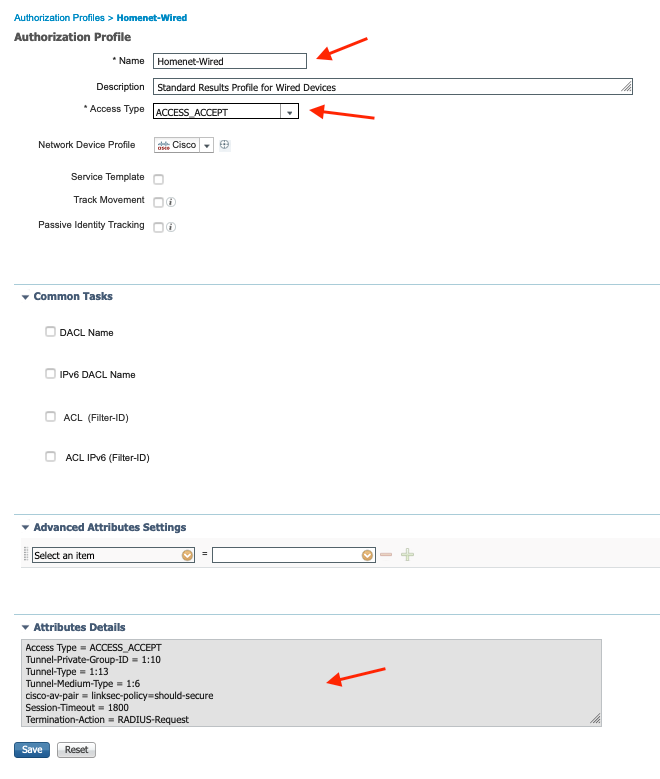
Configure ISE Results Policies here ISE -> Policy -> Policy Elements -> Results -> Authorization -> Authorization Profiles
My AuthZ policy receives a single Results Policy with multiple AV Pairs. I'm sending VLAN: 10, Reauthenticate: 1800, and linksec-policy: Should Secure. Here is what it looks like.
Here is how you configure each of those AV Pairs.
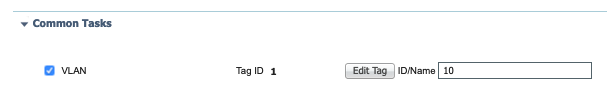
In this Results Profile scroll down to Common Tasks. Inside Common Tasks look for VLAN and add the VLAN you wish to send to the Switch.
Then scroll down a bit more to Reauthentication. Type in a value in seconds that reflects how often you want the workstation to be forced to re-authenticate. In my environment, I use 1,800 seconds or 30 minutes.
Finally, scroll down a bit more to MACsec Policy and select the Should Secure option.
7. Configuring ISE Policy
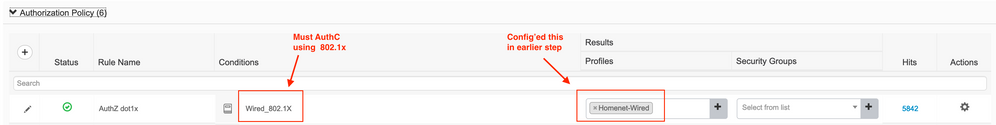
So now we need to apply that Results Profile to a Policy in ISE.
Configure ISE Results Policies here ISE -> Policy -> Policy Sets
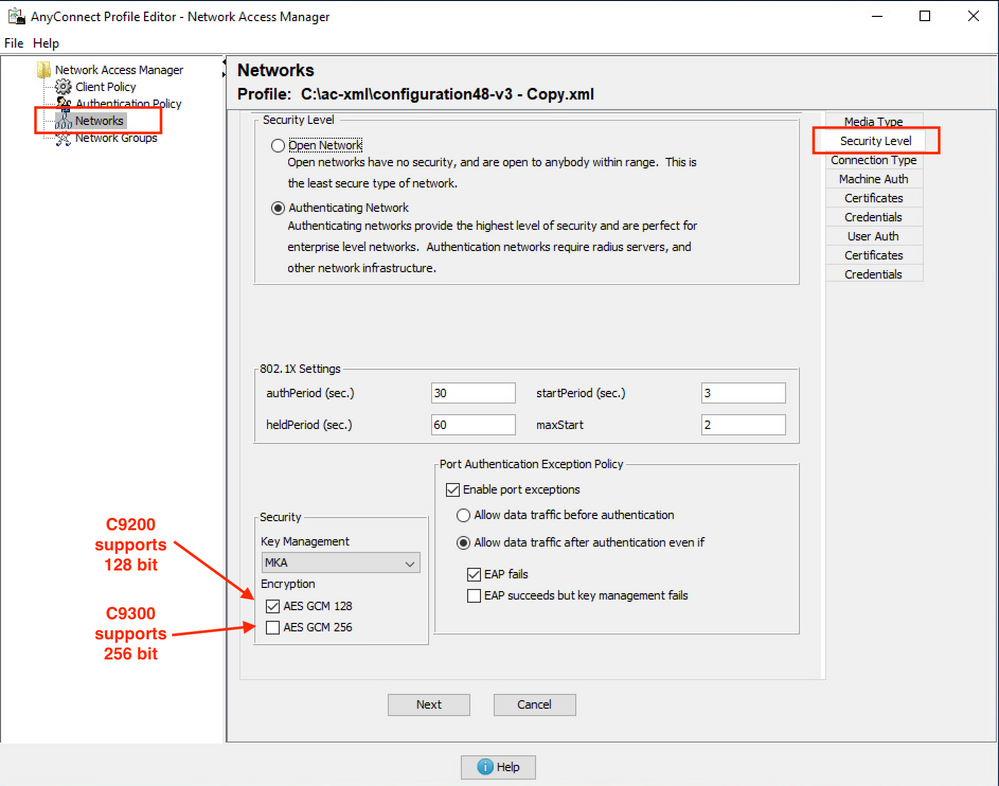
8. Configuring AnyConnect NAM
Cisco AnyConnect Network Access Manager (NAM) works as a 802.1x supplicant, it's also the application that performs the MACsec encryption on the Windows box.
Verification
After completing the steps again your Windows workstation should be securely connected to the network. The commands below will help us assure that it is.
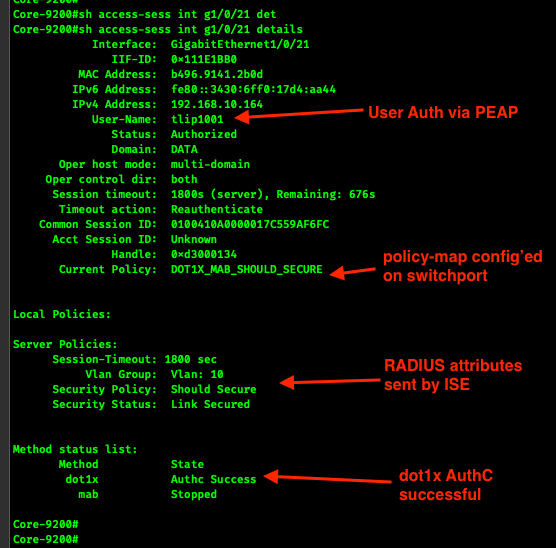
show access-session interface g1/0/21
Check the following items:
Status is Authorized
Server Policies, Security Status is Link Secured
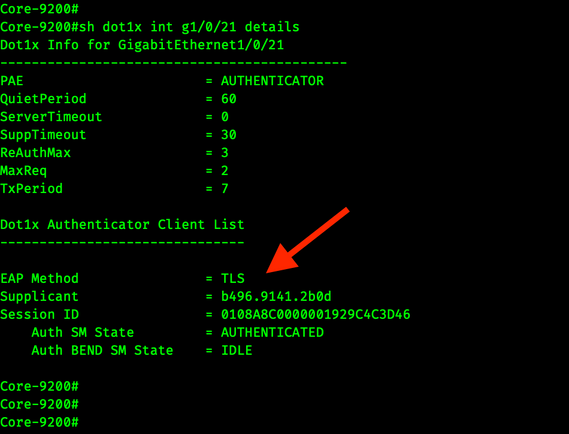
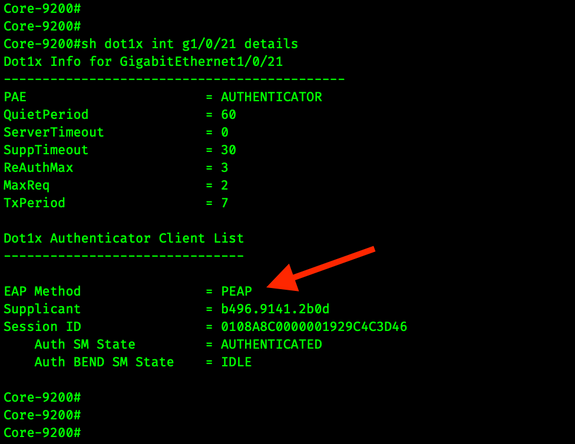
sh dot1x int g1/0/21 details
This screenshot shows the workstation using Machine Auth via EAP-TLS
In my lab config, user authentication is occurring over PEAP. We can confirm that by using that same command.
sh logging
I've added some line breaks to the logs for readability.
Feb 5 00:18:47.117 EST:
%MKA-5-SESSION_START: (Gi1/0/21 : 2)
MKA Session started for RxSCI b496.9141.2b0d/0000,
AuditSessionID 0100410A0000017E70A07F64,
AuthMgr-Handle 21000081
Feb 5 00:18:51.140 EST: %MKA-5-SESSION_SECURED: (Gi1/0/21 : 2)
MKA Session was secured for RxSCI b496.9141.2b0d/0000,
AuditSessionID 0100410A0000017E70A07F64,
CKN D93657DE9B96C60FACC80349F449EC10
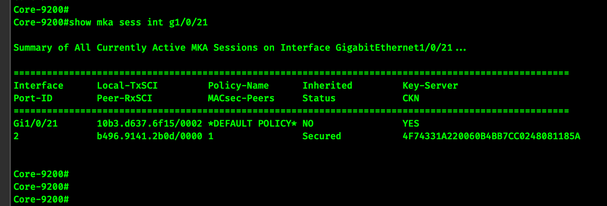
show mka session interface g1/0/21
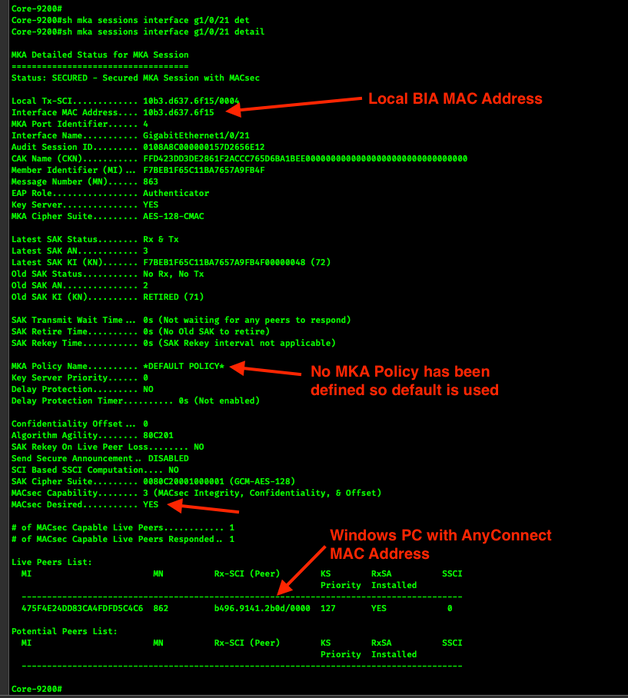
show mka session interface g1/0/21 detail
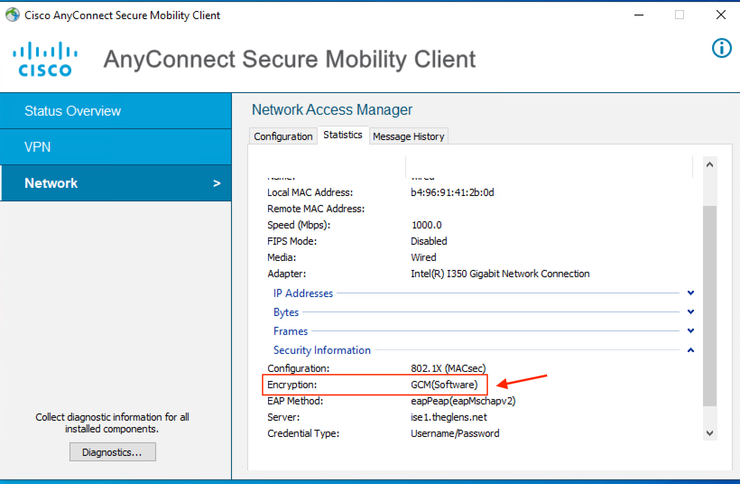
Check AnyConnect and assure Encryption: GCM (Software) is enabled.
Troubleshooting
Show Policy Map Utilization
show policy-map type control subscriber DOT1X_MAB_SHOULD_SECURE detail
References
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Tim Glen Thank you for this guide!
Quick question, would a configuration like this work if a macsec workstation hangs off of an IP Phone?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Users need to enable 802.1X globally on the switch:
dot1x system-auth-control
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: