- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- SD-Access Fabric Zones
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
08-08-2023 12:30 PM - edited 08-21-2023 09:23 AM
- SD-Access Fabric Zones
- Helpful Notes
- Considerations for Fabric Zone Deployments
- How to Set Up SD-Access Fabric Zones with Fabric Site Creation
- How to Set Up SD-Access Fabric Zones with an Existing Fabric Site
- Helpful Resources
SD-Access Fabric Zones
Cisco Software-Defined Access Fabric Zones play a role in enhancing network segmentation and security. Fabric Zones were introduced in Catalyst Center (formerly known as Cisco DNA Center) version 2.2.3 and refer to logical groupings of network devices within an SD-Access Fabric Site. Because they are a Cisco Catalyst Center construct, there is no minimum IOS-XE requirement to deploy them. We do however recommend checking out the SD-Access Compatibility Matrix to make sure the devices you are using are supported for an SD-Access fabric.
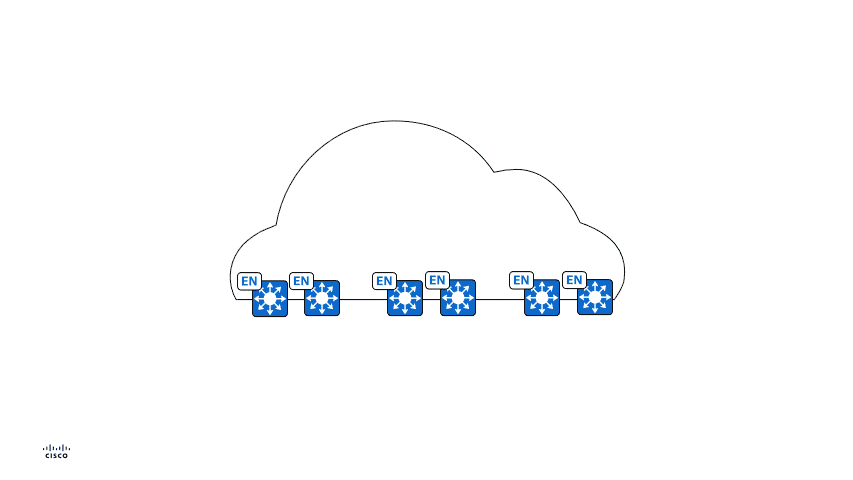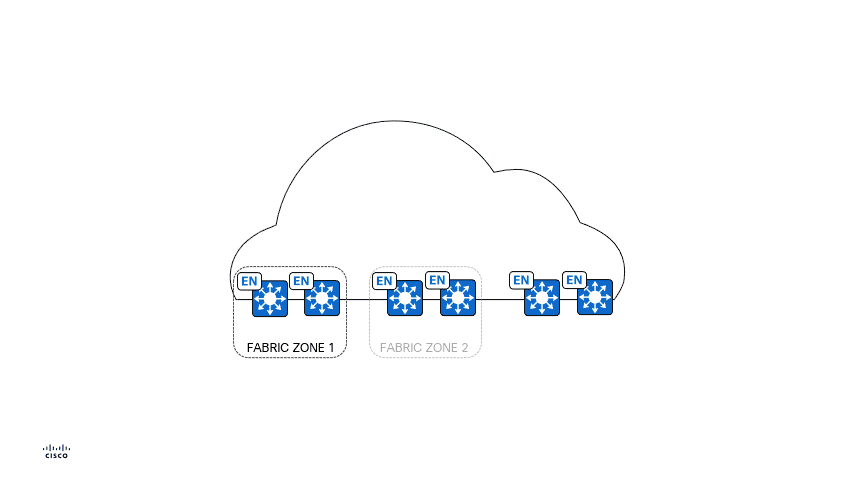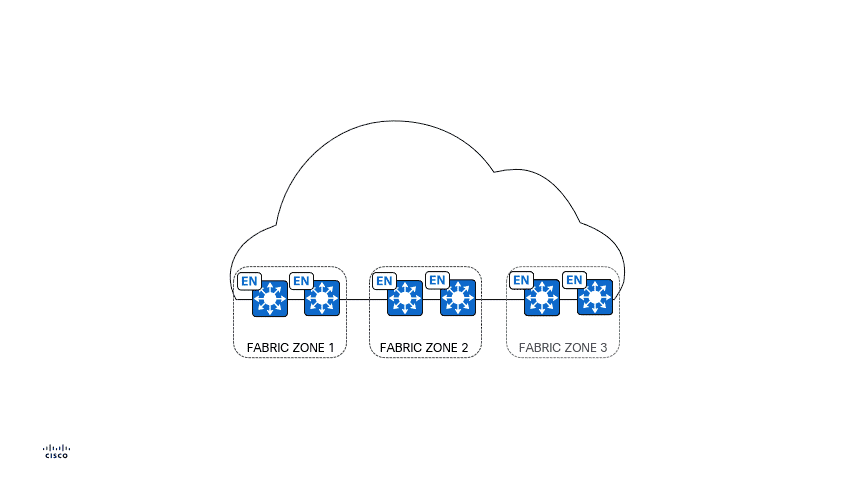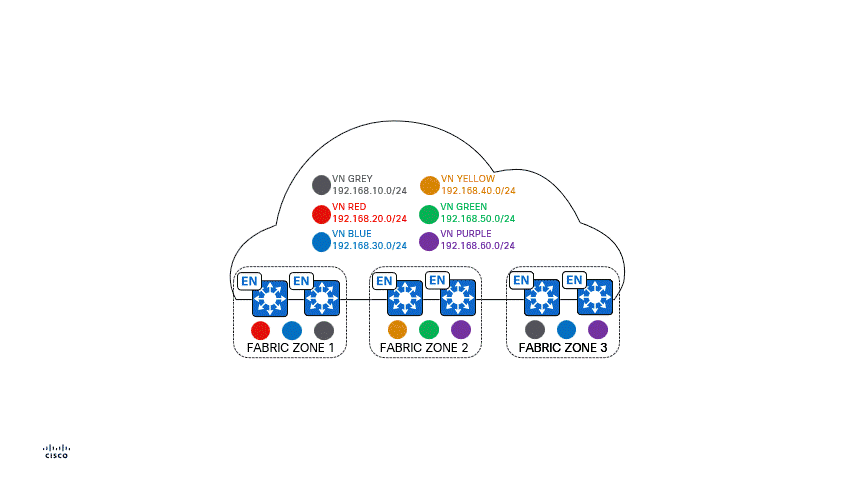
Fabric Zones offer an approach to further your network segmentation journey, and maintain flexibility, by allowing you to restrict your Virtual Networks, or IP Pools, to a contained set of certain Fabric Edge Nodes - refer to the animated GIF below. This concept helps customers who have large-scale deployments of Fabric Edge Nodes in a single fabric site and need a way to manage their network based on smaller locations, or zones. These zones could be multiple buildings, multiple floors within a building, the choice is up to you.
In the below animated GIF, we can take a look at a Fabric Site that has six different Virtual Networks deployed within the Fabric Site - each color represents a different Virtual Network. As we see the Fabric Zones populating, separating Edge Nodes along the way, we can inspect that not every Virtual Network that was deployed to the entire Fabric Site is in each Fabric Zone. For example: VN RED is only located in Fabric Zone 1, but not Fabric Zones 2 and 3. Also VN BLUE is located in Fabric Zones 1 and 3, but not 2. We are able to keep the Virtual Networks we want within a certain set of Edge Nodes and choose where we want the Virtual Networks included.
Helpful Notes
- By default, there is no Fabric Zone created in a Fabric Site.
- Fabric Zones are child sites of a parent Fabric Site
- Fabric Zones can be enabled for Day-0 or Day-N operations (see How to Set Up SD-Access Fabric Zones below).
- For Day-0 operations, Fabric Zones do not have any Virtual Networks, or IP Pools, by default.
- For Day-N operations, Fabric Zones inherit all Layer 3 and Layer 2 Virtual Networks that are mapped to a Fabric Site. An administrator would need to delete the Virtual Network, or IP Pool, which is not needed in the Fabric Zone.
- A Fabric Zone can be created at a building level or a floor level within a Fabric Site.
- A Fabric Zone that is created at a building level will have all the floors within the building part of the same Fabric Zone.
- Fabric Zones must be manually created by the administrator based on their design considerations.
- An IP Pool enabled for wireless needs to be manually added to the Fabric Zone to allow seamless roaming.
- A Fabric Zone is not able to be nested within another Fabric Zone.
Considerations for Fabric Zone Deployments
-
Edge Nodes and Policy Extended Nodes within a Fabric Zone inherit the respective VLANs on the fabric zone.
-
Any IP Pool that is added to an existing Virtual Network in a Fabric Site, and is also anticipated to be used in a Fabric Zone, must be explicitly added to the Virtual Network.
How to Set Up SD-Access Fabric Zones with Fabric Site Creation
Let's set up SD-Access Fabric Zones, assuming you have not created any Fabric Sites yet.
On the Cisco DNA Center dashboard, navigate to the hamburger menu and navigate to Provision > SD-Access > Fabric Sites.
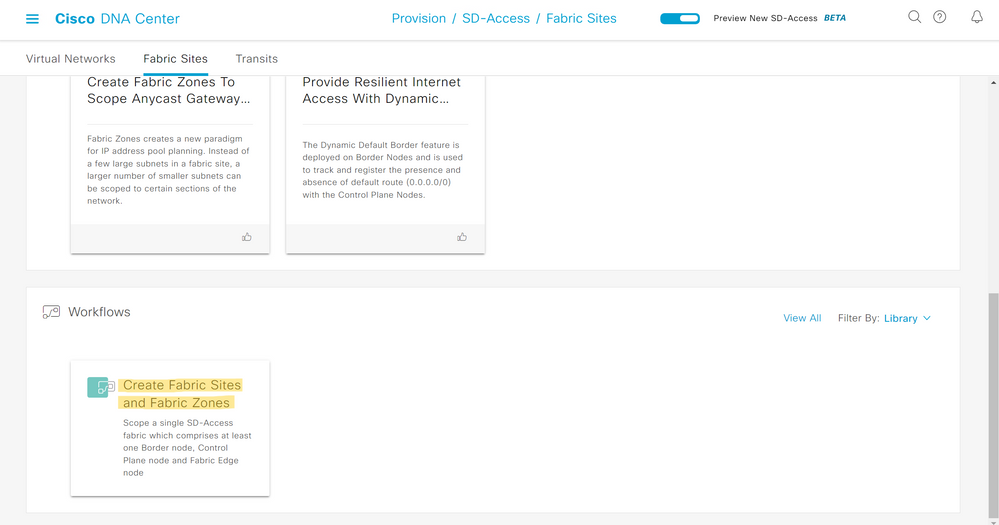
Scroll down to the Workflows section and select "Create Fabric Sites and Fabric Zones".
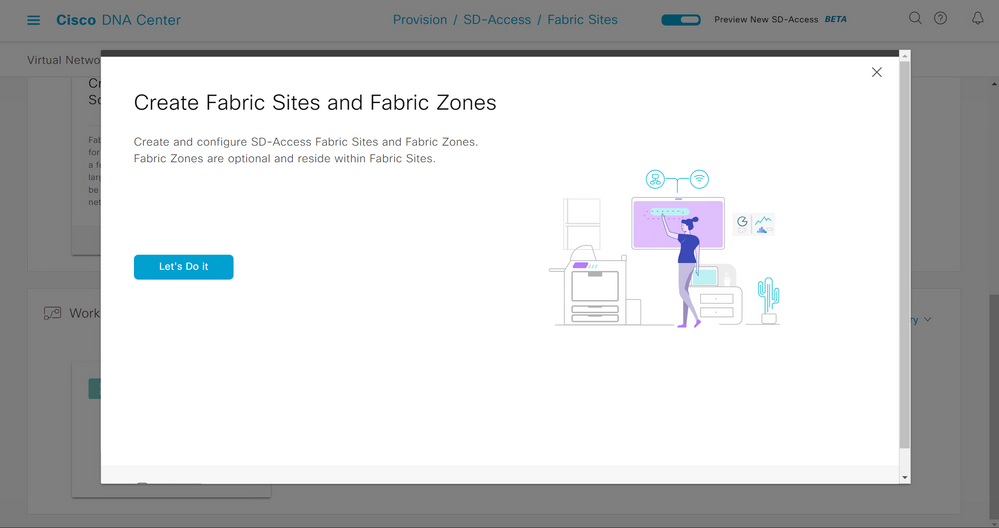
Select Let's Do It.
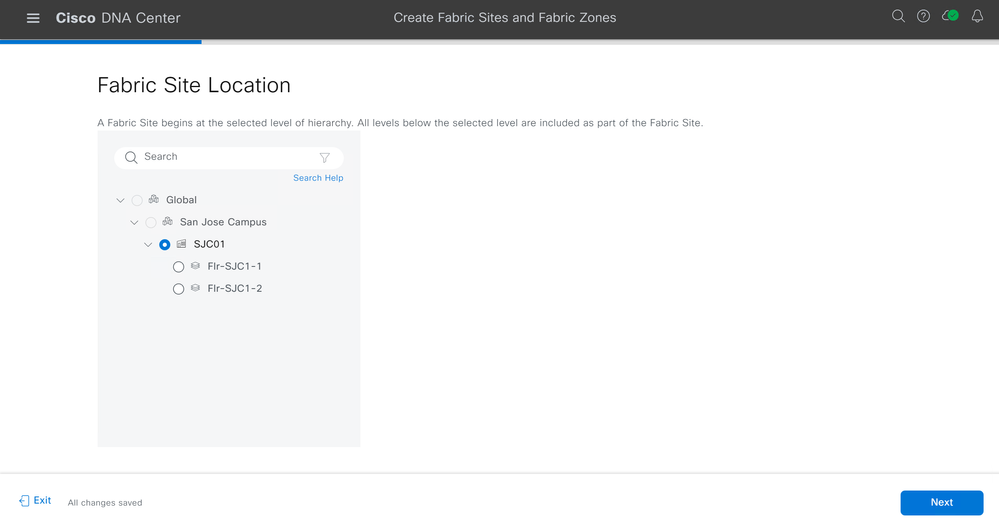
On the Fabric Site Location page, select the building you'd like to designate as a Fabric Site. Click Next.
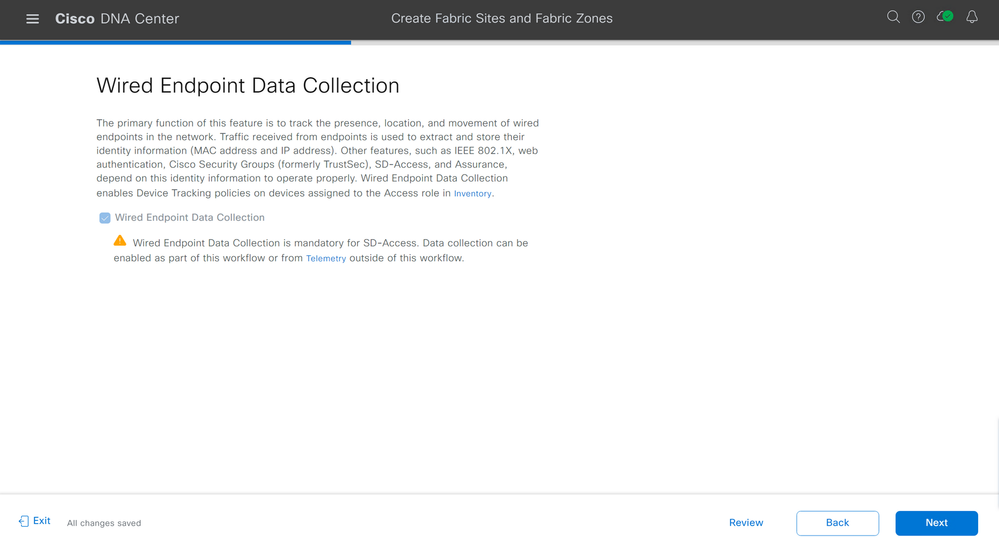
Read through the Wired Endpoint Data Collection page. Click Next.
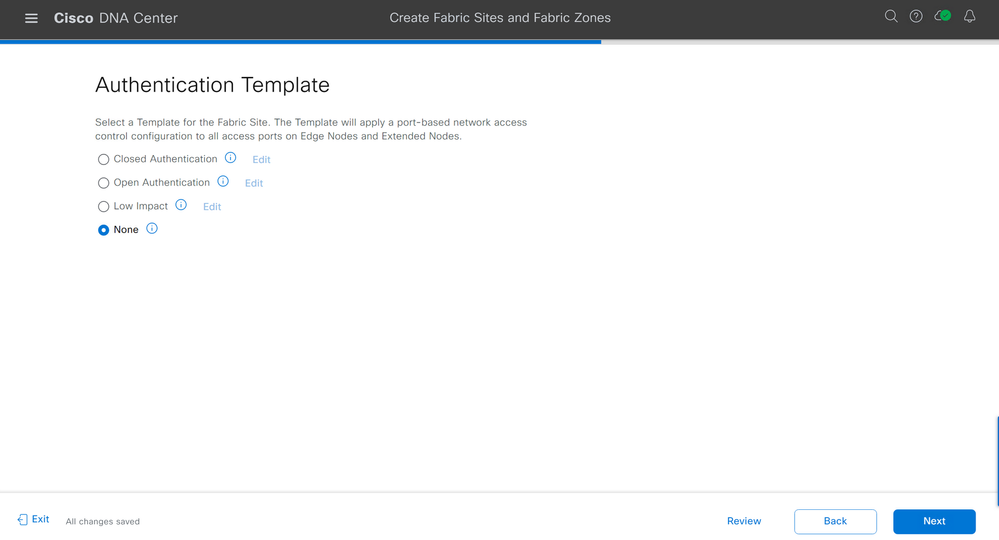
Select the type of authentication you'd like to have for the Fabric Site on the Authentication Template screen. I have selected "None" Click Next.
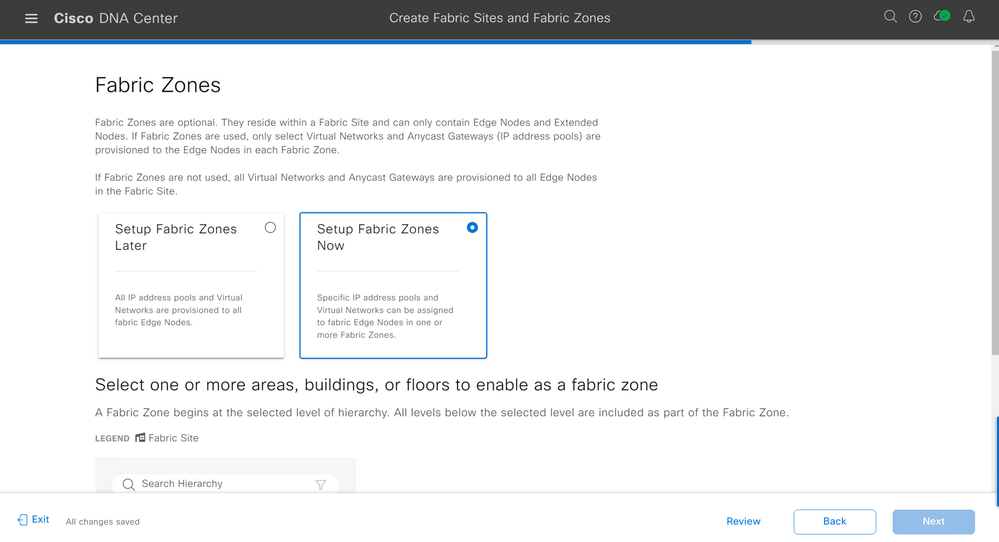
On the Fabric Zones page, select "Setup Fabric Zones Now".
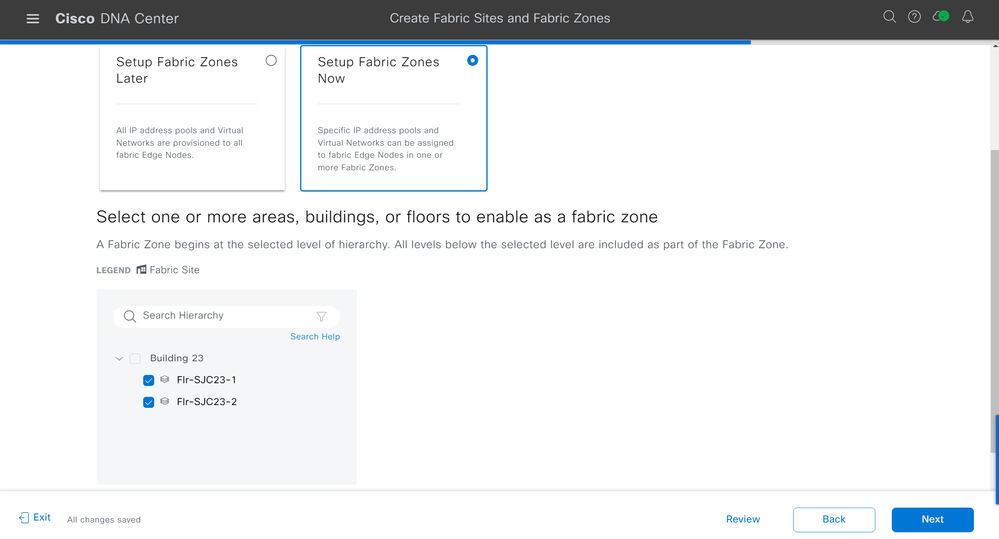
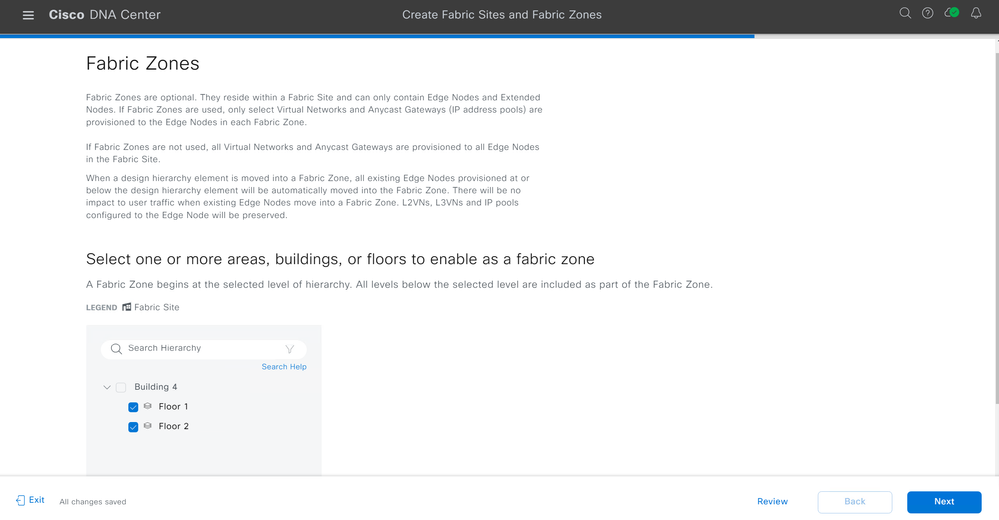
Designate what floors, or building, you would like to be Fabric Zones. Click Next.
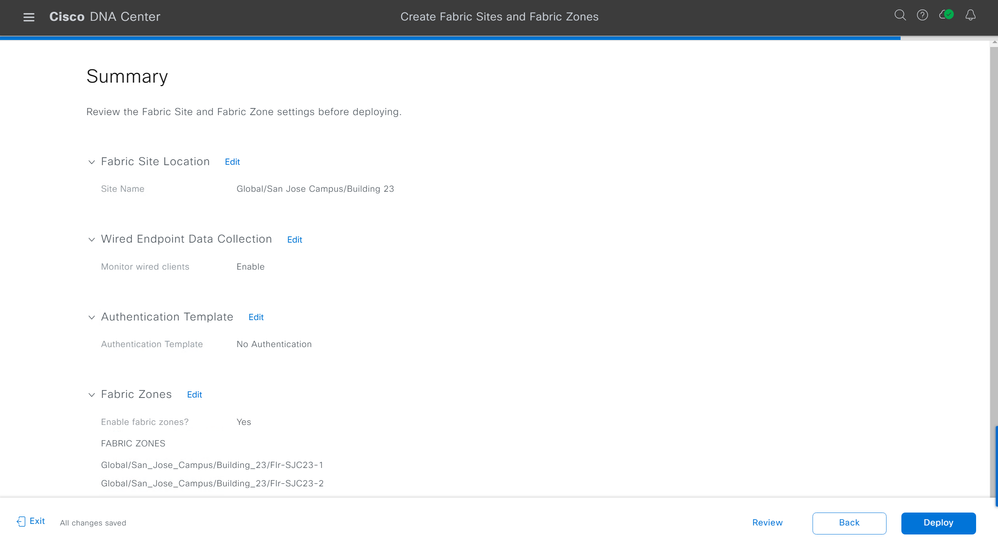
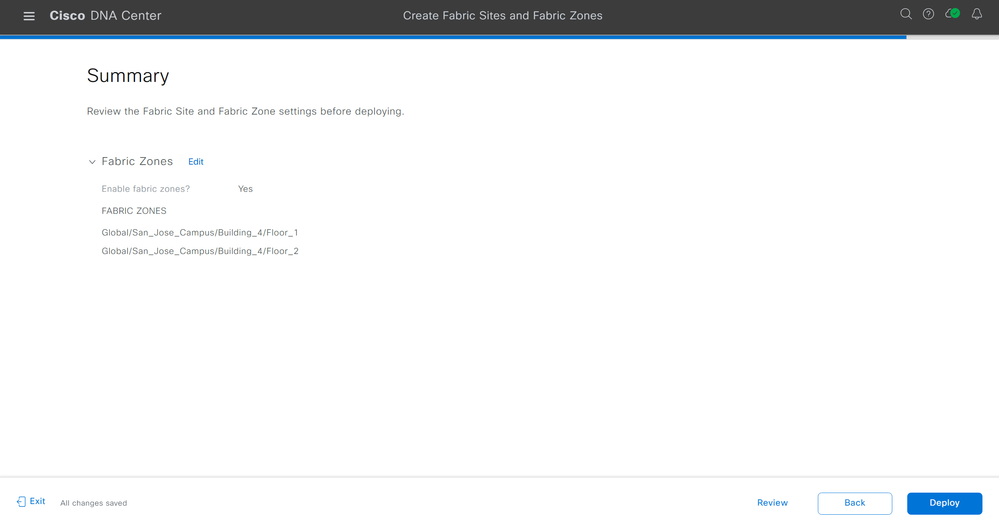
On the "Create Fabric Sites and Fabric Zones" workflow summary page, review your configuration. If you are satisfied with your configuration, click Deploy.
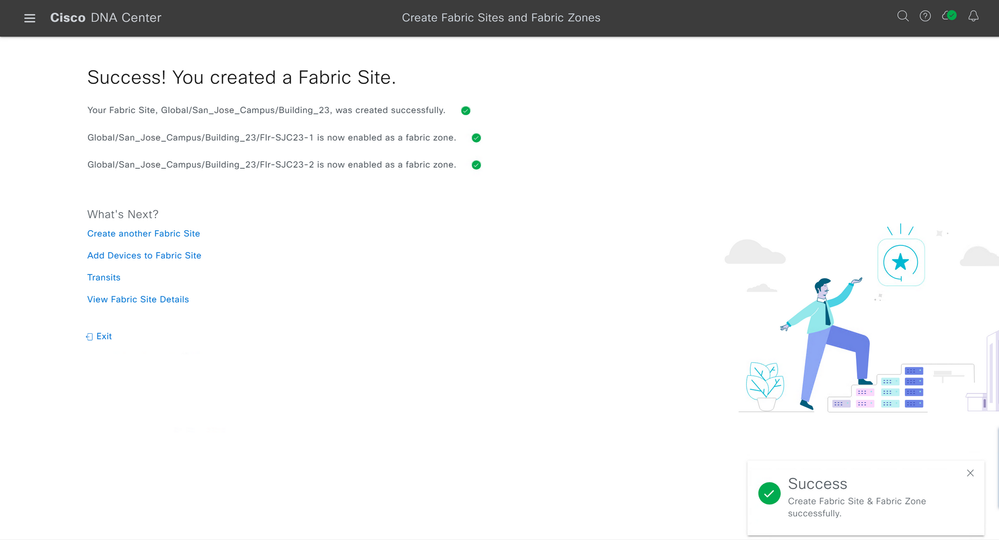
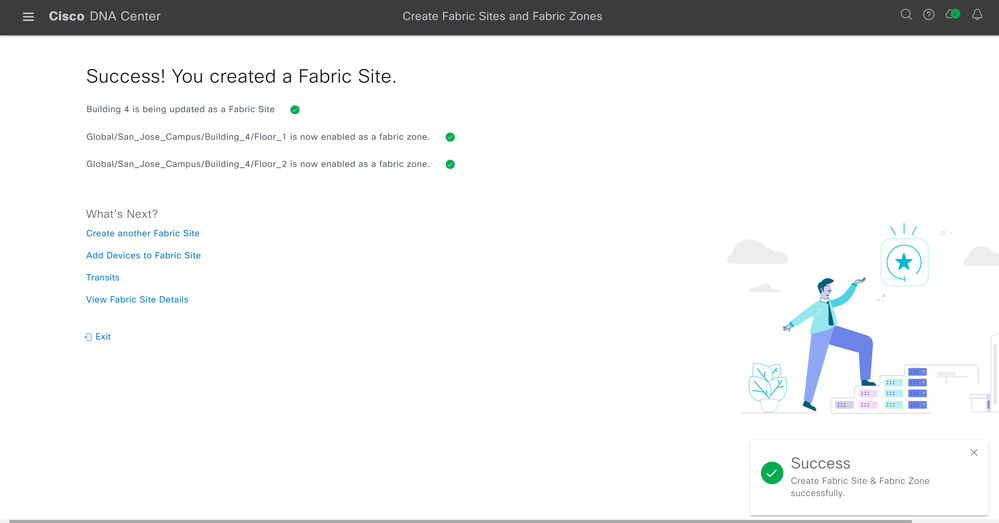
Cisco Catalyst Center will deploy and create your Fabric Site along with any Fabric Zones you have also designated. You will be shown if your deployment was successful.
How to Set Up SD-Access Fabric Zones with an Existing Fabric Site
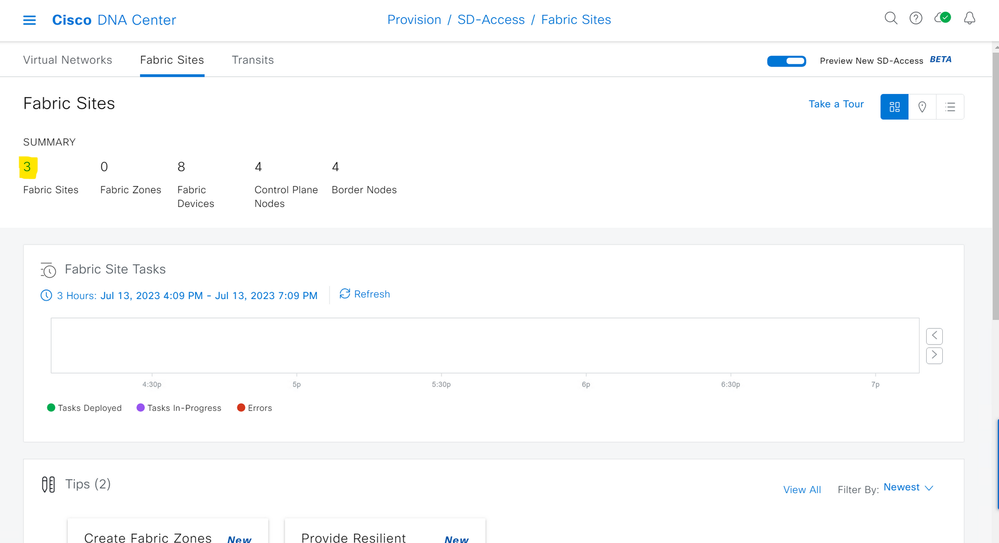
On the Cisco DNA Center dashboard, navigate to the hamburger menu and navigate to Provision > SD-Access > Fabric Sites.
Next, click on the number above Fabric Sites and this will take you to a Fabric Site summary page to view the Fabric Sites you have deployed in your network.
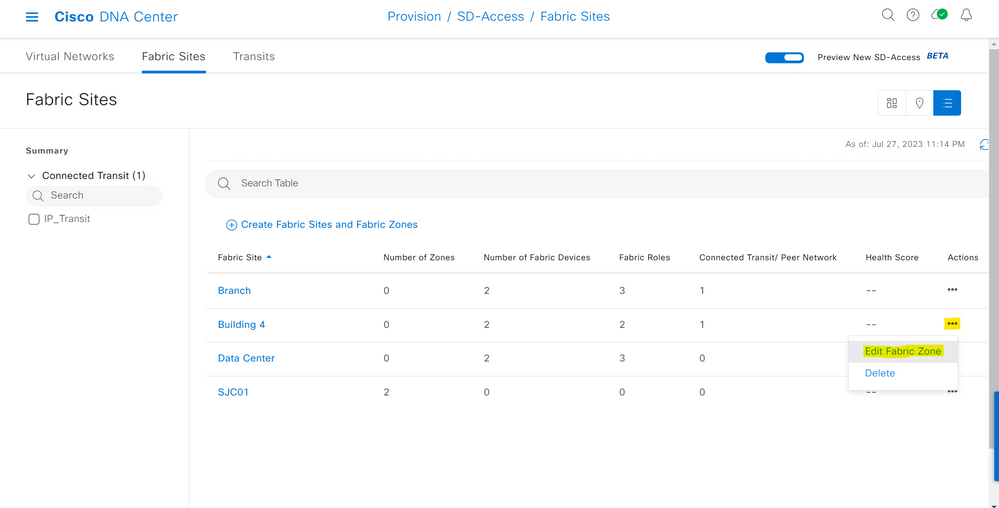
On the Fabric Site summary page, navigate to the Fabric Site you'd like to add Fabric Zones to and hover over the three dots on the right-hand-side. Select "Edit Fabric Zone".
Designate what floors, or building, you would like to be Fabric Zones. Click Next.
On the "Create Fabric Sites and Fabric Zones" workflow summary page, review your configuration. If you are satisfied with your changes, click Deploy.
Cisco Catalyst Center will deploy and create your Fabric Site along with any Fabric Zones you have also designated. You will be shown if your deployment was successful.
Helpful Resources
YouTube Video for SD-Access Fabric Zones
Cisco SD-Access Solution Design Guide
Cisco SD-Access Fabric Resources
Cisco SD-Access YouTube Channel
Cisco SD-Access Compatibility Matrix
Cisco Catalyst Center Compatibility Matrix

- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Comments on this article have been closed.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: