- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Cisco Cloud Web Security (CWS) On ISR-G2 - FAQ
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
02-10-2014 11:42 AM - edited 06-02-2021 07:26 AM
- CWS on ISR-G2 Interoperability with other features
- CWS with WAAS caveats.
- ISR-G2 platforms that support CWS.
- What is the minimum required image for CWS on ISR-G2?
- Does ISR-G2 CWS solution supports VRF?
- Are there MIBs for CWS connector?
- What are the licenses required to enable CWS on ISR-G2?
- What is the purpose of the source interface under content-scan parameter-map?
- Under dual ISP scenario (Active/Standby), which interface needs to be used as source interface?
- What needs checked when CWS Tower doesn’t come UP?
- What is GST?
- Which are the non-default ports that are supported on CWS Tower for traffic redirection?
- Does CWS Tower support Application (Facebook, Twitter, etc.) Scanning?
- What is whitelisting? (Traffic exceptions)
- How do I whitelist all HTTPS traffic?
- Whitelisting order of preference?
- Are Authentication methods always integrated with CWS?
- What is webauth Authentication?
- Is consent-page or Acceptable User Policy (AUP) supported without any Authentication?
- What if only the ip http server command is enabled on the box?
- What is the difference between NLTM/HTTP-BASIC active & passive mode?
- NTLM config sample:
- HTTP-BASIC config example:
- Webauth or auth-proxy configuration example:
- How do we bypass user authentication/exceptions (NTLM/Basic/Webauth)?
- Which browsers support Transparent NTLM Authentication?
- Does the ISR support source interface for LDAP authentication?
- How to pass the username & password securely during authentication?
- Why do I get the certificate warning pages when I enable the ip http secure-server command?
- What is the default order of preference for user-groups?
- How much memory does CWS use?
- What is the purpose of virtual-ip & virtual-host in ip admission rule?
- Does the LDAP server supports Multi-Domain?
- LDAP over SSL supported on ISR-G2?
- Does the AAA server support all Authentication methods?
- What is the maximum length of a single user-group supported?
- Are there any known limitations with respect to large amount of user-groups?
- Is there a limit on the HTTP header size set by default on the ISR?
- How to debug content-scan effectively?
- Is AAA Accounting supported for LDAP?
- Is Root Bind mandatory for NTLM Authentication?
- Why does the "test" command from CLI fail on an ISR?
- Why does active authentication fail while browsing on an AD server?
- Is NTLMv2 supported on ISR-G2?
- Is there support for LDAP Server Failover?
- Are Nested groups for AD supported?
- What happens if authentication fails?
- Are there any known issues with the latest browsers?
- CWS support new protocols like SPEEDY & QUIC?
- CWS support SAML Authentication?
- I see all the user-groups from the AD except “Domain Users” group, why?
- What ports are tower allowed outgoing ports?
- Does CWS support SNMP traps?
- How do I configure CWS?
- How do I configure IP Admissions and LDAP on ISRs for Web Redirection?
- Exciting new features on CWS 15.5(1) and above
- Regarding whitelist download from tower:
- When they are pushed from the CWS portal to the ISR will they show up in the "show run"?
- When they are pushed from the CWS portal to the ISR will they show up in the "show start"?
- When they are pushed from the CWS portal to the ISR, are they persistent after router restart in case towers are not accessible in the period after router is restarted?
- Are there any known limitations with this new Whitelist Download Feature?
- Last Updated On : June 18th, 2015
CWS on ISR-G2 Interoperability with other features
-
CWS with WAAS caveats.
-
WAAS + Akamai Connect at the branch location does have interop with CWS
-
CWS out will be defined on the physical Internet facing interface not the tunnel interface.
-
WCCP 62 redirect in/ 61 redirect out can be defined on the physical interface and the tunnel to optimize both intranet and Internet traffic.
-
In the event CWS is configured for multiple user groups, to maintain policy enforcement between groups when Akamai Connect is enabled on the local WAAS device you will need to select the checkbox in the WAAS Central Manager (WCM) that CWS is present).
-
If user group policies are not in place no need to select this check box to add extra overhead of the IMS check for all cache hit transactions.
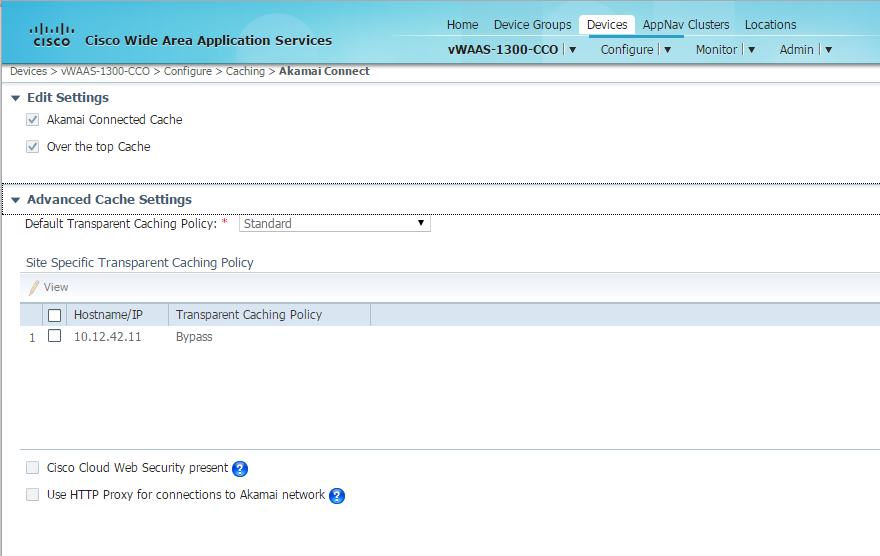
-
Akamai Connect has 3 main caching features, Transparent, Over the Top (OTT), and Connected Cache (ACC). When CWS is in place ACC, which allows the Akamai Connect device to take advantage of specific knowledge about content Akamai delivers, will not work today. This is because in the CWS cloud they implement a squid proxy which performs it’s own caching and the headers sent by WAAS and returned by Akamai are not maintained. There is work going on between the engineering and product teams to address this in a subsequent WAAS release and on the CWS side as well.
- CWS does not interoperate with CBAC Firewall (However, there is a workaround, which is adding explicit pinholes to the CWS Tower IP Address.
We recommend the use of Zone-Based Policy Firewalls with CWS)
CWS on ISR-G2 Limitation
- CWS supports only 32K concurrent sessions (Including both HTTP & HTTPS) irrespective of the platform.
- Header-based whitelisting (which includes host & user-agent based whitelisting) will not work if the network has asymmetric routing configured.
- Some of the Geography-specific services may not work if the CWS Tower does not belong to the same geographic region; the workaround is to whitelist such traffic.
- Host/Header-based whitelisting will not work for HTTPS traffic.
- CWS Tower does not support the traffic from applications; it capable of scanning only the traffic initiated from web browsers.
- ACL-based whitelisting with log options is not supported.
- NTLM Authentication & Browser Authentication Bypass will support only GET method in HTTP, rest of the methods like (POST, PUT, HEAD and so on) are not supported, and if any such request are received the connections are closed.
- Virtual-host resolving to open-DNS server will not work if wrongly configured. Functionality wise it does not have any impact, however customer should be aware of the security loop holes.
- IPV6 is not supported. CWS will not proxy IPv6 addresses nor will it return content from IPv6 only web servers. Today CWS will only proxy IPv4 addresses. It is not supported until we deliver the roadmap item later this year - 2HCY16.
Guidelines for IPv6 Web Traffic: Admin Guide:
-
Unless an exception for an IPv6 address, domain name, address range, or wildcard is specified, IPv6 web traffic is sent to the scanning proxy. The scanning proxy performs a DNS lookup to see if there is an IPv4 address for the URL that the user is trying to reach. If the scanning proxy finds an IPv4 address, it uses it for the connection. If no IPv4 address is found, the connection is dropped.
-
To enable all IPv6 traffic to bypass the scanning proxies, add ::/0 static exception for all IPv6 traffic. This exception makes all IPv6 traffic bypass all scanning proxies; therefore, IPv6 traffic is not protected by Web Security.
ISR-G2 platforms that support CWS.
ProductPlatform
| Cisco 800 series ISR |
819, 841M-4X/8X, 860VAE, 880VA, 881, 881W, 887V, 888E, 888EA, 888, 888W, 891, 891F, 891W, 892, 892F, 892FW, 892W, C892FSP-K9, C-881 |
|
Cisco 1900 Series ISR |
1905, 1921, 1941, 1941W |
|
Cisco 2900 Series ISR |
2901, 2911, 2921 and 2951 |
|
Cisco 3900 Series ISR |
3925, 3925E, 3945, 3945E |
What is the minimum required image for CWS on ISR-G2?
Cisco IOS Release 15.2(1) T1 and later releases support CWS. As of May 30th 2014, the most stable image is 15.3(3) M3; however periodically check Cisco.com for the latest updates.
Does ISR-G2 CWS solution supports VRF?
Yes. Presently the images that support VRF are 15.4(1)T, 15.4(1)T1, 15.4(2)T, 15.5(1)T, 15.4(3)M or above.
Are there MIBs for CWS connector?
No. There are no SNMP MIBs for CWS connector on ISR, ASA or WSA presently.
What are the licenses required to enable CWS on ISR-G2?
- Security k9 bundle on ISR-G2.
- Per seat-based CWS license depending on the number of users (seats) who will use the CWS service.
What is the purpose of the source interface under content-scan parameter-map?
The source interface or IP address is used to poll the CWS tower status using TCP ping on port 8080. This is a mandatory command under the content-scan global parameter-map, with out this command we can’t enable the content feature on the box.
Under dual ISP scenario (Active/Standby), which interface needs to be used as source interface?
In dual-WAN scenarios, we recommend that you configure a loopback interface and configure it as the source interface/IP address under the parameter-map. In this case, if one link goes down and comes back, there is no impact on the CWS feature. Network Address Translation (NAT) or routing rules must be configured correctly to ensure that the loopback address is routable outside the network. Route tracking needs to be configured to detect ISP failure.
What needs checked when CWS Tower doesn’t come UP?
- Ensure that the CWS tower hostname can be resolved to a CWS Tower IP address.
- Ensure that Access Control List (ACL), Domain Name System (DNS), NAT, routing & CWS License are correct.
- Ensure that Network Time Protocol (NTP) is configured on the router.
- Ensure that there is no upstream device that blocks requests to the CWS tower.
- Enable the debug content-scan control-plane CLI to collect more debugs, which will give the information about DNS Resolution, TCP Ping & GST(Gold Standard Test) validation.
What is GST?
GST stands for Gold Standard Test, This test will make sure that we are redirecting all the traffic to the actual CWS Tower instead of misconfigured or fake IP Address. ISR-G2 sends two special bytes while validating the license which can recognized only by the CWS Tower, if this check fails tower wouldn’t come up.
Which are the non-default ports that are supported on CWS Tower for traffic redirection?
HTTP traffic is only allowed on ports 80, 81, 70, 84, 210, 280, 488, 591, 777, and 1025-65535. HTTPS traffic is only allowed on ports 443, 444, 563, 4005, and 8443. Traffic from any other ports are rejected by the CWS Tower.
Does CWS Tower support Application (Facebook, Twitter, etc.) Scanning?
CWS Tower is not capable of scanning the traffic initiated from Andriod/iOS applications. Example: if you have a policy in the CWS Tower, which is configured to block Facebook, that policy will be applicable only for the traffic initiated from the Web browsers. If you use Facebook Apps on Android/iOS, these policies doesn’t get applied which means you will be able to access the Facebook content using those Apps.
What is whitelisting? (Traffic exceptions)
Traffic can be directly forwarded to the actual Web server instead of redirecting it to the CWS Tower. Traffic can be controlled by using IP (through ACLs), host-based (using regex), user-agent (Mozilla, Chrome, Safari and so on) user and user-group-based whitelisting.
Header-based (host) whitelisting is best suited for intranet sites. Example: wwwin*; however it is not recommended to block the real internet websites which are dynamic in nature may not give us the desired results.
Whitelisting is nowhere related to authentication, someone expects when they whitelist the traffic that traffic is not subjected to authentication as well, which is wrong, both are orthogonal features. If the customer wants to bypass the authentication they need to associate an ACL/user-agent to the ip admission rule. Please refer this link: https://supportforums.cisco.com/docs/DOC-34596#Whitelisting_optional
How do I whitelist all HTTPS traffic?
Configure only the HTTP port number under content-scan parameter-map configuration for both primary & secondary towers, so that only HTTP traffic is redirected and all the HTTPS traffic will be whitelisted.
Replace the following lines in the config
server scansafe primary name proxy1442.scansafe.net port http 8080 https 8080 server scansafe secondary name proxy1443.scansafe.net port http 8080 https 8080
With
server scansafe primary name proxy1442.scansafe.net port http 8080 server scansafe secondary name proxy1443.scansafe.net port http 8080
Whitelisting order of preference?
The following are the different types of whitelisting configuration supported on the box in the order of precedence:
- IP-based
- User/User-group-based
- Host/User-agent-based
Are Authentication methods always integrated with CWS?
No. Authentication methods and CWS redirections are two independent features on the ISR-G2, Users can club these features together for user granular policy. Previously, authentication methods were used to restrict the user access by downloading per-user ACL/Downloadable ACL, However, with CWS solution authentication methods are primarily used for user/user-group granular policy applications.
If an organization has unique IT security policy then configure a single global policy on the CWS Tower using the company key.
If an organization needs different policies for different set of users, then they can deploy any one of the authentication methods like (Webauth, HTTP-Basic Auth, or NLTM) based on their requirements and then configure the policies on the CWS Tower based on the user-groups.
What is webauth Authentication?
Follow this link to configure webauth or auth-proxy based authentication:
Is consent-page or Acceptable User Policy (AUP) supported without any Authentication?
There are two options for AUP.
1. AUP on the ISR side
Yes, AUP is supported using the "ip admission name <test>> consent" command without any authentication using the . Users just need to accept the consent policies (Terms & Conditions) then they are allowed to access the web content, which will be scanned through the CWS towers.
Refer the below link to configure AUP on the ISR:
http://www.cisco.com/c/en/us/td/docs/ios/sec_user_services/configuration/guide/12_2sr/sec_securing_user_services_12-2sr_book/sec_cons_feat_rtrs.html
2. AUP on the Tower side
AUP is supported/tested only with Windows/Linux based connectors. AUP is browser and cookie based. So if the browser does not support 3rd party cookies AUP feature may not work even on the Windows/Linux connector. Since this is browser and cookie based, this AUP on the tower side is not supported on the ISR connector.
What if only the ip http server command is enabled on the box?
Only HTTP requests will be intercepted by the ip admission rule [NTLM/WebAuth] and only HTTP web requests will be triggered for authentication. HTTPS web requests are not intercepted.
If the initial web request from a user is an HTTPS request, that request will not trigger any authentication. As the web request does not have any user granularity, the request will receive the default policy from the CWS Tower. This behavior applies until the user accesses an HTTP-based website. When the user accesses an HTTP request, the request is intercepted by the ip admission rule. After entering valid user credentials the session moves to ESTABLISHED state and subsequent HTTPS web requests will not have the user granularity issue.
What is the difference between NLTM/HTTP-BASIC active & passive mode?
In active mode, user validation and fetching of corresponding user-groups as part of authorization are done. In passive mode, user validation is not done; however, fetching of user-group as part of authorization from the LDAP server is carried out.
NTLM config sample:
aaa new-model
aaa group server ldap ss-ldap-gr
server ss-ldap
aaa authentication login default group ss-ldap-gr
aaa authentication login CONSOLE none
aaa authorization network default group ss-ldap-gr
aaa session-id common
ip admission name ntlma ntlm
ip http server
ip http access-class 23
no ip http secure-server
ip http max-connections 16
ldap attribute-map att_map
map type uid username
map type groupmembership supplicant-group
ldap server ss-ldap
ipv4 10.10.129.204
attribute map att_map
timeout retransmit 20
base-dn ou=active,ou=employees,o=cisco.com
authentication bind-first
interface Vlan1
ip admission ntlma
HTTP-BASIC config example:
When you configure the ip admission name http-basic command, client applications always prompt users to enter their credentials. Refer this link:
Router(config)# ip admission name admission1 http-basic
Webauth or auth-proxy configuration example:
Refer this link: http://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_usr_auth/configuration/15-s/sec-usr-auth-15-s-book/sec-cfg-authen-prxy.html
aaa new-model aaa authentication login default group tacacs tacacs-server host 172.31.54.143 tacacs-server key cisco ip http server ip http authentication aaa access-list 61 deny any ip http access-class 61 ip auth-proxy auth-cache-time 60 ip auth-proxy name HQ_users http interface ethernet0 ip address 10.1.1.210 255.255.255.0 ip auth-proxy HQ_users
How do we bypass user authentication/exceptions (NTLM/Basic/Webauth)?
Configure either ACLs or user-agents and then associate to the ip admission rule.
check this link to configure browser based authentication bypass:
Which browsers support Transparent NTLM Authentication?
Internet Explorer & Google Chrome.
Does the ISR support source interface for LDAP authentication?
Starting 15.4(3)M image, support for LDAP source interface has been added. Please refer this link for configuration sample and other details.
How to pass the username & password securely during authentication?
Enable the ip http secure-server command on ISR-G2. Once the ip http secure-server command is enabled, all transactions between the client and the router/server is encrypted.
Why do I get the certificate warning pages when I enable the ip http secure-server command?
While accessing some HTTPS-based websites some clients might encounter SSL errors/Certificate warnings because ISR-G2 uses a test server certificate when ip http secure-server command is enabled. To avoid these SSL errors/Certification warning, replace the certificate on ISR-G2 with a certificate signed by a certificate authority that the clients trust in that domain.
What is the default order of preference for user-groups?
- User-groups learned through authentication methods.
- Default user-group under ingress interfaces.
- Default user-group under global content-scan parameter-map.
How much memory does CWS use?
CWS requires around 10KB of memory per session. 9K session is going to require around 90MB.
What is the purpose of virtual-ip & virtual-host in ip admission rule?
Virtual-IP & virtual-host are required for Transparent NTLM authentication. By defining a virtual-host, initial web requests are redirected first to the virtual-host, which is part of the trusted domain. Because the box thinks that virtual-host belongs to the same trusted domain, it does not prompt for the user authentication because the same trusted domain (LDAP) is configured on the ISR.
The virtual-IP & virtual-hostname must be unique in a network and the virtual-host must be a DNS-resolvable address. Do not configure the virtual-IP address on any other devices in the network, including the ISR-G2 and loopback interfaces. If the virtual-IP address is configured on any other interface, while trying to "ping" the virtual-ip address and no response is received from ISR-G2. The virtual-IP address is not ICMP ping reachable; so the virtual-IP address will not ping. Because the virtual-IP address resides inside the ISR-G2, when the client browser is redirected to the virtual-IP (or virtual hostname) the client computer will try to make a Layer-4 TCP socket connection to that virtual-IP address and that connection attempt must be routed to the ISR-G2, so that the ISR-G2 can recognize the IP address and complete the three-way TCP socket connection with the client browser. If the client PC has multiple NIC cards, configure a static route for the virtual-IP to go through the ISR-G2.
NOTE: Transparent NTLM authentication works mainly on Windows. Users must be logged into the same domain as that configured on the ISR-G2. Transparent NTLM Authentication may not work for the smart devices such as (Android-based phones, iPhone’s, iPADs, and so on.)
iOS & Safari do support NTLM authentication, but they do not support Transparent NTLM Authentication. However, if a user enters the username & password for the first time in an iPAD, it will cache that user/password information and use that for any subsequent requests. The user is not prompted for the authentication unless the user manually clears the browser cache. After the first authentication, the user experience will be similar to NTLM Transparent authentication. This is tested with Apple – iPAD2 - iOS 5.1.1 using a Safari browser.
Minor changes are required in the ISR-G2 configuration for virtual-host for the authentication to work. Example: If the virtual-host name is isrproxy and the domain name is cisco.com, then the virtual-host needs to be appended with the domain name. [isrproxy.cisco.com]
This configuration change is required because iPAD's are not generally part of the domain and we need to explicitly append the domain name in the virtual-host to resolve the virtual-IP.
Does the LDAP server supports Multi-Domain?
No, we support only single domain configuration.
LDAP over SSL supported on ISR-G2?
Yes
Does the AAA server support all Authentication methods?
Webauth works with almost all sorts of authentication servers (RADIUS, TACACS+, LDAP, and Local Authentication). Whereas Basic-Auth & NTLM works only with LDAP.
What is the maximum length of a single user-group supported?
64 bytes (or Characters)
Are there any known limitations with respect to large amount of user-groups?
A single user-group can be up to 64 characters and the total user-groups length together should be 1200, after which the remaining part of the user-group length is truncated and sent to the CWS tower for policy applications.
Is there a limit on the HTTP header size set by default on the ISR?
Upstream devices like ISA may reject packets based on a large header size because of the additional x-CWS headers?
No. There are no such limits on ISR.
How to debug content-scan effectively?
Use conditional debugging for content-scan. You can define an ACL and associate the content-scan debug command which generate debugs only for the flow that matches the configured ACLs. Use buffered logging instead of logging console or terminal monitor.
Is AAA Accounting supported for LDAP?
No, accounting is supported only by RADIUS & TACACS+. Only Webauth can make use of the accounting feature that will help to monitor the usage of bandwidth for billing purpose.
Is Root Bind mandatory for NTLM Authentication?
Root Bind CLI is mandatory for NTLM passive authentication, without this CLI, the feature will not work. For Active NLTM this is not a mandatory requirement.
Why does the "test" command from CLI fail on an ISR?
Ideally test command should be used in conjunction with "no authentication bind-first".
ldap server ldap_server
base-dn DC=aaaldap,DC=com
no authenticate bind-first
By doing "no authentication bind-first" and clearing ldap server binding by the command below,
clear ldap server ldap_server
we are making sure, that the first ldap request sent to server is not bind (authenticate request) but a search request (look up request). By ensuring search first, the exact location of user from ldap server is fetched as part of attribute distinguished name "dn". Once that is done, actual bind (authenticate) with user-dn location (not base-dn command in the config).
Now, the "test aaa group ldap ldapuser3 password new" command will work without any error 49 (bad authentiation) messages in the ldap debugs.
That said, for NTLM deployments "authentication bind-first" command is necessary. So, once the "test" command is successful, we need to put the "authentication bind-first" command back in the config.
Why does active authentication fail while browsing on an AD server?
Active authentication on a browser on an AD server fails because the AD server is trying to protect itself from man-in-the-middle attack when a user uses the AD server to generate traffic and authentication request comes right back to the same AD server.
One can refer these links for further details:
Refer to the discussion with Microsoft support at - https://social.msdn.microsoft.com/Forums/en-US/41adba9a-bf45-4cba-a634-5cbc6bd71054/ntlmv1-authentication-fails-over-ldap-saslgssspnego?forum=os_specifications
Check this link for a workaround: http://support.microsoft.com/kb/914060
Warning This workaround may make a computer or a network more vulnerable to attack by malicious users or by malicious software such as viruses. We do not recommend this workaround but are providing this information so that you can implement this workaround at your own discretion.
Is NTLMv2 supported on ISR-G2?
Yes, it is supported but there is no additional configuration required on the ISR-G2; it is based on the client & server configuration. If the client and server is configured to use NTLMv2 message then the authentication will happen in NTLMv2, or else it will be with NTLMv1, which is less secure when compared to NTLMv2. ISR-G2 cannot be forced to do NTLMv2 authentication.
Is there support for LDAP Server Failover?
Yes. We do support LDAP server failover. Based on the LDAP server configuration, an LDAP server is chosen for user validation and authorization and if it fails, it will failover to the configured Secondary LDAP server and so on. If only one LDAP server is configured with no backup and the primary LDAP server fails, then none of the users will be authenticated.
Are Nested groups for AD supported?
Yes. However, there is no CLI available to specify the nested depth level. It will go and check the last node and fetch all the Nested Groups which may result in significant delays and affect the performance. Be cautious while choosing the Nested Groups option.
What happens if authentication fails?
When user authentication fails, the user becomes part of the default user-group. If watch-list is enabled those users will be displayed under show ip admission watch-list instead of show ip admission cache. The number of failed authentication attempts can be controlled by using the ip admission max-login-attempt command. Configuring the ip admission watch-list expiry timer command can modify the watch-list session expiry timer.
User authentication will fail even if LDAP server is not reachable for whatever reasons.
Are there any known issues with the latest browsers?
Smart browsers these days determine authentication is configured on port 80 and will try to reach the web via some other ports and can entirely skip the authentication and redirection, which is very risky. The solution is to restrict the port number which will have access to Internet either using ACL or firewall. This kind of behavior is mainly observed with BYOD devices.(Andriod/iOS/Windows Mobile)
CWS support new protocols like SPEEDY & QUIC?
No, we do not support any of the new protocols, which means we can’t deploy any CWS solution.
CWS support SAML Authentication?
Yes, it supports SAML Autentication. With this solution ISR-G2 acts just as a redirection device and all the SAML traffic is considered as pass through traffic; there is no specific configuration required on the ISR-G2, all the configs are done on the IDP, CWS Tower and AD. It is recommended not to configure any default user-group under the parameter-map content-scan global or else it will override the user-group learned through SAML authentication.
I see all the user-groups from the AD except “Domain Users” group, why?
Domain users (user-group) may not be fetched with the LDAP query.
Need to tweak the primaryGroupID ( 513 ) in order to get the Domain Users as the memberOf Attribute. Generally it is not recommended to do these changes in the live AD by editing the LDAP Attributes using ADSI edit.
Please refer the following links for this limitation.
http://stackoverflow.com/questions/5754924/ldap-query-not-work-for-group-domain-users
http://stackoverflow.com/questions/4443824/ldap-group-membership-including-domain-users
What ports are tower allowed outgoing ports?
CWS Tower allowed outgoing ports are:
- HTTP traffic is only allowed on ports 80 ,81 ,82 ,84 ,85 ,89 ,21 ,70 ,210 ,280 ,488 ,591 ,777 ,800 and 1025-65535
- HTTPS traffic is only allowed on ports 443, 444, 563 and 1025-65535
We do not support FTP on native port 21, but only support FTP over HTTP.
Does CWS support SNMP traps?
No, presently CWS does not support SNMP. Meaning, we are unable send a syslog message generated by CWS to the SNMP server.
How do I configure CWS?
Please refer this link: https://supportforums.cisco.com/document/147696/ios-scansafe-step-step-configuration
How do I configure IP Admissions and LDAP on ISRs for Web Redirection?
Please refer this link: https://supportforums.cisco.com/document/12116936/configuring-and-troubleshooting-ip-admissions-and-ldap-isrs-web-redirection
Exciting new features on CWS 15.5(1) and above
Release Notes for 15.5(1): http://www.cisco.com/c/en/us/td/docs/ios/15_5m_and_t/release/notes/15_5m_and_t/155-1TNEWF.pdf
Whitelist download from Tower (ISR): http://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_data_cws/configuration/15-mt/sec-data-cws-15-mt-book/cws-whitelist-towr-telmtry.html
Whitelist download from Tower (CWS tower side guide):
ISR connects to cwsuploads.sco.cisco.com (70.39.231.186) and grabs the latest whitelist. The cert with the serial no and expiry date of expiry date is Nov 18 21:59:46 2033 GMT
Serial Number:
61:03:cd:e0:00:00:00:00:00:07
is used to validate the CWS tower side certificate.
The certificate listed in the pool, some of which already expired and some expiring in Oct 2015 should not be of any concern. Those do not related to CWS so, the expiry should not have any impact to CWS service.
TAC UI: This is a troubleshooting feature that has been put in place specifically for TAC engineers to identity traffic patters, CPU and memory utilization on the ISR based on date and time. This is accomplished with the telemetry information that the ISR sends (when enabled) to the tower. There are no public documents for this feature.
Regarding whitelist download from tower:
When they are pushed from the CWS portal to the ISR will they show up in the "show run"?
No. You can only see the whitelist downloaded using a show command. The command is "show cws tower-whitelist". Refer the guide here: http://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_data_cws/configuration/15-mt/sec-data-cws-15-mt-book/cws-whitelist-towr-telmtry.html
When they are pushed from the CWS portal to the ISR will they show up in the "show start"?
No they don't. You can only see the whitelist downloaded using a show command. The command is "show cws tower-whitelist". Refer the guide here: http://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_data_cws/configuration/15-mt/sec-data-cws-15-mt-book/cws-whitelist-towr-telmtry.html
When they are pushed from the CWS portal to the ISR, are they persistent after router restart in case towers are not accessible in the period after router is restarted?
No. Since this doesn't get saved into the startup config (cannot be nvgened) upon router reload, the ISR has to establish connectivity with the tower to download it again.
Are there any known limitations with this new Whitelist Download Feature?
Last Updated On : June 18th, 2015
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello,
The FAQs do not provide clarity on non-domain PCs. For example, if I have 1000 user license for CWS and a non-domain PC that goes straight to the Internet via a broadband service, is LDAP configuration required despite the fact that no AD group needs to be queried.
For the 1000 user names, is uploading the list onto the Tower all that is required? Does the list to be uploaded need to have passwords
Is the ip admission http-basic command still needed for this scenario?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Let me try to clarify this query with three deployments.
Case: 1
Customer got only non-domain PC's and the organization doesn't have any LDAP ( AD server ), in this case we don't need any ip admission rules and all the users will be subjected to a global web policy on the CWS Tower.
Case: 2
Customer got both domain & non-domain PC's ( Eg: Windows & Macintosh Machines ), windows could be part of the domain, but the Macintosh machines are not generally joined to the domain ( non-domain ) PC's, but it can still authenticate to the LDAP server to make use of the user granular policies at the CWS Tower.
Case: 3
Lets say customer got two subnets, Subnet-A which has domain PC's and Subnet-B which has non-domain PC's, in the case customer can configure the Subnet B under the ip admission access-list to skip the authentication, and subject to a default web policy on the CWS tower for Subnet-B and user granular policies for Subnet-A
Thanks
Umanath(umans@cisco.com)
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks very much for the quick response. Apologies for more questions as I am want to properly understand CWS/ISR G2 and do not yet have access to the CWS tower to understand the features.
I understand that CWS licensing is based on User and not devices.
Referring Use case 1, which is a non-domain PC for public Internet use and assuming a 1000 user license;
If a public user logs onto the non-domain PC using a local account and opens a browser, I assume that there will be no pop-up for authentication, right? how does CWS know the license count if no authentication?
If I choose to have authentication with HTTP basic (pop-up only), what are the steps to authenticate 1,000 distinct users, assuming ldap servers are not required?
Thanks a lot
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Even though CWS licensing is based on Users, still it boils down to an ip address. Which means a single user can have multiple devices [ Eg; Mobile, iPAD, Laptop] CWS will treat this devices as 3 users.
Authentication factor is not considered to check the no of active licenses on the CWS Tower.
HTTP Basic ( pop-up only ) authentication without using LDAP server ? I don't think that's is supported if we need to use any one of the authentication method we need a backend server to authenticate the users ( LDAP )
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks Umanath for the clarifications.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Dear Support Community,
I have still have few concern regarding the ordering info of CWS license for ISR G2.
As far as I know about ISR license which is required it is SecK9 license on router ... but how to order for a connector key .. I have to place an order, and I am doing services in Cisco Partner vender...
Irfan Alam
CCNA CCNP CCDA CXFE
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
Sorry not a ISR2 question, but will CWS ever be supported on Cisco CSR 1000V? The commands for configuring CWS don't seem to be present in IOS-XE version 15.5.1 in Amazon.
Thanks
Jon
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
You will get the license key and the primary and secondary tower IPs when you get your router provisioned for CWS.
-Kureli
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
In a CWS deployment using ISR G2 connector:
Can we have multiple Domain Controllers authenticating users on a single ISR G2?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Only single domain authentication is supported.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
