Question
How can I block an IP address on Firepower Threat Defense (FTD) using Threat Response?
Answer
Requirements: Threat Response admin credentials and Firepower Management Center (FMC) with admin credentials. Operational FTD registered to FMC configured with an Access Control policy.
Quick Summary:
- Create an Indicator of type IP watchlist
- Create a Saved Feed referencing the Indicator
- Create a judgement from Threat Response and tie it to the indicator
- Add the Saved Feed to the FMC Threat Intelligence Director
- IP address is blocked by FTD
Note: It is recommended to create a separate Indicator and Saved Feed for IPv4 addresses, IPv6 Addresses, URLs, Domains, and SHA-256 file hashes. This document details the process to block IPv4 addresses on Firepower, however the same process can be followed for other intelligence types. (minor differences will be noted).
- From Threat Response navigate to Intelligence —> Indicators —>and set the Source to Private. Select Create Indicator.
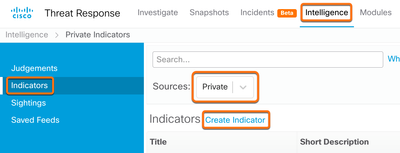
- Create a new Indicator with the required fields of Title, Expiration, and Description. Other fields are optional based on user preference. It is best practice to select IP Watchlist and Private Threat Feed in the Indicator Type section.
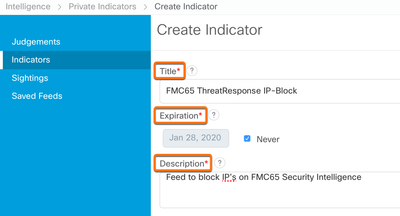
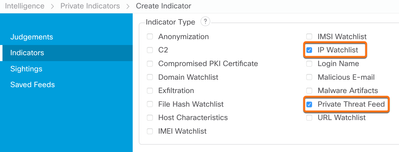
Select Save at the bottom of the page to finish creating the indicator.
Note: Select URL Watchlist instead of IP watchlist if creating an indicator for URLs, Domain Watchlist for Domains, and File Hash Watchlist for SHA-256 file hashes.
- From the Intelligence page navigate to Saved Feeds and select Create Feed URL.
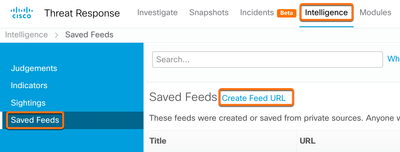
- Enter a Title and choose the Indicator from step 2. Set the output to Observables and select Save to generate the Feed URL.
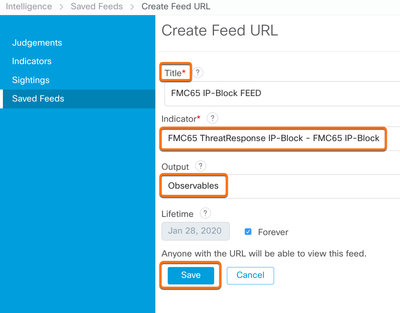
- Copy the generated Feed URL. Keep this URL private as there is no authentication required to view it. We will use this URL below in step 9.
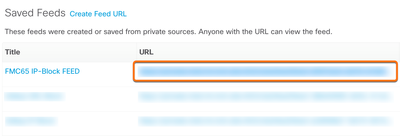
- From the Threat Response investigate UI use the pivot menu to create a Judgement.
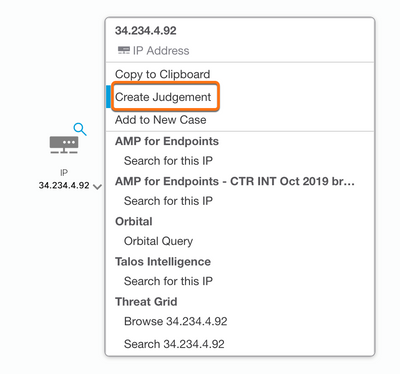
- Tie the Indicator from step 2 to the Judgment. Choose a Disposition and Expiration then select Save.
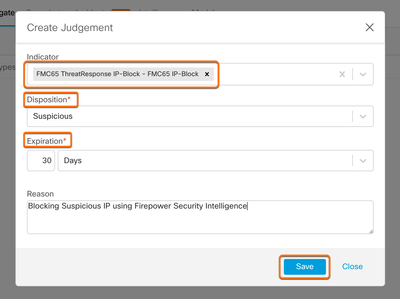
This adds an iP address to the feed created in step 4. Navigating to the feed URL from step 5 will allow us to view all the observables currently added.
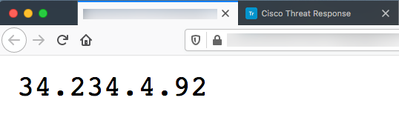
Additionally, creating a new Judgement for another IP address and tying it to the same Indicator from step 2 will append it to the list. For example, creating a judgement for 54.81.104.233 and tying it to the Indicator labeled “FMC65 ThreatResponse IP-Block” will also block the IP on FTD.
- From FMC navigate to Intelligence à Sources. Click the + icon in the upper right-hand corner to add a new Intelligence Source
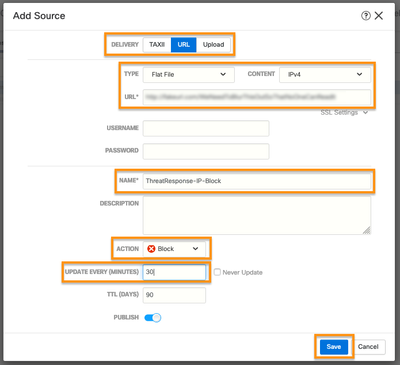
- Select URL as the Delivery method, Flat File as the Type, and IPv4 as the Content. Paste in the Feed URL from step 5. Give the source a Name. Select Block as the Action, set the Update Interval to 30 minutes, and click Save.
Note: Select IPv6, SHA-256, Domain, or URL to consume different types of intelligence. The FMC only supports ingesting homogeneous feeds, but will block all of the intelligence simultaneously.`
- Allow the feed to complete initial synchronization (you may need to click the refresh icon to see the “last updated” time update). Then click the Observables tab.
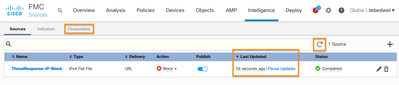
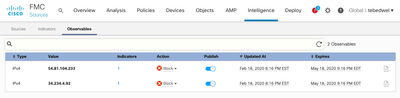
- You should now see the Judgements that you added in step 3 listed in the FMC Intelligence Director. These observables have been dynamically published to your managed Firepower devices and are being blocked.
By Aditya Sankar, Cisco Threat Response Team