- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Identity Services Engine and Splunk Apps Configuration Guide
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on
10-31-2018
10:55 AM
- edited on
04-27-2021
10:46 AM
by
Jason Kunst
![]()
- Introduction
- Prerequisites
- Configure
- Configure Splunk Add-Ons
- Configure ISE to forward Syslog to Splunk
- Verify
Introduction
This document is intended for Cisco Engineers, Partners and Customers deploying Splunk-for-ISE Add-on & Cisco Identity Service Engine (ISE) 2.4+ (use current recommended release). The reader should be familiar with Splunk and ISE. It is assumed that Splunk Enterprise 7.x+ (8.x preferred) has been installed.
The purpose of this guide is to showcase the 2 applications available in Splunkbase to use with Cisco ISE Syslog. There was an application version before this that used pxGrid 1.0 and EPS (endpoint protection services) to quarantine devices. This functionality has been deprecated by Splunk.
For more information, troubleshooting and upgrade, see the associated product documentation for the app
Note: Always check with ISE and Splunk team on current recommended releases
There are two applications that are used in this walk-through:
Splunk Add-on for Cisco Identity Services - https://splunkbase.splunk.com/app/1915/
- It is supported by splunk but not Cisco.
- This is the application used to collect and process information from ISE syslog so that it can be used in its queries/consoles, for more detailed information see the information listed under the application link for the configuration, etc.
Splunk for Cisco Identity Services (ISE) - https://splunkbase.splunk.com/app/1589/
- It is a community based application and not supported by Cisco or Splunk.
- This is used for showcasing of the data received from ISE.
Prerequisites
Requirements
- Cisco Identity Services Engine (ISE) 2.4 or higher (please validate latest recommended release)
- Splunk 7.x+ (8.x preferred) with Splunk for Cisco Identity Services Engine and Splunk Add-On for Cisco Identity Services Engine
- Switch or WLC configured for AAA Authentication
- Test Device (windows/mac)
Components Used
Note: these are the components used when making this document. You should be using the latest recommended versions and patches recommended by the vendor and ISE team.
- Cisco Identity Services Engine (ISE) 2.7
- Splunk Enterprise 8
- Splunk apps
- Splunk for Cisco Identity Services Engine
- Splunk Add-On for Cisco Identity Service Engine
Configure
Configure Splunk Add-Ons
This guide assumes that Splunk is installed and has basic networking configured to communicate with ISE.
- Download Splunk for Cisco Identity Services (ISE)
- Download Splunk Add-on for Cisco Identity Services
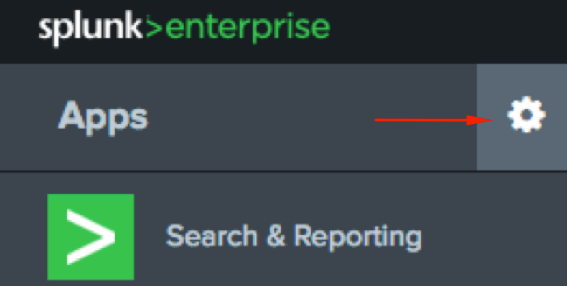
Log in to Splunk and click the cog-wheel to the right of Apps on the left of the screen
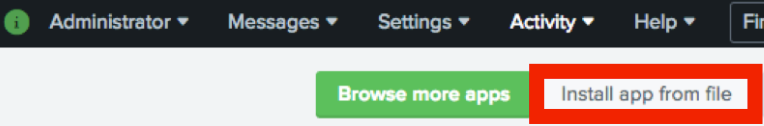
Click Install app from file
Browse and choose the Splunk for Cisco Identity Services (ISE) file downloaded in step 2, then click Upload
Delay the restart until after the second application is installed to prevent the need to restart Splunk twice.
Repeat the process for the Spunk Add-on for Cisco Identity Services file needed to enable pxGrid integration with Splunk
Restart when prompted
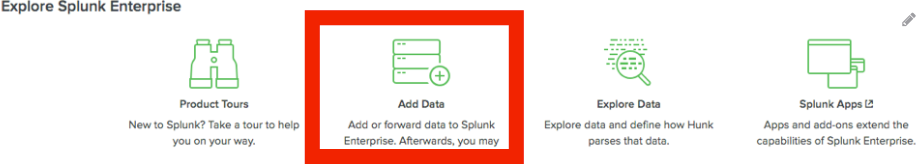
After the restart has completed, log in to the Spunk Enterprise GUI and click on Add Data
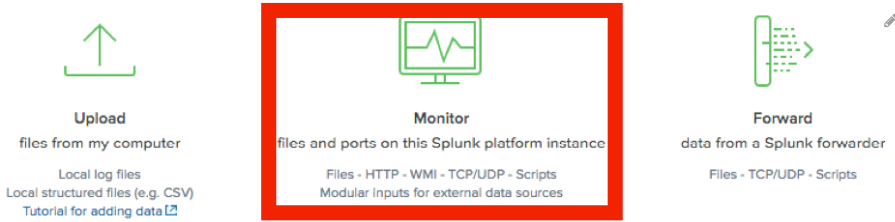
Click Monitor
Click TCP / UDP on the left
Set the UDP Port (514)
Set the ISE IP address (optional)
Click Next
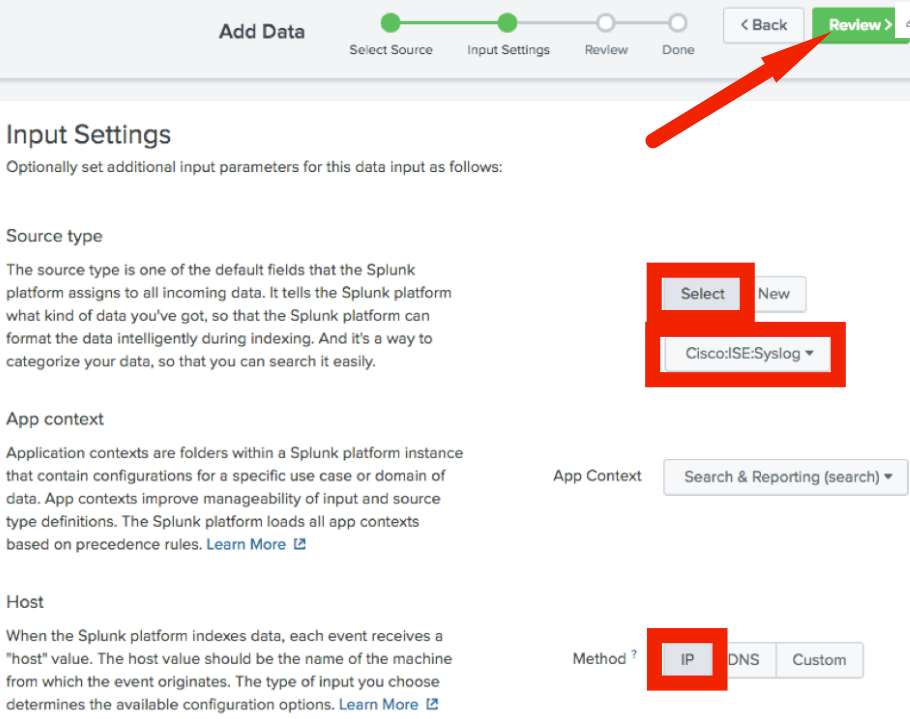
Set the Source type to: “Select”
Type in/select “Cisco:ISE:Syslog”
Set the Host to: “IP”
Click Review
If the settings look correct on the Review page, click Submit
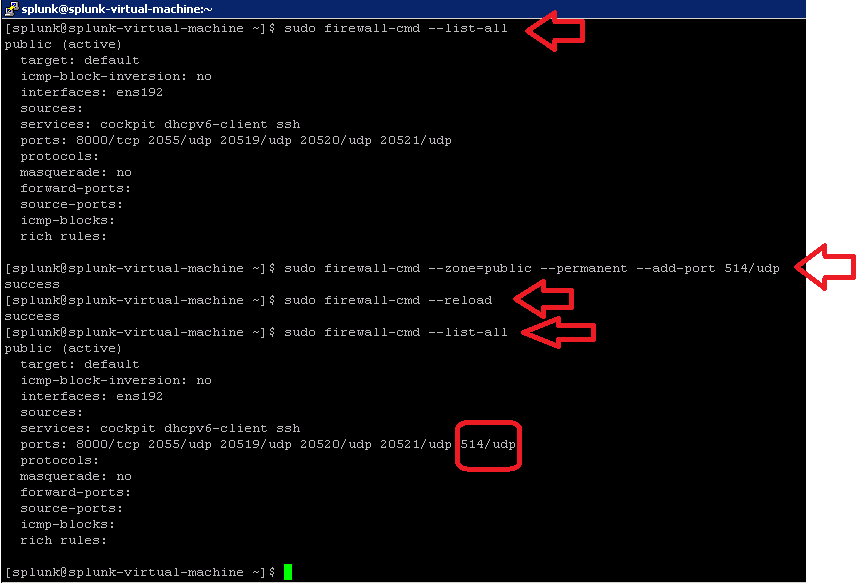
Make sure you update your Linux firewall to allows ISE to send syslog to splunk by taking into account the following detail in Spunk server:
Open the port 514 (CentOS
- sudo firewall-cmd --zone=public --permanent --add-port 514/udp
- sudo firewall-cmd –-reload
- sudo firewall-cmd --list-all
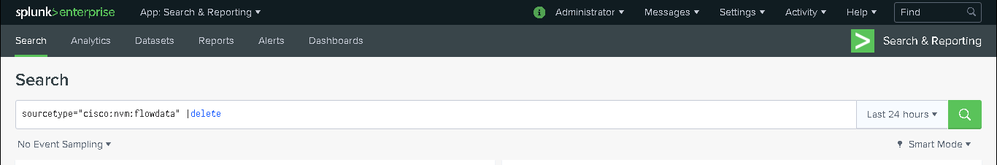
In order to delete any log received from ISE:
- sourcetype="cisco:nvm:flowdata" |delete
Configure ISE to forward Syslog to Splunk
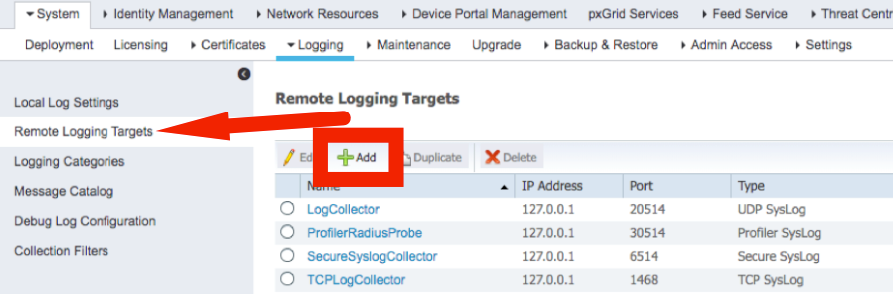
In ISE, navigate to Administration > Logging
Select Remote Logging Targets on the left then click Add
Add the Splunk instance Name, IP address, and the Syslog port configured on Splunk (514)
Name: Splunk
Target type: UDP SysLog
Status: Enabled
Host / IP Address: Splunk IP Address
Port: 514
Facility Code: LOCAL6
Maximum Length: 8192
Confirm the warning about the unsecure connection
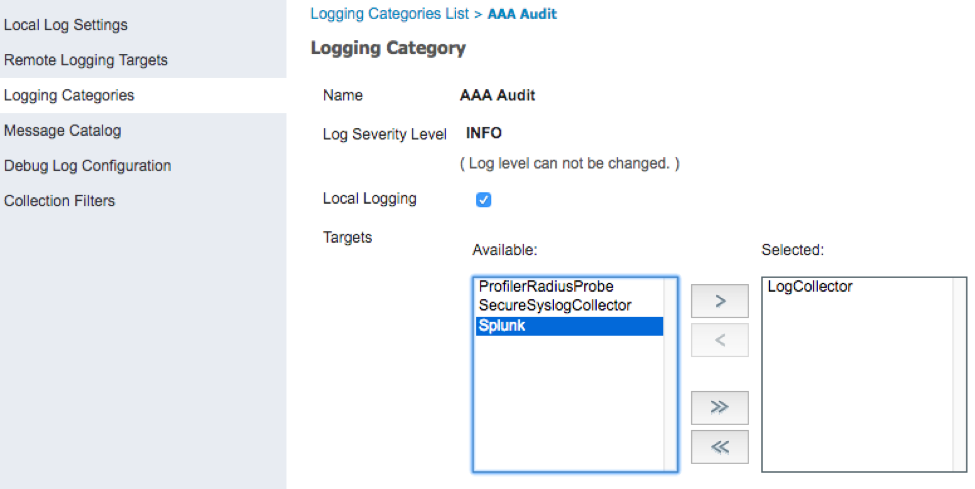
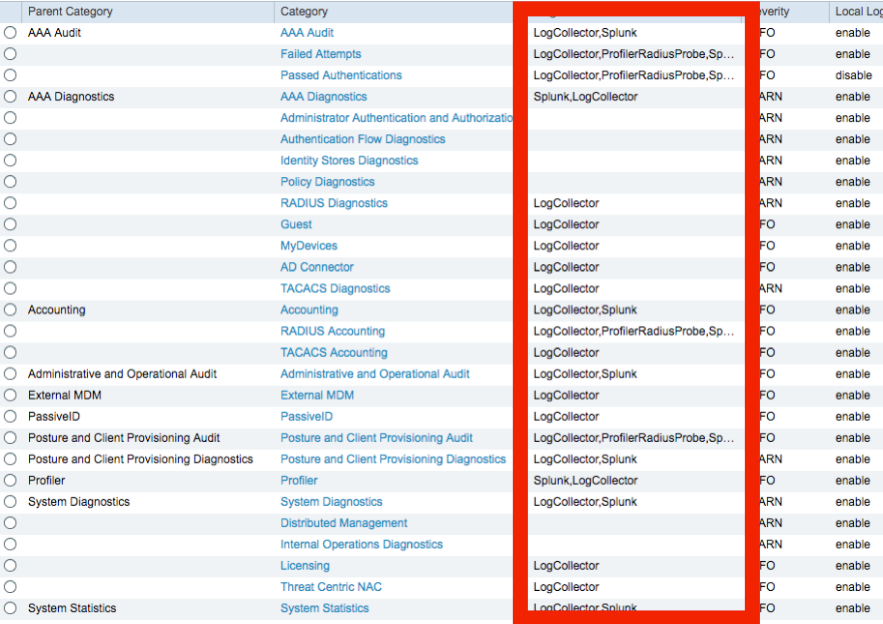
Select Logging Categories from the list on the left
Edit each of the logging categories below to include the Splunk target
AAA Audit
Failed Attempts
Passed Authentications
AAA Diagnostics
Accounting
RADIUS Accounting
Administrative and Operational Audit
Posture and Client Provisioning Audit
Posture and Client Provisioning Diagnostics
External MDM
Profiler
System Diagnostics
System Statistics
To add the Spunk logging target, open each of the categories in this list, select Splunk, then click > and Save
Once completed, the Targets column should display Splunk for any desired messages to be sent to Splunk from ISE
Verify
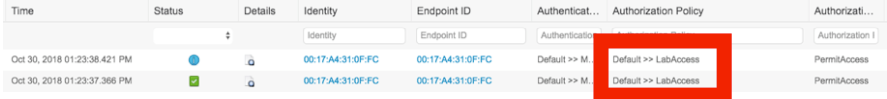
Authenticate a test device against ISE
In ISE, navigate to Operations > RADIUS > Live Logs
The test device should match on the LabAccess policy created in the ISE Policy Set.
In Splunk, select the Cisco ISE application on the left
On the ISE Summary View graph, click on the last Passed-Authentication
This will open the search page. Expand the view of the Passed-Authentication and then expand Event Actions
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for the document.
Question: From "Configure Splunk for the pxGrid connection" and onwards I'm stuck because I've Splunk running on Windows 10 machine, how do I import the certificates on Windows 10? I don't get the Java interaction as well.
Please help.
Thanks
Ain
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
The Splunk-for-ISE Add-on with pxGrid currently works on only Linux or MAC platforms. It does not work on Windows platforms due to limited API support for the encryption of stored pxGrid credentials.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you. That tip helped.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: