
Introduction
What Is Cisco Identity Services Engine?
Cisco Identity Services Engine (ISE) is an all-in-one enterprise policy control product that enables comprehensive secure wired, wireless, and Virtual Private Networking (VPN) access.
Cisco ISE offers a centralized control point for comprehensive policy management and enforcement in a single RADIUS-based product. The unique architecture of Cisco ISE allows enterprises to gather real-time contextual information from networks, users, and devices. The administrator can then use that information to make proactive governance decisions. Cisco ISE is an integral component of Cisco Secure Access.
Cisco Secure Access is an advanced Network Access Control and Identity Solution that is integrated into the Network Infrastructure. It is a fully tested, validated solution where all the components within the solution are thoroughly vetted and rigorously tested as an integrated system.
Cisco Wireless Controllers
Unlike overlay Network Access Control solutions the Cisco Secure Access utilizes the access layer devices (switches, wireless controllers, etc.) for enforcement. The access device itself now handles functions that were commonly handled by appliances and other overlay devices, such as URL redirection for web authentications.
The Cisco Secure Access not only combines standards-based identity and enforcement models, such as IEEE 802.1X and VLAN control, it also has many more advanced identity and enforcement capabilities such as URL Redirect, Named Access Control Lists (AireSpace ACLs), Security Group Tagging (SGT), device profiling, guest and web authentications services, posture assessments, and integration with leading Mobile Device Management (MDM) vendors for compliance validation of mobile devices before and during network access.
About This Document
The following section describes the “universal configuration” for Cisco® Wireless LAN Controllers (WLC). These recommended configurations are compiled as a best practice to be used for all deployments, and they remain consistent through the different stages of deployment, as well as the different deployment types chosen.
The following diagram shows the overall layout of the components. There are two access VLANs, ACCESS VLAN for Employee users and GUEST VLAN for Guest users. Although this document doesn’t include policy configurations on ISE such as BYOD, Posture Assessment, and profiling configuration provided here allows baseline for such operations.
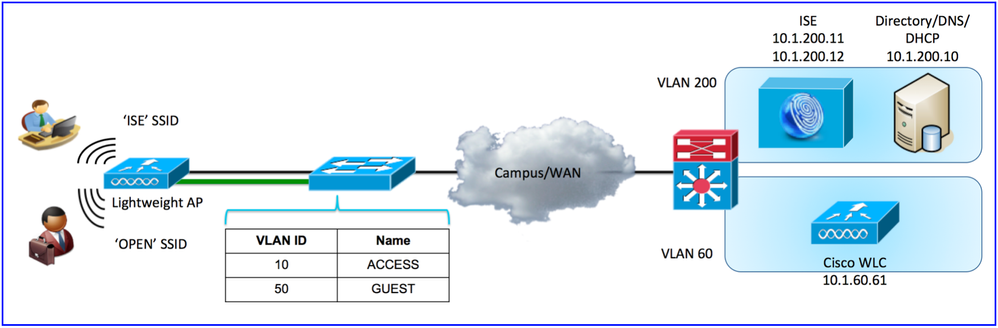
In the appendix, there are sample configurations that can be copied and pasted with minimal modification. Also in the appendix are the additional configurations that pertain to FlexConnect mode WLAN/AP and WLANs configured in Auto-Anchor mode.
Configuration
Initial Configuration
This section covers initial bootstrapping of WLC using the CLI-based configuration tool.
-
Initial Configuration
| Management Interface IP |
10.1.60.61 |
| Management Interface Mask |
255.255.255.0 |
| Management Interface Gateway |
10.1.60.1 |
| Management Interface VLAN ID |
0 (Untagged) |
| Management Interface Port Number |
1 |
| Virtual Gateway IP |
192.0.2.1 |
| Mobility/RF Group Name |
Main |
| NTP Server IP |
10.1.60.1 |
Note: Initial Configuration applies to new WLC with no prior configuration. If the ISE-related configurations are being added to a WLC with existing configuration, then proceed to the Controller Configuration section.
-
Connect to the console port of the WLC or use virtual console for vWLC. Refer to the following settings to bootstrap the WLC.
(Cisco Controller)
Welcome to the Cisco Wizard Configuration Tool
Use the '-' character to backup
Would you like to terminate autoinstall? [yes]:yes
AUTO-INSTALL: process terminated -- no configuration loaded
System Name [Cisco_91:e2:64] (31 characters max):
Enter Administrative User Name (24 characters max): admin
Enter Administrative Password (3 to 24 characters): ********
Re-enter Administrative Password : ********
Service Interface IP Address Configuration [static][DHCP]:dhcp
Enable Link Aggregation (LAG) [yes][NO]: no
Management Interface IP Address: 10.1.60.61
Management Interface Netmask: 255.255.255.0
Management Interface Default Router: 10.1.60.1
Management Interface VLAN Identifier (0 = untagged): 0
Management Interface Port Num [1 to 8]: 1
Management Interface DHCP Server IP Address: 10.1.100.100
Virtual Gateway IP Address: 192.0.2.1
Mobility/RF Group Name: Main
Network Name (SSID): EXAMPLE
Configure DHCP Bridging Mode [yes][NO]: no
Allow Static IP Addresses [YES][no]: no
Configure a RADIUS Server now? [YES][no]: no
Warning! The default WLAN security policy requires a RADIUS server.
Please see documentation for more details.
Enter Country Code list (enter 'help' for a list of countries) [US]:us
Enable 802.11b Network [YES][no]: yes
Enable 802.11a Network [YES][no]: yes
Enable 802.11g Network [YES][no]: yes
Enable Auto-RF [YES][no]: yes
Configure a NTP server now? [YES][no]: yes
Enter the NTP server's IP address: 10.1.60.1
Enter a polling interval between 3600 and 604800 secs: 3600
Configuration correct? If yes, system will save it and reset. [yes][NO]: yes
|
We recommend that you set the Cisco WLC virtual gateway address to 192.0.2.1. The address you use must be a non-routed IP with a fully qualified domain name (FQDN) mapped in the Domain Name System (DNS). This FQDN/ IP address should be added to certificates generated by your CA. This configuration stops users from seeing “untrusted certificate” errors when they are redirected to the WLC’s virtual gateway.
-
After the WLC resets, configure the rest of the WLC settings. This guide includes both GUI and CLI-based configuration for the following sections.
Note: Please note that the SSID named ‘EXAMPLE’ configured during the initialization will not be used in this guide and can be removed by running the following command after the WLC resets.
(WLC) >config wlan delete 1
|
Controller Configuration
This section covers configuration related to the controller. This includes interface and VLAN configurations for endpoint devices and global controller settings.
-
Interface Configuration
| Interface Name |
ACCESS |
GUEST |
| VLAN ID |
10 |
50 |
| Dynamic IP |
10.1.10.61 |
10.1.50.61 |
| Subnet Mask |
255.255.255.0 |
255.255.255.0 |
| Gateway |
10.1.10.1 |
10.1.50.1 |
| DHCP Server |
10.1.200.10 |
10.1.200.10 |
| Port |
1 |
1 |
-
Configure dynamic interfaces. For GUI, go to Controller Interfaces.
(WLC) >config interface create ACCESS 10
(WLC) >config interface create GUEST 50
|
-
Assign a physical port for the dynamic interfaces created above. In this example, all interfaces are assigned to same physical interface and utilize trunking.
(WLC) >config interface port ACCESS 1
(WLC) >config interface port GUEST 1
|
-
Configure ip addresses on the interfaces.
(WLC) >config interface address dynamic-interface ACCESS 10.1.10.61 255.255.255.0 10.1.10.1
(WLC) >config interface address dynamic-interface GUEST 10.1.50.61 255.255.255.0 10.1.50.1
|
-
Configure DHCP server for user interfaces.
(WLC) >config interface dhcp dynamic-interface ACCESS primary 10.1.200.10
(WLC) >config interface dhcp dynamic-interface GUEST primary 10.1.200.10
|
-
Disable DHCP proxy globally and use router’s SVI to forward DHCP request to the DHCP server. For GUI, go to Controller Advanced DHCP.
(WLC) >config dhcp proxy disable
|
Note: When dhcp proxy is disabled, WLC bridges DHCP requests to the upstream router. The upstream router should be configured with ‘ip helper-address’ for the DHCP server, and as an ISE PSN node for profiling purposes. While the WLC device sensor can capture DHCP attributes for ISE, it lacks several DHCP attributes, such as the DHCP options attribute. By configuring the upstream router to forward DHCP requests to the ISE node, ISE can collect additional DHCP information for profiling purposes.
-
(Optional) Enable fast-ssid-change feature to accommodate apple devices transitioning from different SSIDs for dual SSID deployment. For GUI, go to Controller General
(WLC) >config network fast-ssid-change enable
|
Note: When fast SSID changing is enabled, the controller allows clients to move between SSIDs. When the client sends a new association for a different SSID, the client entry in the controller connection table is cleared before the client is added to the new SSID. When fast SSID changing is disabled, the controller enforces a delay before clients are allowed to move to a new SSID, which impacts user experience in dual SSID BYOD deployment.
Security Configuration
This section covers configuration related to the security, which includes RADIUS server and ACLs. The RADIUS servers are using ID values of 11 and 12 so as to not overwrite any existing RADIUS settings.
-
Create a RADIUS Authentication server. In this example, there are two ISE nodes, 10.1.200.11 and 10.1.200.12. CoA is enabled, and timeout is set to 5 seconds (default is 2 seconds). Device Management via RADIUS is disabled, and these RADIUS servers are dedicated for network user authentication. For GUI configuration, go to Security AAA RADIUS Authentication New…
(WLC) >config radius auth add 11 10.1.200.11 1812 ascii ISEc0ld
(WLC) >config radius auth disable 11
(WLC) >config radius auth management 11 disable
(WLC) >config radius auth retransmit-timeout 11 5
(WLC) >config radius auth rfc3576 enable 11
(WLC) >config radius auth enable 11
(WLC) >config radius auth add 12 10.1.200.12 1812 ascii ISEc0ld
(WLC) >config radius auth disable 12
(WLC) >config radius auth management 12 disable
(WLC) >config radius auth retransmit-timeout 12 5
(WLC) >config radius auth rfc3576 enable 12
(WLC) >config radius auth enable 12
|
-
(Optional) Ensure that the MAC address format sent in the Calling-Station-ID field matches the ISE. This should be the default setting.
(WLC) >config radius auth mac-delimiter hyphen
|
-
(Optional) Configure the format of the RADIUS Called-Station-ID attribute with additional information. The default format is APMAC:SSID. The option for this attribute varies depending on the WLC code version. This field can be used to provide location-based authentication using AP location information that endpoint associated for initial authentication.
(WLC) >config radius callStationIdType ap-macaddr-ssid
|
Note: This is different from MSE location integration that uses endpoint location using WiFi triangulation.
-
Configure RADIUS fallback mode so the primary ISE node is used when it is back online. Without this option, a second or tertiary server is used, even if the primary server is back online. For GUI, go to Security AAA RADIUS Fallback.
(WLC) >config radius fallback-test username RADIUS-TEST
(WLC) >config radius fallback-test mode active
|
Note: Selecting active causes the Cisco WLC to revert to a server with a lower priority from the available backup servers. To select a server, it uses RADIUS probe messages to proactively determine whether a server that has been marked inactive is back online. The controller ignores all inactive servers for all active RADIUS requests. Selecting passive mode causes the Cisco WLC to revert to a server with a lower priority from the available backup servers without using extraneous probe messages. The controller ignores all inactive servers for a time period, and retries later when a RADIUS message needs to be sent.
-
(Optional) The interval specifies the probe interval in the case of active mode fallback or inactive time in the case of passive mode fallback. The default value is 300 seconds.
(WLC) >config radius fallback-test mode interval 300
|
-
Disable RADIUS aggressive failover mechanism so the RADIUS server is not marked dead in error.
(WLC) >config radius aggressive-failover disable
|
Note: If the aggressive failover feature is enabled in the WLC, the WLC is too aggressive to mark the AAA server as "not responding". One reason you should not enable this feature is because the AAA server is possibly not responsive only to a particular client, if you configured silent discard. It could also be a response to other valid clients with valid certificates. The WLC can still mark the AAA server as "not responding" and "not functional". To overcome this, disable the aggressive failover feature. If this is disabled, then the controller only fails over to the next AAA server if there are three consecutive clients that fail to receive a response from the RADIUS server.
-
Create RADIUS Accounting servers. For GUI, go to Security AAA RADIUS Accounting New…
(WLC) >config radius acct add 11 10.1.200.11 1813 ascii ISEc0ld
(WLC) >config radius acct disable 11
(WLC) >config radius acct retransmit-timeout 11 5
(WLC) >config radius acct enable 11
(WLC) >config radius acct add 12 10.1.200.12 1813 ascii ISEc0ld
(WLC) >config radius acct disable 12
(WLC) >config radius acct retransmit-timeout 12 5
(WLC) >config radius acct enable 12
|
-
Create ACL_WEBAUTH_REDIRECT ACL. For GUI, go to Security Access Control Lists Access Control Lists New…
(WLC) >config acl delete ACL_WEBAUTH_REDIRECT
(WLC) >config acl create ACL_WEBAUTH_REDIRECT
(WLC) >config acl rule add ACL_WEBAUTH_REDIRECT 1
(WLC) >config acl rule action ACL_WEBAUTH_REDIRECT 1 permit
(WLC) >config acl rule protocol ACL_WEBAUTH_REDIRECT 1 6
(WLC) >config acl rule source port range ACL_WEBAUTH_REDIRECT 1 0 65535
(WLC) >config acl rule destination address ACL_WEBAUTH_REDIRECT 1 10.1.200.12 255.255.255.255
(WLC) >config acl rule destination port range ACL_WEBAUTH_REDIRECT 1 8443 8444
(WLC) >config acl rule add ACL_WEBAUTH_REDIRECT 1
(WLC) >config acl rule action ACL_WEBAUTH_REDIRECT 1 permit
(WLC) >config acl rule protocol ACL_WEBAUTH_REDIRECT 1 6
(WLC) >config acl rule source address ACL_WEBAUTH_REDIRECT 1 10.1.200.12 255.255.255.255
(WLC) >config acl rule source port range ACL_WEBAUTH_REDIRECT 1 8443 8444
(WLC) >config acl rule destination port range ACL_WEBAUTH_REDIRECT 1 0 65535
(WLC) >config acl rule add ACL_WEBAUTH_REDIRECT 1
(WLC) >config acl rule action ACL_WEBAUTH_REDIRECT 1 permit
(WLC) >config acl rule protocol ACL_WEBAUTH_REDIRECT 1 6
(WLC) >config acl rule source port range ACL_WEBAUTH_REDIRECT 1 0 65535
(WLC) >config acl rule destination address ACL_WEBAUTH_REDIRECT 1 10.1.200.12 255.255.255.255
(WLC) >config acl rule destination port range ACL_WEBAUTH_REDIRECT 1 8905 8905
(WLC) >config acl rule add ACL_WEBAUTH_REDIRECT 1
(WLC) >config acl rule action ACL_WEBAUTH_REDIRECT 1 permit
(WLC) >config acl rule protocol ACL_WEBAUTH_REDIRECT 1 6
(WLC) >config acl rule source address ACL_WEBAUTH_REDIRECT 1 10.1.200.12 255.255.255.255
(WLC) >config acl rule source port range ACL_WEBAUTH_REDIRECT 1 8905 8905
(WLC) >config acl rule destination port range ACL_WEBAUTH_REDIRECT 1 0 65535
(WLC) >config acl rule add ACL_WEBAUTH_REDIRECT 1
(WLC) >config acl rule action ACL_WEBAUTH_REDIRECT 1 permit
(WLC) >config acl rule protocol ACL_WEBAUTH_REDIRECT 1 6
(WLC) >config acl rule source port range ACL_WEBAUTH_REDIRECT 1 0 65535
(WLC) >config acl rule destination address ACL_WEBAUTH_REDIRECT 1 10.1.200.11 255.255.255.255
(WLC) >config acl rule destination port range ACL_WEBAUTH_REDIRECT 1 8443 8444
(WLC) >config acl rule add ACL_WEBAUTH_REDIRECT 1
(WLC) >config acl rule action ACL_WEBAUTH_REDIRECT 1 permit
(WLC) >config acl rule protocol ACL_WEBAUTH_REDIRECT 1 6
(WLC) >config acl rule source address ACL_WEBAUTH_REDIRECT 1 10.1.200.11 255.255.255.255
(WLC) >config acl rule source port range ACL_WEBAUTH_REDIRECT 1 8443 8444
(WLC) >config acl rule destination port range ACL_WEBAUTH_REDIRECT 1 0 65535
(WLC) >config acl rule add ACL_WEBAUTH_REDIRECT 1
(WLC) >config acl rule action ACL_WEBAUTH_REDIRECT 1 permit
(WLC) >config acl rule protocol ACL_WEBAUTH_REDIRECT 1 6
(WLC) >config acl rule source port range ACL_WEBAUTH_REDIRECT 1 0 65535
(WLC) >config acl rule destination address ACL_WEBAUTH_REDIRECT 1 10.1.200.11 255.255.255.255
(WLC) >config acl rule destination port range ACL_WEBAUTH_REDIRECT 1 8905 8905
(WLC) >config acl rule add ACL_WEBAUTH_REDIRECT 1
(WLC) >config acl rule action ACL_WEBAUTH_REDIRECT 1 permit
(WLC) >config acl rule protocol ACL_WEBAUTH_REDIRECT 1 6
(WLC) >config acl rule source address ACL_WEBAUTH_REDIRECT 1 10.1.200.11 255.255.255.255
(WLC) >config acl rule source port range ACL_WEBAUTH_REDIRECT 1 8905 8905
(WLC) >config acl rule destination port range ACL_WEBAUTH_REDIRECT 1 0 65535
(WLC) >config acl rule add ACL_WEBAUTH_REDIRECT 1
(WLC) >config acl rule action ACL_WEBAUTH_REDIRECT 1 permit
(WLC) >config acl rule protocol ACL_WEBAUTH_REDIRECT 1 17
(WLC) >config acl rule source port range ACL_WEBAUTH_REDIRECT 1 0 65535
(WLC) >config acl rule destination port range ACL_WEBAUTH_REDIRECT 1 53 53
(WLC) >config acl rule add ACL_WEBAUTH_REDIRECT 1
(WLC) >config acl rule action ACL_WEBAUTH_REDIRECT 1 permit
(WLC) >config acl rule protocol ACL_WEBAUTH_REDIRECT 1 17
(WLC) >config acl rule source port range ACL_WEBAUTH_REDIRECT 1 53 53
(WLC) >config acl rule destination port range ACL_WEBAUTH_REDIRECT 1 0 65535
|
-
(Optional) If desired, DNS ACL entries can be added to the redirect ACL. This allows endpoint access to the Google Play store during the NSP process.
(WLC) >config acl url-domain add play.google.com ACL_WEBAUTH_REDIRECT
(WLC) >config acl url-domain add android.clients.google.com ACL_WEBAUTH_REDIRECT
(WLC) >config acl url-domain add www.googleapis.com ACL_WEBAUTH_REDIRECT
(WLC) >config acl url-domain add ggpht.com ACL_WEBAUTH_REDIRECT
(WLC) >config acl url-domain add android.pool.ntp.org ACL_WEBAUTH_REDIRECT
(WLC) >config acl url-domain add market.android.com ACL_WEBAUTH_REDIRECT
(WLC) >config acl url-domain add mtalk.google.com ACL_WEBAUTH_REDIRECT
(WLC) >config acl url-domain add gvt1.com ACL_WEBAUTH_REDIRECT
|
Note: To accommodate client devices with language setting other than English may require additional domains to be added. Up to 20 domain entries can be added per ACL.
-
Apply ACL to the data path
(WLC) >config acl apply ACL_WEBAUTH_REDIRECT
|
Note: When a client is in the redirect state such as POSTURE_REQ , CWA, Client Provisioning, the default behavior of the WLC is to block all traffic except DHCP/DNS. The ACL_WEBAUTH_REDIRECT ACL (which is called in the url-redirect-acl AV Pair received from Cisco ISE) is applied to the client, and it can reach only resources specifically allowed in the ACL.
-
Create a BLACKHOLE ACL.
(WLC) >config acl delete BLACKHOLE
(WLC) >config acl create BLACKHOLE
(WLC) >config acl rule add BLACKHOLE 1
(WLC) >config acl rule action BLACKHOLE 1 permit
(WLC) >config acl rule protocol BLACKHOLE 1 6
(WLC) >config acl rule source port range BLACKHOLE 1 0 65535
(WLC) >config acl rule destination address BLACKHOLE 1 10.1.200.12 255.255.255.255
(WLC) >config acl rule destination port range BLACKHOLE 1 8444 8444
(WLC) >config acl rule add BLACKHOLE 1
(WLC) >config acl rule action BLACKHOLE 1 permit
(WLC) >config acl rule protocol BLACKHOLE 1 6
(WLC) >config acl rule source address BLACKHOLE 1 10.1.200.12 255.255.255.255
(WLC) >config acl rule source port range BLACKHOLE 1 8444 8444
(WLC) >config acl rule destination port range BLACKHOLE 1 0 65535
(WLC) >config acl rule add BLACKHOLE 1
(WLC) >config acl rule action BLACKHOLE 1 permit
(WLC) >config acl rule protocol BLACKHOLE 1 6
(WLC) >config acl rule source port range BLACKHOLE 1 0 65535
(WLC) >config acl rule destination address BLACKHOLE 1 10.1.200.11 255.255.255.255
(WLC) >config acl rule destination port range BLACKHOLE 1 8444 8444
(WLC) >config acl rule add BLACKHOLE 1
(WLC) >config acl rule action BLACKHOLE 1 permit
(WLC) >config acl rule protocol BLACKHOLE 1 6
(WLC) >config acl rule source address BLACKHOLE 1 10.1.200.11 255.255.255.255
(WLC) >config acl rule source port range BLACKHOLE 1 8444 8444
(WLC) >config acl rule destination port range BLACKHOLE 1 0 65535
(WLC) >config acl rule add BLACKHOLE 1
(WLC) >config acl rule action BLACKHOLE 1 permit
(WLC) >config acl rule protocol BLACKHOLE 1 17
(WLC) >config acl rule source port range BLACKHOLE 1 0 65535
(WLC) >config acl rule destination port range BLACKHOLE 1 53 53
(WLC) >config acl rule add BLACKHOLE 1
(WLC) >config acl rule action BLACKHOLE 1 permit
(WLC) >config acl rule protocol BLACKHOLE 1 17
(WLC) >config acl rule source port range BLACKHOLE 1 53 53
(WLC) >config acl rule destination port range BLACKHOLE 1 0 65535
|
-
Apply ACL to the data path
(WLC) >config acl apply BLACKHOLE
|
WLAN Configuration
This section covers configuration related to the Secured WLAN for Employee devices. This includes WLAN settings. The WLANs are using ID value of 11 and 12 so as not to overwrite any existing WLAN settings. This example configures two WLANs:
-
‘ISE’ is a secured WLAN with WLAN ID 11, used for employee access and Single SSID BYOD flow.
-
‘OPEN’ is an open WLAN with WLAN ID 12, used for guest access.
-
| WLAN ID |
11 |
12 |
| WLAN Name |
ISE |
OPEN |
| SSID |
ISE |
OPEN |
| Interface |
ACCESS |
GUEST |
| L2 Security |
WPA/WPA2 & 802.1X |
MAC Filtering |
| L3 Security |
None |
None |
| RADIUS Auth Server |
11 & 12 |
11 & 12 |
| RADIUS Acct Server |
11 & 12 |
11 & 12 |
| RADIUS Interim ACCT |
Enabled |
Enabled |
| Interim Update Interval |
0 Seconds |
0 Seconds |
| AAA Override |
Enabled |
Enabled |
| Idle Timeout |
180 Seconds |
180 Seconds |
| NAC |
NAC_RADIUS |
NAC_RADIUS |
| Device Sensor |
DHCP & HTTP |
DHCP & HTTP |
-
Create ISE WLAN using WLAN ID 11. For GUI, go to WLANs Create New Go.
(WLC) >config wlan create 11 ISE ISE
|
-
Assign previously created interface ‘ISE’ to the WLAN.
(WLC) >config wlan interface 11 ACCESS
|
Note: When WLANs are added to the WLC, it is already enabled with WPA and 802.1X.
-
Assign previously created RADIUS Auth and Acct servers to the WLAN.
(WLC) >config wlan radius_server auth add 11 11
(WLC) >config wlan radius_server auth add 11 12
(WLC) >config wlan radius_server acct add 11 11
(WLC) >config wlan radius_server acct add 11 12
|
-
Configure interim accounting updates for the endpoints. Following setting applies to 8.x code.
(WLC) >config wlan radius_server acct interim-update 0 11
(WLC) >config wlan radius_server acct interim-update enable 11
|
Note: For 7.6 code disable interim accounting. Although disabled the WLC will still send accounting updates for mobility events for the endpoint.
(WLC) >config wlan radius_server acct interim-update disable 11
|
Note: For any other previous versions.
(WLC) >config wlan radius_server acct interim-update 3600 11
(WLC) >config wlan radius_server acct interim-update enable 11
|
-
Configure WLAN to accept AuthZ attributes from ISE.
(WLC) >config wlan aaa-override enable 11
|
-
(Optional) Configure idle timeout.
(WLC) >config wlan usertimeout 180 11
|
-
Enable nac-radius for the WLAN.
(WLC) >config wlan nac radius enable 11
|
-
Enable device sensor for http and dhcp.
(WLC) >config wlan profiling radius all enable 11
|
-
Enable Secured WLAN.
(WLC) >config wlan enable 11
|
-
Create OPEN WLAN using WLAN ID 12.
(WLC) >config wlan create 12 OPEN OPEN
|
-
Assign previously created interface ‘GUEST’ to the WLAN.
(WLC) >config wlan interface 12 GUEST
|
-
Disable L2 security for open WLAN.
(WLC) >config wlan security wpa disable 12
|
-
Enable MAC filtering for CWA.
(WLC) >config wlan mac-filtering enable 12
|
-
Assign previously created RADIUS Auth and Acct servers to the WLAN.
(WLC) >config wlan radius_server auth add 12 11
(WLC) >config wlan radius_server auth add 12 12
(WLC) >config wlan radius_server acct add 12 11
(WLC) >config wlan radius_server acct add 12 12
|
-
Configure interim accounting updates for the endpoints. Following setting applies to 8.x code.
(WLC) >config wlan radius_server acct interim-update 0 12
(WLC) >config wlan radius_server acct interim-update enable 12
|
Note: For 7.6 code disable interim accounting. Although disabled the WLC will still send accounting updates for mobility events for the endpoint.
(WLC) >config wlan radius_server acct interim-update disable 12
|
Note: For any other previous versions.
(WLC) >config wlan radius_server acct interim-update 3600 12
(WLC) >config wlan radius_server acct interim-update enable 12
|
-
Configure WLAN to accept AuthZ attributes from ISE
(WLC) >config wlan aaa-override enable 12
|
-
Configure session timeout.
(WLC) >config wlan session-timeout 12 1800
|
-
Configure idle timeout.
(WLC) >config wlan usertimeout 180 12
|
-
(Optional) Configure other parameters necessary for open WLAN.
(WLC) >config wlan chd 12 disable
(WLC) >config wlan ccx AironetIeSupport disable 12
(WLC) >config wlan dhcp_server 12 0.0.0.0 required
|
-
Enable nac-radius for the WLAN.
(WLC) >config wlan nac radius enable 12
|
-
Enable device sensor for http and dhcp.
(WLC) >config wlan profiling radius all enable 12
|
-
Enable Open WLAN.
(WLC) >config wlan enable 12
|
Management Configuration
This section covers configuration related to the General Controller Management. This includes Captive Portal Bypass, and HTTPS redirect settings.
-
Enable captive portal bypass to disable mini browser from popping up when Apple device associates to the WLAN. This will be in effect after the WLC has been restarted. There is no GUI for this configuration.
(WLC) >config network web-auth captive-bypass enable
|
-
(Optional) Enable HTTPS redirect on 8.x code. For GUI, go to Management HTTP-HTTPS HTTPS Redirection Enabled.
(WLC) >config network web-auth https-redirect enable
|
Note: This is not recommended in production environment due to added load on the controller and reduced web auth sessions that WLC can handle when enabled.
-
Save configuration.
-
Reload the controller to have captive portal bypass setting take effect.
Appendix A: Sample Configuration
Configuration for WLC Running 8.x Code
Configuration for previous versions of WLC is identical with the exception of interim accounting settings under each of the WLAN configuration. Please refer to main section of the document for proper configuration for previous versions.
config interface create ACCESS 10
config interface create GUEST 50
config interface port ACCESS 1
config interface port GUEST 1
config interface address dynamic-interface ACCESS 10.1.10.61 255.255.255.0 10.1.10.1
config interface address dynamic-interface GUEST 10.1.50.61 255.255.255.0 10.1.50.1
config interface dhcp dynamic-interface ACCESS primary 10.1.200.10
config interface dhcp dynamic-interface GUEST primary 10.1.200.10
config dhcp proxy disable
config radius auth add 11 10.1.200.11 1812 ascii ISEc0ld
config radius auth disable 11
config radius auth management 11 disable
config radius auth retransmit-timeout 11 5
config radius auth rfc3576 enable 11
config radius auth enable 11
config radius auth add 12 10.1.200.12 1812 ascii ISEc0ld
config radius auth disable 12
config radius auth management 12 disable
config radius auth retransmit-timeout 12 5
config radius auth rfc3576 enable 12
config radius auth enable 12
config radius fallback-test username RADIUS-TEST
config radius fallback-test mode active
config radius aggressive-failover disable
config radius acct add 11 10.1.200.11 1813 ascii ISEc0ld
config radius acct disable 11
config radius acct retransmit-timeout 11 5
config radius acct enable 11
config radius acct add 12 10.1.200.12 1813 ascii ISEc0ld
config radius acct disable 12
config radius acct retransmit-timeout 12 5
config radius acct enable 12
config acl delete ACL_WEBAUTH_REDIRECT
config acl create ACL_WEBAUTH_REDIRECT
config acl rule add ACL_WEBAUTH_REDIRECT 1
config acl rule action ACL_WEBAUTH_REDIRECT 1 permit
config acl rule protocol ACL_WEBAUTH_REDIRECT 1 6
config acl rule source port range ACL_WEBAUTH_REDIRECT 1 0 65535
config acl rule destination address ACL_WEBAUTH_REDIRECT 1 10.1.200.12 255.255.255.255
config acl rule destination port range ACL_WEBAUTH_REDIRECT 1 8443 8444
config acl rule add ACL_WEBAUTH_REDIRECT 1
config acl rule action ACL_WEBAUTH_REDIRECT 1 permit
config acl rule protocol ACL_WEBAUTH_REDIRECT 1 6
config acl rule source address ACL_WEBAUTH_REDIRECT 1 10.1.200.12 255.255.255.255
config acl rule source port range ACL_WEBAUTH_REDIRECT 1 8443 8444
config acl rule destination port range ACL_WEBAUTH_REDIRECT 1 0 65535
config acl rule add ACL_WEBAUTH_REDIRECT 1
config acl rule action ACL_WEBAUTH_REDIRECT 1 permit
config acl rule protocol ACL_WEBAUTH_REDIRECT 1 6
config acl rule source port range ACL_WEBAUTH_REDIRECT 1 0 65535
config acl rule destination address ACL_WEBAUTH_REDIRECT 1 10.1.200.12 255.255.255.255
config acl rule destination port range ACL_WEBAUTH_REDIRECT 1 8905 8905
config acl rule add ACL_WEBAUTH_REDIRECT 1
config acl rule action ACL_WEBAUTH_REDIRECT 1 permit
config acl rule protocol ACL_WEBAUTH_REDIRECT 1 6
config acl rule source address ACL_WEBAUTH_REDIRECT 1 10.1.200.12 255.255.255.255
config acl rule source port range ACL_WEBAUTH_REDIRECT 1 8905 8905
config acl rule destination port range ACL_WEBAUTH_REDIRECT 1 0 65535
config acl rule add ACL_WEBAUTH_REDIRECT 1
config acl rule action ACL_WEBAUTH_REDIRECT 1 permit
config acl rule protocol ACL_WEBAUTH_REDIRECT 1 6
config acl rule source port range ACL_WEBAUTH_REDIRECT 1 0 65535
config acl rule destination address ACL_WEBAUTH_REDIRECT 1 10.1.200.11 255.255.255.255
config acl rule destination port range ACL_WEBAUTH_REDIRECT 1 8443 8444
config acl rule add ACL_WEBAUTH_REDIRECT 1
config acl rule action ACL_WEBAUTH_REDIRECT 1 permit
config acl rule protocol ACL_WEBAUTH_REDIRECT 1 6
config acl rule source address ACL_WEBAUTH_REDIRECT 1 10.1.200.11 255.255.255.255
config acl rule source port range ACL_WEBAUTH_REDIRECT 1 8443 8444
config acl rule destination port range ACL_WEBAUTH_REDIRECT 1 0 65535
config acl rule add ACL_WEBAUTH_REDIRECT 1
config acl rule action ACL_WEBAUTH_REDIRECT 1 permit
config acl rule protocol ACL_WEBAUTH_REDIRECT 1 6
config acl rule source port range ACL_WEBAUTH_REDIRECT 1 0 65535
config acl rule destination address ACL_WEBAUTH_REDIRECT 1 10.1.200.11 255.255.255.255
config acl rule destination port range ACL_WEBAUTH_REDIRECT 1 8905 8905
config acl rule add ACL_WEBAUTH_REDIRECT 1
config acl rule action ACL_WEBAUTH_REDIRECT 1 permit
config acl rule protocol ACL_WEBAUTH_REDIRECT 1 6
config acl rule source address ACL_WEBAUTH_REDIRECT 1 10.1.200.11 255.255.255.255
config acl rule source port range ACL_WEBAUTH_REDIRECT 1 8905 8905
config acl rule destination port range ACL_WEBAUTH_REDIRECT 1 0 65535
config acl rule add ACL_WEBAUTH_REDIRECT 1
config acl rule action ACL_WEBAUTH_REDIRECT 1 permit
config acl rule protocol ACL_WEBAUTH_REDIRECT 1 17
config acl rule source port range ACL_WEBAUTH_REDIRECT 1 0 65535
config acl rule destination port range ACL_WEBAUTH_REDIRECT 1 53 53
config acl rule add ACL_WEBAUTH_REDIRECT 1
config acl rule action ACL_WEBAUTH_REDIRECT 1 permit
config acl rule protocol ACL_WEBAUTH_REDIRECT 1 17
config acl rule source port range ACL_WEBAUTH_REDIRECT 1 53 53
config acl apply ACL_WEBAUTH_REDIRECT
config acl delete BLACKHOLE
config acl create BLACKHOLE
config acl rule add BLACKHOLE 1
config acl rule action BLACKHOLE 1 permit
config acl rule protocol BLACKHOLE 1 6
config acl rule source port range BLACKHOLE 1 0 65535
config acl rule destination address BLACKHOLE 1 10.1.200.12 255.255.255.255
config acl rule destination port range BLACKHOLE 1 8444 8444
config acl rule add BLACKHOLE 1
config acl rule action BLACKHOLE 1 permit
config acl rule protocol BLACKHOLE 1 6
config acl rule source address BLACKHOLE 1 10.1.200.12 255.255.255.255
config acl rule source port range BLACKHOLE 1 8444 8444
config acl rule destination port range BLACKHOLE 1 0 65535
config acl rule add BLACKHOLE 1
config acl rule action BLACKHOLE 1 permit
config acl rule protocol BLACKHOLE 1 6
config acl rule source port range BLACKHOLE 1 0 65535
config acl rule destination address BLACKHOLE 1 10.1.200.11 255.255.255.255
config acl rule destination port range BLACKHOLE 1 8444 8444
config acl rule add BLACKHOLE 1
config acl rule action BLACKHOLE 1 permit
config acl rule protocol BLACKHOLE 1 6
config acl rule source address BLACKHOLE 1 10.1.200.11 255.255.255.255
config acl rule source port range BLACKHOLE 1 8444 8444
config acl rule destination port range BLACKHOLE 1 0 65535
config acl rule add BLACKHOLE 1
config acl rule action BLACKHOLE 1 permit
config acl rule protocol BLACKHOLE 1 17
config acl rule source port range BLACKHOLE 1 0 65535
config acl rule destination port range BLACKHOLE 1 53 53
config acl rule add BLACKHOLE 1
config acl rule action BLACKHOLE 1 permit
config acl rule protocol BLACKHOLE 1 17
config acl rule source port range BLACKHOLE 1 53 53
config acl rule destination port range BLACKHOLE 1 0 65535
config acl apply BLACKHOLE
config wlan create 11 ISE ISE
config wlan interface 11 ACCESS
config wlan radius_server auth add 11 11
config wlan radius_server auth add 11 12
config wlan radius_server acct add 11 11
config wlan radius_server acct add 11 12
config wlan radius_server acct interim-update 0 11
config wlan radius_server acct interim-update enable 11
config wlan aaa-override enable 11
config wlan usertimeout 180 11
config wlan nac radius enable 11
config wlan profiling radius all enable 11
config wlan enable 11
config wlan create 12 OPEN OPEN
config wlan interface 12 GUEST
config wlan security wpa disable 12
config wlan mac-filtering enable 12
config wlan radius_server auth add 12 11
config wlan radius_server auth add 12 12
config wlan radius_server acct add 12 11
config wlan radius_server acct add 12 12
config wlan radius_server acct interim-update 0 12
config wlan radius_server acct interim-update enable 12
config wlan aaa-override enable 12
config wlan session-timeout 12 1800
config wlan usertimeout 180 12
config wlan chd 12 disable
config wlan ccx AironetIeSupport disable 12
config wlan dhcp_server 12 0.0.0.0 required
config wlan nac radius enable 12
config wlan profiling radius all enable 12
config wlan enable 12
config network web-auth captive-bypass enable
save config
|
Configuration for Cisco IOS Switch Interface Connected to the WLC
description WLC Port 1
switchport trunk encapsulation dot1q
switchport trunk native vlan 60
switchport mode trunk
|
Configuration for Cisco IOS Switch SVI
interface vlan 10
description ACCESS
ip address 10.1.10.1 255.255.255.0
ip helper-address 10.1.200.10
ip helper-address 10.1.200.11
interface vlan 50
description GUEST
ip address 10.1.50.1 255.255.255.0
ip helper-address 10.1.200.10
ip helper-address 10.1.200.11
|
Appendix B: Design Considerations
FlexConnect AP & WLAN
FlexConnect mode, formerly known as H-REAP mode, allows APs to locally switch user traffic for certain WLANs typically deployed in branch offices. That allows wireless traffic to stay within the branch office. In this design, when an endpoint associates to a FlexConnect enabled WLAN, the endpoint authenticates inside the CAPWAP tunnel from the LAP to the controller. However, once authenticated, the traffic is switched locally from the LAP to the local LAN instead of through the central Wireless Controller. The integration with ISE and FlexConnect mode AP has been supported since WLC v7.5. However, the integration requires a specific configuration. Aside from configuring WLANs and APs into FlexConnect mode, the Redirect ACLs also must be re-created as FlexConnect ACLs, and downloaded to the FlexConnect group or individual APs.
First create ACL_WEBAUTH_REDIRECT & BLACKHOLE FlexConnect ACLs
config flexconnect acl create ACL_WEBAUTH_REDIRECT
config flexconnect acl rule add ACL_WEBAUTH_REDIRECT 1
config flexconnect acl rule action ACL_WEBAUTH_REDIRECT 1 permit
config flexconnect acl rule protocol ACL_WEBAUTH_REDIRECT 1 6
config flexconnect acl rule source port range ACL_WEBAUTH_REDIRECT 1 0 65535
config flexconnect acl rule destination address ACL_WEBAUTH_REDIRECT 1 10.1.200.12 255.255.255.255
config flexconnect acl rule destination port range ACL_WEBAUTH_REDIRECT 1 8443 8444
config flexconnect acl rule add ACL_WEBAUTH_REDIRECT 1
config flexconnect acl rule action ACL_WEBAUTH_REDIRECT 1 permit
config flexconnect acl rule protocol ACL_WEBAUTH_REDIRECT 1 6
config flexconnect acl rule source address ACL_WEBAUTH_REDIRECT 1 10.1.200.12 255.255.255.255
config flexconnect acl rule source port range ACL_WEBAUTH_REDIRECT 1 8443 8444
config flexconnect acl rule destination port range ACL_WEBAUTH_REDIRECT 1 0 65535
config flexconnect acl rule add ACL_WEBAUTH_REDIRECT 1
config flexconnect acl rule action ACL_WEBAUTH_REDIRECT 1 permit
config flexconnect acl rule protocol ACL_WEBAUTH_REDIRECT 1 6
config flexconnect acl rule source port range ACL_WEBAUTH_REDIRECT 1 0 65535
config flexconnect acl rule destination address ACL_WEBAUTH_REDIRECT 1 10.1.200.12 255.255.255.255
config flexconnect acl rule destination port range ACL_WEBAUTH_REDIRECT 1 8905 8905
config flexconnect acl rule add ACL_WEBAUTH_REDIRECT 1
config flexconnect acl rule action ACL_WEBAUTH_REDIRECT 1 permit
config flexconnect acl rule protocol ACL_WEBAUTH_REDIRECT 1 6
config flexconnect acl rule source address ACL_WEBAUTH_REDIRECT 1 10.1.200.12 255.255.255.255
config flexconnect acl rule source port range ACL_WEBAUTH_REDIRECT 1 8905 8905
config flexconnect acl rule destination port range ACL_WEBAUTH_REDIRECT 1 0 65535
config flexconnect acl rule add ACL_WEBAUTH_REDIRECT 1
config flexconnect acl rule action ACL_WEBAUTH_REDIRECT 1 permit
config flexconnect acl rule protocol ACL_WEBAUTH_REDIRECT 1 6
config flexconnect acl rule source port range ACL_WEBAUTH_REDIRECT 1 0 65535
config flexconnect acl rule destination address ACL_WEBAUTH_REDIRECT 1 10.1.200.11 255.255.255.255
config flexconnect acl rule destination port range ACL_WEBAUTH_REDIRECT 1 8443 8444
config flexconnect acl rule add ACL_WEBAUTH_REDIRECT 1
config flexconnect acl rule action ACL_WEBAUTH_REDIRECT 1 permit
config flexconnect acl rule protocol ACL_WEBAUTH_REDIRECT 1 6
config flexconnect acl rule source address ACL_WEBAUTH_REDIRECT 1 10.1.200.11 255.255.255.255
config flexconnect acl rule source port range ACL_WEBAUTH_REDIRECT 1 8443 8444
config flexconnect acl rule destination port range ACL_WEBAUTH_REDIRECT 1 0 65535
config flexconnect acl rule add ACL_WEBAUTH_REDIRECT 1
config flexconnect acl rule action ACL_WEBAUTH_REDIRECT 1 permit
config flexconnect acl rule protocol ACL_WEBAUTH_REDIRECT 1 6
config flexconnect acl rule source port range ACL_WEBAUTH_REDIRECT 1 0 65535
config flexconnect acl rule destination address ACL_WEBAUTH_REDIRECT 1 10.1.200.11 255.255.255.255
config flexconnect acl rule destination port range ACL_WEBAUTH_REDIRECT 1 8905 8905
config flexconnect acl rule add ACL_WEBAUTH_REDIRECT 1
config flexconnect acl rule action ACL_WEBAUTH_REDIRECT 1 permit
config flexconnect acl rule protocol ACL_WEBAUTH_REDIRECT 1 6
config flexconnect acl rule source address ACL_WEBAUTH_REDIRECT 1 10.1.200.11 255.255.255.255
config flexconnect acl rule source port range ACL_WEBAUTH_REDIRECT 1 8905 8905
config flexconnect acl rule destination port range ACL_WEBAUTH_REDIRECT 1 0 65535
config flexconnect acl rule add ACL_WEBAUTH_REDIRECT 1
config flexconnect acl rule action ACL_WEBAUTH_REDIRECT 1 permit
config flexconnect acl rule protocol ACL_WEBAUTH_REDIRECT 1 17
config flexconnect acl rule source port range ACL_WEBAUTH_REDIRECT 1 0 65535
config flexconnect acl rule destination port range ACL_WEBAUTH_REDIRECT 1 53 53
config flexconnect acl rule add ACL_WEBAUTH_REDIRECT 1
config flexconnect acl rule action ACL_WEBAUTH_REDIRECT 1 permit
config flexconnect acl rule protocol ACL_WEBAUTH_REDIRECT 1 17
config flexconnect acl rule source port range ACL_WEBAUTH_REDIRECT 1 53 53
config flexconnect acl apply ACL_WEBAUTH_REDIRECT
config flexconnect acl create BLACKHOLE
config flexconnect acl rule add BLACKHOLE 1
config flexconnect acl rule action BLACKHOLE 1 permit
config flexconnect acl rule protocol BLACKHOLE 1 6
config flexconnect acl rule source port range BLACKHOLE 1 0 65535
config flexconnect acl rule destination address BLACKHOLE 1 10.1.200.12 255.255.255.255
config flexconnect acl rule destination port range BLACKHOLE 1 8444 8444
config flexconnect acl rule add BLACKHOLE 1
config flexconnect acl rule action BLACKHOLE 1 permit
config flexconnect acl rule protocol BLACKHOLE 1 6
config flexconnect acl rule source address BLACKHOLE 1 10.1.200.12 255.255.255.255
config flexconnect acl rule source port range BLACKHOLE 1 8444 8444
config flexconnect acl rule destination port range BLACKHOLE 1 0 65535
config flexconnect acl rule add BLACKHOLE 1
config flexconnect acl rule action BLACKHOLE 1 permit
config flexconnect acl rule protocol BLACKHOLE 1 6
config flexconnect acl rule source port range BLACKHOLE 1 0 65535
config flexconnect acl rule destination address BLACKHOLE 1 10.1.200.11 255.255.255.255
config flexconnect acl rule destination port range BLACKHOLE 1 8444 8444
config flexconnect acl rule add BLACKHOLE 1
config flexconnect acl rule action BLACKHOLE 1 permit
config flexconnect acl rule protocol BLACKHOLE 1 6
config flexconnect acl rule source address BLACKHOLE 1 10.1.200.11 255.255.255.255
config flexconnect acl rule source port range BLACKHOLE 1 8444 8444
config flexconnect acl rule destination port range BLACKHOLE 1 0 65535
config flexconnect acl rule add BLACKHOLE 1
config flexconnect acl rule action BLACKHOLE 1 permit
config flexconnect acl rule protocol BLACKHOLE 1 17
config flexconnect acl rule source port range BLACKHOLE 1 0 65535
config flexconnect acl rule destination port range BLACKHOLE 1 53 53
config flexconnect acl rule add BLACKHOLE 1
config flexconnect acl rule action BLACKHOLE 1 permit
config flexconnect acl rule protocol BLACKHOLE 1 17
config flexconnect acl rule source port range BLACKHOLE 1 53 53
config flexconnect acl rule destination port range BLACKHOLE 1 0 65535
config flexconnect acl apply BLACKHOLE
|
Once created, add them to the FlexConnect Aps.
config ap flexconnect policy acl add ACL_WEBAUTH_REDIRECT AP_NAME
config ap flexconnect policy acl add BLACKHOLE AP_NAME
|
Note: While FlexConnect mode supports additional configurations such as Local authentication, those options have not been tested as part of ISE integration. Also, while this document goes over the required configuration using individual APs, it is generally easier to configure FlexConnect groups to manage settings for the APs. Also note following caveats for FlexConnect mode AP Local Switching deployment with ISE:
-
Endpoints utilizing FlexConnect must be able to access the ISE node
-
FlexConnect ACL does not support DNS ACL
-
TrustSec for locally switched traffic is not supported
While it is the FlexConnect ACL that gets applied to the FlexConnect endpoint sessions, older versions of WLC may fail to apply the FlexConnect ACL without regular ACL with same ACL name already in place. At minimum it will require a regular ACL name registered to the WLC. In that case, simply create an empty ACL as following:
config acl create ACL_WEBAUTH_REDIRECT
config acl apply ACL_WEBAUTH_REDIRECT
config acl create BLACKHOLE
config acl apply BLACKHOLE
|
Auto-Anchored WLAN
Customers often configure Auto-Anchor (AKA Guest Tunneling) to tunnel guest WLAN traffic to an anchor controller residing in a DMZ for added security. This is a supported configuration with ISE Central WebAuth. However, there is specific configuration to make this work. This can be setup normally for an Auto-Anchor setup with one exception, which is the RADIUS Accounting server needs to be disabled on the Anchor Controller WLAN. Assuming the OPEN WLAN is being anchored, here is an example of WLAN setting on the anchor controller.
config wlan create 12 OPEN OPEN
config wlan interface 12 GUEST
config wlan security wpa disable 12
config wlan mac-filtering enable 12
config wlan radius_server auth disable 12
config wlan radius_server acct disable 12
config wlan radius_server acct interim-update disable 12
config wlan aaa-override enable 12
config wlan session-timeout 12 1800
config wlan usertimeout 180 12
config wlan chd 12 disable
config wlan ccx AironetIeSupport disable 12
config wlan dhcp_server 12 0.0.0.0 required
config wlan nac radius enable 12
config wlan profiling radius all enable 12
config wlan enable 12
|
Note: The RADIUS settings are disabled in the preceding example, however, the anchor controller will receive the ACL name to apply to the session from ISE relayed by the foreign controller in the mobility message. It is essential that the anchor controller configuration includes the redirect ACL, so it can be applied to the user session when called upon by the foreign controller.
Appendix C: Use case specific sample configurations
Configuration for WLC Running 8.x Code for 802.1X WLAN
Configuration for previous versions of WLC is identical with the exception of interim accounting settings under the WLAN configuration. Please refer to main section of the document for proper configuration for previous versions.
| ISE IP |
10.1.200.11 |
| RADIUS shared secret |
ISEc0ld |
| RADIUS ID |
11 |
| User VLAN |
10 |
| User VLAN Name |
ACCESS |
| User VLAN dynamic IP |
10.1.10.61 |
| User VLAN DHCP server |
10.1.200.10 |
| User VLAN gateway |
10.1.10.1 |
| User WLAN Name |
ISE |
| User WLAN ID |
11 |
config interface create ACCESS 10
config interface port ACCESS 1
config interface address dynamic-interface ACCESS 10.1.10.61 255.255.255.0 10.1.10.1
config interface dhcp dynamic-interface ACCESS primary 10.1.200.10
config radius auth add 11 10.1.200.11 1812 ascii ISEc0ld
config radius auth disable 11
config radius auth management 11 disable
config radius auth retransmit-timeout 11 5
config radius auth rfc3576 enable 11
config radius auth enable 11
config radius acct add 11 10.1.200.11 1813 ascii ISEc0ld
config radius acct disable 11
config radius acct retransmit-timeout 11 5
config radius acct enable 11
config wlan create 11 ISE ISE
config wlan interface 11 ACCESS
config wlan radius_server auth add 11 11
config wlan radius_server acct add 11 11
config wlan radius_server acct interim-update 0 11
config wlan radius_server acct interim-update enable 11
config wlan aaa-override enable 11
config wlan usertimeout 180 11
config wlan nac radius enable 11
config wlan profiling radius all enable 11
config wlan enable 11
|



