- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Anyconnect XML settings.
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 07-06-2015 05:37 PM
For Anyconnect preferences part 1 and part 2 check the link below
https://supportforums.cisco.com/document/12549161/anyconnect-xml-preferences
Backup Server
You can configure a list of backup servers the client uses in case the user-selected server fails.
You can use the IP or the FQDN of the ASA.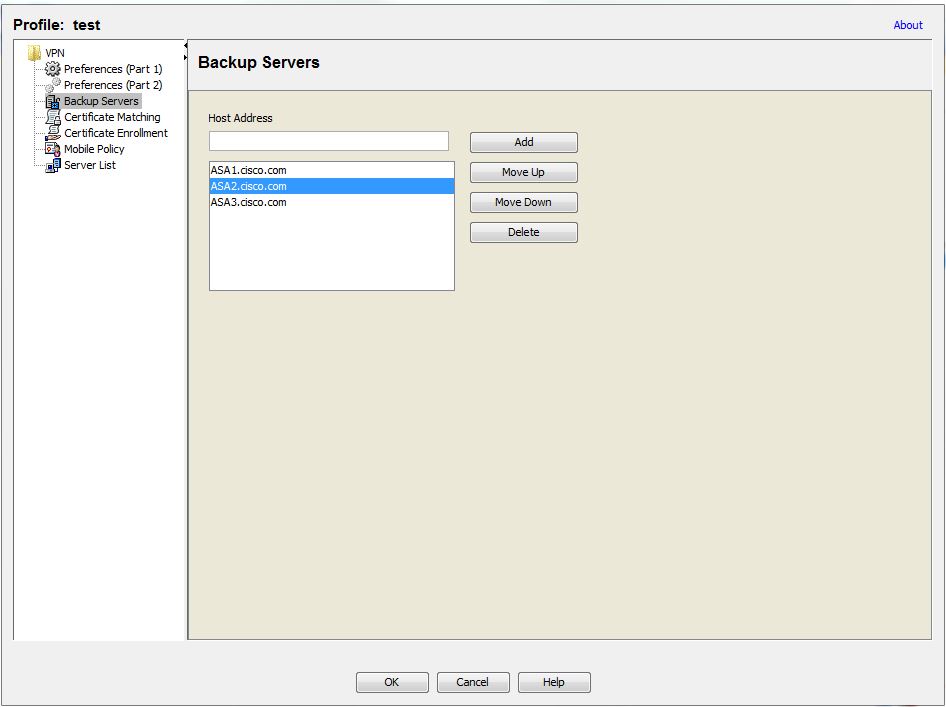
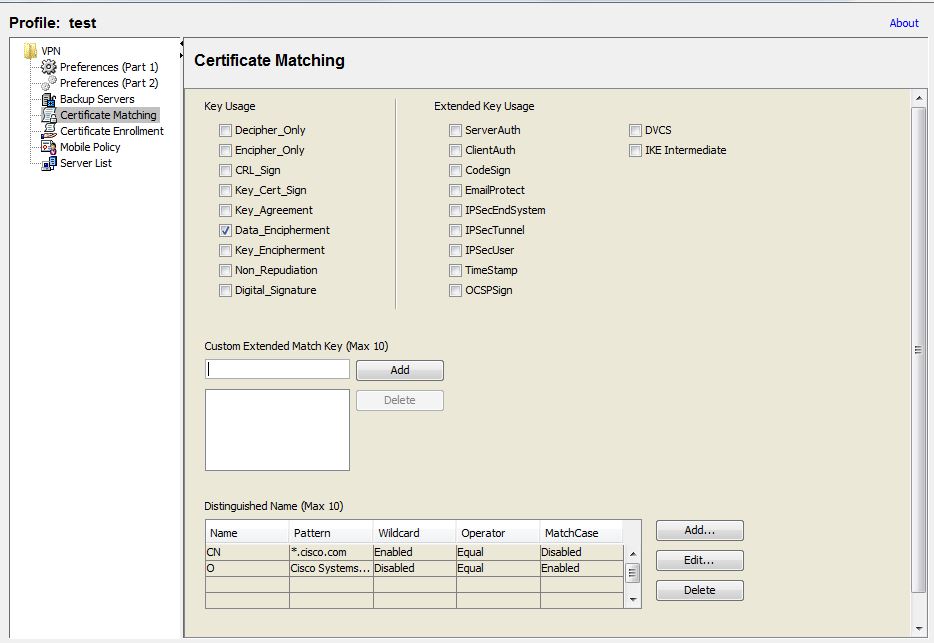
Certificate matching
Anyconnect can limit its search of certificates to those certificates that match a specific set of keys
Key Usage:
Use the following Certificate Key attributes for choosing acceptable client certificates
- Decipher_Only: Deciphering data, and that no other bit (except Key_Agreement) is set.
- Encipher_Only: Enciphering data and any other bit (except Key_Agreement) is not set.
- CRL_Sign: Verifying the CA signature on a CRL.
- Key_Cert_Sign: Verifying the CA signature on a certificate.
- Key_Agreement: Key agreement.
- Data_Encipherment: Encrypting data other than Key_Encipherment.
- Key_Encipherment : Encrypting keys.
- Non_Repudiation : Verifying digital signatures protecting against falsely denying some action, other than Key_Cert_sign or CRL_Sign.
- Digital_Signature: Verifying digital signatures other than Non_Repudiation, Key_Cert_Sign or CRL_Sign.
Extended Key Usage:
Use these Extended Key Usage settings. The OIDs are included in parenthesis ():
- ServerAuth (1.3.6.1.5.5.7.3.1)
- ClientAuth (1.3.6.1.5.5.7.3.2)
- CodeSign (1.3.6.1.5.5.7.3.3)
- EmailProtect (1.3.6.1.5.5.7.3.4)
- IPsecEndSystem (1.3.6.1.5.5.7.3.5)
- IPsecTunnel (1.3.6.1.5.5.7.3.6)
- IPsecUser (1.3.6.1.5.5.7.3.7)
- TimeStamp (1.3.6.1.5.5.7.3.8)
- OCSPSign (1.3.6.1.5.5.7.3.9)
- DVCS (1.3.6.1.5.5.7.3.10)
Custom Extended Match Key (Max 10):
Specifies custom extended match keys, if any (maximum 10). A certificate must match all of the specified key(s) you enter. Enter the key in the OID format (for example, 1.3.6.1.5.5.7.3.1).
Distinguished Name (Max 10):
Specifies distinguished names (DNs) for exact match criteria in choosing acceptable client certificates.
- CN—Subject Common Name
- C—Subject Country
- DC—Domain Component
- DNQ—Subject Dn Qualifier
- EA—Subject Email Address
- GENQ—Subject Gen Qualifier
- GN—Subject Given Name
- I—Subject Initials
- L—Subject City
- N—Subject Unstruct Name
- O—Subject Company
- OU—Subject Department
- SN—Subject Sur Name
- SP—Subject State
- ST—Subject State
- T—Subject Title
- ISSUER-CN—Issuer Common Name
- ISSUER-DC—Issuer Component
- ISSUER-SN—Issuer Sur Name
- ISSUER-GN—Issuer Given Name
- ISSUER-N—Issuer Unstruct Name
- ISSUER-I—Issuer Initials
- ISSUER-GENQ—Issuer Gen Qualifier
- ISSUER-DNQ—Issuer Dn Qualifier
- ISSUER-C—Issuer Country
- ISSUER-L—Issuer City
- ISSUER-SP—Issuer State
- ISSUER-ST—Issuer State
- ISSUER-O—Issuer Company
- ISSUER-OU—Issuer Department
- ISSUER-T—Issuer Title
- ISSUER-EA—Issuer Email Address
Certificate enrollment
Anyconnect can use the Simple Certificate Enrollment Protocol (SCEP) to provision and renew a certificate as part of client authentication. The goal of SCEP is to support the secure issuance of certificates to network devices in a scalable manner, using existing technology.
Certificate enrollment using SCEP is supported by Anyconnect IPSec and SSL VPN connections to the ASA in the following ways:
SCEP Proxy: The ASA acts as a proxy for SCEP requests and responses between the client and the Certificate Authority (CA). The CA must be accessible to the ASA, not the Anyconnect client, since the client does not access the CA directly.
Enrollment is always initiated automatically by the client. No user involvement is necessary.
Legacy SCEP: The Anyconnect client communicates with the CA directly to enroll and obtain a certificate. The CA must be accessible to the Anyconnect client, not the ASA, through an established VPN tunnel or directly on the same network the client is on.
Enrollment is initiated automatically by the client and may be initiated manually by the user if configured.
Certificate Authority Requirements
- All SCEP-compliant CAs, including IOS CA, Windows Server 2003 CA, and Windows Server 2008 CA, are supported.
- The CA must be in auto-grant mode; polling for certificates is not supported.
- You can configure some CAs to email users an enrollment password for an additional layer of security.
Notes:
- Clientless (browser-based) VPN access to the ASA does not support SCEP proxy, but WebLaunch (clientless-initiated Anyconnect) does.
- The ASA does not indicate why an enrollment failed, although it does log the requests received from the client. Connection problems must be debugged on the CA or the client.
- If you use %machineid%, then Hostscan/Posture must be loaded for the desktop client.
- For mobile clients, at least one certificate field must be specified
ASA Configuration
group-policy SPLIT attributes
scep-forwarding-url value http://server/certsrv/mscep/mscep.dll
tunnel-group SPLIT general-attributes
scep-enrollment enable
tunnel-group SPLIT webvpn-attributes
group-alias SPLIT enable
authentication certificate aaa
Certificate Expiration Threshold:
Specifies when Anyconnect should warn users that their certificate is going to expire.
Automatic SCEP Host:
The host attempts automatic certificate retrieval if this attribute specifies the ASA host name and connection profile (tunnel group) for which SCEP certificate retrieval is configured.
Display Get Cert Button:
Permits users to manually request provisioning or renewal of authentication certificates

Mobile policy
Currently depreciated, not supported on Anyconnect 3.0 or later, used by Windows Mobile devices.
Server list
HostName
An alias used to refer to the host, FQDN, or IP address, This will be the seen by the user.
Host Address
An IP address or Full-Qualified Domain Name (FQDN) used to refer to the host.
Primary Protocol
The encryption protocol for the VPN tunnel, either SSL (default) or IPSec with IKEv2.
Standard Authentication Only (IOS gateway)
Use this parameter to change the authentication method from the default proprietary Anyconnect EAP authentication method to a standards-based method.
Be aware that doing this limits the dynamic download features of the client and disables some features and disables the ability of the ASA to configure session timeout, idle timeout, disconnected timeout, split tunneling, split DNS, MSIE proxy configuration, and other features.
IKE Identity (IOS gateway)
If you choose a standards-based EAP authentication method, you can enter a group or domain as the client identity in this field. The client sends the string as the ID_GROUP type ID payload. By default, the string is *$AnyConnectClient$*
UserGroup
The connection profile (tunnel group) to use when connecting to the specified host.
If you specify the Primary Protocol as IPsec, the User Group must be the exact name of the connection profile (tunnel group). For SSL, the user group is the group-url or group-alias of the connection profile.
Additional mobile-only settings:
Apple iOS / Android Settings
Certificate authentication:
- Automatic: Anyconnect automatically chooses the client certificate with which to authenticate. Anyconnect views all the installed certificates, disregards those certificates that are out of date, applies the certificate matching criteria defined in VPN client profile, and then authenticates using the certificate that matches the criteria. This happens every time the user attempts to establish a VPN connection.
- Manual: Anyconnect searches for the certificate with which to authenticate just as it does with automatic authentication. Once Anyconnect finds a certificate that matches the certificate matching criteria defined in the VPN client profile, it assigns that certificate to the connection and it will not search for new certificates when users attempt to establish new VPN connections.
- Disabled: Client Certificate will never be used for authentication.
Apple iOS Only Settings
Reconnect when roaming between 3G/Wifi networks
The box is checked by default so AnyConnect will attempt to maintain the VPN connection when switching between 3G and Wifi networks. If you uncheck the box, AnyConnect will not attempt to maintain the VPN connection which switching between 3G and Wifi networks.
Connect on Demand
This area allows you to configure the Connect on Demand functionality provided by Apple iOS. Connect on Demand can only be checked if the Certificate Authentication field is set to Manual or Automatic
The Connect on Demand rules, defined by the Match Domain or Host and the On Demand Action fields
- Always connect: iOS will always attempt to initiate a VPN connection when rules in this list are matched.
- Connect if needed: iOS will attempt to initiate a VPN connection when rules in this list are matched only if the system could not resolve the address using DNS.
- Never connect: iOS will never attempt to initiate a VPN connection when rules in this list are matched. Any rules in this list will take precedence over Always connect or Connect if needed rules.

Hope it helps
- Randy -
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: