- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Threat Centric NAC Service: Integrate Cisco ISE with Qualys
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
05-30-2020 02:05 AM - edited 08-04-2024 01:03 AM
Introduction
Cisco Identity Services Engine (ISE) gives you intelligent Integrated protection through intent-based policy and compliance solution. Cisco ISE supports TC-NAC integration with in-house and third party vendors such as AMP for endpoint Security, CTA, Qualys, Nexpose and Tenable Security Center to get the vulnerability assessment of endpoints and give access to endpoints based on vulnerability, compliance and threats seen on endpoint.
Components
Cisco Identity Services Engine (ISE)
Qualys Information Security and Compliance.
ISE Configuration
Considering you have already deployed a Qualys instance (vm or appliance) in your intranet environment to scan and provide vulnerability information to ISE, This section will give you an idea on how to integrate Cisco Identity Services Engine with Qualys Server.
- Login to ISE admin portal with super admin privileges
- In order to enable TC-NAC, you must have Apex license available. Ensure that your ISE deployment has Apex License available.
- Navigate to Administration > System > Deployment > <ISE PSN Node> and enable check box “Enable Threat Centric NAC Service”
- Wait for few minutes for the ISE to bring up the TC NAC adaptor instance. You can check the service status by login to CLI and executing command “show application status ise”.
- Navigate to Administration > Threat Centric NAC > Third Party Vendors and click on ADD. Select “Qualys : VA” as the vendor and provide Instance Name for ISE reference.
- Save the configuration and wait for few seconds to show the status as Ready to Configure
- Fill in the details such as REST API based on the Qualys cloud server that you are using, port, username & password. If ISE in your organization could reach Qualys cloud server through proxy, then please provide proxy details too and click on Next.
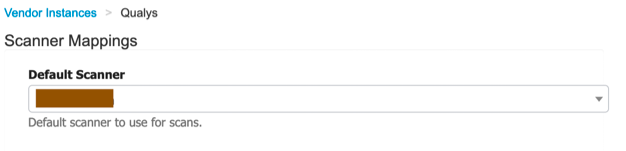
- Select the scanner from the drop down, leave the rest of the settings as default and click on Next
- Leave the default configuration as is and click on Next to review and save the configuration. ISE will try to connect to Qualys server and if the connection is successful, ISE downloads Knowledge base from Qualys server. It will take few minutes for ISE to complete the process.
- Navigate to Administration > Identity Management > Identities > Users, click on Add to configure an internal user. Provide Details like username and password and submit the configuration.
- Navigate to Work Centers > Network Access > Network Resources > Network Devices, click on ADD to configure Network Access device. Provide details such as name, IP address of WLC (in this example) and shared secret.
- Navigate to Policy > Policy Elements > Results > Authorization > Authorization Profile and click on Add. Provide Name of the authorization profile, and enable Assess Vulnerabilities under common tasks by selecting Qualys (name of the Qualys server given earlier) as the adaptor instance.
- Navigate to Policy > Policy sets > Default policy set. Leave the authentication policies as is and configure one authorization policy for assessing vulnerabilities of successful dot1x users’ devices by Qualys and select authorization profile created above.
- Go to Global authorization policy and configure one authorization policy for dot1x users and having vulnerability greater than 4 (say) to give restricted/deny/ISE blackhole page.
NOTE: it is advised to create global exception policies as it is going to be common for all policy sets and better way to give restricted access if vulnerable endpoints coming onto your network without assessing any other authorization rules.
Troubleshooting
If ISE is unable to connect to Qualys server through the REST API..
- Check for certificates whether Qualys server is trusted under Trusted Certificates store.
- Check whether proxy details are proper or not.
- Check the connectivity to Qualys whether Qualys server and port is allowed for ISE in your organization.
End user perspective and Validation
- Authenticate the device using the user credentials created in earlier section. (windows device used in this demonstration).
- Ensure you have a successful session authenticated and authorized against ISE by login into ISE and navigating to Operation > RADIUS > Live Logs
- Ensure ISE submitted the authenticated session of endpoint for vulnerability assessment to Qualys by going to Operation > Reports > Reports > Threat Centric NAC > Vulnerability Assessment
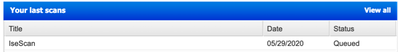
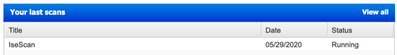
- Login to your Qualys Dashboard and look for the active scans. Based on your scanning selection in Qualys, it will take few minutes to complete the scanning and give back the results to ISE.
- Navigate to Operations > RADIUS > Live Logs and check whether endpoint received different authorization based on vulnerability report received from Qualys
- Once Qualys scanning is completed, ISE will give different authorization based on the global exception policy written earlier.
- Navigate to Context Visibility > Endpoints > Endpoints > <endpoint> , check for vulnerabilities that was learnt from Qualys
- Navigate to Context Visibility > Endpoints > Vulnerable Endpoints to check for vulnerabilities retrieved for the endpoint.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: