Introduction
Cisco ISE can be configured to enable strong client suppression when an authentication request from an endpoint fails five times with the same failure reason. Strong suppression rejects every request that it receives from that endpoint without processing it and is active for the configured Request Rejection interval in minutes. Only after the interval expires, the Cisco ISE will process the authentication request from that particular endpoint. If the request again fails with the same failure reason or a different one, the endpoint’s strong suppression is not renewed. It is renewed only if the request again fails five times with the same failure reason.
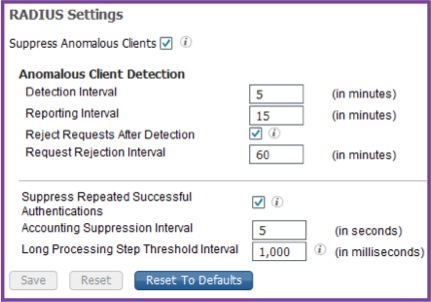
Configuration
1) Navigate to Administration > System > Settings > Protocols > RADIUS.
2) In the RADIUS settings Check the " Suppress Anomalous Clients" check box to detect the clients for which the authentications fail repeatedly. A summary of the failures will be reported every Reporting Interval.
3)Under Anomalous Client Detection section provide the following details:
a) Detection Interval - Time interval in minutes for the clients to be detected.
b) Reporting Interval - Time interval in minutes for the failed authentications to be reported.
c) Reject Requests After Detection - Ensure that this check box is checked to reject the requests after the clients are detected. The requests for anomalous clients will be rejected in every Request Rejection Interval.
d) Request Rejection Interval - This is the time interval in minutes for which the requests will be rejected. This option is available to be configured only when you have checked the "Reject Requests After Detection" checkbox as mentioned in the previous step.
e) Suppress Repeated Successful Authentications - This check box should be checked to prevent repeated reporting of successful authentication requests in last 24 hours that have no changes in identity context, network device, and authorization.
f) Accounting Suppression Interval - The time interval in seconds for which the reporting of accounting requests are to be suppressed.
g) Long Processing Step Threshold Interval - This parameter is to set the maximum time allowed for each step in the authentication process to be completed. If the time exceeds in a specific step, this is highlighted in the authentication details report.
4) Above steps completes the configuration of Anomalous Clients Suppression.
Find the image below for more information about the configuration steps:
Problem
Specific set of users/devices are temporarily blocked by ISE from making connection attempts. How can we ensure that the devices are allowed to make connection attempts without any issues?
Solution
This issue occurs when the user/device is detected to be anomalous and hence the request from these users/devices are rejected untill the "Request Rejection Interval" expires. Reducing the interval to a lower time or disabling the option of rejecting the requests from the clients detected will solve this issue.
Source