- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Monitor only access to ASDM (ASA) for user authenticated via LDAP
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
06-03-2013 05:23 AM - edited 02-21-2020 10:00 PM
Introduction
We can configure ASA to provide monitor only or read only access, to it's ASDM for a user who authenticates using LDAP.
Configuration
1. We need to configure a AAA server on the ASA, in the following configuration I have configured and LDAP as AAA server:
aaa-server LDAP protocol ldap
aaa-server LDAP (inside) host 192.168.26.55
ldap-base-dn DC=MCS55, DC=COM
ldap-scope subtree
ldap-naming-attribute sAMAccountName
ldap-login-password *****
ldap-login-dn CN=ashish AV. varghese,CN=Users,DC=MCS55,DC=com
server-type microsoft
ldap-attribute-map LDAPreadonly
ciscoasa#2. Configure an LDAP attribute map, in the following configuration I have granted privilege 6 to the group and privilege 5 to the user:
ciscoasa# sh run ldap attribute-map LDAPreadonly
map-name memberOf IETF-Radius-Service-Type
map-value memberOf "CN=Account Operators,CN=Builtin,DC=MCS55,DC=com" 6
map-name sAMAccountName Privilege-Level
map-value sAMAccountName "ashishv" 5
ciscoasa#3. Configure AAA on ASA
ciscoasa# sh run aaa
aaa authentication telnet console LOCAL
aaa authentication ssh console LOCAL
aaa authentication http console LDAP LOCAL
aaa authorization command LOCAL
aaa authorization exec authentication-server
ciscoasa#ASA is now ready to grant read only access to the user called "ashishv"
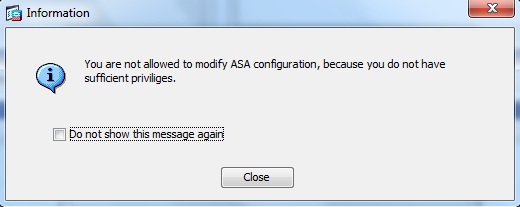
4. On authenticating to ASDM we will get this message, which indicates we have monitor only access.
5. View of the ASDM once you have access:

Debugs
6. This is how "debug ldap 255” will look like for a successful user authentication:
ciscoasa#
[45] Session Start
[45] New request Session, context 0xda1861b4, reqType = Authentication
[45] Fiber started
[45] Creating LDAP context with uri=ldap://192.168.26.55:389
[45] Connect to LDAP server: ldap://192.168.26.55:389, status = Successful
[45] supportedLDAPVersion: value = 3
[45] supportedLDAPVersion: value = 2
[45] Binding as ashish AV. varghese
[45] Performing Simple authentication for ashish AV. varghese to 192.168.26.55
[45] LDAP Search:
Base DN = [DC=MCS55, DC=COM]
Filter = [sAMAccountName=ashishv]
Scope = [SUBTREE]
[45] User DN = [CN=ashish AV. varghese,CN=Users,DC=MCS55,DC=com]
[45] Talking to Active Directory server 192.168.26.55
[45] Reading password policy for ashishv, dn:CN=ashish AV. varghese,CN=Users,DC=MCS55,DC=com
[45] Read bad password count 0
[45] Binding as ashishv
[45] Performing Simple authentication for ashishv to 192.168.26.55
[45] Processing LDAP response for user ashishv
[45] Message (ashishv):
[45] Authentication successful for ashishv to 192.168.26.55
[45] Retrieved User Attributes:
[45] objectClass: value = top
[45] objectClass: value = person
[45] objectClass: value = organizationalPerson
[45] objectClass: value = user
[45] cn: value = ashish AV. varghese
[45] sn: value = varghese
[45] givenName: value = ashish
[45] initials: value = AV
[45] distinguishedName: value = CN=ashish AV. varghese,CN=Users,DC=MCS55,DC=com
[45] instanceType: value = 4
[45] whenCreated: value = 20121224152326.0Z
[45] whenChanged: value = 20130119142646.0Z
[45] displayName: value = ashishvarghese
[45] uSNCreated: value = 186542
[45] memberOf: value = CN=Account Operators,CN=Builtin,DC=MCS55,DC=com
[45] mapped to IETF-Radius-Service-Type: value = 6
[45] uSNChanged: value = 190878
[45] name: value = ashish AV. varghese
[45] objectGUID: value = ...+...M.`/.....
[45] userAccountControl: value = 66048
[45] badPwdCount: value = 0
[45] codePage: value = 0
[45] countryCode: value = 0
[45] badPasswordTime: value = 130030933379843750
[45] lastLogoff: value = 0
[45] lastLogon: value = 130030933572968750
[45] pwdLastSet: value = 130030792063437500
[45] primaryGroupID: value = 512
[45] objectSid: value = ............4E'y...&R.Egt...
[45] adminCount: value = 1
[45] accountExpires: value = 9223372036854775807
[45] logonCount: value = 0
[45] sAMAccountName: value = ashishv
[45] mapped to Privilege-Level: value = 5
[45] sAMAccountType: value = 805306368
[45] userPrincipalName: value = ashishv@MCS55.com
[45] objectCategory: value = CN=Person,CN=Schema,CN=Configuration,DC=MCS55,DC=com
[45] lastLogonTimestamp: value = 130027602762031250
[45] Fiber exit Tx=561 bytes Rx=2534 bytes, status=1
[45] Session EndPlease feel free to comment in case of any query.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for this, it really helped me out, but I did find that your solution didn't scale well, and also did not allow any user not explicitly stated into the firewall.
I have written up how I solved this, and hope that others might find it useful:
http://www.802101.com/2013/09/separating-monitor-only-and-admin.html
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Stuart,
thanks for sharing this.
This is a very creative way of making this scalable.
Regards,
Ashish
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Great guide!
For read-only access to a Group of Users, I tried the commands below:
map-name memberOf Privilege-Level
map-value memberOf "CN=Account Operators,CN=Builtin,DC=MCS55,DC=com" 5
instead of
map-name memberOf IETF-Radius-Service-Type
map-value memberOf "CN=Account Operators,CN=Builtin,DC=MCS55,DC=com" 6
map-name sAMAccountName Privilege-Level
map-value sAMAccountName "ashishv" 5
which worked really well for me
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

