- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Orbital Query Corner - Hunting WMI based backdoor mechanisms
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 07-30-2020 10:26 AM
The Advisory
On July 16 2020, the U.K. National Cyber Security Centre and Canada’s Communication Security Establishment, in cooperation with the U.S. National Security Agency and Cybersecurity and Infrastructure Security agency, issued an advisory [0] that the threat actor commonly known as APT29 or “Cozy Bear” was targeting organizations involved in COVID-19 vaccine development.
Here in the Query Corner, this got us wondering what sort of interesting Orbital searches we could derive from an advisory like this. You might be wondering that, too – especially if your organization happens to be involved in vaccine research, or has a business or supply chain relationship with another such organization.
As is often the case, the advisory includes an extensive appendix of Indicators of Compromise (IoCs) associated with the threats it describes, so an obvious first step would be to look for those IoCs, including long lists of file hashes and IP addresses, in our own environment. But, of course, we don’t need Orbital queries for that. For one thing, file hashes and IP addresses can easily be handles with AMP blocklists; more to the point, by the time such an advisory is published, the associated hashes and such are usually well known to normal threat intelligence. And in fact, running a quick sample of IoCs through the Talos reputation center [1] shows them already marked as malicious, so there’s no real point in adding them to a customer AMP list after the fact.
Great, so we’re done, right? All covered? Well, certainly the known IoCs are now covered by AMP. But remember that the “A” in APT stands for “Advanced” … and the “P” stands for “Persistent”. So what possible steps might such an advanced and persistent opponent try to take, in order to retain their ill-gotten access to your resources, even after their initial points of entry have been discovered and fixed? Suppose we had been targeted by APT29, and at some point they did get in? Now Talos, and therefore also AMP, has coverage for the indicators in the advisory, but is there something still lurking inside?
The Hunt
A great starting point for understanding more about a specific threat group is the MITRE ATT&CK project. ATT&CK is much more than just a laundry list of tactics and techniques; the true value of the project comes in its application to actual threat actors. [2]
Reviewing the entry for APT29, we see that a number of specific techniques are known to be used by the group, including a few that specifically relate to persistence.
The one that caught our eye as an interesting candidate for an Orbital search involves the use of Microsoft’s Windows Management Instrumentation (WMI). In Microsoft’s own words, WMI is “the infrastructure for management data and operations on Windows-based operating systems.” [3] It is ubiquitous in Windows environments and used to automate system management tasks, especially in response to events. Using WMI event filters, actions can be taken automatically in response to specific system events.
Okay, but what does all that have to do with attack persistence? Well, an attacker with sufficient access to a Windows system can use WMI to set up automated actions with a more nefarious purpose. For example, a WMI event filter could look for a login failure message for a specific user, and then open a reverse shell listening on a specific port when the failure occurs.
In other words, if we change the password on a compromised account in order to lock the attacker out, the very fact of the attacker’s next failed attempt will open up a back door to let the attacker back in! Not only that, but it’s the operating system’s own core functionality which is being turned against us, and in a somewhat obscure corner of Windows arcana that most people probably aren’t watching very closely, if at all.
The Queries
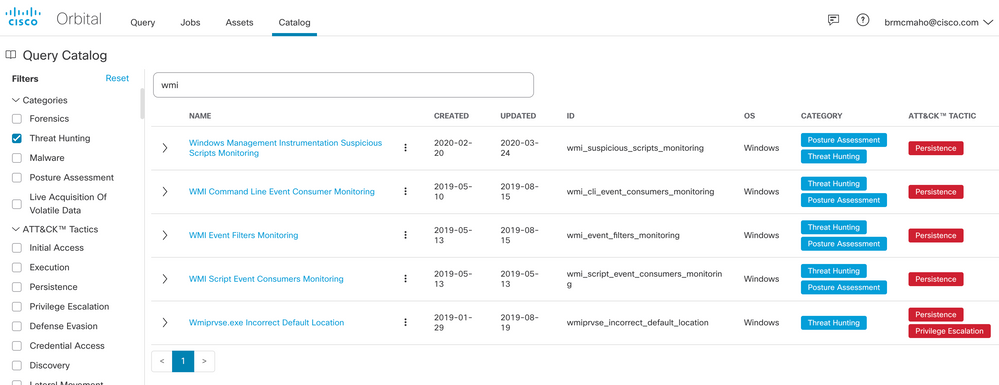
Well, that certainly does sound like an opportunity for an Orbital query! And fortunately, a quick search for WMI-related Threat Hunting queries at the Orbital catalog shows that we do have some relevant items ready to use.
But wait – WMI is a perfectly legitimate management tool. How can we tell the good from the bad here? Part of the answer lies in knowing what “normal” is in your environment.
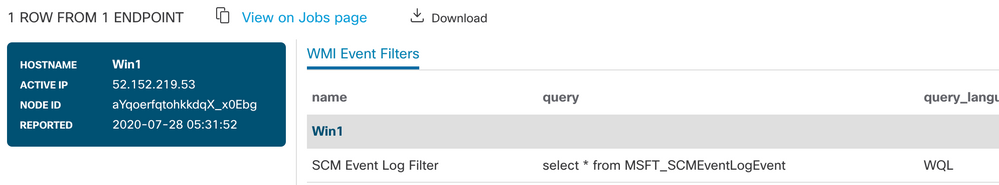
To see that, we will use the wmi_event_filters_monitoring query from the catalog to see what things look like on a freshly installed Windows 10 desktop running in Azure. There’s a single event log filter installed, looking for Service Control Manager (SCM) events.
WMI event filters by themselves aren’t the whole story, of course. Generally, an event filter will be bound to a “consumer” to handle it. At this time, there isn’t an Orbital catalog query to see the bindings, but it turns out that this query is so simple, it hardly matters.
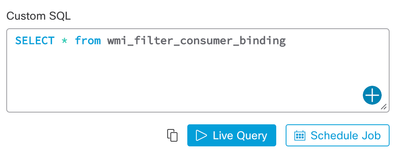
Just drop “SELECT * FROM wmi_filter_consumer_binding” into the Custom SQL window, and we’ll see that the SCM event filter binds to NTEventLogEventConsumer, or to put that in short prose, it logs the event to the Application event log. Not very exciting, right?
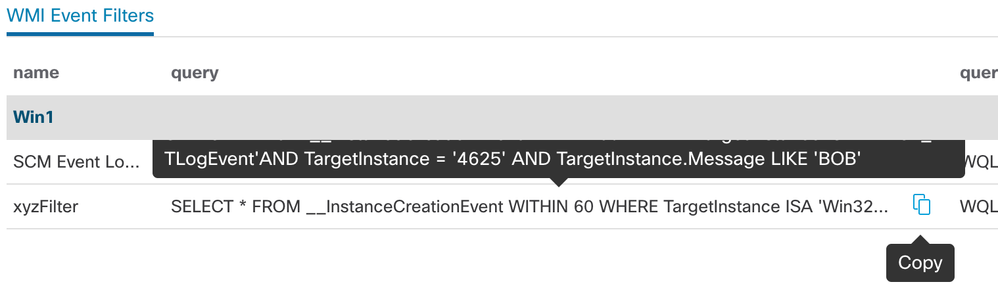
Well, compare that to the same event filter query, but now we run it after adding an event similar to the backdoor scenario described above.
That “xyzFilter” is filtering for log events with an ID of 4625, which is a failed logon attempt, and it’s also searching for “BOB”. But wait – why do we care if user BOB fails to log in? Do we even have a “BOB” on this system? What’s up with that?
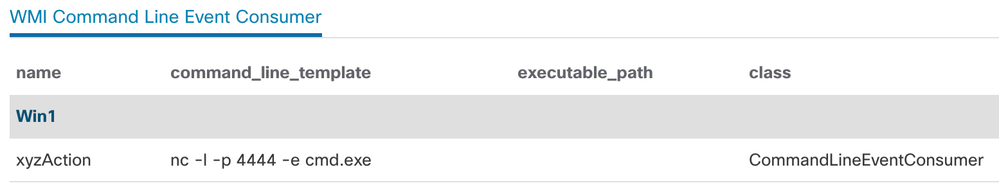
To drill deeper, let’s see what happens if that event does trigger. For that, we’ll pull another query out of the Orbital catalog, namely wmi_cli_event_consumers_monitoring.
Whoa! That sets up a reverse shell using netcat, listening on a funny TCP port. That’s not right! And who left netcat lying around on this system, anyway? Looks like it might be time to take a closer look at that endpoint, and maybe hit the “Start Isolation” button, while we're at it.
The Links
[1] https://talosintelligence.com/reputation
[2] https://attack.mitre.org/groups/G0016/
[3] https://docs.microsoft.com/en-us/windows/win32/wmisdk/wmi-start-page
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: