If you have Duo MFA, Duo Access, or Duo Beyond, you can use Duo LDAP Proxy for admin access to ISE with MFA and be able to use role-based access control (RBAC). Below are instructions that were done on ISE version 3.0.
Duo Configuration
Start with Duo. Install the Duo Authentication Proxy and configure the [ad_client] and [ssl_proxy] sections of the authproxy.cfg as instructed here https://duo.com/docs/ldap. Do yourself a favor and configure at least 2 authentication proxies for HA.
Add the following lines to the [ldap_server_auto] section:
exempt_primary_bind=false
exempt_ou_1=[dn_of_ldap_svc_acct]
Where “dn_of_ldap_svc_acct” is the LDAP Distinguished Name of an account with permission to query AD LDAP. Typically, this can be any domain user account.
Your authproxy.cfg might look something like this:
[ad_client]
host=1.2.3.4
service_account_username=duoservice
service_account_password=password1
search_dn=cn=Users,dc=example,dc=com
[ldap_server_auto]
client=ad_client
ikey=DIXXXXXXXXXXXXXXXXXX
skey=XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
api_host=api-XXXXXXXX.duosecurity.com
failmode=safe
exempt_primary_bind=false
exempt_ou_1= dn=duoservice,ou=users,dc=example,dc=com
ssl_key_path=ldap_server.key
ssl_cert_path=ldap_server.pem
ISE Configuration
Log in with a “local” ISE account (e.g. ‘admin’) to make these changes.
Go to Administration > External Identity Sources > LDAP and add a new entry:
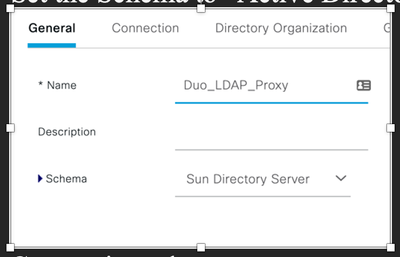
- On the General tab:
- Give it a name and optionally a description. Duo_LDAP_Proxy in this example.
- Set the Schema to “Active Directory”
- On the Connection tab:
- Add the IP address or hostname for your Duo Authentication Proxy/Proxies
- Specify the same port that you specified in the authproxy.cfg of your Duo Authentication Proxy/Proxies. Port 389 is the default for LDAP, 636 for LDAPS, but you can choose any available port, as long as it matches in the authproxy.cfg and in ISE.
- For Access, select Admin DN and enter the same DN that you entered in the [ldap_server_auto] section of the authproxy.cfg of your Duo Authentication Proxy/Proxies.

- On the Directory Organization tab:
- Enter the Subject Search Base
- Enter the Group Search Base
- Back to the Connections tab:
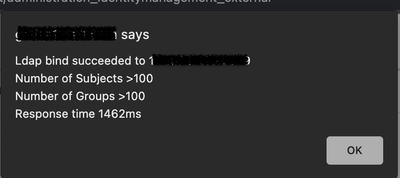
- Click the “Test Bind to Server” button at the bottom of the page. If it works, it will look something like this
- On the Groups tab, add the AD/LDAP groups that you want to assign ISE RBAC to.
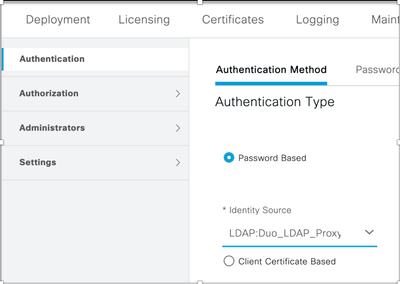
Now go to Administration > System > Admin Access
- On the Authentication Tab:
- Set the Authentication Type to Identity Source and pick the LDAP External Identity Source that you defined above. Duo_LDAP_Proxy in this example.
Go to Administration > Admin Access > Authorization > Permissions and configure Menu Access and Data Access, as well as Administration > Admin Access > Authorization > RBAC Policy to your liking.
Go to Administration > Admin Access > Administrators > Admin Groups.
- Pick a Group to assign an LDAP group to.
- Check “external”
- Select the predefined external groups specified above.
Good luck!