- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- How To Configure Wired 802.1X & MAB Authentication with ISE on a Router
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
09-06-2017 06:21 AM - edited 08-06-2024 12:49 PM
- Introduction
- Requirements
- ISE IP Address
- Router IP
- Router Configuration
- Add Network Device to ISE
- Create a User Identity
- Validate the User (Optional)
- Validate 802.1X with a Wired Client
- Validate MAB Failover with a Wired Client
Introduction
You want to demonstrate not only wireless 802.1X but also wired 802.1X with a single router that has a built-in AP and switchport(s). This guide will show you how to update the configuration to do 802.1X on one or more of the router switchports.
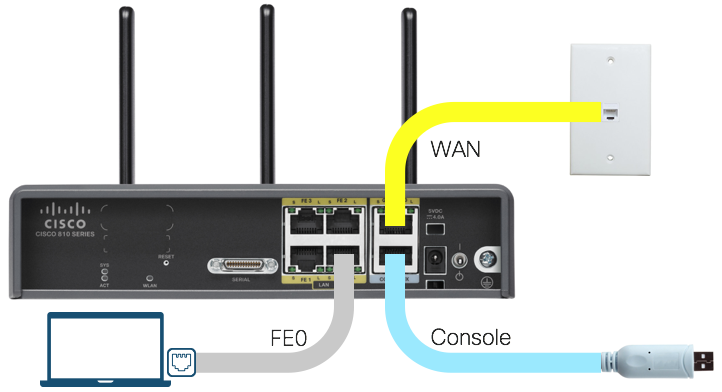
Requirements
This guide assumes you have Identity Services Engine (ISE) running in your lab or dCloud.
This guide was created using a Cisco 819HWD @ IOS 15.4(3)M1 and ISE 2.2.
Note that the 819HWD and 8xx series routers in general are only capable of VLAN-based enforcement on the FastEthernet switchports - it cannot handle downloadable ACLs from ISE.
ISE IP Address
Step 1: Find the IP address used for ISE.
If using ISE in dCloud, this should be in the topology diagram or in the demo documentation:

Step 2: Record the ISE IP address for use in the router's RADIUS configuration.
Router IP
Step 1: From the router's console, find and verify the router interface and IP address that can reach ISE :
router# ping 198.18.133.27 source vlan10 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 198.18.133.27, timeout is 2 seconds: Packet sent with a source address of 10.64.10.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 20/21/24 ms router#
Step 2: Record the router's source IP address (10.64.10.1 in the example above) for use in the RADIUS client configuration for ISE.
Router Configuration
Step 1: Get into your router's configuration mode:
router# configure terminal
Step 2: Copy and paste the global RADIUS client configuration below into your dCloud router after replacing
- {ISE-IP} with the ISE IP address above
- {Router-Interface-Name} with the router's management interface above
- {dCloud-PreSharedKey} with the default dCloud pre-shared key / password (typically C1sco12345)
aaa authentication dot1x default group ise-group
aaa authorization network default group ise-group
aaa accounting update newinfo
aaa accounting dot1x default start-stop group ise-group
!
!
radius server ISE-1
address ipv4 {ISE-IP} auth-port 1812 acct-port 1813
key {dCloud-PreSharedKey}
!
aaa group server radius ise-group
server name ISE-1
!
!
aaa server radius dynamic-author
client {ISE-IP}
server-key {dCloud-PreSharedKey}
auth-type any
!
device-sensor accounting
!
dot1x system-auth-control
!
ip radius source-interface {Router-Interface-Name}
!
ip device tracking
ip dhcp snooping
!
radius-server vsa send authentication
radius-server vsa send accounting
radius-server attribute 6 on-for-login-auth
radius-server attribute 8 include-in-access-req
radius-server attribute 25 access-request include
radius-server attribute 31 mac format ietf upper-case
radius-server attribute 31 send nas-port-detail
radius-server dead-criteria time 10 tries 3
!
! --- Required for discovery by ISE Visibility Setup Wizard
snmp-server community {dCloud-PreSharedKey} ro
!
Note: For discussion about each of these configurations, please see the How To: Universal IOS Switch Config for ISE
Step 3: Copy and paste the following 802.1X+MAB configuration below into below into your dCloud router's switchport(s) that you want to enable edge authentication on :
interface FastEthernet0 description Secure Access Edge with 802.1X & MAB switchport mode access switchport access vlan 10 switchport trunk native vlan 10 switchport voice vlan 100 no ip address authentication control-direction in authentication event fail action next-method authentication event server dead action reinitialize vlan 10 authentication event server dead action authorize voice authentication event server alive action reinitialize authentication host-mode multi-auth authentication open authentication order dot1x mab authentication priority dot1x mab authentication port-control auto authentication timer reauthenticate server mab dot1x pae authenticator dot1x timeout tx-period 10 spanning-tree portfast
Note: The 819HWD is only capable of VLAN-based enforcement on the FastEthernet switchports - it cannot handle downloadable ACLs from ISE.
Add Network Device to ISE
Step 1: In ISE, navigate to Administration > Network Resources > Network Devices
Step 2: Add the dCloud router with the following settings:
| Attribute | Value |
|---|---|
| Network Device | |
| Name | dCloud-Router |
| IP Address | 10.64.10.1/32 |
| Device Profile | Cisco |
| ✓ RADIUS Authentication Settings | |
| Shared Secret | C1sco12345 |
| ✓ SNMP Settings | |
| SNMP Version | 2c |
| SNMP RO Community | C1sco12345 |
Step 3: Submit the changes.
Create a User Identity
Create a user identity in ISE if you haven't already. This will be used for the test authentication.
Step 1: In ISE, navigate to Administration > Identity Management > Users
Step 2: Click on +Add to add a new network user
Step 3: Fill in the form with the following settings:
| Attribute | Value |
|---|---|
| Network Access User |
|
| Name | test |
| Status | Enabled |
| Passwords | |
| Password Type | Internal Users |
| Login Password | C1sco12345 |
| User Groups | |
| User Groups | Employee |
Step 4: Click on Submit
Validate the User (Optional)
You can use the router CLI to perform a RADIUS test authorization from the router to ensure you have RADIUS connectivity to ISE.
Step 1: Open the dCloud Router console
Step 2: Run the test aaa command to ISE which has the format
test aaa group {group-name | radius} {username} {password} new-code
Example output using the user identity above:
router# test aaa group ise-group test C1sco12345 new-code User successfully authenticated USER ATTRIBUTES username 0 "test"
Validate 802.1X with a Wired Client
Step 1: Connect an endpoint (Windows, MacOS, Linux) to the dCloud router's switchport interface configured for 802.1X.
Step 2: On the router console You should immediately events for
Link-Up:
000376: *Sep 14 03:09:10.383: %LINK-3-UPDOWN: Interface FastEthernet0, changed state to up
Starting 802.1X:
000377: *Sep 14 03:09:10.763: %AUTHMGR-5-START: Starting 'dot1x' for client (20c9.d029.a3fb) on Interface Fa0 AuditSessionID 0A66930B0000000300845614
Step 3: On your endpoint, if 802.1X is enabled for the wired interface you should be prompted to enter your user identity credentials (test:C1sco12345). Enter the credentials and submit them

Step 4: Your identity should immediately be authenticated and your endpoint authorized onto the network.
Step 5: On the router console, view the authentication and authorization events:
Authentication:
000379: *Sep 14 03:09:11.443: %DOT1X-5-SUCCESS: Authentication successful for client (20c9.d029.a3fb) on Interface Fa0 AuditSessionID 0A66930B0000000300845614
Authentication Result:
000380: *Sep 14 03:09:11.443: %AUTHMGR-7-RESULT: Authentication result 'success' from 'dot1x' for client (20c9.d029.a3fb) on Interface Fa0 AuditSessionID 0A66930B0000000300845614
Authorization Success:
000381: *Sep 14 03:09:11.447: %AUTHMGR-5-SUCCESS: Authorization succeeded for client (20c9.d029.a3fb) on Interface Fa0 AuditSessionID 0A66930B0000000300845614
Step 6: View the authentication session information for the router interface
router# show authentication sessions interface FastEthernet 0
Interface: FastEthernet0
MAC Address: 20c9.d029.a3fb
IP Address: Unknown
User-Name: test
Status: Authz Success
Domain: DATA
Oper host mode: multi-auth
Oper control dir: both
Authorized By: Authentication Server
Vlan Group: N/A
AAA Policies:
Session timeout: N/A
Idle timeout: N/A
Common Session ID: 0A66930B0000000300845614
Acct Session ID: 0x00000006
Handle: 0x21000004
Runnable methods list:
Method State
dot1x Authc Success
mab Not run
router#
Step 7: In ISE, navigate to Operations > RADIUS > Livelogs to view the authentication for user test in ISE

![]() indicates that there was a successful authentication for the user test@20:C9:D0:29:A3:FB
indicates that there was a successful authentication for the user test@20:C9:D0:29:A3:FB
![]() indicates that there is an active RADIUS session for this device
indicates that there is an active RADIUS session for this device
Validate MAB Failover with a Wired Client
If for some reason you miss the 802.1X authentication challenges and it times out, your endpoint should still be successfully authenticated with MAC Authentication Bypass (MAB).
Starting 802.1X:
000392: *Sep 14 03:39:43.831: %AUTHMGR-5-START: Starting 'dot1x' for client (20c9.d029.a3fb) on Interface Fa0 AuditSessionID 0A66930B0000000500A05470 000393: *Sep 14 03:39:44.967: %LINK-3-UPDOWN: Interface FastEthernet0, changed state to up
After approximately 30 seconds (3 x 10 second timeouts) you will see 802.1X fail due to a lack of response from the endpoint:
000395: *Sep 14 03:40:14.739: %DOT1X-5-FAIL : Authentication failed for client (20c9.d029.a3fb) on Interface Fa0 AuditSessionID 0A66930B0000000500A05470 000396: *Sep 14 03:40:14.739: %AUTHMGR-7-RESULT: Authentication result 'no-response' from 'dot1x' for client (20c9.d029.a3fb) on Interface Fa0 AuditSessionID 0A66930B0000000500A05470
The switchport will then begin to failover from 802.1X authentication into MAB authentication:
000397: *Sep 14 03:40:14.739: %AUTHMGR-7-FAILOVER: Failing over from 'dot1x' for client (20c9.d029.a3fb) on Interface Fa0 AuditSessionID 0A66930B0000000500A05470 000398: *Sep 14 03:40:14.739: %AUTHMGR-5-START: Starting 'mab' for client (20c9.d029.a3fb) on Interface Fa0 AuditSessionID 0A66930B0000000500A05470
And this should be successful:
000399: *Sep 14 03:40:14.811: %MAB-5-SUCCESS: Authentication successful for client (20c9.d029.a3fb) on Interface Fa0 AuditSessionID 0A66930B0000000500A05470 000400: *Sep 14 03:40:14.811: %AUTHMGR-7-RESULT: Authentication result 'success' from 'mab' for client (20c9.d029.a3fb) on Interface Fa0 AuditSessionID 0A66930B0000000500A05470 000401: *Sep 14 03:40:14.815: %AUTHMGR-5-SUCCESS: Authorization succeeded for client (20c9.d029.a3fb) on Interface Fa0 AuditSessionID 0A66930B0000000500A05470
You can see how the authentication session information shows a successful MAB authentication for the MAC address (not the username) into the DATA VLAN:
router# show authentication sessions interface FastEthernet 0
Interface: FastEthernet0
MAC Address: 20c9.d029.a3fb
IP Address: Unknown
User-Name: 20-C9-D0-29-A3-FB
Status: Authz Success
Domain: DATA
Oper host mode: multi-auth
Oper control dir: both
Authorized By: Authentication Server
Vlan Group: N/A
AAA Policies:
Session timeout: N/A
Idle timeout: N/A
Common Session ID: 0A66930B0000000500A05470
Acct Session ID: 0x00000008
Handle: 0xB8000006
Runnable methods list:
Method State
dot1x Failed over
mab Authc Success
router#
Step 7: In ISE, navigate to Operations > RADIUS > Livelogs to view the MAB authentication for the endpoint MAC address:

Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: