- Cisco Community
- Technology and Support
- Networking
- Routing
- Converting private to public IP for VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Converting private to public IP for VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2011 09:01 PM - edited 03-04-2019 01:19 PM
Dear team,
We have an issue here, whereby the scenario is as below. I am pulling out my hair figuring this out. It look simple though.
We have a VPN router(ASA 5505) which connects to the client, B. IP address for one si 195.xx.xx.xx and for B it is 14.xx.xx.xx. Both can extablish a IPSEC VPN nicely. Not a problem.
Now, B throws a condition that the IP coming thru the VPN has to be PUblic. They want it as such so that they can be routed across the VPN tunnel.
It still can because the firewall does not do NAT.
Anyway, as such, the condition stands.
So, internal network (172.31.13.xx) --------> FW--------->client
this is tough... help
Thanks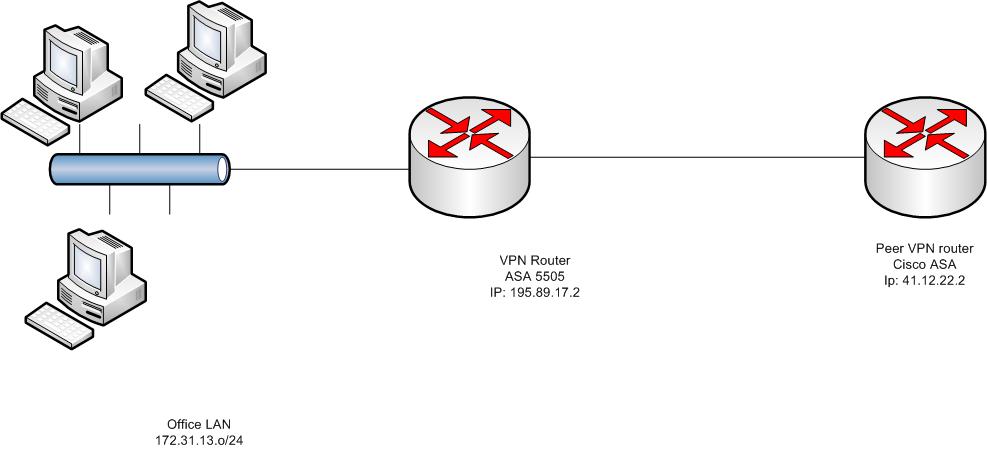
- Labels:
-
Other Routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2011 10:38 PM
first of all the ASA is a firewall not a router because there is a deference in the way they work
about the VPN is the tunnel up and this is just site to site VPN ( not client to server VPN aka easy VPN )
if its site to site VPN then you need to have access-list that match private IP LAN to the other end private IP LAN and included in the VPN policy config called interesting traffic to be encrypted and also used same for nat expmtion as well
please refer to the bellow example where you have LAN to LAN communications directly over the VPN tunnel
http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a0080950890.shtml
HTH
if helpful Rate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2011 01:36 AM
What we need is public IPs.. Not to match private ips.
One way I can think about is to add a router to the internet cloud, fix an ip (we have ips) and from there, connect a switch. From the switch, create a VLAN that incorporates the VPN router.
The characteristics for this VLAN would be:
1. connects to the VPN ASA
2. No NAT happens on the VLAN interface
I believe, from here, the VPN ASA will only be exposed to public IP address and shielded from the rest of the private network.
What do you think?

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2011 02:09 AM
If u have router you can use gre over IPSec and the ip to the public one over the gre
Sent from Cisco Technical Support iPhone App
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2011 04:17 AM
This is a good.. but could you elaborate a bit more.. where do i use the gre over ipsec? And where to apply the public one?
thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2011 04:50 AM
look i am not getting your point 100%
but in general if you want to NAT your LAN over the Tunnel then you can use GRE tunnel and apply the NATingon that Tnnel
while you apply the IPsec crypto MAP on the physical interface
LAN --- Tunnel -NATed---IPSEc encryption---IPSECVPN------IPsec decryption---Tunnel ----LAN
but GRE work with Cisco routers not firewalls
if you can have a router behain each ASA then creat a notmral Site to Site VPN between the ASAs and the gre tunnel will be the interesting traffic for VPN IPsecc tunnel between the routers behaind the ASAs
https://learningnetwork.cisco.com/docs/DOC-2457
HTH
if helpful Rate
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide