- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 02-02-2021 03:25 AM
Overview
Securing the network by ensuring the right users, the right access, to the right set of resources is the core function of Cisco’s Identity Services Engine (ISE). ISE builds context about users (Who), device type (What), access time (When), access location (Where), access type (wired/wireless/VPN) (How), and most important threats, and vulnerabilities. All of these pieces of contextual data is fed into defining logical policy groups, called Scalable Group Tags, for every connected endpoint. These context-aware tags are then used to form the basis of security policies, centrally managed on ISE and enforced on different parts of the network in a traditional way or using the network fabric- as part of Software Defined Access (SDA).
Duo Security is highly aligned to our intent-based networking vision and strategy, and reinforces our existing ISE and DNA Center capabilities. Additionally, it will help accelerate the adoption of SDA, by extending policy into the cloud and by unifying network segmentation with cloud access control. We are bringing together application zero trust capabilities from Duo, with network zero trust capabilities from SDA, to create the industry's only comprehensive network and cloud access control solution.
Configuration Objective:
“I have employees and contractors on my network. My objective is to securely connect these users by using MFA and then assign them a secure network policy by using ISE for segmentation. Employees and Contractor’s are on the same network but they cannot talk to each other. Employee’s get full access to my on-prem network resources or network resources in my data center, Contractors get limited network access.
Configuration Overview:
Configure ISE’s web-based authentication portal as a protected application with Duo MFA. After successful 2FA, ISE grants users network access based upon Group-Based Policies.
Segmentation Policy:
- Employees connect to the network and get a network policy with SGT=Employee
- Contractors connect to the network and get a network policy with SGT=Contractor
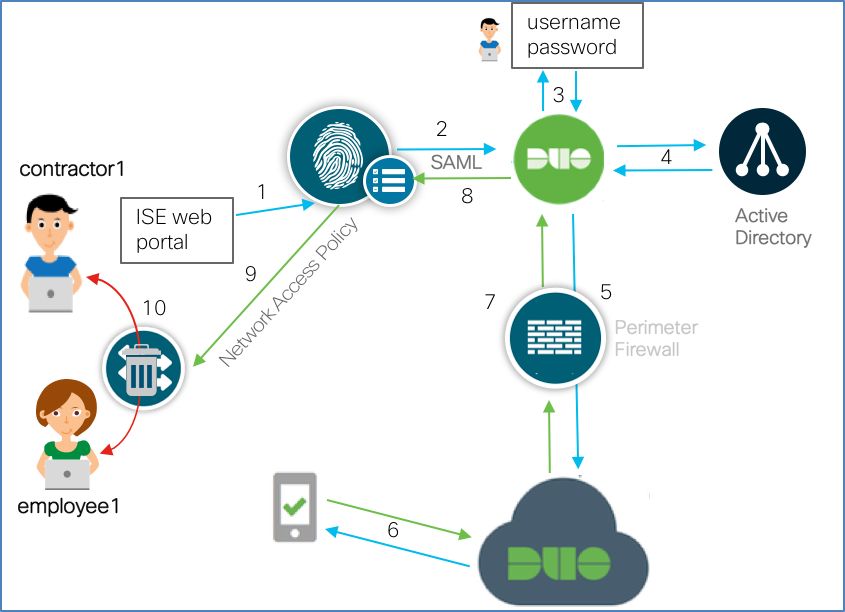
Connection flow:
- Users connects and is redirected to ISE portal
- ISE redirects the unauthenticated request to the Duo Access Gateway (DAG)
- Because the ISE portal is a protected application, prompts the user for authentication
- Users’s credentials are verified against Active Directory
- DAG then sends notification for MFA
- Users get a notification for DUO PUSH, Users click “Approve” on mobile device
- DAG receives authentication success notification.
- ISE receives response
- ISE authorizes network access and pushes Employee or Contractor Scalable Group Tag (SGT)
- As per SGT-based network policy, Employees and contractors are on the same Layer 2 network but cannot talk to each other (East-West segmentation/Microsegmentation)
Configuration Part 1: Protecting ISE web portal with Duo MFA
The Duo terminology “protecting an application” simply means that access to that application is redirected through the Duo Access Gateway. This redirection is necessary to add in second factor authentication before allowing application access (this assumes that network layer access is not restricted). In addition, the DAG can also enforce additional application policies such as checking the user, device, and network permissions specified by the DUO Administration panel.
Adding an application to Duo
Note: Before proceeding it is assumed that an identity source has been configured. If this step has not been done, please reference Duo Access Gateway for more details.
The steps below ties in the ISE Guest web portal as a protected application to add in the secondary authentication sequence with Duo PUSH. ISE Guest allows users to gain network access via a HTTP or HTTPS login. Duo Single Sign on will then initiate the 2nd authentication back to the user via DUO push.
- Log into your DUO Access Gateway
- In the left side bar, navigate to Applications
- Scroll down to the center of the page to the MetaData section and click “download XML metadata” and save the file
- Log into ISE
- Navigate to Administration->Identity Management->External Identity Sources->SAML ID Providers
- Click ADD
- On the resulting window, starting from left to right, configure the settings within each tab menu item as follows:
- In the General tab, use “duoSAML” as the Id Provider Name
- In the Identity Provider Config tab, upload the xml file from Step 3
- Skip the Service Provider Info tab, you’ll come back to it later
- In the Groups tab, select the user groups relevant to your authentication requirements
- Click Submit
8. Navigate to Work Centers->Guest Access->Portals & Components->Guest Portals
9. Click the link Sponsored Guest Portal (default)
10. Expand “Portal Settings” and select the profile name configured in step 5a. (e.g. duoSAML)
11. Click Save
12. Navigate back to Administration->Identity Management->External Identity Sources->SAML ID Providers-duoSAML
13. From the Service Provider Info tab, click Export and save the resulting zip file.
Note: The files in this zip contain the application configuration data required to bind Duo to the ISE guest portal
Binding ISE web authentication portal with Duo
15. Extract the zip and view the extracted xml file
16. Search for the "Entity ID" string and copy the resulting string ( the string would look something link this: "http://CiscoISE/f079c670-7159-11e7-a355-005056aba474")
17. Log in to the Duo Admin Panel and click Applications, and then click Protect an Application
18. Locate SAML Service Provider in the list of applications, and then click the Protect this Application link.
19. Enter the following information:
| Name | Description |
| Service Provider Name | e.g. ISE Portal |
| Entity ID | copied string from Step 16 |
| Assertion Consumer Service | https://<ISE FDQN>:8443/portal/SSOLoginResponse.action |
20. Scroll to the bottom and click Save Configuration button and download the configuration file.
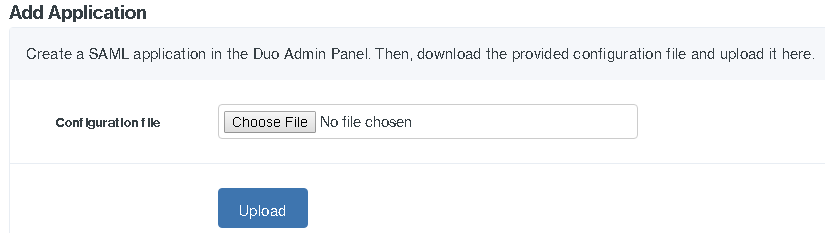
Add ISE Portal to Duo Access Gateway
21. Log in to the Duo Access Gateway
22. Navigate to Applications. Upload the .json configuration file from Step 20
Verifying ISE and DUO MFA
23. On ISE, navigate to Work Centers->Guest Access->Portals -> Components->Guest Portals
24. Click the link Sponsored Guest Portal (default)
25. Right click and copy the link for “Portal Test URL”
- Paste the link address into a text editor
- Change the link address from using the ISE IP to the ISE FQDN (include port 8443)
Note: These steps are to workaround an ISE defect
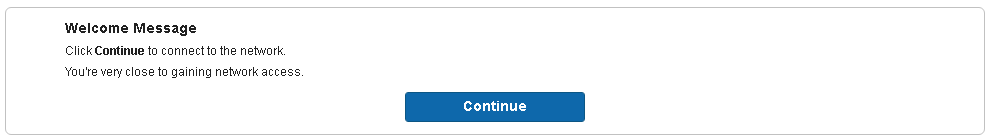
26. Paste the edited link into a browser. After successfully authenticating, you should see the following pop up
27. Click Continue. This concludes the test
Finalizing ISE and Duo MFA Integration
In the steps below, you will enable web authentication so that users are redirected to the ISE Guest Portal to start the MFA process.
28. Log into ISE, navigate to Policy->Policy Elements->Results->Authorization->Authorization Profiles
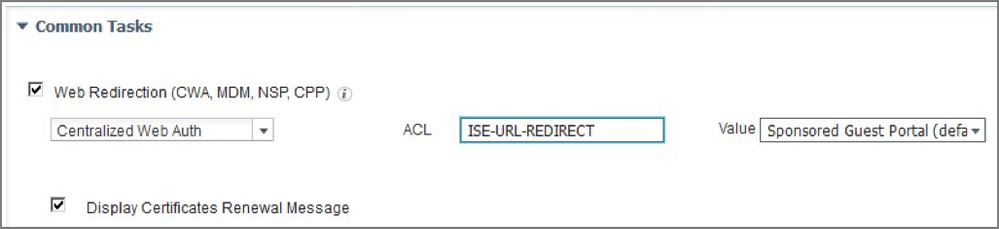
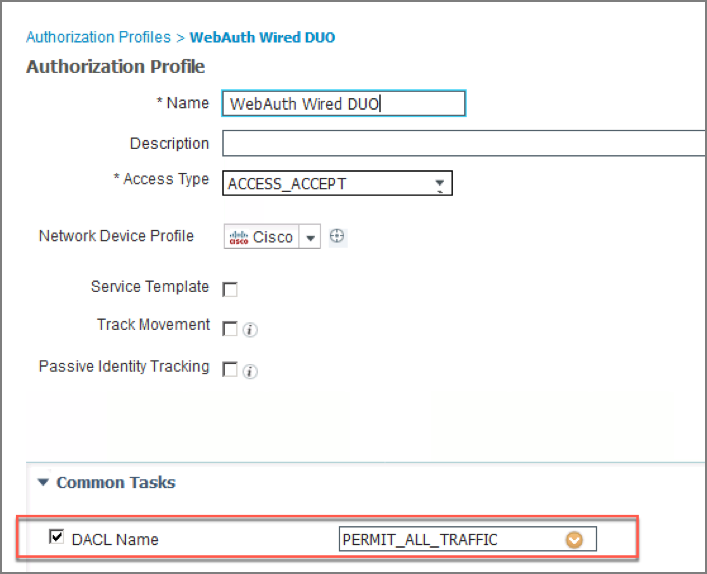
29. Create an authorization profile, such as “WebAuth Wired DUO”, with the following configuration:
30. Continue to scroll down within Common Tasks to select “Web Redirection”. Configure as follows:
31. Click Submit
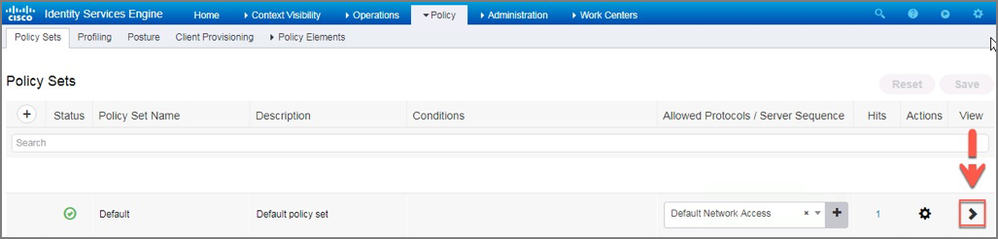
32. Navigate to Policy->Policy Sets
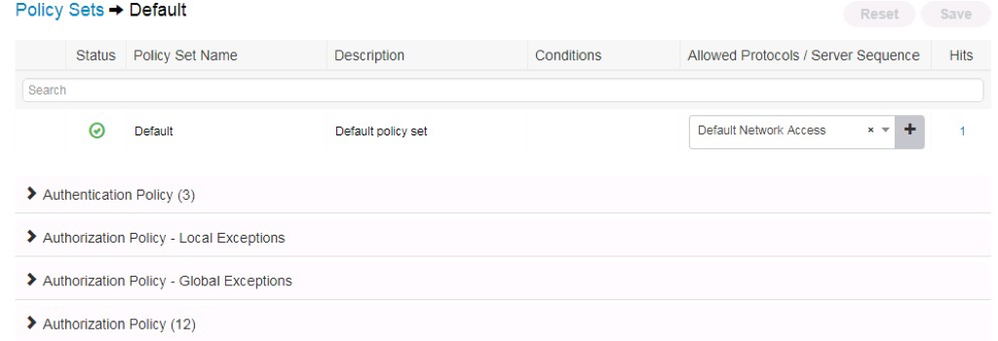
33. Expand the default policy set by clicking the > on the right of the screen
The resulting view will look like this:
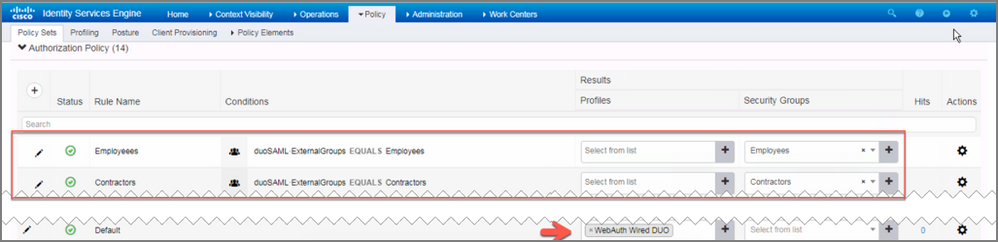
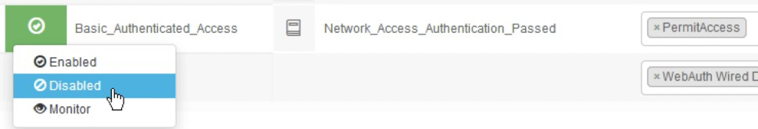
34. Expand Authorization Policy. Add new policies that reference the SAML groups from Step 7. Also modify the Default policy to user the "WebAuth Wired DUO" profile rather than "Deny Access"
Note: Also disable the Basic_Authenticated_Access rule
Configuration Part 2: Securing Network Access with Micro-Segmentation
In the previous exercise you configured ISE and DUO to work together to secure the network connection process with Duo MFA. Now that the user is connected, in the steps below you will further secure network access using group-based segmentation. In the example below, the policy created will mitigate the spread of malware between Employees and Contractors.
Note: Some TrustSec configuration steps have been pre-configured. Please see the appendix for these details.
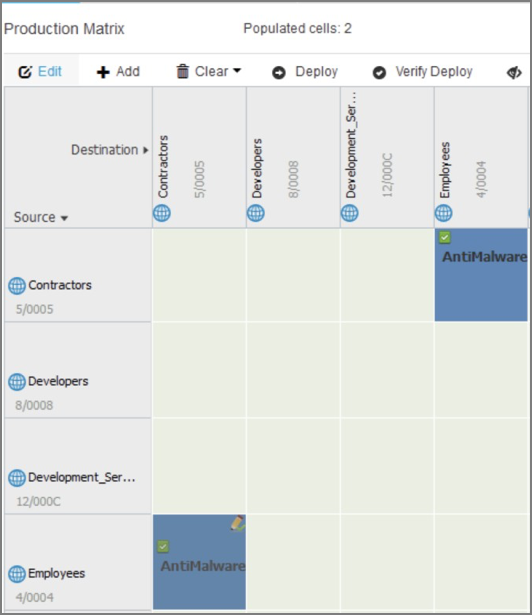
1. On ISE, navigate to Work Centers->TrustSec->TrustSec Policy
2. Select ADD in the policy matrix menu
3. Configure new policies as follows:
4. Click Save
Note: The “Anti-Malware SGACL” contains rules that deny specific tcp and udp traffic. To review the rules contained within this SGACL, navigate to Work Centers->TrustSec->Components->Security Group ACLs
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @faylee ,
Great Post. I got some idea after reading your post and increase my confidence level. I have a query, regarding an use case currently facing in deployment with a customer. Customer has 11 GCP workspace domain separately. Our team suggest them to integrate but they said not possible. Rather our team created 2 different duo admin accounts ,integrated with GCP and ISE. Currently one known user in first domain case is tested but second one domain result is not like first one. My question is can we create 11 different SAML idp in ISE and apply in authorization policy like you mentioned above ,and also TRUSTSEC. Will it work for 11 different domain authenticate in same OPEN ssid and communicate each other? And also we opened a TAC case that how customer duo one subscription license for n user will be applicable to different duo account that can be fetched from cisco software smart licensing.
Cheers,
Santhosh
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: