- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Cisco Secure Firewall Device Manager - SNMP configuration using API
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
02-06-2021 04:23 AM - edited 11-08-2023 12:03 AM
Problem:
SNMP on FDM was introduced in version 6.7. As of now, we only have the option to push via API. The current method is time-consuming, and knowledge of API is needed.
Here is the current guide we have.
https://www.cisco.com/c/en/us/support/docs/security/firepower-ngfw/216551-configure-and-troubleshoot-snmp-on-firep.html
Solution
@Dinesh Verma and I created a script that automates the entire workflow using Python. You only need to enter the details pertaining to SNMPv2/SNMPv3; the script takes care of everything else. The script is available in the following GitHub repository.
https://github.com/anupamx47/FDM-SNMP/tree/main
1) Preparation:
1.Download the Script:
- Go to the script's GitHub page: fdm-snmp.py.
- Click the "Download Zip" button, under "code" to download the Python script to your computer.
2.Install Python:
- Make sure you have Python installed on your computer. You can download and install the latest version of Python from the official Python website: Python Downloads. Follow the installation instructions for your operating system.
3.Install Required Dependencies:
- Open a command prompt or terminal.
- Navigate to the directory where you downloaded the script.
- Run the following command to install the necessary dependencies:
pip3 install -r requirements.txt
4.Execute the Script:
- Open a command prompt or terminal.
- Navigate to the directory where you downloaded the script using the cd command.
- Run the script using Python:
python3 fdm-snmp.py
****************************************************************************************************
2) Create SNMPv2 Host
| C:\Users\anpavith\OneDrive\Desktop\scripts\FDM-SNMP> python3 fdm-snmp.py ########################################################### # CONFIGURE SNMP ON FDM # ########################################################### Enter the device IP address: 10.106.55.56 Enter the username of the FTD: admin Enter the password of the FTD: ########################################################### Auth-Status code is 200 Successfully Authenticated Would you like to configure (1) SNMPv2 or (2) SNMPv3 : 1 Enter the SNMP Server object name : solar22 Enter the SNMP Server object IP : 22.22.22.22 Enter SNMPv2 community string : cisco123 ########################################################### 1 diagnostic Management0/0 2 dmz GigabitEthernet0/2 3 inside GigabitEthernet0/1 4 outside GigabitEthernet0/0 Select the interface (Integer value only) : 4 Enter SNMP host object name : snmp22 ########################################################### Successfully Created, please deploy and check SNMP config ########################################################### |
3) Create SNMPv3 Host along with SNMPv3 user
| C:\Users\anpavith\OneDrive\Desktop\scripts\FDM-SNMP> python3 .\fdm-snmp.py ########################################################### # CONFIGURE SNMP ON FDM # ########################################################### Enter the device IP address: 10.106.55.56 Enter the username of the FTD: admin Enter the password of the FTD: ########################################################### Auth-Status code is 200 Successfully Authenticated Would you like to configure (1) SNMPv2 or (2) SNMPv3 : 2 Enter the SNMP Server object name : solar21 Enter the SNMP Server object IP : 21.21.21.21 Enter SNMPv3 username : cisco21 Enter Security Level => Options ['AUTH', 'NOAUTH', 'PRIV'] : PRIV Enter authentication Algorithm => Options ['SHA', 'SHA256'] : SHA Enter authentication password : cisco123 Enter encryption Algorithm => Options ['AES128', 'AES192', 'AES256', '3DES'] : AES128 Enter encryption password : cisco123 ########################################################### 1 diagnostic Management0/0 2 dmz GigabitEthernet0/2 3 inside GigabitEthernet0/1 4 outside GigabitEthernet0/0 Select the interface (Integer value only) : 4 Enter SNMP host object name : host21 ########################################################### Successfully Created, please deploy and check SNMP config ########################################################### |
Please use the script and provide us with any feedback.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Anupam Pavithran and @Dinesh Verma thanks so much for creating this useful script.
However, I found that it does not return the diagnostic Management1/1 interface as an option. (This is when I attempt to use it on a Firepower 2140 HA pair running FTD 6.7 with FDM management). It mostly returns currently unconfigured interfaces on the target FTD. Eth1/3 is a configured interface and Eth1/13-16 are assigned to portchannels (13-14 = Po1 and 15-16 = Po2)
Here is my output:
###########################################################
# CONFIGURE SNMP ON FDM #
###########################################################
Enter the device IP address: <redacted>
Enter the username of the FTD: admin
Enter the password of the FTD:
###########################################################
Auth-Status code is 200
Successfully Authenticated
Would you like to configure (1) SNMPv2 or (2) SNMPv3 : 1
Enter the SNMP Server object name : prime
Enter the SNMP Server object IP : <redacted>
###########################################################
1 Ethernet1/14
2 Ethernet1/11
3 Ethernet1/8
4 Ethernet1/10
5 Ethernet1/7
6 Ethernet1/9
7 Ethernet1/4
8 Ethernet1/5
9 Ethernet1/2
10 Ethernet1/6
Select the interface (Integer value only) :
(Note I also had to install the prerequisite requests module in my local python environment. "python -m pip install requests")
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Marvin,
Thanks for testing, I'll review the script and update.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
HI Anupam - I'm getting the following message when I try to use the script on my FP1010 running 6.7.0-65 with snort
I'm not sure if it matters, but Ethernet1/2-1/8 are all set up as switch ports. They are all set up as trunk ports, with Vlan1 (my legacy network VLAN) set as the native VLAN, and they also have access to VLANS 8 (core), 16 (userdevices), 24 (iot) and 32 (guestwifi) as well. For SNMP, they'd be talking to my Stealthwatch SMC on VLAN 8.
Here's the output from me running your script:
###########################################################
# CONFIGURE SNMP ON FDM #
###########################################################
Enter the device IP address: 172.16.8.1
Enter the username of the FTD: admin
Enter the password of the FTD:
###########################################################
Auth-Status code is 200
Successfully Authenticated
Would you like to configure (1) SNMPv2 or (2) SNMPv3 : 1
Enter the SNMP Server object name : snmpserver
Enter the SNMP Server object IP : 172.16.10.0
###########################################################
1 diagnostic Management1/1
2 outside Ethernet1/1
3 None Ethernet1/4
4 None Ethernet1/7
5 None Ethernet1/6
6 None Ethernet1/2
7 None Ethernet1/5
8 None Ethernet1/8
9 None Ethernet1/3
Select the interface (Integer value only) : 6
Enter SNMP host object name : snmphost
###########################################################
{'error': {'severity': 'ERROR', 'key': 'General', 'messages': [{'description': 'The server understands the content type of the request entity and the syntax of the request entity is correct but was unable to process the contained instructions', 'code': None, 'location': None}, {'description': 'InvalidTypeIdException: Missing type id when trying to resolve subtype of [simple type, SNMPSecurityConfiguration]: missing type id property \'type\' (for POJO property \'securityConfiguration\')\n at [Source: (UnclosableInputStream); line: 1, column: 374] (through reference chain: SNMPHost["securityConfiguration"])', 'code': None, 'location': None}]}}
###########################################################
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Marvin Rhoads and @davebush, we have fixed both the issues in the new build which is attached "Release_1.2.zip".
Thanks a lot for testing and sharing your valuable feedback
- Anupam
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Marvin Rhoads Just updated the attachment, you were way too fast
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @Anupam Pavithran - Looks like 1.2 has removed all options except the management interface and the outside interface.
davebush@lc19:~$ python3 fdm-snmp.py
###########################################################
# CONFIGURE SNMP ON FDM #
###########################################################
Enter the device IP address: 172.16.8.1
Enter the username of the FTD: admin
Enter the password of the FTD:
Auth-Status code is 200
Successfully Authenticated
Would you like to configure (1) SNMPv2 or (2) SNMPv3 : 1
Enter the SNMP Server object name : snmpserver
Enter the SNMP Server object IP : 172.16.10.0
Enter SNMPv2 community string : public
###########################################################
1 diagnostic Management1/1
2 outside Ethernet1/1
Select the interface (Integer value only) :
Ideally, I'd like to have this tied to Vlan8 which has the name core on my FP1010.
I'm happy to do a Webex if you'd like to get on my FP1010 and take a look. Just reach out to me on Teams.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for v1.2. I was able to use the updated script to successfully associate my snmp-server with the diagnostic interface.
I did need to go into FDM and then add an address for diagnostic interface (must be in same subnet as management interface) as well as a route for the diagnostic interface to the SNMP server address. (The route assigned to management for the clish dosen't also include traffic from the diagnostic interface in the LINA subsystem.) Once I did that I was able to successfully add the FTD device to my Cisco Prime Infrastructure server.
Now I need to work on generating some syslog messages. My goal is to have Prime send an email alert when a certain severity of log message is received from FTD (e.g. a firewall failover).
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@davebush Thanks for testing, as seen over WebEx vlan interfaces needs to be added too.
We'll include the same in the next build.
-Anupam
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Marvin Rhoads Sounds great! Again, thanks for testing
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks again, @Anupam Pavithran ! I'm glad we were able to get this working on my VLANs last night. I can confirm that after the work we did last night, 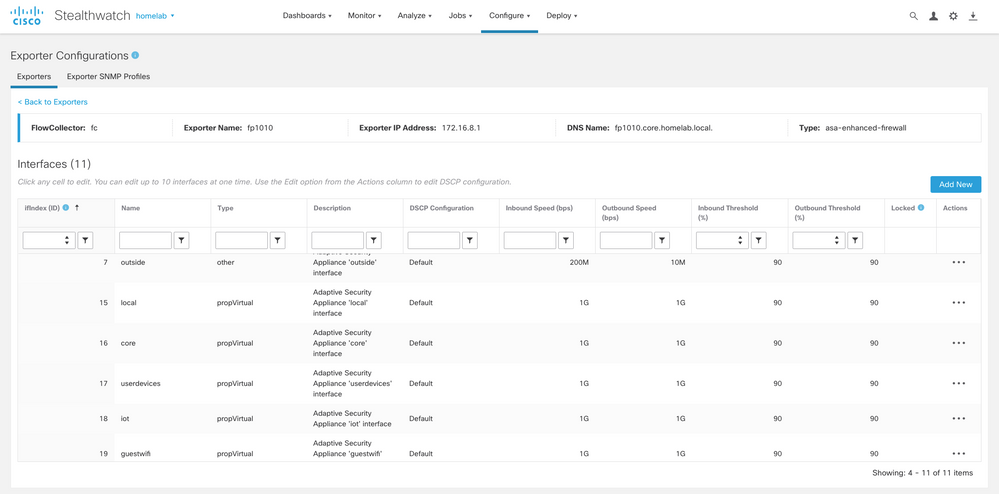
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Is there a way for me to do it via API explorer?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@IvanAlvarenga25979 you can follow the below link for configuring using API explorer
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
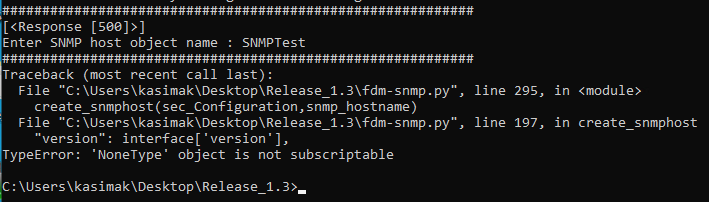
Hello,
I am trying to use it with FTD 6.6.1
I get the following
I see that it does not bring the interfaces
Is it because of the version or sth else?
Thanks and regards,
Konstantinos
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
The script is applicable for version FTD 6.7 and above.
-Anupam
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello,
I have a FP1010 managed using FDM. Need to configure SNMP on it. Version is 6.7.0-65. Have couple of questions as below
---- Step 3: Make sure proper permission is given to script to execute (This applies specifically if you're executing script from linux machine) --- If I use Windows Machine Permission perspective what I need to check ?
---- @Marvin Rhoads
Can you explain a little more for your below note ? I see my management Interface and diagnostic interface is same. Hence I do not think i will fall into below situation. Route perspective how can I check that from diagnostic/management Interface it can reach SNMP Server ? Note that I only have OutSide Interface and Mgmt/Diag Interface , other Interfaces is not connected yet which is part of Vlan 1.
"I did need to go into FDM and then add an address for diagnostic interface (must be in same subnet as management interface) as well as a route for the diagnostic interface to the SNMP server address. (The route assigned to management for the clish dosen't also include traffic from the diagnostic interface in the LINA subsystem.)"
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: