Introduction
Groups and Attributes Mapping from Radius Token Server
Overview
For some types of external user databases, ACS supports the assignment of users to specific ACS groups based on the RADIUS authentication response from the external user database.
ACS provides this assignment in addition to the unknown user group mapping described in Group Mapping by External User Database.
RADIUS-based group specification overrides group mapping.
To provide the per-user group mapping feature in ACS 5.3, use the attribute retrieval and authorization mechanism for users that are authenticated with an external RADIUS identity store.
For this, you must configure the RADIUS identity store to return authentication responses that contain the [009\001] cisco-av-pair attribute with the following value:
ACS:CiscoSecure-Group-Id=N, where N is a value returned from the external radius server to ACS.
Then, this attribute is available in the policy configuration pages of the ACS web interface while creating authorization and group mapping rules.
You can use the RADIUS attributes retrieved during authentication against the RADIUS identity store in ACS policy conditions for authorization and group mapping. You can select the attributes that you want to use in policy conditions while configuring the RADIUS identity store. These attributes are kept in the RADIUS identity store dedicated dictionary and can be used to define policy conditions.
You cannot query the RADIUS server for the requested attributes. You can only configure the RADIUS identity store to return the requested attributes. These attributes are available in the Access-Accept response as part of the attributes list.
ACS Configuration
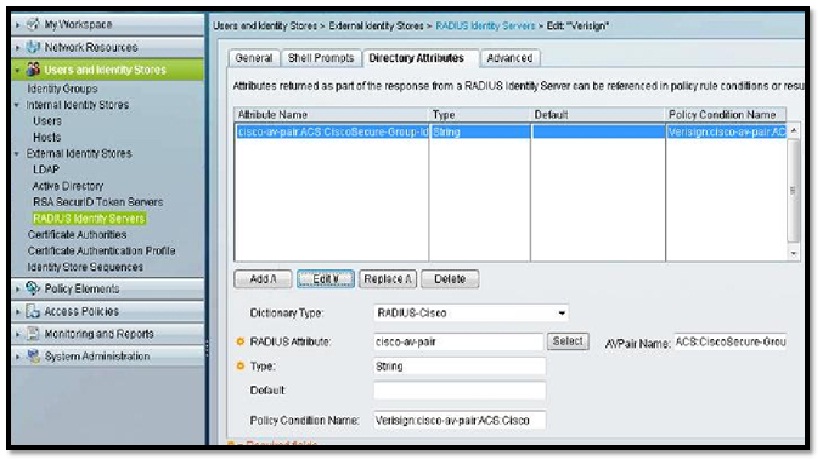
In the below screenshot, under the “Directory Attributes” of “Radius Token Servers”, we have added a “cisco-av-pair” dictionary and the AV pair name is “ACS:CiscoSecure-Group-Id”.
You can give any policy condition name which will be available as an option under the Authorization section of Access Policy.
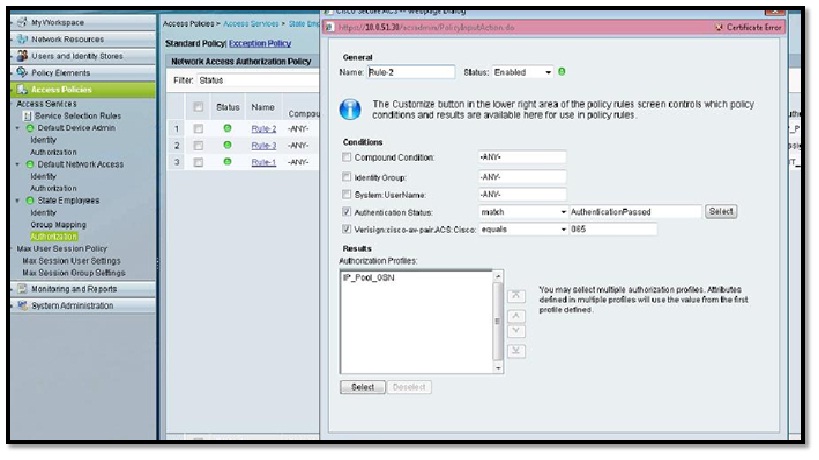
In the below screen shot, we have used the “Policy Condition Name” defined earlier.
In this case, the value returned from Radius Identity/Token server for the attribute “ACS:CiscoSecure-Group-Id” is supposed to be “065” and based on that he will hit the desired authorization rule.
Attributes visible under ACS Monitoring Report
SSG Attributes:
Cisco-AVPairs: ip:source-ip=xx.xx.xx.xx
Other Attributes: ACSVersion=acs-5.3.0.40-B.839
ConfigVersionId=55
Protocol=Radius
State=29SessionID=farnyb/148436699/52;
Called-Station-ID=xx.xx.xx.xx
cisco-av-pair:ACS:CiscoSecure-Group-Id=065
Device IP Address=xx.xx.xx.xx
We need to go through the ACS logs to make sure what exact value for the "cisco-av-pair:ACS:CiscoSecure-Group-Id" being returned by the radius-token-server. The same value need to be used in the authorization rule that we have created above.
Please feel free to comment in case of any query.