Description:
Cisco IPSec VPN tunnels on Cisco IOS routers secures endpoints by forming a tunnel and encrypting the traffic within. Setting up these site to site VPNs can be cumbersome and often involves setting up complicated matching crypto maps on both end devices. Changing one end’s encryption domain requires a modifying ACLs on both ends of the tunnel.
GRE tunnels on the other hand doesn’t require that as all you need to do is point the routes to the GRE tunnel endpoints on both ends and traffic will magically route through. However the downside is GRE tunnel is not as secure and does not have encryption.
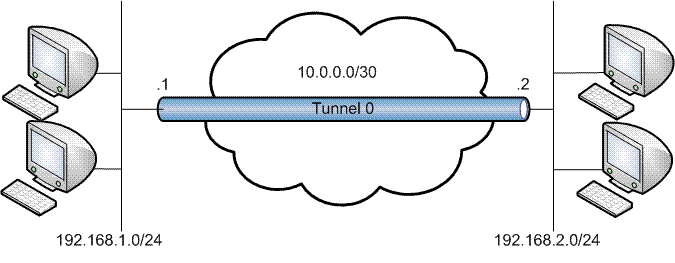
Configuration:
Step1. Create a PHASE 1 isakmp policy on both ends and put in the remote router IP address along with the pre-shared secret key.
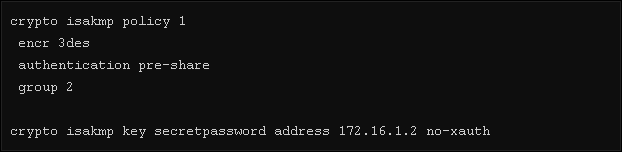
Note: Disable isakmp phase one extended authentication (x-auth) when the same interface uses xauth for another VPN, ie (VPN clients which asks for username and passwords for secondary authentication)
Step 2: Create a PHASE 2 ipsec profile and define the encryption parameters
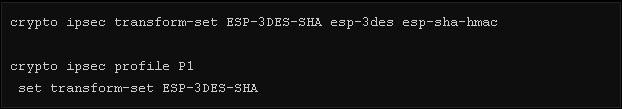
Step3. Create a VTI on both ends and select the ipsec profile defined in the previous step
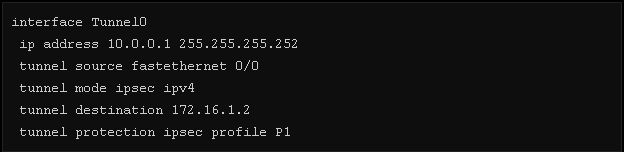
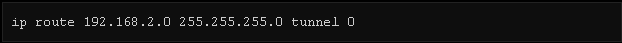
Step4. Simply add a route for the destination you like to reach and a corresponding route other end to the tunnel interface and the router will automatically encrypt them
Also See: