- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Configure L2TP over IPsec using Cisco ASA 8.4 and LDAP Authentication
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 12-13-2014 03:51 AM
Introduction:
This document describes the process of configuring L2TP over IPsec between Cisco ASA and windows 7 machine using LDAP authentication.
Prerequesites:
This document requires a basic understanding of IPsec protocol. To learn more about IPSec, please refer to An Introduction to IP Security (IPsec) Encryption.
Components Used:
Cisco Adaptive Security Appliance Software Version 8.4(2)
Cisco ASA 5520
Windows 7 machine
Windows 2008 Server (For LDAP)
Configuring AAA parameters:
We are talking about user authentication here. This authentication is done within L2TP framework, not IPSec. Depending on a LAC/LNS combination, and user database we are using, there are several choices here:
- PAP
- CHAP
- MS-CHAPv1
- MS-CHAPv2
- EAP
I would like to point out that all of these methods, except for some EAP types, are not considered secure and there are tools and ways of breaking these methods.
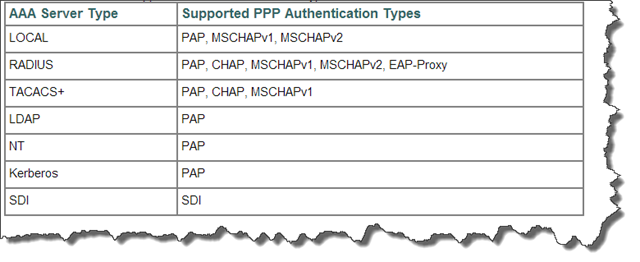
Diagram:
Configuration on Cisco ASA:
ASA Version 8.4(2)
!
!
interface GigabitEthernet0
nameif outside
security-level 0
ip address 47.47.47.100 255.255.255.0
!
interface GigabitEthernet1
nameif inside
security-level 100
ip address 192.168.2.1 255.255.255.0
!
!
object network local_lan
subnet 192.168.2.0 255.255.255.0
!
object network obj_192.168.2.0
subnet 192.168.2.0 255.255.255.0
!
object network obj_192.168.100.0
subnet 192.168.100.0 255.255.255.0
!
!
ip local pool L2TP-Pool 192.168.100.1-192.168.100.100 mask 255.255.255.0
!
!
nat (inside,outside) source static obj_192.168.2.0 obj_192.168.2.0 destination static obj_192.168.100.0 obj_192.168.100.0 no-proxy-arp route-lookup
!
object network local_lan
nat (inside,outside) dynamic interface
!
route outside 0.0.0.0 0.0.0.0 47.47.47.47 1
!
!
aaa-server LDAP protocol ldap
aaa-server LDAP (inside) host 192.168.2.100
ldap-base-dn DC=testlab,DC=com
ldap-scope subtree
ldap-naming-attribute sAMAccountName
ldap-login-password Y0u@rmyl1fe
ldap-login-dn CN=ASA Admin,CN=Users,DC=testlab,DC=com
server-type microsoft
!
!
crypto ipsec ikev1 transform-set L2TP-set esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set L2TP-set mode transport
!
crypto dynamic-map client-map 10 set ikev1 transform-set L2TP-set
crypto map outside-map 65535 ipsec-isakmp dynamic client-map
crypto map outside-map interface outside
!
!
crypto ikev1 enable outside
crypto ikev1 policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
!
!
group-policy L2TP-Client internal
group-policy L2TP-Client attributes
dns-server value 192.168.2.100
vpn-tunnel-protocol l2tp-ipsec
default-domain value testlab.com
!
!
tunnel-group DefaultRAGroup general-attributes
address-pool L2TP-Pool
authentication-server-group LDAP
default-group-policy L2TP-Client
tunnel-group DefaultRAGroup ipsec-attributes
ikev1 pre-shared-key cisco
tunnel-group DefaultRAGroup ppp-attributes
authentication pap
no authentication chap
no authentication ms-chap-v1
no authentication ms-chap-v2
!
!
: end
Configuration on Windows Machine:
1. Click on Start and select Control Panel:
2. Select Network and Sharing center :
3. Select "Set up a new connection or network":
4. Select "Connect to a workplace:
5. Select Use my Internet Connection (VPN):
6. Add the public IP address of the ASA (IP on the outside interface of the ASA). Destination name is optional and you can choose anything of your choice and then click on NEXT:
7. Add the username and the password and select "Remember Password" and click on create:
8. In the network and sharing center you will see the connection tab, right click on and click on Properties.
9. In the general TAB make sure the IP address is correct.
10. In the security TAB make sure that type of connection is set to L2TP/IPsec.
11. Go to Advanced settings and add the pre-shared key
12. In the Security, under allow these protocols select only PAP as with ldap only pap is supported and then click on OK.
13. Double click on L2TP icon and you will get the connection window. Make sure username and passwords are correct. Then click on Connect. And if everything else in place it will get connected :)
Successful debug ldap 255:
[28] Session Start
[28] New request Session, context 0xbc440bd0, reqType = Authentication
[28] Fiber started
[28] Creating LDAP context with uri=ldap://192.168.2.100:389
[28] Connect to LDAP server: ldap://192.168.2.100:389, status = Successful
[28] supportedLDAPVersion: value = 3
[28] supportedLDAPVersion: value = 2
[28] Binding as ASA Admin
[28] Performing Simple authentication for ASA Admin to 192.168.2.100
[28] LDAP Search:
Base DN = [DC=testlab,DC=com]
Filter = [sAMAccountName=l2tp_test]
Scope = [SUBTREE]
[28] User DN = [CN=l2tp,CN=Users,DC=testlab,DC=com]
[28] Talking to Active Directory server 192.168.2.100
[28] Reading password policy for l2tp_test, dn:CN=l2tp,CN=Users,DC=testlab,DC=com
[28] Read bad password count 0
[28] Binding as l2tp_test
[28] Performing Simple authentication for l2tp_test to 192.168.2.100
[28] Processing LDAP response for user l2tp_test
[28] Message (l2tp_test):
[28] Authentication successful for l2tp_test to 192.168.2.100
[28] Retrieved User Attributes:
[28] objectClass: value = top
[28] objectClass: value = person
[28] objectClass: value = organizationalPerson
[28] objectClass: value = user
[28] cn: value = l2tp
[28] givenName: value = l2tp
[28] distinguishedName: value = CN=l2tp,CN=Users,DC=testlab,DC=com
[28] instanceType: value = 4
[28] whenCreated: value = 20141208213229.0Z
[28] whenChanged: value = 20141213085354.0Z
[28] displayName: value = l2tp
[28] uSNCreated: value = 28717
[28] uSNChanged: value = 32836
[28] name: value = l2tp
[28] objectGUID: value = ..%..l.G..W...:.
[28] userAccountControl: value = 66048
[28] badPwdCount: value = 0
[28] codePage: value = 0
[28] countryCode: value = 0
[28] badPasswordTime: value = 0
[28] lastLogoff: value = 0
[28] lastLogon: value = 0
[28] pwdLastSet: value = 130629337074722838
[28] primaryGroupID: value = 513
[28] userParameters: value = m: d.
[28] objectSid: value = .............XpXY>.....JP...
[28] accountExpires: value = 9223372036854775807
[28] logonCount: value = 0
[28] sAMAccountName: value = l2tp_test
[28] sAMAccountType: value = 805306368
[28] userPrincipalName: value = l2tp_test@testlab.com
[28] objectCategory: value = CN=Person,CN=Schema,CN=Configuration,DC=testlab,DC=com
[28] dSCorePropagationData: value = 16010101000000.0Z
[28] lastLogonTimestamp: value = 130625488281374696
[28] Fiber exit Tx=527 bytes Rx=2286 bytes, status=1
[28] Session End
Check the connection Status on ASA:
show vpn-sessiondb detail ra-ikev1-ipsec
Session Type: IKEv1 IPsec Detailed
Username : l2tp_test Index : 14
Assigned IP : 192.168.100.1 Public IP : 57.57.57.110
Protocol : IKEv1 IPsec L2TPOverIPsec
License : Other VPN
Encryption : 3DES Hashing : SHA1 none
Bytes Tx : 3678 Bytes Rx : 25834
Pkts Tx : 41 Pkts Rx : 231
Pkts Tx Drop : 0 Pkts Rx Drop : 0
Group Policy : L2TP-Client Tunnel Group : DefaultRAGroup
Login Time : 11:44:42 UTC Sat Dec 13 2014
Duration : 0h:02m:26s
Inactivity : 0h:00m:00s
NAC Result : Unknown
VLAN Mapping : N/A VLAN : none
IKEv1 Tunnels: 1
IPsec Tunnels: 1
L2TPOverIPsec Tunnels: 1
IKEv1:
Tunnel ID : 14.1
UDP Src Port : 500 UDP Dst Port : 500
IKE Neg Mode : Main Auth Mode : preSharedKeys
Encryption : 3DES Hashing : SHA1
Rekey Int (T): 28800 Seconds Rekey Left(T): 28692 Seconds
D/H Group : 2
Filter Name :
IPsec:
Tunnel ID : 14.2
Local Addr : 47.47.47.100/255.255.255.255/17/1701
Remote Addr : 57.57.57.110/255.255.255.255/17/1701
Encryption : 3DES Hashing : SHA1
Encapsulation: Transport
Rekey Int (T): 3600 Seconds Rekey Left(T): 3492 Seconds
Rekey Int (D): 250000 K-Bytes Rekey Left(D): 249975 K-Bytes
Idle Time Out: 30 Minutes Idle TO Left : 29 Minutes
Bytes Tx : 3678 Bytes Rx : 25834
Pkts Tx : 41 Pkts Rx : 231
L2TPOverIPsec:
Tunnel ID : 14.3
Username : l2tp_test
Assigned IP : 192.168.100.1 Public IP : 110.57.57.57
Encryption : none Auth Mode : PAP
Idle Time Out: 30 Minutes Idle TO Left : 29 Minutes
Client OS : Microsoft
Client OS Ver: 6.1
Bytes Tx : 3151 Bytes Rx : 23666
Pkts Tx : 36 Pkts Rx : 223
NAC:
Reval Int (T): 0 Seconds Reval Left(T): 0 Seconds
SQ Int (T) : 0 Seconds EoU Age(T) : 146 Seconds
Hold Left (T): 0 Seconds Posture Token:
Redirect URL :
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
can you please share the same config in GUI?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello. Can you explain how to config VPN L2TP over IPsec using Cisco ASA 8.4 and RADIUS Authentication, similar to (https://supportforums.cisco.com/document/12376201/l2tp-over-ipsec-cisco-ios-router-using-radius-authentication), but applied to the ASA, as this article.
Thank you
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello,
Nice Post. Thanks For Sharing.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @Jeet Kumar
Can we have multiple users to connect to it. I have local authentication happening on the ASA as per this config:
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

