- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- What's New for Cisco Defense Orchestrator (CDO)
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on
03-22-2021
04:40 AM
- edited on
06-27-2024
09:07 AM
by
coferrer
![]()
Cisco Defense Orchestrator (CDO) is a cloud-based, multi-device manager that manages security products like Adaptive Security Appliance (ASA), Firepower Threat Defense next-generation firewall, and Meraki devices, to name a few.
We make improvements to CDO every week and when we have some big news to share, we're going to tell you about it here. Here are the latest features that we have deployed on CDO.
If you're not already a CDO customer, you can get a demo account by contacting cdosales@cisco.com.
June 27, 2024
Upgraded ASA Access Control Policy Interface
CDO now introduces an upgraded ASA access control policy interface featuring enhanced shared access lists, simplified rule management, and enhanced search result navigation. See New Access policy for more information.
June 20, 2024
View the Event Timestamps in Local Time Zone or UTC
Added toggle buttons for UTC and local time zones on the CDO Event Logging page. With this update, the events generated by your device will now be displayed with timestamps in either the local time zone or UTC, depending on your selection. By default, event timestamps are now displayed in your Local time zone.
For more information, see Change the Time Zone for the Event Timestamps.
June 13, 2024
New Threat Defense Dashboard Widgets for Application Monitoring
CDO now features four new dashboard widgets: Top Web Applications, Top Client Applications, Top Blocked Web Applications, and Top Users by Blocked Connections. These new widgets provide you with an at-a-glance view of the most used web and client applications as well as the users with the most blocked connections. Note that the information the threat defense dashboard provides depends on how you license, configure, and deploy the devices in your system. Click Analytics > FTD Dashboard to view the new dashboard widgets.
See About the FTD Dashboard for more information.
Pause Threat Defense to Cloud-delivered Firewall Management Center Migration to Review Imported Shared Policies
You can now pause the threat defense to the cloud-delivered Firewall Management Center migration process to review the imported shared policy configuration. At this stage, neither the evaluation period is initiated, nor the threat defense's manager is changed, which provides you time to review the configurations. After reviewing the configuration, you can resume the migration process to import the device-specific configuration to the cloud-delivered Firewall Management Center during the scheduled migration period. Click Tools & Services > Migrate FTD to cdFMC.
See Threat Defense to Cloud-delivered Firewall Management Center Migration for more information.
June 06, 2024
Firewall Management with Cisco AI Assistant
CDO administrators now have a more efficient way to manage Secure Firewall Threat Defense policies and access documentation with the integration of the Cisco AI Assistant in Cisco Defense Orchestrator (CDO) and cloud-delivered Firewall Management Center. The Cisco AI Assistant has several key features:
-
Pre-Enabled Assistant: The AI Assistant is enabled by default on every CDO tenant. If needed, you can disable it on the General Settings page of your tenant.
-
Easy Access: CDO Super Admins and Admin can access the AI Assistant directly from the top menu bar of their tenant’s dashboard after logging in. -
User Orientation: Upon opening the AI Assistant widget for the first time, users are greeted with a carousel window that introduces the AI Assistant, explains data privacy protections, and provides tips on effective usage.
-
Policy Rule Assistance: The AI Assistant simplifies the process of creating policy rules on Secure Firewall Threat Defense devices. Administrators can quickly create access control rules using simple prompts.
-
Product Knowledge Resource: The AI Assistant has ingested CDO's and the cloud-delivered Firewall Management's documentation. If you need help, you can ask it a question.
-
User-Friendly Interface:
-
Simple Text Input Box: Located at the bottom of the window for easy engagement with the Assistant.
-
Thread History: The questions, or series of questions, you ask the AI Assistant are called threads. The AI Assistant retains your thread history so you can refer to the questions you’ve asked.
-
Feedback: Provide feedback on the Assistant’s responses with thumbs up or thumbs down.
-
See the Cisco AI Assistant User Guide for more information.
May 30, 2024
CDO in India!
CDO is now available in India at https://in.cdo.cisco.com. You can create yourself a tenant in India by going to https://www.getcdo.com.
Updates to Cloud-Delivered Firewall Management Center
Cisco Defense Orchestrator released an update to the cloud-delivered Firewall Management Center. Read the Release Notes for Cloud-delivered Firewall Management Center to learn about the many new features included in the update.
May 23, 2024
CDO in Australia!
CDO is now available in Australia at https://aus.cdo.cisco.com. You can create yourself a tenant in Australia by going to https://www.getcdo.com.
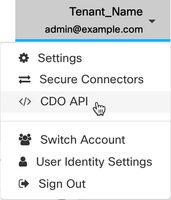
CDO API
CDO now offers a RESTful API that allows you to programmatically interact with CDO. The API provides access to a wide range of CDO features, including device management and deployment, object management, searches, changelog monitoring, and user management. Learn more by reading the Cisco Defense Orchestrator API Documentation. You can also reach the CDO API documentation by navigating from the user menu located in the top right corner of your CDO tenant.
Note: The CDO GraphQL API is no longer supported or available.
Updates to Firewall Migration Tool
CDO now hosts an updated version of the Firewall Migration Tool. You can now optimize network and port objects before migrating them from a Secure Firewall ASA device to a threat defense device. In addition, you can migrate DHCP, DDNS, and SNMPv3 configurations from an FDM-managed device to a threat defense device.
To know more about the other new features, refer to the Cisco Secure Firewall Migration Tool Release Notes.
CDO Tenant Notifications and User Notification Preferences Relocation
The tab for notifications and user preferences have moved. Notifications, now located in the navigation bar located to the left with Settings > Notification Settings, allow you to manage email subscriptions and third-party service integrations. User Preferences, now located Username ID > Preferences > Notification Preferences, can be configured to trigger whenever a device associated with your tenant experiences a specific action, a device certificate is expiring or has expired, or a background log search starts, finishes or fails. Note that User Notification Preferences are unique to each individual user whereas Tenant Notifications are applied to every user affiliated with the tenant. See Tenant Management for more information.
Device Certificate Expiry Notification
CDO now monitors the expiration status of the Cisco Secure Client (formerly AnyConnect) certificate, and the management certificate of ASA, FDM-Managed, and FTD devices. It notifies the user when these certificates are nearing their expiration date or have expired.
See Device Certificate Expiry Notification.
May 16, 2024
Cisco Security Cloud Control support for Multicloud Defense
The Cisco Security Cloud Control enterprise now supports adding an existing Multicloud Defense account; you can add a Multicloud Defense tile to your Security Cloud enterprise dashboard to monitor and centralize your management of other Cisco product instances, user identity, and user access management across Cisco Security Cloud portfolio.
See Multicloud Defense in Cisco Security Cloud Control in the Multicloud Defense User Guide for more information.
April 25, 2024
Dark Theme in CDO
CDO now offers a Dark theme option for a more customizable user interface look. Click the admin drop-down on the top right corner, navigate to Settings > General Settings > User Settings, and click Dark in the Theme field. The default theme is the Light theme.
See User Settings for more information.
April 18, 2024
Automatically Synchronize Network Objects to On-Prem Secure Firewall Management Centers
You can now automatically and continuously synchronize your network objects in CDO to On-Prem FMCs managed by CDO. Note that this feature is disabled by default. To enable this feature, navigate to Tools & Services > Firewall Management Center, select an On-Prem FMC, choose Settings in the Actions pane, click Discover and Manage Network Objects, and click Enable automatic sync of network objects. Ensure you have the Discover and Manage Network Objects toggle enabled."
See Discover and Manage On-Prem Firewall Management Center Network Objects for more information.
April 3, 2024
The cloud-delivered Firewall Management Center was updated on April 2, 2024. This update introduces stability, hardening, and performance enhancements. See the Release Notes for Cloud-delivered Firewall Management Center for more information.
March 7, 2024
Improved CDO Tenant Provisioning
You can now create a CDO tenant using an enhanced, faster provisioning process. You can also create new CDO tenants even if you already have tenants. In addition, if you have an On-Prem Firewall Management Center that is not SecureX-enabled, you can now register it to the Cisco Security Cloud through CDO. If you do not have a CDO account, you can create one during the registration process. See Create a CDO Tenant for more information.
Disable Individual Threat Defense Devices From Sending Event Logs to the Cisco Cloud
You can now disable individual cloud-delivered Firewall Management Center-managed threat defense devices (Version 7.4.1 or later) from sending event logs to the Cisco cloud. This device-level control allows you to temporarily stop threat defense devices from sending event logs sent to the cloud, if required. To specify which threat defense devices are to be disabled from sending event logs to the Cisco cloud, click Inventory, select the corresponding threat defense devices, and click Cloud Events from the Device Management pane.
Simplified Secure Device Connector and Secure Event Connector Installation on Ubuntu
You can now easily deploy Secure Device Connector and Secure Event Connector on Ubuntu server using the GitHub project available on the Cisco DevNet site. For more information, refer to this document and watch this video on YouTube.
February 13, 2024
Updates to Cloud-Delivered Firewall Management Center
Cisco Defense Orchestrator released an update to the cloud-delivered Firewall Management Center. Read the Release Notes for Cloud-delivered Firewall Management Center to learn about the many new features included in the update.
January 25, 2024
Updates to Firewall Migration Tool
CDO now hosts an updated version of the Firewall Migration Tool. You can now migrate WebVPN configurations from your Secure Firewall ASA devices to Zero Trust Access Policy configurations on threat defense devices managed by the cloud-delivered Firewall Management Center. You can also migrate SNMP, DHCP, DVTI configurations from ASAs to threat defense devices and ECMP routing configurations when migrating from a multi-context ASA device to a single-instance threat defense device. Read the Cisco Secure Firewall Migration Tool Release Notes to know about the other new features included in the release.
December 14, 2023
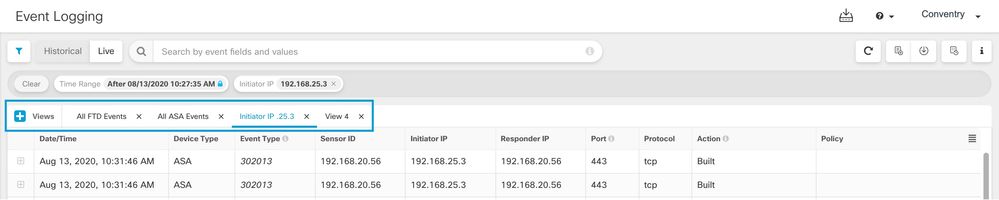
Monitor Additional Event Types for Threat Defense Devices
CDO now supports new firewall event types such as AAA, BotNet, Failover, and SSL VPN for threat defense devices.
Navigate Analytics > Event Logging and filter from the new list of events available under FTD Events. See Event Types in CDO for more information.
December 07, 2023
Manage On-Prem Firewall Management Center Network Objects Using CDO
You can now manage and share network objects from a CDO-managed On-Prem Firewall Management Center to threat defense devices managed by other On-Prem Firewall Management Centers, the cloud-delivered Firewall Management Center, and to CDO-managed ASA and threat defense devices. This helps promote consistency in network object definitions across platforms managed by CDO.
After onboarding an On-Prem Firewall Management Center, navigate Tools & Services > Firewall Management Center, select the device and choose Settings, and enable the Discover & Manage Network Objects toggle button.
See Discover and Manage On-Prem Firewall Management Center Network Objects for more information.
November 30, 2023
Schedule a Secure Firewall Threat Defense Device Backup in Cloud-delivered Firewall Management Center
Use the cloud-delivered Firewall Management Center to perform scheduled backups of the Secure Firewall Threat Defense devices it manages. See Schedule Remote Device Backups for more information.
November 16, 2023
Improved Cloud-Delivered Firewall Management Center Provisioning
CDO now provides an enhanced, faster provisioning process for cloud-delivered Firewall Management Center. When you enable the cloud-delivered Firewall Management Center on your tenant, CDO provisions it automatically and notifies you through the CDO notifications center and the applications in which you have configured incoming webhooks. To enable it, navigate Tools & Services > Firewall Management Center > > FMC > Enable Cloud-Delivered FMC.
See Enable Cloud-delivered Firewall Management Center on Your CDO Tenant and Notification Settings for more information.
November 2, 2023
Onboard a Threat Defense Device to an On-Prem Management Center with Low-Touch Provisioning
You can now select an On-Prem Firewall Management Center as the managing platform when you onboard a threat defense device with the low-touch provisioning method. This supports on-prem management for new devices or devices that have not been previously configured or managed. See Onboard a Secure Firewall Threat Defense Device With Low-Touch Provisioning for more information.
October 26, 2023
CDO Support for FDM-Managed Devices, Version 7.4
CDO now supports version 7.4 for FDM-managed devices. These are the aspects of support CDO provides:
-
Onboard a supported physical or virtual FDM-managed devices running version 7.4 to CDO.
-
Upgrade FDM-managed devices from versions 6.4+ to version 7.4.
-
Support for existing Secure Firewall Threat Defense features.
-
Onboard a supported physical or virtual device running version 7.4 to cloud-delivered Firewall Management Center.
See Cisco Secure Firewall Threat Defense Compatibility Guide for more information.
Updates to Firewall Migration Tool
CDO hosts an updated version of the Firewall Migration Tool. Using this, you can merge multiple transparent firewall-mode contexts that are present in your Secure Firewall ASA devices into a transparent-mode instance and migrate them.
In addition, you can migrate the site-to-site and remote access VPN configurations from your Fortinet and Palo Alto Networks firewalls to the threat defense devices managed by Cisco's cloud-delivered Firewall Management Center. See the Secure Firewall Migration Tool Release Notes for more information.
October 19, 2023
Updates to Cloud-Delivered Firewall Management Center
Cisco Defense Orchestrator released an update to the cloud-delivered Firewall Management Center. Read the release notes for cloud-delivered Firewall Management Center to learn about the many new features included in the update. See the Release Notes for Cloud-delivered Firewall Management Center: A Feature of Cisco Defense Orchestratorfor a complete list of the new features.
Migrate Secure Firewall Threat Defense Devices with Site-to-Site VPN Configurations from On-Prem to Cloud-Delivered Firewall Management Center
Site-to-site VPN configurations on Secure Firewall Threat Defense devices are now migrated along with the rest of the configuration when the device is migrated from the on-prem Firewall Management Center to the cloud-delivered Firewall Management Center. See Migrate On-Prem Management Center managed Secure Firewall Threat Defense to Cloud-delivered Firewall Management Center for more information.
October 12, 2023
ASA System Settings Policy
CDO provides the ability to create a system settings policy to effortlessly manage essential configurations for ASA devices such as domain name services, HTTP, enabling the secure copy server, message logging, and allowing VPN traffic without checking access control lists. You can apply this policy to multiple ASA devices, and any change made to the policy affects all devices using this policy. Additionally, you can individually edit device-specific settings for a single ASA device and override the shared system settings with device-specific values.
Choose Policies > ASA System Settings.
See ASA System Settings for more information.
October 5, 2023
CDO Support for ASA Static Routing
You can now use the CDO user interface to configure static routes for the ASA. This feature lets you specify where to send traffic for specific IPv4 or IPv6 destination networks without having to use the CLI.
See ASA Static Routing for more information.
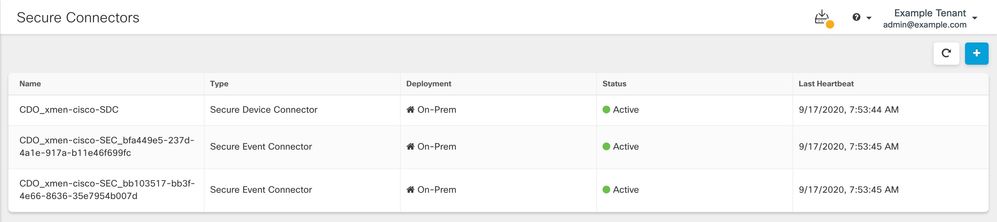
September 14, 2023
Navigation Change for Secure Event Connectors
You can no longer access the Secure Connectors page by expanding the admin menu in the top right. To manage Secure Connectors, navigate to Tools & Services > Secure Connectors.
See Secure Event Connectors for more information.
September 7, 2023
Configure ASA Interfaces using CDO User Interface
You can now configure ASA’s physical network interfaces, logical subinterfaces, and EtherChannels using a graphical user interface in CDO. You can also view Virtual Tunnel Interfaces that are created during route-based site-to-site VPN.
See ASA Interface Configuration for more information.
August 31, 2023
Manage Your Cloud-Delivered FMC, On-Prem FMCs, and Secure Connectors from the Services Page
You can now manage your cloud-delivered Firewall Management Center, On-Prem Firewall Management Centers, and secure connectors from the new Services page. Choose Tools & Services > Firewall Management Center or Secure Connectors. Refer View Services Page Information to know more.
August 17, 2023
Know the Health Status of Your Threat Defense Devices
CDO now displays the health and node status for threat defense devices on the Inventory page. For more details about the device health, you can click on the health status of a device to navigate to the device's health monitoring page in the cloud-delivered Firewall Management Center or the On-Prem Firewall Management Center user interface. Note that node status is displayed only for threat defense devices managed by cloud-delivered Firewall Management Center.
For more information, see Managing On-Prem FMC with Cisco Defense Orchestrator and Managing Cisco Secure Firewall Threat Defense Devices with Cloud-delivered Firewall Management Center.
August 3, 2023
Updates to Firewall Migration Tool
Cisco Defense Orchestrator now hosts an updated version of the Firewall Migration Tool. You can now merge multiple contexts in your Secure Firewall ASA devices to a routed-mode instance and migrate them to threat defense devices managed by the cloud-delivered Firewall Management Center. In addition, the migration tool now leverages the virtual routing and forwarding (VRF) functionality to replicate the segregated traffic flow observed in a multi-context ASA environment, which will be part of the new merged configuration.
See Migrating Secure Firewall ASA Managed by CDO in Migrating Firewalls with the Firewall Migration Tool in Cisco Defense Orchestrator guide for more information.
July 20, 2023
EasyDeploy for Virtual Threat Defense Devices Managed by GCP
You can now create a virtual threat defense device and deploy it to a Google Cloud Platform (GCP) project simultaneously. The EasyDeploy method combines the steps required to create a new virtual device and then associating the device with the cloud environment, streamlining the procedure and minimizing the amount of time required for setup.
Note that you must have cloud-delivered Firewall Management Center enabled for these onboarding flows. See Deploy a Threat Defense Device to Google Cloud Platform for more information.
July 13, 2023
Open CDO and Cloud-delivered Firewall Management Center Portals on Different Browser Tabs
You can now open CDO and cloud-delivered Firewall Management Center portal pages in different browser tabs and simultaneously work in both CDO and cloud-delivered Firewall Management Center.
See Support to Open CDO and Cloud-delivered Firewall Management Center Applications on Different Tabs for more information.
June 29, 2023
Schedule a Background Search in the Event Viewer
You can now run a background search in the Event Viewer on a re-occurring schedule. The schedule supports absolute time (example: May 1 to May 5th) or a sliding window (example: "The last day").
See Schedule a Background Search in the Event Viewer for more information.
Support for New Event Attributes
Now, Security Group, Encrypted Visibility Process Confidence Score, Encrypted Visibility Threat Confidence, Encrypted Visibility Threat Confidence Score, Encrypted Visibility Fingerprint are supported syslog event attributes in CDO's event viewer. When you customize your event logging view you can create a column for any of these newly supported attributes.
June 15, 2023
Migrate Your Firewalls using the Firewall Migration Tool in CDO
You can now migrate configurations from your Secure Firewall ASA devices, FDM-managed threat defense devices, and third-party firewalls such as Check Point, Palo Alto Networks, and Fortinet firewalls to the cloud-delivered Firewall Management Center using the Firewall Migration Tool in Cisco Defense Orchestrator. See Migrating Firewalls with the Firewall Migration Tool in Cisco Defense Orchestrator guide for more information.
June 8, 2023
EasyDeploy for Virtual Threat Defense Devices Managed by AWS and Azure
You can now create a virtual threat defense device and deploy it to an Amazon Web Services (AWS) or Azure
environment simultaneously. The easydeploy method combines the steps required to create a new virtual
device and then associating the device with the cloud environment, streamlining the procedure and minimizing
the amount of time required for setup.
Note that you must have cloud-delivered Firewall Management Center enabled for these onboarding flows.
See Deploy a Threat Defense Device with AWS and Deploy a Threat Defense Device with an Azure VNet
respectively for more information.
June 5, 2023
CDO Introduces the Multicloud Defense Solution
Multicloud Defense Solution specializes in security policy orchestration and protection of cloud network traffic, and cloud applications and workloads. It delivers unified security policies and web protection across multiple cloud types, provides network visibility into your cloud assets, and integrates services like threat intelligence and external logging. It enforces ingress traffic to, and egress traffic from, your cloud account, as well as the "east-west" network traffic within your cloud account.
Multicloud Defense Solution currently supports AWS, Azure, Google Cloud Platform, and Oracle OCI cloud accounts.
See About Multicloud Defense for more information, and Multicloud Defense 90-Day Free Trial to try out the Multicloud Defense Solution.
April 27, 2023
Improved Event Filtering
You can now filter events further with a relative time range. Absolute time range is an explicitly stated time frame. An example of a relative time range is last 3 days or last 3 hours. This can help target traffic and events that may not necessarily be included in an absolute time range. See Search for Events in the Events Logging Page for more information.
March 23, 2023
Background Search for Event Logging
CDO provides you the ability to define a search criteria and search for events in event logs based on any defined search criteria. Using the background search capability, you can perform event log searches in the background, and view the search results once the background search is completed.
Based on the subscription alert and service integrations you have configured, you can be notified once the background search has been completed. Learn more about background searches used with event logging.
January 18, 2023
Monitor Remote Access VPN Sessions of FTDs
Cisco Defense Orchestrator can now monitor Remote Access VPN sessions of FTDs managed using the cloud-delivered Firewall Management Center in CDO.
The RA VPN monitoring page provides the following information:
- A list of active and historical sessions.
- The details of the device and user associated with each session.
For more information, see Monitor Remote Access Virtual Private Network Sessions.
December 15, 2022
Updates to Cloud-Delivered Firewall Management Center
Cisco Defense Orchestrator released an update to the cloud-delivered Firewall Management Center. Read the release notes for cloud-delivered Firewall Management Center to learn about new features included in the update.
December 1, 2022
Route Based Site-to-Site VPN Support for ASA
Using Cisco Defense Orchestrator, you can now create a site-to-site VPN tunnel between peers with Virtual Tunnel Interfaces configured. This supports route based VPN with IPsec profiles attached to the end of each tunnel. Any traffic routed into the IPSec tunnel is encrypted regardless of the source/destination subnet.
VTI-based VPNs can be created between:
- A CDO-managed ASA and any route-based VPN-capable device.
- Two CDO-managed ASAs.
See Site-to-Site Virtual Private Network for more information.
Global Search
The global search feature in CDO allows you to search for and navigate to devices managed by CDO. This feature now supports the search capability for devices that are managed in cloud-delivered Firewall Management Center from the CDO user interface. From the search results, you can navigate to the corresponding pages in cloud-delivered Firewall Management Center.
See Global Search for more information.
October 27, 2022
Duo Admin Panel Onboarding and Multi-Factor Authentication Logging
CDO can now onboard the Duo Admin Panel and show the logs as MFA events in the dashboard and tabular forms. You can also export the MFA sessions of one or more devices to a file containing a comma-separated value (.csv).
The Duo Admin Panel records a Multi-Factor Authentication (MFA) log containing information on whether the user's two-factor authentication has passed or failed.
See "Onboard Duo Admin Panel" and "Monitor Multi-Factor Authentication Events" in Cisco Defense Orchestrator Guide for more information.
October 20, 2022
New Features in Cloud-Delivered Firewall Management Center
Support for Configuring Next-hop IP Addresses in a Policy-based Route Map
Policy-Based Routing (PBR) helps route network traffic for specified applications based on your priorities, such as source port, destination address, destination port, protocol, applications, or a combination of these objects, rather than by destination network criteria. For example, you can use PBR to route your high-priority network traffic over a high-bandwidth, expensive link and your lower priority network traffic over a lower bandwidth, lower cost link.
The cloud-delivered Firewall Management Center now supports defining next-hop IP addresses when creating a policy-based route map. See About Policy Based Routing and Configure Policy-Based Routing Policy in Managing Firewall Threat Defense with Cloud-Delivered Firewall Management Center in Cisco Defense Orchestrator for more information.
URL Filtering Enhancements
URL filtering lets you control access to websites that the users on your network can use. You can filter websites based on category and reputation, for which your device needs a URL-filtering license, or manually by specifying URLs. The category and reputation-based filtering—the quicker and smarter way to filter URLs—uses Cisco's up-to-date threat intelligence information and is highly recommended.
The cloud-delivered Firewall Management Center can now query for up-to-date URL category and reputation information directly from the Cisco Talos cloud instead of using the local database information. The local database gets updated every 24 to 48 hours. See URL Filtering Options in Managing Firewall Threat Defense with Cloud-Delivered Firewall Management Center in Cisco Defense Orchestrator for detailed information.
Umbrella Tunnel Integration with Secure Firewall Threat Defense using Cloud-Delivered Firewall Management Center
You can now automatically deploy IPsec IKEv2 tunnels to Umbrella from a threat defense device using cloud-delivered Firewall Management Center. This tunnel forwards all internet-bound traffic to the Umbrella Secure Internet Gateway (SIG) for inspection and filtering. Create a SASE topology, a new type of static VTI-based site-to-site VPN topology, using a simple wizard to configure and deploy the Umbrella tunnels.
See About Umbrella SASE Topology in Managing Firewall Threat Defense with Cloud-Delivered Firewall Management Center in Cisco Defense Orchestrator for more information.
Support for Remote Access VPN Policy in FTD to Cloud Migration
CDO now imports the remote access VPN policy during the migration of the FTD to cloud.
See Migrate FTD to Cloud in Managing Firewall Threat Defense with Cloud-Delivered Firewall Management Center in Cisco Defense Orchestrator for more information.
Migrate Flex Configured Routing Policies
Cloud-Delivered Firewall Management Center now supports the migration of Flex configured ECMP, VxLAN, and EIGRP policies to using the Migration Config option in the user interface.
See Migrating FlexConfig Policies in Managing Firewall Threat Defense with Cloud-Delivered Firewall Management Center in Cisco Defense Orchestrator for more information.
Smart Licensing Standardization
The license names used by cloud-delivered Firewall Management Center have been changed.
|
Old Name |
is now |
New Name |
|---|---|---|
| Base |
is now |
Essentials |
| Threat | is now | IPS |
| Malware | is now | Malware Defense |
| RA VPN/AnyConnect License | is now | Cisco Secure Client |
| AnyConnect Plus | is now | Secure Client Advantage |
| AnyConnect Apex | is now | Secure Client Premier |
| AnyConnect Apex and Plus | is now | Secure Client Premier and Advantage |
| AnyConnect VPN Only | is now | Secure Client VPN Only |
See License Types and Restrictions in Managing Firewall Threat Defense with Cloud-Delivered Firewall Management Center in Cisco Defense Orchestrator for more information.
New REST API Methods and Endpoints
New API endpoints and Methods
|
Name |
Methods |
URL |
|---|---|---|
|
Health |
||
|
Remote Access VPN Gateways |
GET, GET by ID |
|
|
Terminate VPN Sessions |
POST |
|
|
Integration |
||
|
Tunnel Deployments |
GET, POST |
|
|
Tunnel Transcripts |
GET by ID |
|
|
Policy |
||
|
Flex Config Policies |
GET, GET by ID, POST |
|
|
FTD Platform Settings |
GET, GET by ID |
|
Policy-Based Site-to-Site VPN Wizard for ASA
CDO now allows configuring a policy-based site-to-site VPN tunnel between two peers. This means that any traffic routed into the IPSec tunnel is encrypted regardless of the source/destination subnet.
To configure a policy-based site-to-site VPN, one of the following conditions must be met:
- Both peers are CDO-managed ASAs.
- One of the peers is a CDO-managed ASA and the other is any policy-based VPN capable device.
See Site-to-Site Virtual Private Network for more information.
August 4, 2022
CDO Support for FDM-Managed Devices, Version 7.2
CDO now supports version 7.2 for FDM-managed devices. These are the aspects of support CDO provides:
- Onboard a supported physical or virtual FDM-managed device running version 7.2 to CDO.
- Upgrade FDM-managed devices from versions 6.4+ to version 7.2.
- Support for existing Secure Firewall Threat Defense features.
- Onboard a supported physical or virtual FDM-managed device running version 7.2 to Cloud-Delivered Firewall Management Center.
Note: CDO does not support features introduced in the Secure Firewall Threat Defense, version 7.2 release.
June 30, 2022
Cisco Secure Firewall Migration Tool Supports Migrations to Cisco Secure Firewall Threat Defense
The Secure Firewall migration tool allows you to migrate Secure Firewall ASA configurations to a Cisco Secure Firewall Threat Defense managed by either an on-premises or virtual Secure Firewall Management Center, or by our new cloud-delivered Firewall Management Center in Cisco Defense Orchestrator. The desktop tool also supports migrations from third-party vendors Check Point, Palo Alto Networks, and Fortinet.
Cisco Secure Firewall Migration Tool Version 3.0 supports migrations to a Secure Firewall Threat Defense device running threat defense software version 7.2. That version of threat defense can be managed by a cloud-delivered Firewall Management Center on CDO. The migration process is part of CDO and does not require any specific license other than the CDO license.
You can download the Secure Firewall Migration Tool from the Software Download page.
CDO provides a wizard to help you migrate the following elements of the ASA's running configuration to the threat defense template:
- Access Control Rules (ACLs)
- Interfaces
- Network Address Translation (NAT) rules
- Network objects and network group objects
- Routes
Once these elements of the ASA running configuration are migrated, you can deploy the configuration to a new threat defense device that is managed by cloud-delivered Firewall Management center on CDO.
For more information, see Migrating ASA Firewall to Cisco Secure Firewall Threat Defense with the Cisco Secure Firewall Migration Tool.
June 9, 2022
Managing Cisco Secure Firewall Threat Defense Devices with Cloud-Delivered Firewall Management Center
Cisco Defense Orchestrator (CDO) is now the platform for the cloud-delivered Firewall Management Center.The cloud-delivered Firewall Management Center is a software-as-a-service (SaaS) product that manages Secure Firewall Threat Defense devices. It offers many of the same functions as an on premises Secure Firewall Management Center, it has the same appearance and behavior as an on-premises Secure Firewall Management Center, and uses the same FMC API.
This product is designed for Secure Firewall Management Center customers who want to move from an on-premises version of the Secure Firewall Management Center to a SaaS version.As a SaaS product, the CDO operations team is responsible for maintaining it. As new features are introduced, the CDO operations team updates CDO and the cloud-delivered Firewall Manager for you.
A migration wizard is available to help you migrate your Secure Firewall Threat Defense devices registered to your on-premises Secure Firewall Management Center to the cloud-delivered Firewall Management Center.
Onboarding Secure Firewall Threat Defense devices is carried out in CDO using familiar processes such as onboarding a device with its serial number or using a CLI command that includes a registration key. Once the device is onboarded, it is visible in both CDO and in the cloud-delivered Firewall Management Center, however, you configure the device in the cloud-delivered Firewall Management Center. Secure Firewall Threat Defense devices running Version 7.2 or later can be onboarded.
The license for cloud-delivered Firewall Management Center is a per-device-managed license and there is no license required for the cloud delivered FMC itself. Existing Secure Firewall Threat Defense devices re-use their existing smart licenses and new Secure Firewall Threat Defense devices provision new smart licenses for each feature implemented on the FTD.
In a remote branch office deployment, the data interface of the threat defense device is used for Cisco Defense Orchestrator management instead of the Management interface on the device. Because most remote branch offices only have a single internet connection, outside CDO access makes centralized management possible. In the case of remote branch deployment, CDO provides high availability support for the threat defense devices that it manages through the data interface.
You can analyze syslog events generated by your onboarded threat defense devices using Security Analytics and Logging (SaaS) or Security Analytics and Logging (On Premises). The SaaS version stores events in the cloud and you view the events in CDO. The on premises version stores events in an on premises Secure Network Analytics appliance and analysis is done in the on premises Secure Firewall Management Center. In both cases, just as with an on premises FMC today, you can still send logs to a log collector of your choice directly from the sensors.
The FTD dashboard provides you an at-a-glance view of the status, including events data collected and generated by all threat defense devices managed by the cloud-delivered Firewall Management Center. You can use this dashboard to view collective information that is related to the device status and the overall health of the devices in your deployment. The information that the FTD dashboard provides depends on how you license, configure, and deploy the devices in your system. The FTD dashboard displays data for all CDO-managed threat defense devices. However, you can choose to filter device-based data. You can also choose the time range to display for specific time range.
The Cisco Secure Dynamic Attributes Connector enables you to use service tags and categories from various cloud service platforms in cloud-delivered Firewall Management Center access control rules. Network constructs such as IP addresses may be ephemeral in virtual, cloud and container environments due to the dynamic nature of the workloads and the inevitability of IP address overlap. Customers require policy rules to be defined based on non-network constructs such as VM name or security group, so that firewall policy is persistent even when the IP address or VLAN changes.
Proxy sequences of one or more managed devices can be used to communicate with an LDAP, Active Directory, or ISE/ISE-PIC servers. It is necessary only if Cisco Defense Orchestrator(CDO) cannot communicate with your Active Directory or ISE/ISE-PIC server. For example, CDO might be in a public cloud but Active Directory or ISE/ISE-PIC might be in a private cloud.
Although you can use one managed device as a proxy sequence, we strongly recommend you set up two or more so that, in the event one managed device cannot communicate with Active Directory or ISE/ISE-PIC, another managed device can take over.
Any customer can use CDO to manage other device types like, the Secure Firewall ASA, Meraki, Cisco IOS devices, Secure Firewall Cloud Native, Umbrella, and AWS virtual private clouds. If you use CDO to manage a Secure Firewall Threat Defense device configured for local management with Firepower Device Manager, you can continue to manage them with CDO as well. If you are new to CDO, you can manage Secure Firewall Threat Defense devices with the new cloud-delivered Firewall Management Center and all of the other device types as well.
Learn more about the Firewall Management Center features we support in the cloud-delivered Firewall Management Center.
- Health Monitoring
- Secure Firewall Threat Defense Device Backup/Restore
- Scheduling
- Import/Export
- External Alerting with Alert Responses
- Transparent or Routed Firewall mode
- High Availability for Secure Firewall Threat Defense Devices
- Interfaces
- Network Access Control (NAT)
- Static and Default Routes and other routing configurations
- Object Management and Certificates
- Remote Access VPN and Site to Site VPN configuration
- Access Control policies
- Cisco Secure Dynamic Attributes Connector
- Intrusion and Detection and Prevention policies
- Network Malware and Protection and File Policies
- Encrypted Traffic Handling
- User Identity
- FlexConfig Policies
Onboard an On-Prem FMC with SecureX
If you have an on-prem FMC that is already associated with your SecureX account, you can onboard the FMC to CDO through SecureX. Devices onboarded through SecureX experience the same amount of feature support and functionality as a FMC onboarded through traditional methods. See Onboard an FMC with SecureX for more information.
Note: Even if your FMC account is associated with SecureX, we strongly recommend merging your CDO account with SecureX before you attempt to onboard the FMC. See Merge Your CDO and SecureX Accounts for more information.
May 12, 2022
ASA Policy Support for IPv6
ASA access policies and NAT configurations now support rules that use network objects and network groups containing IPv6 addresses. In addition, these rules can also specify ICMP and ICMPv6 protocols. Finally, ASAs now support AnyConnect Connection Profiles containing IPv6 addresses. See ASA Network Policies for more information.
Navigation to the Secure Connectors Page
The Secure Connectors page is accessible from the CDO menu bar. To view the Secure Connectors page, choose Admin > Secure Connectors.
April 14, 2022
This is the new feature we released this week.
Monitor AWS VPC tunnels using AWS Transit Gateway
CDO can now monitor AWS VPC tunnels using AWS Transit Gateway. For more information, see Monitor AWS VPC tunnels using AWS Transit Gateway.
April 6, 2022
Global Search
Global search provides an option to search for all onboarded devices and associated objects available within CDO. The search results allow you to navigate to the corresponding device and object pages. Currently, CDO supports global search for ASA, Firepower Management Center, Firepower Threat Defense, Meraki, and Secure Firewall Cloud Native devices.
For more information, see "Global Search" in the following documents:
Support for Cisco Secure Firewall 3100
Cisco Defense Orchestrator supports onboarding ASA and Firepower Threat Defense devices running on new Cisco Secure Firewall 3100 Series devices. Firepower Threat Defense devices can be onboarded using Low Touch Provisioning or by using a registration key or serial number.
February 3, 2022
Active Directory (AD) Groups in User Management
For an easier way to manage users in CDO, you can now map your Active Directory (AD) groups in CDO instead of managing individual users. Any user changes, such as a new user(s) addition, removing existing user(s), or changing roles can now be done in Active Directory without changing anything within CDO. CDO now also supports multiple-roles per user with AD. For more information, see the "Active Directory Groups in User Management" section of the User Management chapter of you're device's configuration guide.
Improved Charts View for Active Remote Access VPN Sessions
CDO now provides a new and improved charts view for your active RA VPN sessions. In addition to the charts you are already familiar with, CDO now displays a heat map of the location of users connected to your RA VPN headends. This map is available only in the live view.To view the new charts view, on the RA VPN Monitoring page, click the Show Charts View icon appearing at the top-right corner of the screen. 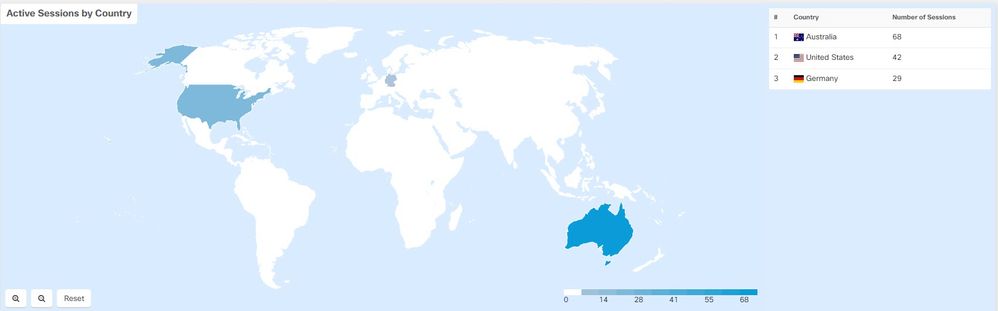
January 20, 2022
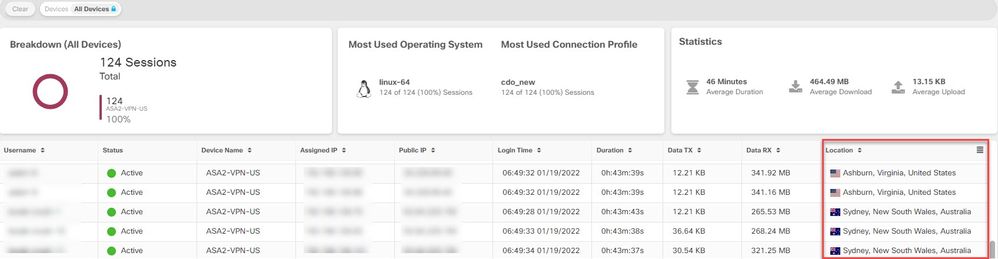
Geolocation Information of Remote Access VPN Users
The remote access VPN monitoring page now shows the location of all users who are connected to the VPN headend. CDO obtains this information by geolocating the public IP addresses of the users. This information is available on live and historical views. On clicking the location in the User Details area in the left pane, the precise location of the user is shown on a map.
Devices & Services Page Renamed to Inventory
The Devices & Services page has been renamed, "Inventory." The Inventory table lists all the devices and services you manage with CDO. No features were added or removed as a result of the name change.
January 13, 2022
Enhanced Devices & Services Interface
The CDO Devices & Services interface now classifies devices and templates based on their type and displays them in the corresponding tabs dedicated to each device type.
December 9, 2021
CDO Support for Firepower Threat Defense, Version 7.1
CDO now supports Firepower Threat Defense (FTD), version 7.1 devices. These are the aspects of support CDO provides:
- Onboard a supported physical or virtual device running Firepower Threat Defense version 7.1.
- Upgrade from Firepower Threat Defense versions 6.4+ to version 7.1.
- Support for existing Firepower Threat Defense features.
These caveats apply to Firepower Threat Defense, version 7.1 support:
- CDO currently does not support backing up Firepower Threat Defense devices running version 7.1. Support for this functionality is planned for the first maintenance release of Firepower Threat Defense, version 7.1.
- CDO does not support features introduced in the Firepower Threat Defense, version 7.1 release.
For more information about the FTD features CDO currently supports, see Managing FTD with Cisco Defense Orchestrator.
New CDO Documentation Platform
Online Help
- Content describing all your devices in a single place.
- Context-sensitivity.
- Content matches found as you search.
- Search results highlighted in a table of contents puts information in a larger context.
Content Maintained on Cisco.com
- Availability on Cisco.com places all your Cisco documentation on one site.
- Device-specific configuration guides makes finding information easier.
- What's New for Cisco Defense Orchestrator continues to describe the latest features available in CDO.
November 11, 2021
This is the new feature we are releasing this week:
New SASE Tunnel Functionality in CDO
You can now edit SASE tunnels that have been read into or created through the CDO UI. Note that this function only supports tunnels between an Umbrella organization and an ASA peer device that is already onboarded to CDO. See Edit a SASE Tunnel for more information.
October 21, 2021
Improved SecureX Integration
For users who have not already linked SecureX with their CDO tenant, CDO now offers a streamlined integration with SecureX. This process allows you to quickly and securely connect your CDO tenant to your SecureX Organization and add a CDO module to the SecureX dashboard with a single click. If you do not have a SecureX Organization, you can create one during this process. See SecureX and CDO Integration for more information.
Upload an AnyConnect Package from CDO Repository
CDO now supports uploading the AnyConnect package to ASA and FTD devices from the CDO repository. The Remote Access VPN Configuration wizard presents AnyConnect packages per operating system, which you can select and upload to a device. See Upload AnyConnect package for ASA and FTD.
September 16, 2021
CDO Notifications with Service Integrations
CDO notifications now integrate with webhooks. The notifications selected in the Notification Settings page will be sent to the application or service integration of your choice. See Enable Service Integrations for CDO Notifications for more information.
Cisco Secure Firewall Cloud Native Support for Cisco Security Analytics and Logging
Cisco Security Analytics and Logging has been greatly expanded to support logging events from Secure Firewall Cloud Native!
Secure Firewall Cloud Native logging: Security Analytics and Logging (SAL SaaS) now supports logging from any Secure Firewall Cloud Native device. Users can choose to store Secure Firewall Cloud Native events in syslog format, NetFlow Security Event Logs (NSEL) format, or both in the Cisco Cloud and use Cisco Secure Cloud Analytics to analyze them. Customers that want to enable logging analytics will be required to enable NSEL logs to provide the necessary telemetry for the higher-tier SAL licenses.
- Traffic Analysis: Secure Firewall Cloud Native logs can be run through SAL’s traffic analysis and observations and alerts can be reviewed by cross-launching Cisco Secure Cloud Analytics from CDO. Cloud Native customers only logging syslog events must switch to NSEL logs to enable traffic analytics.
- Customers acquiring Logging Analytics and Detection and Total Network Analytics Detection licenses can provision and use a Secure Cloud Analytics portal for analysis. Secure Cloud Analytics detections include observations and alerts specifically enabled using firewall logging data, in addition to the other detections available to SAL users as part of Secure Cloud Analytics core capability. Existing Logging and Troubleshooting license holders can test the detection capabilities of higher licenses with no commitment for 30 days.
- Free Trials: You can start a no-commitment 30-day SAL trial for all licenses by filling out this form. This trial requires only a minimal set of on-premises connectors for exporting data to the cloud. You can use this trial to evaluate SAL capabilities, and estimate the data volume required to support production environments, as a precursor to purchasing the appropriate daily volume for SAL licenses. To this end, the SAL trial will not throttle data for most user volumes. In addition, an estimator tool helps you estimate SAL daily volume.
See Cisco Security Analytics and Logging for Secure Firewall Cloud Native and Implementing Cisco Security Analytics and Logging for Secure Firewall Cloud Native for more information.
August 26, 2021
CDO and Umbrella Integration
CDO now supports Umbrella integration. You can onboard Umbrella organizations and view, manage, and create SASE tunnels that exist between Umbrella and ASA devices. ASA devices utilize Umbrella's SIG tunnel and inspection which provides centralized management for easy-to-use security. For more information about what Umbrella is and how CDO communicates with it, see Managing Umbrella with Cisco Defense Orchestrator.
When you onboard an Umbrella organization, we recommend onboarding the ASA devices associated with that organization as well. See Onboard an Umbrella Organization for more information.
August 13, 2021
Duo Configuration Support using LDAP for FTD RA VPN
You can now configure Duo two-factor authentication using LDAP for an FTD Remote Access VPN connection.
Use the Duo LDAP server as the secondary authentication source along with a Microsoft Active Directory (AD) or RADIUS server as the primary authentication source. With Duo LDAP, the secondary authentication validates the primary authentication with a Duo passcode, push notification, phone call, or SMS.
See Duo Two-Factor Authentication using LDAP for more information.
July 8, 2021
Digital Certificate Management Support for ASA
CDO now manages digital certificates on ASA devices. You can add a digital certificate such as identity certificates and trusted CA certificates as trustpoint objects and install them on one or more managed ASA devices. You can also export an installed identity certificate to duplicate a trustpoint configuration on a different ASA manually.
You can upload or create an identity certificate in the following formats:
- PKCS12 file with a passphrase
- Self-signed certificate
- Certificate Signing Request (CSR) signed by a certificate authority
The Remote Access VPN uses digital certificates for authenticating ASA and AnyConnect clients to establish a secure VPN connection.
See ASA Certificate Management for more information.
AnyConnect Module Support for RA VPN ASA and FTD
CDO now supports managing AnyConnect modules on ASA and FTD devices.
Note: This feature is supported on FTD running software version 6.7 or later versions.
As part of your RA VPN group policy creation, you can now configure a variety of optional modules to be downloaded and installed when a user downloads the Cisco AnyConnect VPN client. These modules can provide services such as web security, malware protection, off-network roaming protection, and so on.
You can associate each module with a profile containing your custom configurations, created in the AnyConnect Profile Editor and uploaded to the CDO as an AnyConnect File object.
See Upload RA VPN AnyConnect Client Profile, Create New ASA RA VPN Group Policies, and Create New FTD RA VPN Group Policies topics to learn how to upload the profiles and assign them to group policies.
July 1, 2021
This is the new feature we are releasing this week:
Snort 3 Support
CDO now supports the Snort 3 processing engine for FTD devices running Version 6.7 and later. The Snort engine automatically updates new snort rules to keep your device compliant with the latest vulnerabilities. You can perform a standalone upgrade from Snort 2 to Snort 3 or upgrade the device system and the Snort engine simultaneously for an abridged upgrade experience.
See Upgrade Snort 3 for more information.
Custom Intrusion Prevention System Policy
CDO now supports Snort 3 and customized Intrusion Prevention System (IPS) policies for FTD devices running Version 6.7 and later. The improved Snort 3 processing engine allows you to create and customize IPS policies using rules provided by the Cisco Talos Intelligence Group (Talos). The best practice is to create your own policy based on the provided Talos policy templates and change that if you need to adjust rule actions. See Custom Firepower Intrusion Prevention System Policy for more information.
Note: Be aware of the differences and limitations when you upgrade to or from Snort 3, as the upgrade may change how your rules are configured. See About Snort 3 for more information.
June 17, 2021
CDO Support for Firepower Threat Defense, Version 7.0
CDO now supports Firepower Threat Defense (FTD), 7.0. You can onboard an FTD device running FTD 7.0, or use CDO to upgrade the device to that version. CDO continues to support existing FTD features in addition to the new Reputation Enforcement on DNS Traffic. This features is an access control policy setting. Enable this option to apply your URL filtering category and reputation rules to DNS lookup requests. See Configuring Access Policy Settings. CDO has limited support for these features:
- FTDv Tiered License Support-Version 7.0 supports performance-tiered Smart Licensing for FTDv devices based on throughput requirements and RA VPN session limits. CDO does not fully support tiered smart licensing at this time. You can onboard an FTDv device that uses a tiered license but you cannot update the license using CDO. Use the device's Firepower Device Manager to install and manage licenses on the FTDv. See FTD Licensing Types for more information.
- Scan Interface Support-If an interface is added to a Firepower device by using the Firepower eXtensible Operating System (FXOS) Chassis Manager, on the Firepower 4100 series or 9300 series devices, you will need to configure that interface on FDM and then have CDO "check for changes" to the device to read in the configuration. See Synchronizing Interfaces Added to a Firepower Device using FXOS for more information.
- Virtual Router Support-VRF routes are not seen in CDO. You can onboard a device with virtual route support but you will not be able to see the virtual route in CDO's static routing page. See About Virtual Routing and Forwarding for more information.
- Equal Cost Multi Path Routing (ECMP) - CDO can onboard a device that uses ECMP and read the configuration but doesn't allow you to modify them. You can create and change the ECMP configuration through FDM and then read it into CDO. See Static Routes for more information.
- Rulesets - You cannot apply rulesets to an FTD 7.0 device.
See Managing FTD with Cisco Defense Orchestrator for more information about the FTD features CDO currently supports.
June 10, 2021
This is the new feature we are releasing this week:
Cisco Secure Firewall Cloud Native Support
The Cisco Secure Firewall Cloud Native seamlessly extends Cisco's industry-leading security to a cloud-native form factor (CNFW) using Kubernetes (K8s) orchestration to achieve scalability and manageability. Amazon Elastic Kubernetes Service (Amazon EKS) gives you the flexibility to start, run, and scale Kubernetes applications in the AWS cloud. Amazon EKS helps you provide highly-available and secure clusters and automates key tasks such as patching, node provisioning, and updates.
CDO allows onboarding of this firewall and provides complete firewall management:
- View real-time and historical data from AnyConnect RA VPN sessions.
- Create and manage objects and use them in different policies that handle ingress and egress traffic in your network.
- Recognizes and reconciles changes made to the firewall outside of CDO, using the Kubernetes command-line tool.
See Managing Cisco Secure Firewall Cloud Native With CDO for more information. You can also read Cisco Secure Firewall Cloud Native At-a-Glance for additional information.
Enhanced Remote Access VPN Monitoring
In addition to monitoring the live AnyConnect Remote Access VPN session, CDO now allows monitoring the historical data from AnyConnect Remote Access VPN sessions recorded over the last three months.
You can monitor VPN sessions across all Adaptive Security Appliance (ASA), Firepower Threat Defense (FTD), and Cisco Secure Firewall Cloud Native (SFCN) VPN head-ends in your tenant.
These are some of the salient enhancements made to the current release:
- Displays intuitive graphical visuals to provide at-a-glance views from all active VPN head-ends managed by CDO.
- The live session screen shows the most used operating system and VPN connection profile in the CDO tenant. It also shows the average session duration and data uploaded and downloaded.
- The historical session screen plots a bar graph to show data recorded for all devices in the last 24 hours, 7 days, and 30 days.
- Provides new filtering capabilities to narrow down your search based on criteria such as device type, session length, and upload and download data range.
Open the Remote Access VPN Monitoring screen from the navigation bar by clicking VPN > Remote Access VPN Monitoring.
Open the Remote Access VPN Monitoring screen from the navigation bar by clicking VPN > Remote Access VPN Monitoring.
See Remote Access Virtual Private Network Monitoring for more information.
New User Role
CDO now provides a new user role, the VPN Sessions Manager user role, that allows specific users the ability to terminate VPN sessions per tenant. Note that terminating VPN sessions is the only action this role allows; users designated with this role are otherwise limited with read-only capabilities. See User Roles for more information.
May 27, 2021
This is the new feature we are releasing this week:
Improved Device Notifications in CDO
You can now subscribe to CDO email alerts and view recent notifications within the CDO UI.
Receive email alerts for when a device associated with your tenant experiences a workflow or event change. Workflow changes include deployments, upgrades, or backups; event changes include devices going online or offline, conflict detection, HA or failover state, and site-to-site VPN connection status.
Note that these customizable notifications and alerts are applied to all devices associated with your tenant and are not device-specific. See Notification Settings for more information.
March 25, 2021
Cisco Security Analytics and Logging Availability in APJC
Cisco Security Analytics and Logging is now available in the Asia (APJC) region through the newly commissioned Tokyo data store. Security Analytics-enabled accounts will have access to the Cisco Stealthwatch Cloud service in Sydney, Australia for security-related alerting. With this, the Asia region has been brought up to par with capabilities available in the Americas and EU regions. See the Cisco Security Analytics and Logging Ordering Guide for more information.
March 18, 2021
EtherChannel Interface Support
CDO now supports EtherChannel interface configuration on supported models running Firepower Version 6.5 and later, such as the Firepower 1010, 1120,1140,1150, 2110, 2120, 2130, 2140. EtherChannel is a port link aggregation technology or port-channel architecture that allows the grouping of several physical Ethernet links to create one logical Ethernet link for the purpose of providing links between switches, routers and servers.
Note that the configuration that you apply to the physical ports affects only the LAN port where you apply the configuration. For more information about device support and configuration limitations, see Guidelines and Limitations for Firepower Interface Configuration for more information.
March 15, 2021
These are the new features we are releasing this week.
ASA Remote Access VPN Support
CDO now allows creating Remote Access Virtual Private Network (RA VPN) configuration on Adaptive Security Appliance (ASA) devices to enable remote users to connect to the ASA and securely access the remote network. It also allows managing the RA VPN settings that have already been configured using other ASA management tools, such as the Adaptive Security Defense Manager (ASDM) or Cisco Security Manager (CSM).
AnyConnect is the only client that is supported on endpoint devices for RA VPN connectivity.
CDO supports the following aspects of RA VPN functionality on ASA devices:
- SSL client-based remote access
- IPv4 and IPv6 addressing
- Shared RA VPN configuration across multiple ASA devices
See Configuring Remote Access VPN for an ASA for more information.
ASA File Management Support
CDO provides the File Management tool for performing basic file management tasks such as viewing, uploading, or deleting files present on the ASA device's flash (disk0) space. Using this tool, you can upload any files such as the AnyConnect software images, DAP.xml, data.xml, host scan image files to a single or multiple ASA device using URL-based file upload from the remote server.
This tool helps you to upload the newly released AnyConnect image to multiple ASA devices simultaneously.
See ASA File Management for more information.
February 11, 2021
This is the new feature deployed by CDO this week:
Multiple Secure Device Connector Support
You can now deploy more than one on-premises Secure Device Connector (SDC) for your tenant. This allows you to manage more devices with CDO and maintain communication performance between CDO, your SDCs, and your managed devices.
You can move managed ASA, AWS VPC, and Meraki MX devices from one SDC to another.
Having multiple SDCs also allows you to use one CDO tenant to manage devices in isolated network segments. Do this by assigning all managed devices in the isolated network segment to a single SDC.
See Using Multiple SDCs on a Single CDO Tenant for more information.
January 21, 2021
This is the feature and improvement to CDO made this week.
Firepower Management Center Object Reading
Now when you onboard an FMC to CDO, CDO imports the objects from the FMC-managed FTD devices. Once imported to CDO, the objects are read-only. Though the FMC objects are read-only, CDO allows you to apply a copy of the objects to other devices on your tenant that are not managed by the FMC. The copy is disassociated from the original object so you can edit the copy without changing the value of the object that was imported from the FMC. FMC objects can be used on any device you manage that support that object type. See FMC Objects for more information.
January 14, 2021
Exporting CLI Command Results
You can export the results of CLI commands issued to a standalone device, or several devices, to a comma separated value (.csv) file so you can filter and sort the information in it however you like. You can export the CLI results of a single device, or many devices at once. See Export CLI Command Results for more information.
Configuring Cloud Services for your FTD Devices
Connecting to the Cisco Success Network and configuring which events are sent to the Cisco cloud are features that can be configured on FTD devices running software version 6.6 or higher.
Cisco Success Network
By enabling Cisco Success Network, you are providing usage information and statistics to Cisco to improve the FTD and to make you aware of unused or additional features that will help you maximize the value of Cisco products in your network. When you enable the Cisco Success Network, your device establishes a secure connection to the Cisco Cloud and maintains this secure connection at all times. See Connecting to the Cisco Success Network for more information.
Send Events Directly to Cisco Cloud
You can now specify which types of events you send from your FTD directly to the Cisco cloud. Once stored in the Cisco cloud, you can use cloud applications, such as Cisco Threat Response, to analyze the events and to evaluate threats that the device might have encountered. See Sending Events to the Cisco Cloud for more information.
Web Analytics
Enabling web analytics provides anonymous product usage information to Cisco based on page hits. The information includes pages viewed, the time spent on a page, browser versions, product version, device hostname, and so forth. This information can help Cisco determine feature usage patterns and improve the product. All usage data is anonymous and no sensitive data is transmitted. See Enabling or Disabling Web Analytics for more information. You can use CDO to configure this feature on all versions of FTD.
January 7, 2021
This is the new feature and improvement CDO released this week.
FTD HA Pair Onboarding
CDO has enhanced the process of onboarding an FTD HA pair. Once you onboard one of the HA peers with either the registration token method or the login credentials method, CDO automatically detects that the corresponding peer is not onboarded yet and prompts you to take action. The improvement minimizes the effort required to onboard both devices, shortens how long it takes to onboard the peer device, and reuses any registration keys or smart license tokens you may have used to onboard the first device. See Onboard an FTD HA Pair with a Registration Key or Onboard an FTD HA Pair using Username, Password, and IP Address respectively for more information.
You can onboard either the active or the standby device, and once synced, CDO will always detect that the device is part of an HA pair.
Note: We strongly recommend onboarding your FTD devices with the registration key method.
December 17, 2020 - CDO Public API
CDO has published its public API and provided you with documentation, examples, and a playground to try things out. The goal of our public API is to provide you with a simple and effective way to perform a lot of what you would normally be able to do in the CDO UI, but in code.
To use this API, you will need to know GraphQL. It is very easy to learn, and their official guide (https://graphql.org/learn/) provides a thorough, light read. We chose GraphQL because it is flexible, strongly typed, and auto-documenting.
To find the full schema documentation, simply go to the GraphQL Playground, and click the docs tab on the right side of the page.
You can launch the CDO Public API by selecting it from the user menu.
December 10, 2020
Export FTD Configuration
You can now export the complete configuration of an FTD device as a CDO-readable JSON file. You can import this file as an FTD model (FTD template) on any CDO tenant that you manage. For more information, see Export FTD Configuration.
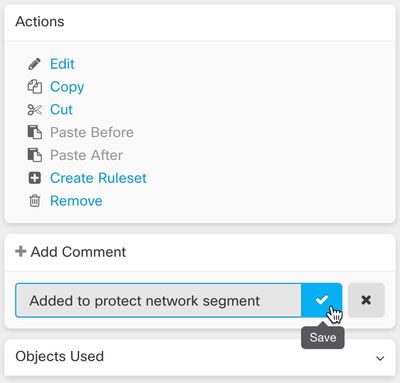
Adding Comments to FTD Rules
You can now add comments to rules in FTD policies and rulesets. Rule comments are are only visible in CDO; they are not written to the FTD nor are they visible in FDM. See Adding Comments to Rules in FTD Policies and Rulesets for more information.
November 13, 2020
Low Touch Provisioning and Serial Number Onboarding
Low touch provisioning is a feature that allows a new factory-shipped or re-imaged Firepower 1000 or 2100 series device, running FTD software version 6.7 or later, to be plugged in to your network, onboarded to CDO automatically, and then configured remotely. This eliminates many of the manual tasks involved with onboarding the device to CDO. The low touch provisioning process minimizes the need to log in to a physical device. It's intended for remote offices or other locations where your employees are less experienced working with networking devices.
Firepower 1000 and 2100 series devices with factory-installed FTD 6.7 images are expected to be orderable from Cisco at the end of calendar year 2020 or the beginning of calendar year 2021.
It is also possible to onboard a configured Firepower Threat Defense (FTD) version 6.7+ device to FTD 6.7, to CDO using the device's serial number.
See these articles for more information:
- Low Touch Provisioning
- Onboarding a FTD 6.7 Device with its Serial Number
- Firepower Easy Deployment Guide for Cisco Firepower 1000 or 2100 Firewalls
Assigning Firepower Threat Defense Interfaces to Security Zones
You can now assign an FTD interface to a security zone to further classify and manage traffic. See Assign a Firepower Interface to a Security Zone for more information.
November 6, 2020
CDO now supports Firepower Threat Defense (FTD), versions 6.6.1 and 6.7. You can onboard a new FTD device running FTD 6.6.1 or 6.7, or use CDO to upgrade to those versions. CDO continues to support existing FTD features and these new FTD 6.7 features:
- Secure Group Tags and SGT Groups
- Active Directory Realm Objects
- CDO TLS Server Identity Discovery and TLS 1.3
See Managing FTD with Cisco Defense Orchestrator for more information about the FTD features CDO currently supports.
October 15, 2020
New User Roles
CDO now provides two additional user roles that divide the responsibilities of editing policies and deploying policies. The new Edit-Only role allows users to make configuration changes to devices, but they are not allowed to deploy those changes. The new Deploy-Only role allows users to deploy pending configuration changes, but they are not allowed to make configuration changes. For the full list of capabilities and limitations of these new roles, see User Roles.
October 2, 2020
FTD API Support
CDO now provides the API tool interface to execute the Representational State Transfer (REST) Application Programming Interface (API) requests for performing advanced actions on an FTD device. Additionally, this interface provides the following features:
- Records a history of already executed API commands.
- Provides system-defined API macros that can be reused.
- Allows creating user-defined API macros using the standard API macros, from a command you have already executed, or another user-defined macro.
For more information about the FTD API tool, see Using FTD API Tool.
September 25, 2020
Multi-Tenant Portal Support
CDO now introduces a Multi-Tenant Portal that provides a consolidated view of devices from tenants across various regions. This view helps you glean information from your tenants in a single-window. You can have the CDO support team create one or more portals based on your requirements.
- Provides the Device Details view that provides the following information:
- Shows device location, software version, onboarding method, and many more details for each device.
- Allows you to manage the device on the CDO tenant page that owns that device.
- Provides a link to sign in to the CDO tenant in a different region and manage that device.
- Exports the portal's information to a comma-separated value (.csv) file to analyze or send it to someone who doesn't have access.
- Allows seamless addition of a new tenant using its API token.
- Allows switching between the portals without signing out from CDO.
For more information, see Manage Multi-Tenant Portal.
Secure Event Connector Support for Cloud-based Secure Device Connectors
Cisco Security Analytics and Logging (SaaS) customers can now install Secure Event Connectors when their Secure Device Connector is installed in the Cisco cloud. They no longer need to switch to an on-premises Secure Device Connector to configure Cisco Security Analytics and Logging.
See Installing Secure Event Connectors for more information.
September 17, 2020
Support for Multiple Secure Event Connectors
The Secure Event Connector (SEC) forwards events from ASAs and FTDs to the Cisco cloud so that you can view them in the Event Logging page and investigate them with Stealthwatch Cloud, depending on your Cisco Security Analytics and Logging licensing. Having more than one SEC allows you to install them in different locations and distribute the work of sending events to the Cisco cloud.
See these articles to learn how to install additional SECs on your tenant:
- Installing Multiple SECs, Using CDO Images, on Tenants with On-Premises SDCs
- Install Multiple SECs Using Your VM Image
Learn more about Cisco Security Analytics and Logging.
August 20, 2020
These are the new features and improvements CDO released this week.
Firepower Management Center Support
CDO can now onboard an Firepower Management Center (FMC) running Version 6.4 or later and all of its managed devices. FMC support is limited to onboarding an FMC, viewing the devices it manages, and cross-launching to the FMC UI.
- To review how CDO manages an FMC appliance, see Managing FMC with Cisco Defense Orchestrator.
- To onboard an FMC, see Onboard an FMC.
- To review supported FMC hardware and software versions, see Software and Hardware Support by CDO.
Customizable Event Filters
Cisco Security Analytics and Logging (SaaS) customers can create and save customized event filters on the Event Logging page for repeated use. See Customizable Event Filters for more information.
Improved Search Capabilities in the Event Logging Page
Cisco Security Analytics and Logging (SaaS) customers will now benefit from these improvements to the search capability on the Event Logging page:
- Click an element attribute to add it to the search field.
- Drag and drop columns on the Event Logging page to view your event information the way you want to.
- New AND NOT and OR NOT search operators in the Event Logging page provide more granular event search capability.
See Searching for and Filtering Events in the Event Logging Page for more information.
August 13, 2020
These are the new features we are releasing this week.
Custom Conflict Detected Polling Interval
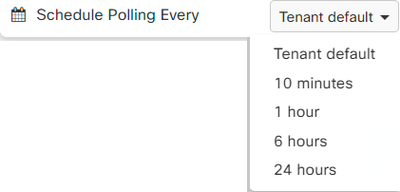
You can now configure custom polling intervals by device, regardless of the device type or any previously configured polling intervals. This includes detection for device state or any detected out of band changes.
See Schedule Polling for Device Changes for more information.
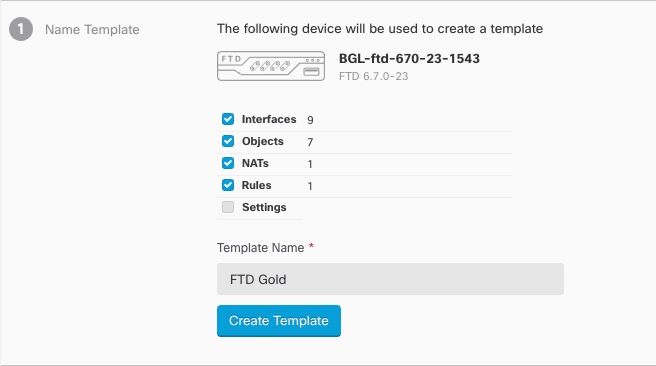
Custom FTD Templates
You can now create a custom FTD template by selecting one or more parts (Access Rules, NAT Rules, Settings, Interfaces, and Objects) of an onboarded FTD device's configuration. Applying a custom template to other FTDs will retain, update, or remove the existing configuration based on the included parts. However, CDO still allows you to select all parts to create a complete template and apply it to other FTDs.
See FTD Templates for more information.
July 30, 2020
These are the new features we are releasing this week.
Object Overrides
CDO introduces “Object Overrides” that allow you to provide an alternate value for a shared network object, which the system uses for the devices that you specify. It enables you to create a smaller set of shared policies for use across devices without giving up the ability to alter policies when needed for individual devices. Object override makes it possible to create an object that can be overridden on some or all devices that use it in a shared policy or ruleset.
To override an object, see Object Overrides.
Improved Network Group Wizard
The Network Group editing wizard has been improved to create new network objects instantly and modify the existing ones. It also allows you to add device-specific additional values to devices on which the shared network group is defined.
For more information about the improvements made to Network Group Wizard, see Create or Edit a Firepower Network Object or Network Group and Create or Edit ASA Network Objects and Network Groups.
July 9, 2020
These are the features and improvements deployed today!
Customize the RA VPN and Events Views
You can now customize the tables generated for Remote Access Virtual Private Network (RA VPN), as well as both live and historical event views. Organize and save the tables in the manner that best suits your needs and what is crucial to your portfolio. To customize the RA VPN view, see Remote Access Virtual Private Network Monitoring. To customize the Events view, see Viewing Live Events and Viewing Historical Events.
July 2, 2020
These are the features and improvements deployed today!
SecureX
You can now incorporate CDO into SecureX, which provides a summarization of devices, policy, and applied objects per tenant to strengthen your visibility and automation across your security portfolio. See SecureX for more about how to incorporate CDO and SecureX.
For more information about SecureX capabilities, see Cisco's SecureX product page. To log into your SecureX account, click here.
Cisco Security Analytics and Logging Event Downloads
After filtering ASA and FTD events on the Event Logging page, you can now download your results in a compressed .CSV file.
- The events you add to a downloadable .CSV file are defined by a time range.
- A single .CSV file can accommodate up to approximately 50 GB of compressed information.
- Generation of downloadable files can be done in parallel.
- Once created, the .CSV files are stored in Cisco cloud and downloaded directly from there. These files do not consume any CDO/SWC server resources.
- Completed downloadable .CSV files are stored for 7 days and then deleted.
See Downloading Events for more information.
June 18, 2020
These are the new features we are releasing this week.
Firepower Threat Defense Executive Summary Report
You can now generate a custom Executive Summary Report on any or all of your onboarded Firepower Threat Defense (FTD) devices. The report displays a collection of operational statistics such as encrypted traffic, intercepted threats, detected web categories, and more. Read FTD Executive Summary Report for more information about what the report offers and how you can use it to improve your network infrastructure. To create and manage your reports, see Generating FTD Executive Summary Reports.
Cisco Security Analytics and Logging Improvements
ASA Syslog and NSEL Events Support
Cisco Security Analytics and Logging has been greatly expanded to support logging events from ASAs!
- ASA logging: Security Analytics and Logging (SAL) now supports logging from any Cisco ASA Firewall, regardless of how it is managed. Users can choose to send ASA logs in syslog format, NetFlow Security Event Logs (NSEL) format, or both. Customers that want to enable logging analytics will be required to enable NSEL logs to provide the necessary telemetry for the higher-tier SAL licenses.
In addition to existing FTD logging, this makes CDO the first product in Cisco’s Security portfolio to truly aggregate and unify logging for Cisco’s entire firewall fleet.
See Cisco Security Analytics and Logging for ASA Devices and Implementing Cisco Security Analytics and Logging for ASA Devices for more information.
- Longer-term Storage and Download: Users can now opt-in to store logs for 1, 2, or 3 years when initially ordering SAL, or as an add-on later. Note that the default retention period of firewall logging remains 90 days. See Data Storage Plans.
- Traffic Analysis: Both FTD connection-level logs and ASA (NSEL) logs can be run through SAL’s traffic analysis, and observations and alerts can be reviewed by cross-launching to Stealthwatch Cloud using SecureX Sign-On. ASA customers only logging syslog must switch to NSEL logs to enable traffic analytics. Customers acquiring Logging Analytics and Detection and Total Network Analytics and Detection licenses can provision and use a Stealthwatch Cloud portal for analysis at no extra charge. Stealthwatch Cloud detections include observations and alerts specifically enabled using firewall logging data, in addition to the other detections available to SAL users as part of Stealthwatch Cloud’s core capability. Existing Logging and Troubleshooting license holders can test the detection capabilities of higher licenses with no commitment for 30 days.
- Free Trials: You can start a no-commitment 30-day SAL trial for all licenses by filling out this form. This low-touch trial requires only a minimal set of on-prem connectors for exporting data to the cloud. You can use this trial to evaluate SAL capabilities, and estimate the data volume required to support production environments, as a precursor to purchasing the appropriate daily volume for SAL licenses. To this end, the SAL trial will not throttle data for most user volumes. In addition, an estimator tool helps you estimate SAL daily volume.
Improved Event Monitoring for Security Analytics and Logging
- The Event Logging page in CDO now provides filtering of ASA events by type. You can see all your syslog events or NSEL events separately or together.
- Many ASA syslog events are parsed, providing greater detail about the event. That detail can be used to analyze the event in SWC.
- You can customize your view of the Event Logging page by showing only the columns of information you want to see and by hiding the rest.
- See Filtering Events in the Event Logging Page for more information.
June 4, 2020
Take a look at the new features and offers we are highlighting this week.
Monitor and Terminate Remote Access VPN Sessions
You can now use CDO to monitor live AnyConnect Remote Access VPN sessions across all Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) VPN head-ends in your tenant. It gathers information on the total number of active VPN sessions, currently connected users and sessions, the volume of data received and transferred.
You can view the performance of each RA VPN head-end in your tenant, filter sessions by head-ends, and select the session properties that you want to view in the VPN monitoring table. Also, you can export the RA VPN sessions of one or more devices to a comma-separated value (.csv) file. See Export RA VPN Sessions to a CSV File for more information.
You can terminate all the active RA VPN sessions of a single user on an ASA, and terminate all active RA VPN sessions of all users on an ASA. See Disconnect Active RA VPN Sessions on ASA and Disconnect Active RA VPN Sessions on FTD for more information.
Open the Remote Access VPN Monitoring screen from the navigation bar by clicking VPN > Remote Access VPN Monitoring. See Monitoring Live AnyConnect Remote Access VPN Sessions for more information.
AWS Virtual Private Cloud Management - Free Trial
Try managing your AWS VPC from CDO for free for 90 days. Open the Devices & Services page in CDO and onboard your AWS VPC to get started. See Onboard an AWS VPC for more information.
What's New Tile
The CDO landing page now has a What's New tile to showcase the latest features and when CDO implemented those features. If there is a feature that interests you, click the title of the feature to read the documentation about that specific feature.
May 20, 2020 - New API Only User
CDO now allows a Super Admin to create an “API Only User” that can be used to generate an API token for authenticating to CDO when making CDO REST API calls. This user account and the corresponding API token continues to function even after the original Super Admin departs your organization. See Create API Only Users for more information.
May 7, 2020 - Backup Firepower Threat Defense Devices Using CDO
- Backup devices on demand.
- Schedule recurring backups on a cadence from every day to every month, at the time you choose.
- Download backups and use Firepower Device Manager (FDM) to restore them.
See Backing Up FTDs for more information.
April 16, 2020
These are the features that we released this week:
CDO Support for Devices Running Firepower Threat Defense 6.6.0
CDO now manages FTD 6.6.0 devices. These are the new aspects of support CDO provides:
- Onboading a device running Firepower Threat Defense (FTD) 6.6.0.
- Upgrading FTD 6.4.x+ devices to FTD 6.6.0 devices. Devices can be individual FTDs or FTDs configured in a high-availability pair. These caveats apply to upgrade support:
- Upgrades for Firepower 4100 and Firepower 9300 devices is not currently supported.
- Customers can upgrade to FTD 6.6.0 using the drop-down in the upgrade page in CDO.
- CDO continuously develops support for FTD features and releases new feature support as it is ready.
For more information about the FTD features CDO supports, review Managing Firepower Threat Defense with Cisco Defense Orchestrator. See Firepower Threat Defense Support Specifics for a complete list of supported device types.
April 9, 2020 - Firepower Threat Defense Command Line Interface
You can now issue CLI requests to your FTD devices directly from CDO. See FTD Command Line Interface Documentation and Using the CDO Command Line Interface for more information.
April 2, 2020 - Improved License Management for Firepower Threat Defense Devices
Viewing FTD device license information, enabling and disabling licenses, and refreshing licenses is now all managed from a single button in the Device Actions pane on the Devices & Services page.
March 2020
These are the highlights of the features that we deployed in March 2020.
FTD Security Database Updates
CDO allows you to immediately update and, simultaneously, schedule future updates for security databases when you onboard you FTD device. This feature updates the SRU, security intelligence (SI), vulnerability (VDB), and geolocation databases. Note that you can only schedule future updates as part of the onboarding process. See Update FTD Security Databases for more information.
Support for Port Ranges in FTD Service Objects
CDO now supports creating service objects (also referred to as port objects in FTD) that contain a range of port numbers. See Create a Firepower Service Object for more information.
Cisco Secure Sign-on Domain Migration
On Tuesday March 24, 2020, at 5pm Pacific Daylight Savings Time, the official domain for Cisco Security Single Sign-on solution was moved from https://security.cisco.com to https://sign-on.security.cisco.com.
If you experience any issues please contact Cisco TAC, who can provide you with technical support.
FTD Rulesets
CDO introduces Rulesets for Firepower Threat Defense devices. A ruleset is a collection of access control rules that can be shared by multiple FTD devices. Any change made to the rules of a ruleset affects the other FTD devices that use the ruleset. An FTD policy can have both device-specific (local) and shared (rulesets) rules. You can also create rulesets from existing rules in an FTD device.
This feature is currently available for devices running Firepower Threat Defense 6.5 and later releases.
See FTD Rulesets for more information.
Copy or Move rules within an FTD Policy or to Another FTD Policy
It’s now possible to copy or move rules from the policy on one FTD to the policy on another FTD. We have also made it easier to move rules within an FTD policy so you can fine-tune the order in which rules evaluate network traffic.See Copy FTD Access Control Rules and Move FTD Access Control Rules for more information.
AnyConnect Software Package Upload to FTD Version 6.5+
You can now use CDO's Remote Access VPN wizard to upload AnyConnect packages from a remote server to a Firepower Threat Defense (FTD) device running FTD 6.5 or later. Ensure that the remote server supports HTTP or HTTPS protocol.See Upload AnyConnect Software Packages to an FTD Device Running FTD Version 6.5 or Later for more information.
Terminology Update in CDO's Interface
In order to manage a device, Cisco Defense Orchestrator (CDO) must have a copy of the device's configuration stored in its own database. When CDO "reads" a configuration, it makes a copy of the configuration stored on the device and saves it to CDO's database. We have renamed some interface options to better describe what you are doing when you perform a read action. This is the new terminology:
- Check for Changes. If a device's configuration status is Synced, the Check for Changes link is available. Clicking Check for Changes directs CDO to compare its copy of the device's configuration with the device's copy of the device's configuration. If there is a difference CDO immediately overwrites its copy of the device's configuration with the copy stored on the device.
- Discard Changes. If a device's configuration is Not Synced, clicking Discard Changes deletes any changes CDO made to its copy of the device configuration and also overwrites it with a copy of the configuration found on the device.
- Accept Without Review. This action overwrites CDO's copy of a device's configuration with the copy of the configuration stored on the device. CDO does not prompt you to confirm the action.
See Reading, Discarding, Checking for, and Deploying Configuration Changes for more information.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Would be nice to have the following features implemented for FTD Devices:
- EVERYTHING that's available for the ASA devices.
Definitely underwhelmed when I got this up for my firepower devices.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi CDO team, please stop adding new features, just fully test the ones that exist. It's a nightmare dealing with CDO for FTDs, I've been talking to TAC more than actually doing any work.
Thank you.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@edondurguti Thank you for the feedback. We are always looking how to make the product better and more robust. I am sorry to hear you are running into issues. I am a leader in the CDO engineering organization and would love to have a call with you to discuss what you have been dealing with and share our progress on some initiatives we have going on. Please send me a private message so we can connect. Thanks again!
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: