- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Java Update enforces CRL checks by default preventing NSP and Guest Flows
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
08-05-2013 12:49 PM - edited 02-21-2020 10:00 PM
Introduction
The latest java update breaks supplicant provisioning and some guest flows that utilize ACLs and redirection. The error is in the CiscoSPWDownloadFacilitator and reads "Failed to validate certificate. The application will not be executed."
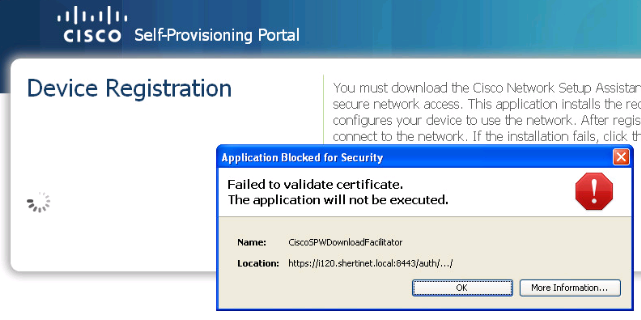
If you click 'More Information' you get an output that complains about CRL.
java.security.cert.CertificateException: java.security.cert.CertPathValidatorException: java.io.IOException: DerInputStream.getLength(): lengthTag=127, too big. at com.sun.deploy.security.RevocationChecker.checkOCSP(Unknown Source) at com.sun.deploy.security.RevocationChecker.check(Unknown Source) at com.sun.deploy.security.TrustDecider.checkRevocationStatus(Unknown Source) at com.sun.deploy.security.TrustDecider.getValidationState(Unknown Source) at com.sun.deploy.security.TrustDecider.validateChain(Unknown Source) at com.sun.deploy.security.TrustDecider.isAllPermissionGranted(Unknown Source) at sun.plugin2.applet.Plugin2ClassLoader.isTrustedByTrustDecider(Unknown Source) at sun.plugin2.applet.Plugin2ClassLoader.getTrustedCodeSources(Unknown Source) at com.sun.deploy.security.CPCallbackHandler$ParentCallback.strategy(Unknown Source) at com.sun.deploy.security.CPCallbackHandler$ParentCallback.openClassPathElement(Unknown Source) at com.sun.deploy.security.DeployURLClassPath$JarLoader.getJarFile(Unknown Source) at com.sun.deploy.security.DeployURLClassPath$JarLoader.access$1000(Unknown Source) at com.sun.deploy.security.DeployURLClassPath$JarLoader$1.run(Unknown Source) at java.security.AccessController.doPrivileged(Native Method) at com.sun.deploy.security.DeployURLClassPath$JarLoader.ensureOpen(Unknown Source) at com.sun.deploy.security.DeployURLClassPath$JarLoader.<init>(Unknown Source) at com.sun.deploy.security.DeployURLClassPath$3.run(Unknown Source) at java.security.AccessController.doPrivileged(Native Method) at com.sun.deploy.security.DeployURLClassPath.getLoader(Unknown Source) at com.sun.deploy.security.DeployURLClassPath.getLoader(Unknown Source) at com.sun.deploy.security.DeployURLClassPath.getResource(Unknown Source) at sun.plugin2.applet.Plugin2ClassLoader$2.run(Unknown Source) at java.security.AccessController.doPrivileged(Native Method) at sun.plugin2.applet.Plugin2ClassLoader.findClassHelper(Unknown Source) at sun.plugin2.applet.Applet2ClassLoader.findClass(Unknown Source) at sun.plugin2.applet.Plugin2ClassLoader.loadClass0(Unknown Source) at sun.plugin2.applet.Plugin2ClassLoader.loadClass(Unknown Source) at sun.plugin2.applet.Plugin2ClassLoader.loadClass0(Unknown Source) at sun.plugin2.applet.Plugin2ClassLoader.loadClass(Unknown Source) at sun.plugin2.applet.Plugin2ClassLoader.loadClass(Unknown Source) at java.lang.ClassLoader.loadClass(Unknown Source) at sun.plugin2.applet.Plugin2ClassLoader.loadCode(Unknown Source) at sun.plugin2.applet.Plugin2Manager.initAppletAdapter(Unknown Source) at sun.plugin2.applet.Plugin2Manager$AppletExecutionRunnable.run(Unknown Source) at java.lang.Thread.run(Unknown Source) Suppressed: com.sun.deploy.security.RevocationChecker$StatusUnknownException at com.sun.deploy.security.RevocationChecker.checkCRLs(Unknown Source) ... 34 more Caused by: java.security.cert.CertPathValidatorException: java.io.IOException: DerInputStream.getLength(): lengthTag=127, too big. at sun.security.provider.certpath.OCSP.check(Unknown Source) at sun.security.provider.certpath.OCSP.check(Unknown Source) at sun.security.provider.certpath.OCSP.check(Unknown Source) ... 35 more Caused by: java.io.IOException: DerInputStream.getLength(): lengthTag=127, too big. at sun.security.util.DerInputStream.getLength(Unknown Source) at sun.security.util.DerValue.init(Unknown Source) at sun.security.util.DerValue.<init>(Unknown Source) at sun.security.provider.certpath.OCSPResponse.<init>(Unknown Source) ... 38 more
Problem
In the latest (August 5th) version of Java (version 7 update 25), Oracle has introduced a new default setting that forces the client to validate the certificate associated with any applet against any Certificate Revocation List (CRL) or Online Certificate Status Protocol (OCSP).
The signing certificate Cisco has associated with these applets have a listed CRL and OCSP with Thawte. Because of this new change, when the java client attempts to reach out to Thawte, they are blocked by either a port ACL and/or a redirect ACL.
The problem is being tracked under bug ID CSCui46739  .
.
Solution
Option 1. - Switch or Wireless Controller side fix. Re-write any redirect or port-based ACLs to allow traffic to Thawte and Verisign. Unforunately, one limitation with this option is that we cannot create ACLs based off domain names. Resolve the CRL list manually, and put it in our redirect ACL.
Note: Firewall rules may need to be updated if the client needs to communicate through a firewall.
[user@user-linux logs]$ nslookup
> crl.thawte.com
Server: 64.102.6.247
Address: 64.102.6.247#53
Non-authoritative answer:
crl.thawte.com canonical name = crl.ws.symantec.com.edgekey.net.
crl.ws.symantec.com.edgekey.net canonical name = e6845.ce.akamaiedge.net.
Name: e6845.ce.akamaiedge.net
Address: 23.5.245.163
> ocsp.thawte.com
Server: 64.102.6.247
Address: 64.102.6.247#53
Non-authoritative answer:
ocsp.thawte.com canonical name = ocsp.verisign.net.
Name: ocsp.verisign.net
Address: 199.7.48.72
If these DNS names change and clients resolve something else, re-write the redirect URL with the updated addresses.
Example redirect ACL
5 remark ISE IP address
10 deny ip any host 14.36.147.120 (467 matches)
15 remark crl.thawte.com
20 deny ip any host 23.5.245.163 (22 matches)
25 remark ocsp.thawte.com
30 deny ip any host 199.7.52.72
40 deny udp any any eq domain (10 matches)
50 permit tcp any any eq www (92 matches)
60 permit tcp any any eq 443 (58 matches)
Option 2. - Client side fix. Inside the Advanced section of the Java Control Panel, set 'Perform certificate revocation checks on' to 'Do not check (not recommended)'.
OSX: System Preferences > Java
Advanced
Perform certificate revocation using: Change to 'Do not check (not recommended)'
Windows: Control Panel > Java
Advanced
Perform certificate revocation using: Change to 'Do not check (not recommended)'
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Sam,
This is a great writeup.
thanks,
Tarik Admani
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: