- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Cisco IP Phone Anyconnect VPN to IOS
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
07-22-2010 08:01 AM - edited 08-23-2017 11:26 PM
- Feature Overview
- Supported Platforms
- Cisco Ip phone Software Requirements
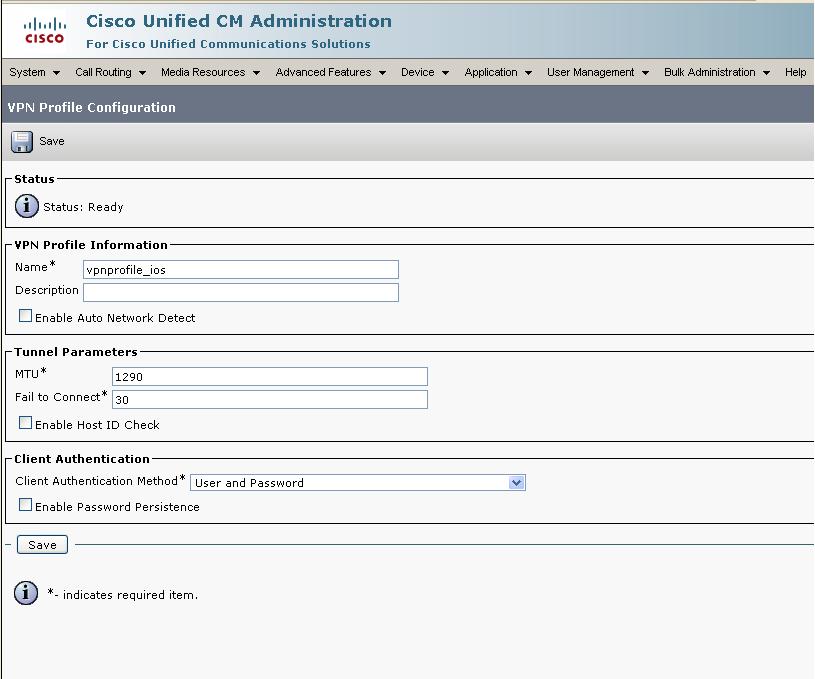
- Configuration
- CUCM Configuration
- Phone Configuration
- IOS Configuration
- Configuration Examples
- Configuration Example 1: Phone to IOS using username and password
- Troubleshooting
- Common Issues
Feature Overview
The Cisco IP Phone now has a built in VPN client based on SSL TLS/DTLS, the phone can directly establish a VPN connection (using anyconnect) to a ASA or IOS headend. This requires that the phone establish the initial connection inside of the corporate network to retrieve the phone configuration, then subsequent connections can be made using VPN as the configuration is retrieved on the phone. On IOS Cisco Ip phone client is supported starting 15.(1)2T.
Supported Platforms
Only the following phones are currently supported 7942 / 7962 / 7945 / 7965 / 7975
You can use Cisco Unified Reporting to determine which Cisco Unified IP Phones support the VPN client. From Cisco Unified Reporting, click Unified CM Phone Feature List. For the Feature, choose Virtual Private Network Client from the pull-down menu. The system displays a list of products that support the feature. For more information about using Cisco Unified Reporting, see the Cisco Unified Reporting Administration Guide.
Cisco Ip phone Software Requirements
The phone should be running load 9.0(2)SR1S - SCCP or later version.
CUCM should be running 8.0.1.100000-4 or greater.
IOS should be running 15.1(2)Tor later
Configuration
CUCM Configuration
The following document provides a complete set of configuration tasks required to configure CUCM for this feature:
http://www.cisco.com/en/US/docs/voice_ip_comm/cucm/security/8_0_1/secugd/secuvpn.html
Note: Please make sure the URL for the VPN Gateway contains the full URI including the path to reach the right context on the router. Example https://172.18.124.236/phonevpn
Phone Configuration
1. Use a supported phone model per the CUCM release notes
http://www.cisco.com/en/US/customer/docs/voice_ip_comm/cucmbe/rel_notes/8_0_1/delta/phones.html#wp1489245
2. Configure the IP Phone with a TFTP server manually.
3. Import the root certificate or identity certificate used by the router into to phone via CUCM
IOS Configuration
Use this as a baseline for router configuration:
http://www.cisco.com/en/US/products/ps5855/products_configuration_example09186a0080af314a.shtml
Configuration Examples
Configuration Example 1: Phone to IOS using username and password
IOS Router Configuration
Use this as a baseline for router configuration:
http://www.cisco.com/en/US/products/ps5855/products_configuration_example09186a0080af314a.shtml
This is a snippet of the configuration that pertains to webvpn/anyconnect on the router.
aaa new-model
aaa authentication login default local
webvpn gateway mygateway
! The ip address should match that of your router public interface
ip address 172.18.124.236 port 443
! The trustpoint will vary depending on your router- use show cry ca cert to find out
ssl trustpoint TP-self-signed-743301245
inservice
!
webvpn install svc flash:/webvpn/anyconnect-dart-win-2.5.0217-k9.pkg sequence 1
!
webvpn context mycontext
ssl authenticate verify all
!
!
policy group default
functions svc-enabled
svc address-pool "mypool"
svc keep-client-installed
svc split include 192.168.88.0 255.255.255.0
! Dtls is required
svc dtls
virtual-template 99
default-group-policy default
aaa authentication list default
gateway mygateway
inservice
Notes:
1) The gateway ip address should be changed to your router public interface ip address
2) The trustpoint will be different for each router. Use "show crypto ca cert" to see whats the router cert
3) SVC DTLS is a required command to enable DTLS, which is required for vpn phone due to the delay sensitivity for VOIP traffic.
This is enabled by default in the ISR G2 platforms:
C3900, C2951, C2900, C1900, CGR2010, C1906C, C890, C880
Other platforms, it will use software crypto. Use caution when enabling svc dtls when using software crypto
and high number of sessions as it may result in a high CPU condition affecting overall performance.
Importing the IOS Router Certificate into CUCM
The phone will not connect to any headend (ASA or IOS), unless the id cert of the router or the issuer cert (CA ) is imported into the call manager and configured on the vpn gateway on CM.
The first step is to get the router identity certificate or the issuing CA certificate as a file in base64 format so that it can be imported into CUCM. One way to get the certificate is to use a browser and browse to the IOS router URL configured for anyconnect in the previous step as show below using Internet Explorer:
1) Open IE and browse to the URL of the router configured for webvpn/anyconnect.
2) On the upper right corner you will see a "Certificate Error" with a cross icon or a pad-lock icon (if the certificate is trusted by your browser). Click on the red cross icon or the pad-lock icon and you will see a popup window like below.
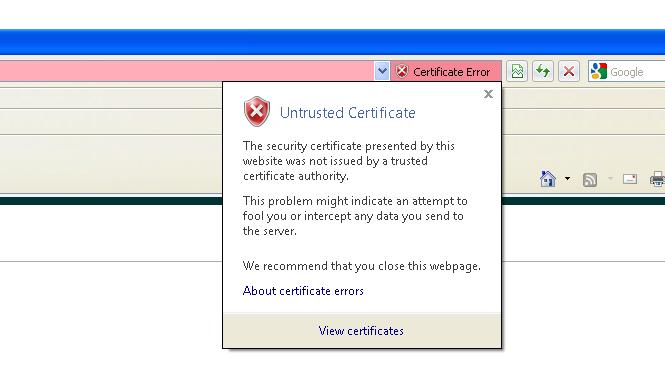
3) Click on View Certificates
4) Go to the details page.
Here, you can also see the CN (common name) and subject alternative name of router identity certificate. This can be used for verification that the router webvpn URL matches with the CN or SAN.
5) Click on "Copy to File" to copy the certificate to a file.
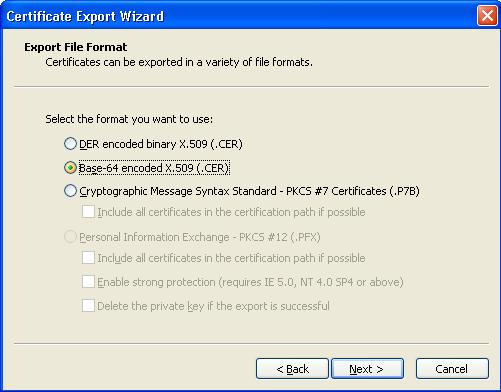
6) Select Base-64 as this is the format that CUCM will accept when importing.
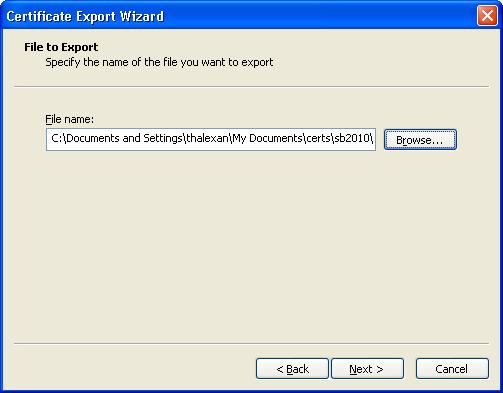
7) Click Next and then select a file name for the certificate.
Once the certificate file is saved in base 64 format, the next step is to import it into CUCM.
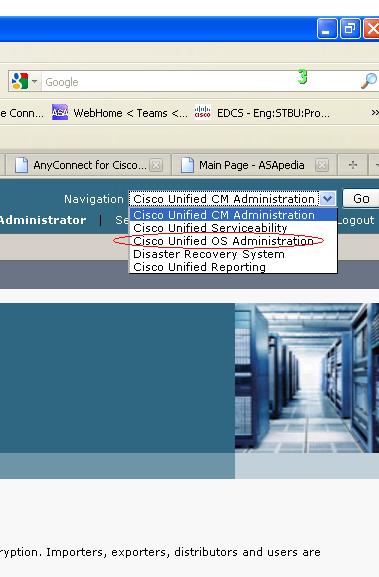
1) Log on to the CUCM administration page. Select "Cisco Unified OS Administration" from the Navigation drop down list.
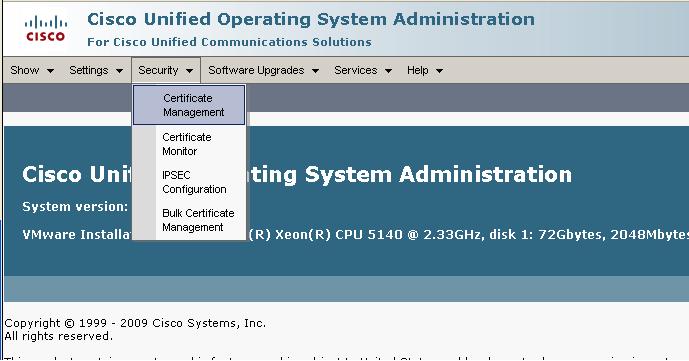
2)Select Security--->Certificate Management
3)Click on Upload certificate
4)For Certificate Name, Select Phone-VPN-trust and then select the base 64 file name for router that you get in earlier steps above. Then click on "upload file"
5) Now go back to the certificate list and click "find" to verify the id certificate of router exists on the CUCM.

CUCM Configuration
Use this a reference, when configuring CUCM: http://www.cisco.com/en/US/docs/voice_ip_comm/cucm/security/8_0_1/secugd/secuvpn.html
1. Login to CUCM Administration page
2.Configuring the VPN Gateway
Go to Advanced Features > VPN > VPN Gateway
Click Add to add a new VPN Gateway.
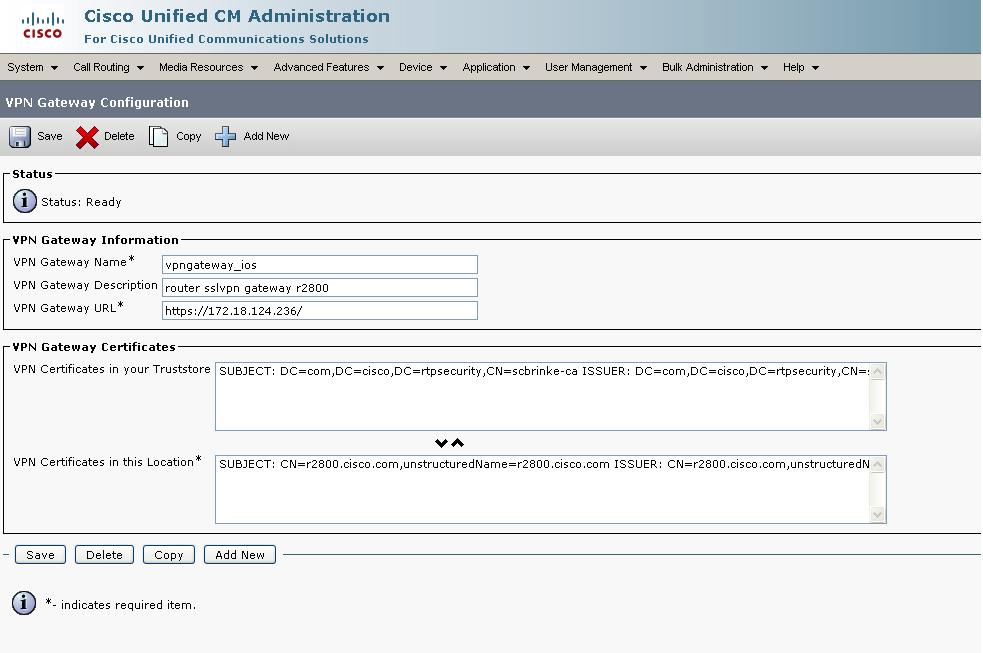
Enter a vpn gateway name and description. Enter VPN gateway URL https://172.18.124.236/ , this should match with the group-url created on the router. Now, select the rutercertificate that was imported earlier and move it to the "VPN Certificates in this Location" container, so that the ceritificate is put in the phone trusted list.
Note: Here we are using the default URL without a path, for this it work , hence the gateway URL configured on CUCM should have a slash "/" at the end: https://172.18.124.236/. This is a specific requirement for the phone when using the default URL.
3. Adding the VPN Group
In Cisco Unified Communications Manager Administration, choose Advanced Features > VPN > VPN Group. Click add to add a new vpn group.
Select and move the VPN Gateway vpngateway_ios that was created in step2 to the "Selected VPN Gateways in this VPN Group" container.
4.Configuring the VPN Profile
In Cisco Unified Communications Manager Administration, choose Advanced Features > VPN > VPN Profile.
Click "Add New" to create a new profile.
Select the default values .
Note: if the CN/SAN of the router certificate does not match the FQDN or ip address configured on the gateway under CUCM, then the "Enable Host ID Check" should be unchecked
Troubleshooting
Common Issues
Gateway url is not configured (or mismatch) on IOS/CUCM (call manager)
If the gateway url configured on CUCM does not match with the gateway URL configured on IOS router, then the phone VPN will fail to connect.
The phone when using username/password, will just attempt to connect and then fail and prompt again for username/password.
IOS Router Id cert or CA cert is not imported into CUCM (Call Manager)
The phone will not connect to any headend (ASA or IOS), unless the id cert of the router or the issuer cert (CA ) is imported into the call manager and configured on the vpn gateway on CM. The message on the phone is VPN Authentication failed Required Action: Please follow the steps in the Sample configuration above to import the certificates.
Router Gateway URL on phone does not match IOS router cert CN or SAN
By default in the VPN profile "Enable Host Id Check" is enabled, where the gateway certificate subjectAltName or CN must match the URL to which the VPN client is connected.If they dont, match you will get a "Authentication Failed" message
Suggested Action :
1) Modify the URL configured on CM to match the CN / SAN of the ceritificate. You can also create a new certificate that matches the URL configured
2) Unselect "Enabled Host ID check" from the VPN profile configuration.
One way voice or no audio
Make sure there is routing / network connectivity between the two phones
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Good one Tom,
Can I suggest to add same thing/section for ASA since you already mentioned it ?
Marcin
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Tom
I was testing this scenario, I am using CUCM 8.6, but i didnt found any option for VPN Group & phone-vpn-feature in CUCM. We have to activate this feature first or we have to purchase additional security license ?
Awais
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Awais,
What is the complete CUCM version you are running. As per the below document "The VPN menu and its options are not available in the U.S. export unrestricted version of Cisco Unified Communications Manager."
http://www.cisco.com/en/US/docs/voice_ip_comm/cucm/security/8_6_1/secugd/secuvpn.html
If this is not the issue, then the VPN option should show up under the Advanced Features option.
Regards,
Raees Shaikh
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Raees
Thanks buddy. Yes this was the issue, i just checked with other version & it work fines
Regards,
Awais
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Does this allow for the data port to pass traffic? I guess the real quesiton is can I use my phone to provide VPN services to my PC plugged into the data port?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
No, the data port is fully isolated from the phone VPN session, just like without VPN.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi everyone!
I have a problem
I've configured webvpn on my router that is behind ASA-firewall (nat, and other features configured correctly)
When I tried to connect to webvpn with anyconnect. User authenticates successfully. But this message appears in debug. And connected client can't see anything except his own IP address
Jun 8 04:57:58.371: %IPRT-6-STATICROUTESACROSSTOPO: Cannot install inter-topology static route 192.168.200.100/32 topology base on outgoing interface Virtual-Access2
Regards,
Kirill Sulima
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
LOL I've fixed this by myself
everything that was needed is to configure interface virtual-template 99
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: