- Cisco Community
- Technology and Support
- Security
- Other Security Subjects
- Re: How to (V)ACL to control inter-VLAN routing
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to (V)ACL to control inter-VLAN routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2018 02:44 AM - edited 02-20-2020 09:44 PM
Hello,
I need to implement ACL's to control the traffic in my network, but i can't get it to work.
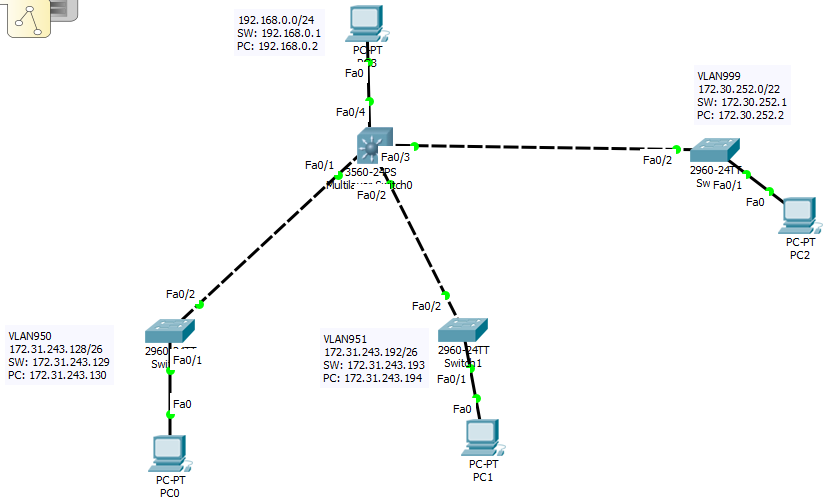
I have a network which consists of SVIs on the L3 switches, where the first IP in that subnet is the IP of the VLAN interface. The layer 3 switch is the core switch, and connected to that are layer 2 switches. And connected to those layer 2 switches are the VLANs mentioned below.
Customer VLANs 950-998, from subnet: 172.31.243.128/26 through: 172.31.255.128/26
Management VLAN: 999, subnet: 172.30.252.0/22
This is what the ACLs SHOULD do:
- Deny traffic from any customer VLAN 950-998 to any other customer VLAN 950 - 998.
- Deny traffic from any customer VLANs (950-998) to the management VLAN 999.
- Permit all other traffic from customer VLANs (950-998) to any other part of the network.
- Permit the management network VLAN 999 to access anything in the network.
What i have tried to create in packet tracer, but doesn't seem to work is:
ip access-list extended VLAN950
deny ip 172.31.243.128 0.0.0.63 172.31.243.192 0.0.0.63 <<<< deny VLAN950 to access VLAN951
deny ip 172.31.243.128 0.0.0.63 172.30.252.0 0.0.3.255 <<<<<< deny VLAN950 to access the management VLAN999
permit ip any any <<<< allow anything else.
ip access-list extended VLAN950_Management
permit ip 172.30.252.0 0.0.3.255 172.31.243.128 0.0.0.63 <<<<<< permit Management VLAN999 to access VLAN950
deny ip any any <<<< Deny anything else.
interface vlan950
ip address 172.31.243.129 255.255.255.192
ip access-group VLAN950 out
ip access-group VLAN950_Management in
But after i set this up in PT this is what happens:
The PC in VLAN950 can't ping anything in the network (not even it's default gateway and not the 192.168.0.0/24 network)
The management PC in VLAN999 cannot ping the PC in VLAN950 even though it should be allowed.
In the attachements i have added the .pkt file so maybe hopefully someone can help me to build what i need to build.
Thanks in advance!
Here is a picture of the network i have build in PT:
- Labels:
-
Access List
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2018 09:53 AM
bump
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2018 04:03 AM
Hello, there are a couple of issues here. For starters, if you consider a VLAN interface as an ethernet port it is easier to get the direction correct for ACLs.
That said, regarding the restriction of VLAN 950 to 951, it would be best implemented as:
!
ip access-list extended VLAN950_In
deny ip 172.31.243.128 0.0.0.63 172.31.243.192 0.0.0.63 (Denies from 950 to 951)
permit ip any any
!
ip access-list extended VLAN950_Out
deny ip 172.31.243.192 0.0.0.63 172.31.243.128 0.0.0.63 (Denies from 951 to 950)
permit ip any any
!
interface vlan950
ip address 172.31.243.129 255.255.255.192
ip access-group VLAN950_In in
ip access-group VLAN950_Out out
!
Now what you are trying to accomplish with the management VLAN has a conflict. In your inbound list you deny access to it from 950, then in the outbound you permit access. It has to be one or the other. You could define source and/or destination ports if that is possible to allow only certain protocols and hosts but that would depend on the magnitude and manageability of something like that.
Finally, the "deny any any" in your VLAN950_Management ACL would block ALL traffic from the VLAN 950 hosts, thus the total loss of connectivity.
Hope this helps
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide